Legal Privacy Ethical Issues K Salah 1 Overview


















- Slides: 20

Legal, Privacy, & Ethical Issues K. Salah 1

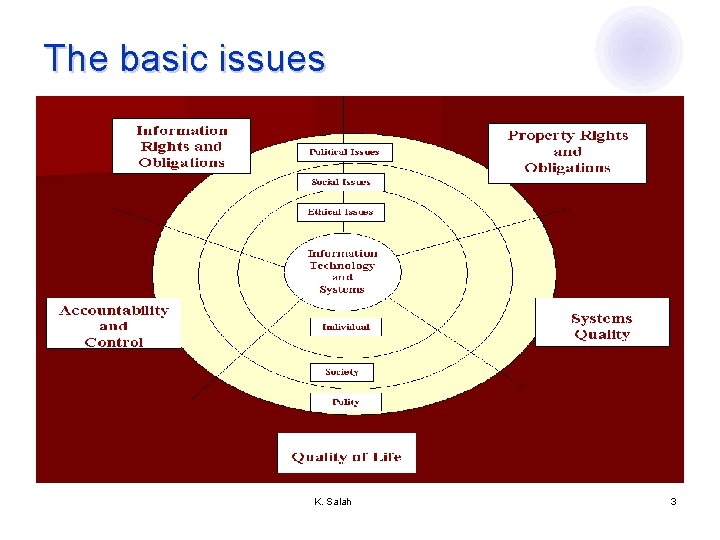
Overview l Human Controls Applicable to Computer Security The Basic Issues l Computer Crime l Privacy l Ethical Issues l Codes of Professional Ethics l K. Salah 2

The basic issues K. Salah 3

Protecting Programs and Data l Copyrights—works of the mind Intellectual Property l Digital Millennium Copyright Act l l Patents—tangible objects l Trade Secrets—competitive edge info K. Salah 4

Intellectual Property l Intellectual property == information that belongs to someone ¡ ¡ ¡ l May be protected by ¡ ¡ ¡ l Book Movie Program Copyright Patent Trade secret Computer security can help with some of these ¡ Not much help with patents K. Salah 5

Copyrights l Designed to protect the expression of ideas ¡ ¡ Limited to a particular specific expression May be more than one copyright for a given expression l l Limited in time ¡ ¡ ¡ l Expire 70 years after author’s death Expire after 95 years (if owned by corporation) These limits can change, and have been getting longer recently Public domain ¡ ¡ ¡ l Composer: the score Lyricist: the lyrics to the song Artist: a particular performance of the song Public “owns” the copyright Common for government documents Older works pass into the public domain Collections can be copyrighted even if the individual components aren’t subject to copyright K. Salah 6

Fair use l Copyrighted item is subject to fair use ¡ ¡ l May be excerpted for teaching, criticism, etc. Definition of fair use depends on many factors First sale ¡ ¡ ¡ Author controls the first sale of a copyrighted work: receives benefits from its sale Owner controls future sales: owner may resell it to anyone without contacting the copyright holder Owner may only sell a copy he currently owns K. Salah 7

Patents l Cover an implementation of an idea ¡ ¡ l Patents are public ¡ ¡ l Searchable at www. delphion. com Download PDF for $3 each Patent protection ¡ ¡ l Patent has details on how to implement the object Patent should have enough information to allow someone to actually build the object! Nobody is allowed to make an object covered by the patent without licensing it from the patent owner Deciding what’s covered is difficult. Patent lasts for about 18 years K. Salah 8

More on patents l Patent must be novel ¡ ¡ l Patent holder must oppose all infringement ¡ ¡ l Even small infringers have to be pursued Copyright holder need only go after major offenders Patent can be lost ¡ ¡ ¡ l Only one patent per idea: if multiple independent inventors, still only one patent (one inventor loses) Patent must not be obvious Holder didn’t pursue all infringers Patent was obvious and shouldn’t have been granted Someone else invented it first Patents best for big companies, not individuals K. Salah 9

Trade secrets l Not legally protected ¡ ¡ l Can’t uncover the secret, but can ¡ ¡ l Must be kept secret! Legal action can be taken against someone who (illegally) reveals the secret Reverse engineer the process Independently invent something that does the same thing Difficult to enforce! ¡ ¡ ¡ Reverse engineering -- OK Revealing the secret isn’t Distinguishing these can be difficult K. Salah 10

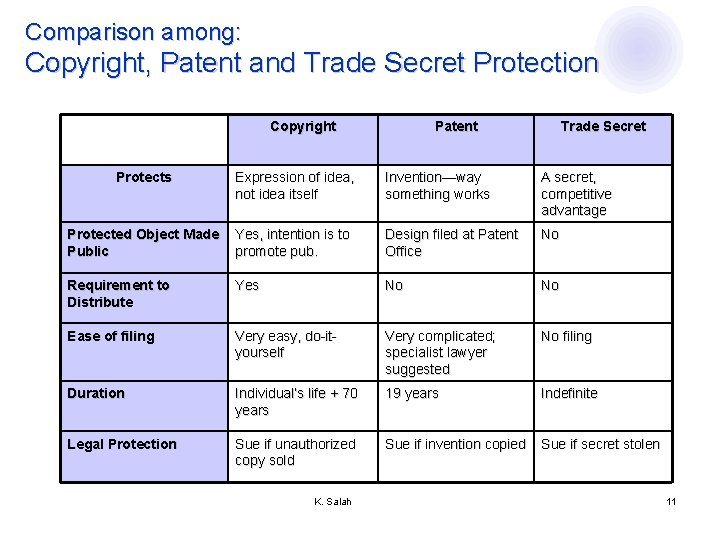
Comparison among: Copyright, Patent and Trade Secret Protection Copyright Patent Trade Secret Protects Expression of idea, not idea itself Invention—way something works A secret, competitive advantage Protected Object Made Public Yes, intention is to promote pub. Design filed at Patent Office No Requirement to Distribute Yes No No Ease of filing Very easy, do-ityourself Very complicated; specialist lawyer suggested No filing Duration Individual’s life + 70 years 19 years Indefinite Legal Protection Sue if unauthorized copy sold Sue if invention copied Sue if secret stolen K. Salah 11

Licensing vs. Ownership If program is sold (under copyright), owner can resell it to someone else l If program is licensed, “owner” must abide by licensing terms l ¡ ¡ l May restrict redistribution May restrict other uses (it’s a license) Licensing may avoid some problems, but opens others ¡ What if the program doesn’t work? l l ¡ ¡ Copyright has no guarantees License has to say what you’re licensing for Making backup copies? Using the program on multiple machines? K. Salah 12

Rights of Employees/Employers l Ownership of Products l Ownership of a Patent l Ownership of a Copyright l Work for Hire l Licenses l Trade Secret Protection l Employment Contracts K. Salah 13

Software Failures l Selling correct software l Reporting software flaws Vendor interests l User interests l Responsible vulnerability reporting l Quality Software l K. Salah 14

Computer Crime l l l l Rules of Property Rules of Evidence Threats to Integrity and Confidentiality Value of Data Acceptance of Computer Terminology Hard to Define Hard to Prosecute l US Computer Fraud and Abuse Act l US Economic Espionage Act l US Electronic Funds Transfer Act l US Freedom of Information Act l US Privacy Act l US Electronic Communications Privacy Act l USA Patriot Act K. Salah 15

Computer Crime (cont’d) l International EU Data Protection Act l Restricted Content l Cryptography Use l l Criminals are hard to catch l Law is not precise K. Salah 16

Cryptography Challenges l Controls on export l Controls on use l Free speech issues l Key escrow issues K. Salah 17

III. Privacy l l l l l Identity Theft Aggregation and Data Mining Poor System Security Government Threats The Internet Privacy vs. Security Concerns Corporate Rights and Private Business Privacy for Sale Controls l l l Authentication Anonymity Computer Voting Pseudonymity The Law—EU Protection Act, HIPAA, Graham-Leach-Bailey K. Salah 18

IV. Ethical Issues l Law vs. Ethics l Ethics vs. Religion Universality ? ? l Pluralism ? ? l l Ethical Approaches Consequence-based—i. e. utilitarianism l Rules-based—deontology l K. Salah 19

V. Codes of Ethics l IEEE l ACM l Computer Ethics Institute l 10 Commandments of Computer Use Brookings Institute K. Salah 20
 Legal and ethical issues chapter 5
Legal and ethical issues chapter 5 Chapter 2 ethical and legal issues
Chapter 2 ethical and legal issues Ethical issues in e-commerce
Ethical issues in e-commerce Ethical and legal issues chapter 2
Ethical and legal issues chapter 2 Legal and ethical aspects of nursing chapter 3
Legal and ethical aspects of nursing chapter 3 Medical legal and ethical issues chapter 3
Medical legal and ethical issues chapter 3 Chapter 6 legal and ethical issues
Chapter 6 legal and ethical issues Legal and ethical issues in use of ict in education
Legal and ethical issues in use of ict in education What is the difference between ethical and legal issues
What is the difference between ethical and legal issues Medical legal and ethical issues chapter 3
Medical legal and ethical issues chapter 3 Legal and ethical issues in information security
Legal and ethical issues in information security Legal and ethical issues in computer security
Legal and ethical issues in computer security Chapter 2 ethical and legal issues
Chapter 2 ethical and legal issues Legal and ethical issues chapter 3
Legal and ethical issues chapter 3 Chapter 3 legal and ethical issues
Chapter 3 legal and ethical issues Resourceful citer
Resourceful citer Ethical and legal issues in community health nursing
Ethical and legal issues in community health nursing Chapter 6 legal and ethical issues
Chapter 6 legal and ethical issues Legal issues in psychiatric nursing
Legal issues in psychiatric nursing Ethical and legal issues involved in practicum
Ethical and legal issues involved in practicum Chapter 5 legal and ethical responsibilities
Chapter 5 legal and ethical responsibilities






































