ITIS 3200 Introduction to Information Security and Privacy








- Slides: 9

ITIS 3200: Introduction to Information Security and Privacy Dr. Weichao Wang

• Chapter 2: A concrete example: Access Control Matrix – First introduced in OS and databases – Describe allowed access using a matrix – Protection state of the system – Describe the protection state by characterizing rights of each subject over objects. – We are especially interested in state transitions that will affect the protection states.

• Access control matrix model – Objects O: the set of protected entities – Subjects S: the set of active objects that can perform actions (process or user) – Rights R: the full right set. For every pair (s, o), a subset of rights is granted. – The set of protection states is represented by (S, O, A) – Some subjects can also be objects – An example

• Access control matrix model (continued) – The meaning of rights depends on system and objects involved – The access control matrix can model a large system containing multiple machines, or a programming language at the micro level – The matrix can also contain functions to determine rights (mutual access)

• Protection state transitions – Operations will lead to changes of states, and updates in access control matrix • State Xi will change to state X(i+1) under command c(i+1) • A command may have multiple parameters and lead to multiple state transitions (share a folder in a OS)

• Primitive command – Create subject s – Create object o – Enter right r into a[s, o] – Delete right r from a[s, o] – Destroy subject s – Destroy object o

• Primitive commands can be combined into commands – System usually does not directly call primitive commands, but through another level of wrapper – A command invoking only one primitive is called mono-operational command – Conditional commands do not support negation

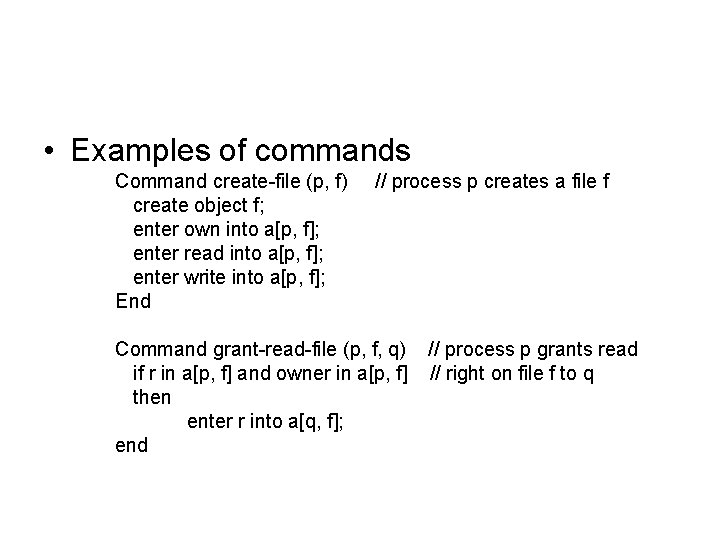
• Examples of commands Command create-file (p, f) create object f; enter own into a[p, f]; enter read into a[p, f]; enter write into a[p, f]; End // process p creates a file f Command grant-read-file (p, f, q) if r in a[p, f] and owner in a[p, f] then enter r into a[q, f]; end // process p grants read // right on file f to q

• Some concepts that we need to understand: – Protection state and access control matrix – State transition caused by operations and command – Access control matrix is not used directly because of space requirements.