ITIS 3200 Introduction to Information Security and Privacy














- Slides: 15

ITIS 3200: Introduction to Information Security and Privacy Dr. Weichao Wang

Syllabus • See handout – Homework will usually have 4 -5 questions and due in one week. It is due at the time that the class begins. – Late homework and term paper • Within 24 hours: 50% of full score • After that: 0% – Project • Individual project – Conduct some hands-on experiments – Or choose a security problem and write a survey paper – A reference question list will be provided – Midterm and final exam – Misc: eating, drinking, and cell phone (text & twitter)

Before class • An interesting question – Two companies each has some private data. They need to jointly calculate some result without disclosing their information. • Secure multiparty computation • Is this solution useful? – Zero knowledge proof: • Can I prove to you that I know a secret without telling you anything? (practically) – Anonymously publishing data or information

Perfect Storm of Social Networks • In 2011, Facebook announced they had surpassed 750 M users. Twitter claims 175 M registered users • Almost 68% of all Internet traffic is social media or search • Facebook is the 4 th largest website in the world having grown 157% between 2008 and 2009 – 1, 928% in the US alone • Social media marketing will grow from $714 M in 2009 to $3. 1 B by 2014 • Attacks on social media sites is up 240% from phishing attacks alone 4

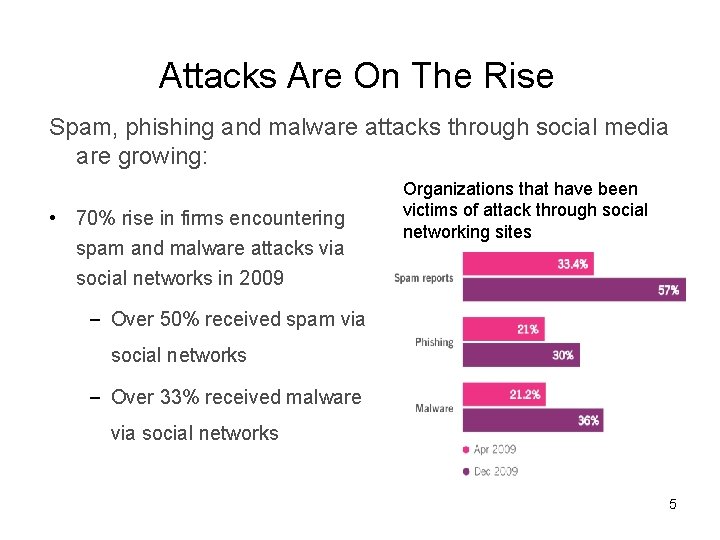
Attacks Are On The Rise Spam, phishing and malware attacks through social media are growing: • 70% rise in firms encountering spam and malware attacks via social networks in 2009 Organizations that have been victims of attack through social networking sites ‒ Over 50% received spam via social networks ‒ Over 33% received malware via social networks 5

Examples in real life • Attack on Twitter – Hack into the victim’s email account – DDo. S to paralyze Twitter, facebook, etc • Data mining attacks on public database – In Tenn, a newspaper generates a database about all residents that have CCW permits. – In CA, there is a webpage listing all people that donate to Proposition 8 ballot measure

Examples in real life • Worm attack on smart grid • Use social network to detect disease breakout • Remotely control insulin pump of a patient • Code during the war – Navajo Code in WWII – http: //www. imdb. com/gallery/ss/0245562/W 266 R. jpg

– Computers have controlled our lives • Medical, ATM, banking, business • Air traffic control

Security overview • Risks – Why there are risks • Adversaries – Smart and dedicated – Many of them, considering the high employment rate – Hiding in the dark – From fun to profit (worm self-changing botnet target at specific systems)

Security overview • Physical security is not enough (can you be sure that your physical security methods are sound and enough? Example in Las Vegas, supply chain attacks, internal attacks) • Networked computers can be accessed remotely

Security overview • What can go wrong – Trojan war story (trojan horse): USB keys – Corrupted internal worker – Vulnerabilities of protocols or security mechanisms (security patch has problems too) – By-passing protection walls – Backdoors for systems (Linux password) – Known attacks ignored (push and poll)

Information security • Encryption – You can read the information only when you know the key • Authentication – You are who you claim you are • Authorization – The role and the right

Information security • Information integrity – The data has never be changed or changed in an inappropriate way • Non-repudiation – Cannot deny your words (digital cash example) • Privacy – Who should know, how much, how to use the information • Your cell phone or medical records • RFID • Your smart meter

Security overview • Defending methods – Prevention • • Prevent (password, salt, private salt, searching) Deter: raising the bar (password guessing, login slow) Deflect: making other target more attractive Diversify – Detection • • Monitoring (who, what, and how) Intrusion detection (signature based, anomaly based) IP telephony track Authenticity of the evidence (digital media)

Security Overview • Recovery – Recover data (check point) – Identify the damage – Forensics – Confinement • Tolerance – Maintain a decent service quality – Automatically degrade video quality while reserving bandwidth for voice