Griffin Software Security Project Static and Runtime Solutions

- Slides: 6

Griffin Software Security Project Static and Runtime Solutions for Web Application Vulnerabilities TRUST NSF Site Visit, Berkeley, April 27 th- 28 th, 2006

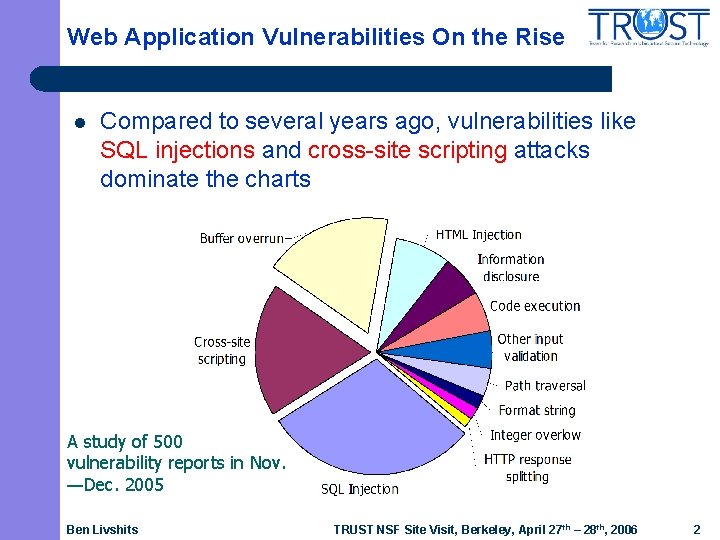
Web Application Vulnerabilities On the Rise l Compared to several years ago, vulnerabilities like SQL injections and cross-site scripting attacks dominate the charts A study of 500 vulnerability reports in Nov. —Dec. 2005 Ben Livshits TRUST NSF Site Visit, Berkeley, April 27 th – 28 th, 2006 2

Griffin Application Security Project l Project home: – l http: //suif. stanford. edu/~livshits/work/griffin/ We propose a hybrid static/runtime solution to Web application vulnerabilities – Goes after the most prominent vulnerability types: l l l – SQL injections Cross-site scripting Path traversal HTTP splitting etc. Our focus is on Java J 2 EE applications Ben Livshits TRUST NSF Site Visit, Berkeley, April 27 th – 28 th, 2006 3

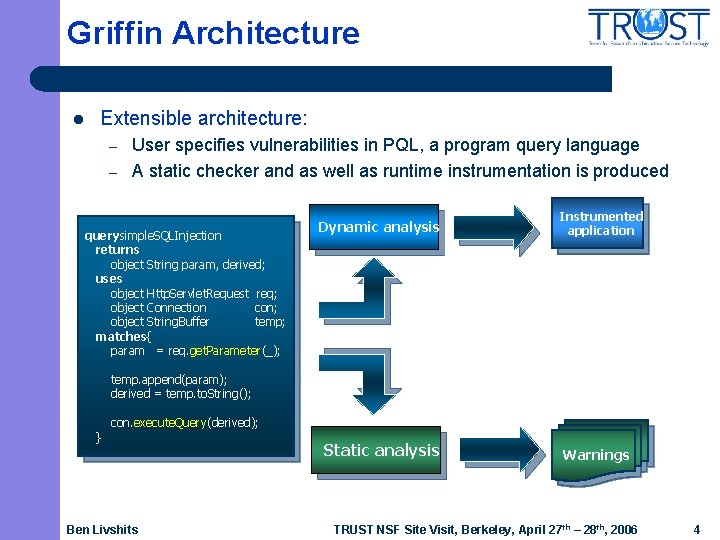
Griffin Architecture l Extensible architecture: – – User specifies vulnerabilities in PQL, a program query language A static checker and as well as runtime instrumentation is produced query simple. SQLInjection returns object String param, derived; uses object Http. Servlet. Request req; object Connection con; object String. Buffer temp; matches{ param = req. get. Parameter(_); Dynamic analysis Instrumented application temp. append(param); derived = temp. to. String(); } con. execute. Query(derived); Ben Livshits Static analysis Warnings TRUST NSF Site Visit, Berkeley, April 27 th – 28 th, 2006 4

Static Error Detection l Advantages – – – l Result summary – – – l Finds vulnerabilities early in development cycle Sounds, so finds all vuln. of a particular type Can run after every build ensuring continuous security Analyzed 9 large open-source Web applications in Java Thousands of users combined 29 vulnerabilities found, most confirmed and fixed Publication – Described in Finding Security Vulnerabilities in Java Applications with Static Analysis, B. Livshits and M. S. Lam, In Proceedings of the Usenix Security Symposium, 2005. Ben Livshits TRUST NSF Site Visit, Berkeley, April 27 th – 28 th, 2006 5

Runtime Prevention & Recovery l Advantages – – l Result summary: – – l Prevents vulnerabilities from doing harm Safe mode for Web application execution Quarantines suspicious actions, application continues to run Perfect runtime information means no false positives Detected and prevented exploits in all our experiments Unoptimized overhead: 57% average Optimized overhead: 14% average Static privation removes 82 -99% of instr. points Publication – Finding Application Errors and Security Flaws Using PQL: a Program Query Language, M. Martin, B. Livshits, and M. S. Lam, Presented in OOPSLA 2005. Ben Livshits TRUST NSF Site Visit, Berkeley, April 27 th – 28 th, 2006 6