Goals of Cryptography Confidentiality Data integrity Authentication Nonrepudiation






- Slides: 15

Goals of Cryptography • • Confidentiality Data integrity Authentication Non-repudiation

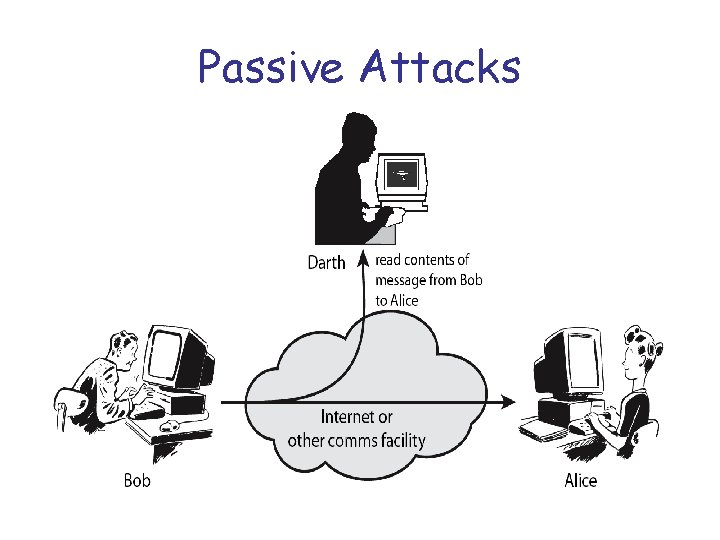
Classify Security Attacks as • passive attacks - eavesdropping on, or monitoring of, transmissions to: – obtain message contents, or – monitor traffic flows

Passive Attacks

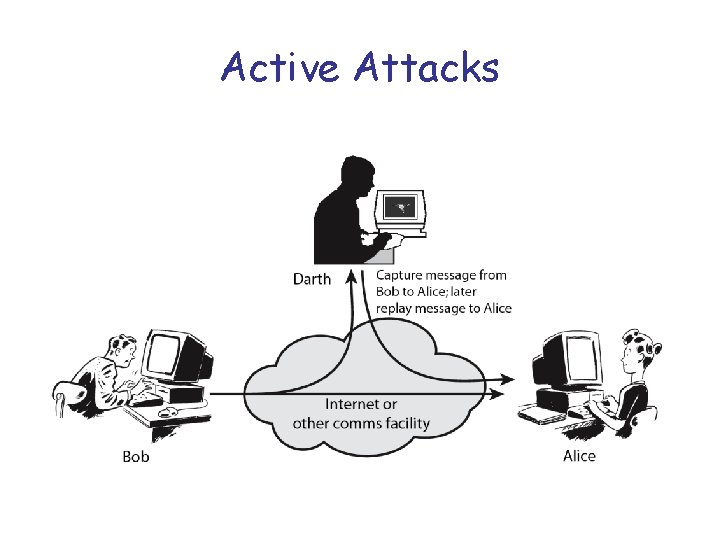
Active attacks • active attacks – modification of data stream to: – – masquerade of one entity as some other replay previous messages modify messages in transit denial of service

Active Attacks

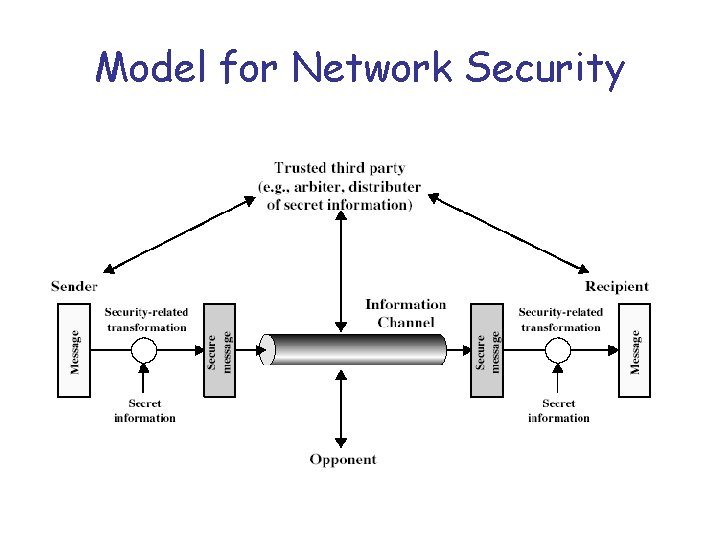
Model for Network Security

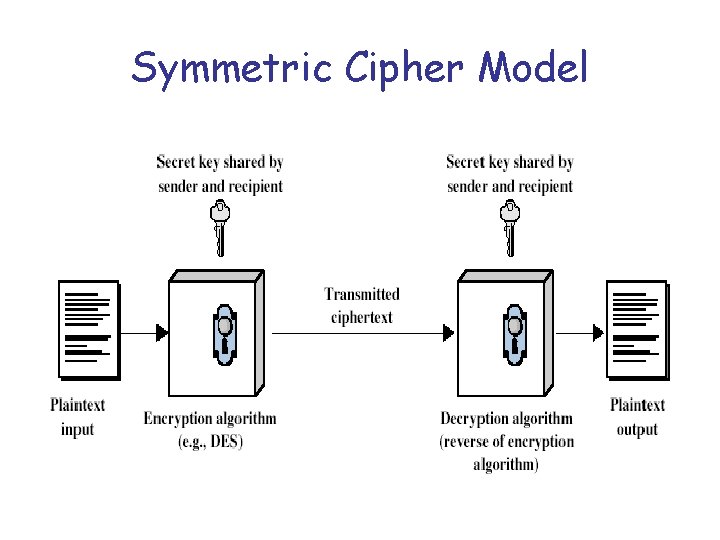
Symmetric Cipher Model

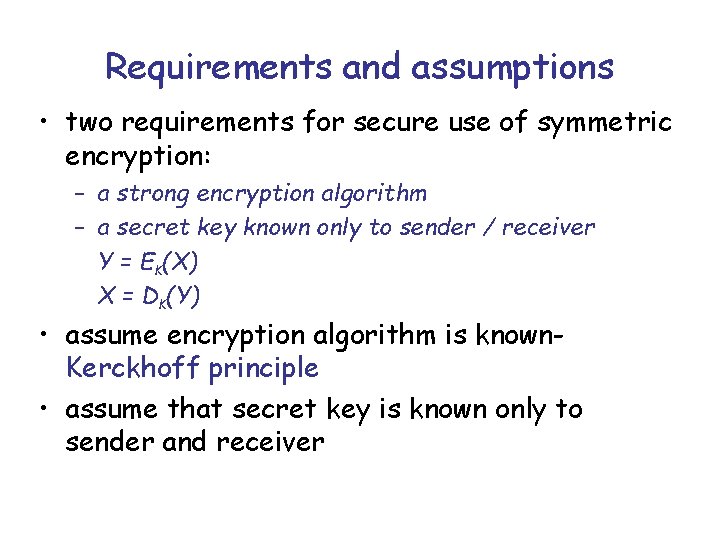
Requirements and assumptions • two requirements for secure use of symmetric encryption: – a strong encryption algorithm – a secret key known only to sender / receiver Y = EK(X) X = DK(Y) • assume encryption algorithm is known. Kerckhoff principle • assume that secret key is known only to sender and receiver

Private-Key Cryptography • Up to know we considered a traditional private/secret/single key cryptography when the same key is shared by both sender and receiver • If this key is disclosed communications are compromised • It is called also symmetric since parties are equal in the sense that they share the same key hence does not protect sender from receiver forging a message & claiming is sent by sender

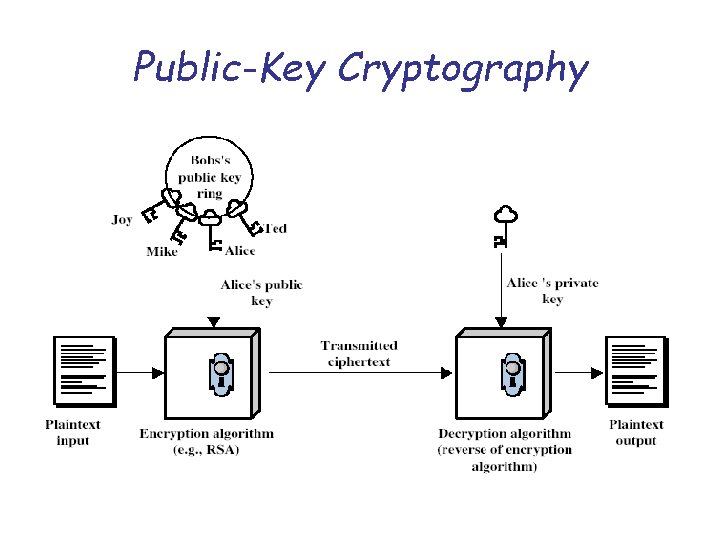
Public-Key Cryptography • public-key/two-key/asymmetric cryptography involves the use of two keys: – a public-key, which may be known by anybody, and can be used to encrypt messages, and verify signatures – a private-key, known only to the recipient, used to decrypt messages, and sign (create) signatures • is asymmetric because – those who encrypt messages or verify signatures cannot decrypt messages or create signatures

Public-Key Cryptography

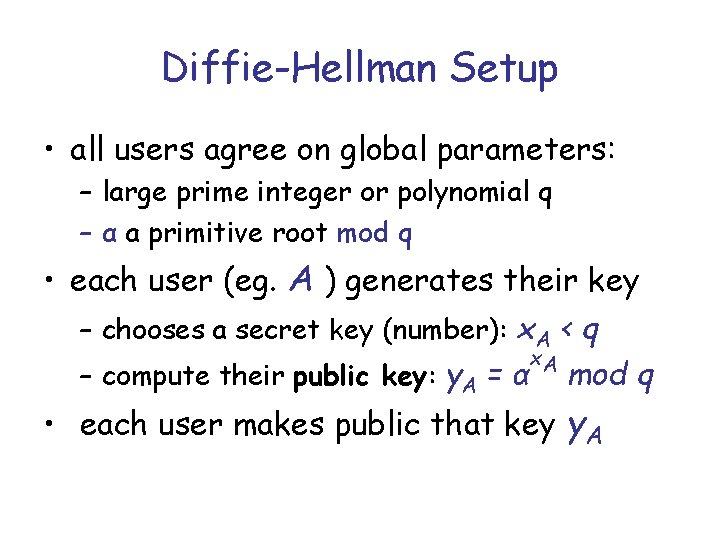
Diffie-Hellman Setup • all users agree on global parameters: – large prime integer or polynomial q – α a primitive root mod q • each user (eg. A ) generates their key – chooses a secret key (number): x. A < q x. A – compute their public key: y. A = α mod q • each user makes public that key y. A


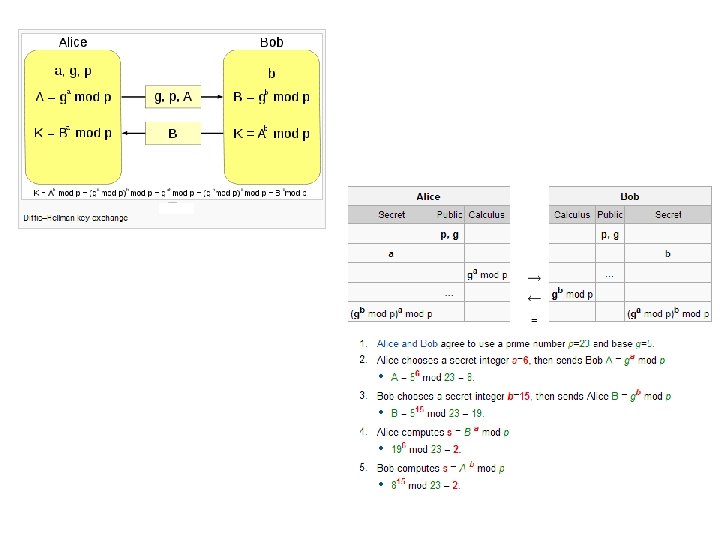
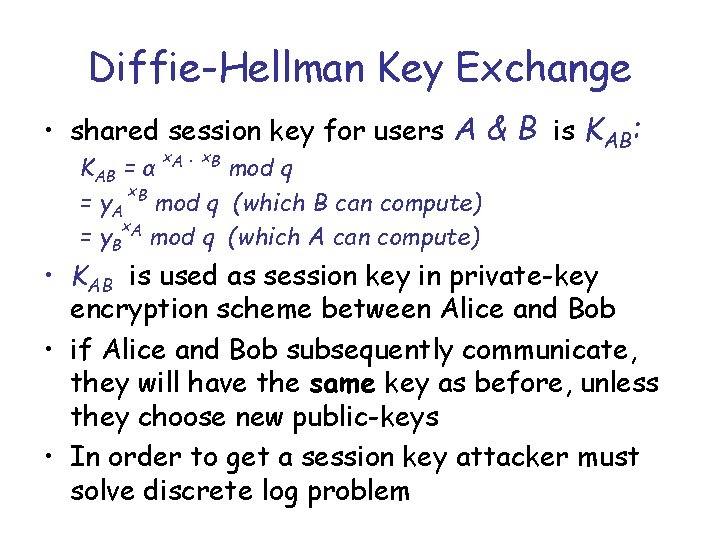
Diffie-Hellman Key Exchange • shared session key for users A & B is KAB: x. A ∙ x. B KAB = α mod q x = y. A B mod q (which B can compute) x. A = y. B mod q (which A can compute) • KAB is used as session key in private-key encryption scheme between Alice and Bob • if Alice and Bob subsequently communicate, they will have the same key as before, unless they choose new public-keys • In order to get a session key attacker must solve discrete log problem

Diffie-Hellman Example • users Alice & Bob who wish to swap keys: • agree on prime q=353 and α=3 • select random secret keys: – A chooses x. A=97, B chooses x. B=233 • compute public keys: 97 – y. A = 3 mod 353 = 40 233 – y. B = 3 mod 353 = 248 (Alice) (Bob) • compute shared session key as: x. A 97 KAB= y. B mod 353 = 248 = 160 x. B 233 KAB= y. A mod 353 = 40 = 160 (Alice) (Bob)