Ethernet Neil Tang 9172008 CS 440 Computer Networks


- Slides: 13

Ethernet Neil Tang 9/17/2008 CS 440 Computer Networks 1

Outline Ø Major Concern for MAC Design Ø Basic Architecture Ø Physical Properties Ø MAC Protocol Ø Strengths and Weaknesses CS 440 Computer Networks 2

Major Concerns for MAC Design Ø Throughput Ø Fairness CS 440 Computer Networks 3

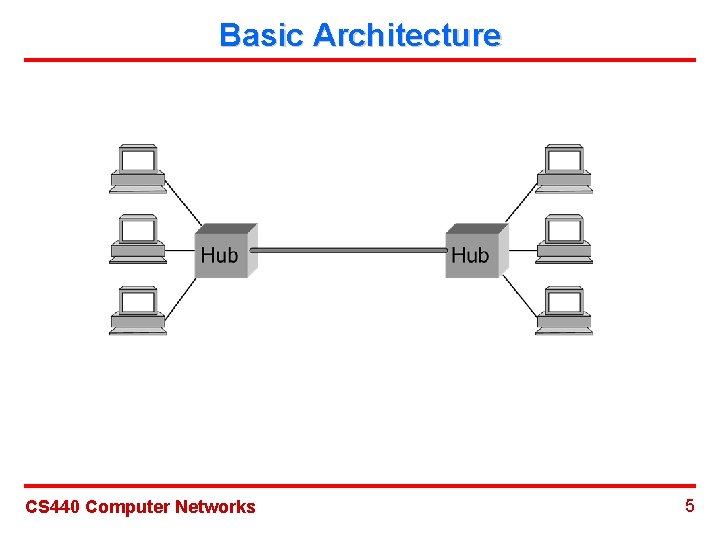
Ethernet (802. 3) Ø Basic Architecture: multiple hosts share a physical medium. Ø MAC Protocol: CSMA/CD CS 440 Computer Networks 4

Basic Architecture CS 440 Computer Networks 5

Physical Properties Ø Ø Ø Ø Broadcast: Any signal placed on Ethernet is broadcast. Encoding: Manchester Error Detection: CRC Physical Distance: 2500 m Number of Hosts: 1024 Data Rate: 10 Mbps/100 Mbps, 1 Gbps Cables: 10 Base 2(200 m), 10 Base 5(500 m), 10 Base. T(100 m) CS 440 Computer Networks 6

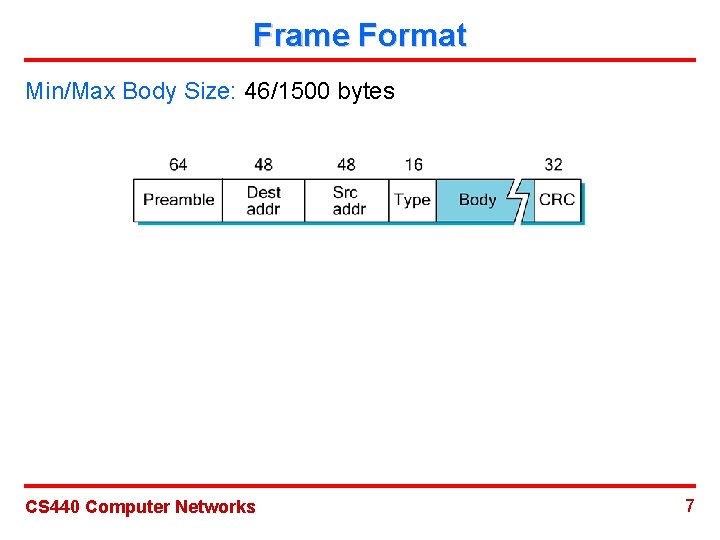
Frame Format Min/Max Body Size: 46/1500 bytes CS 440 Computer Networks 7

Addressing Ø 48 -bit Address: e. g. , 08: 00: 2 b: e 4: b 1: 02 Ø The address is burned to the ROM of each adaptor. Every adaptor has a world-wide unique address. Ø Each manufacturer is allocated a different prefix. CS 440 Computer Networks 8

MAC Algorithm In the receiver The receiver in an adaptor receives all frames but only accepts: Ø frames addressed to its own address Ø frames addressed to the broadcast address (FF: FF: FF: FF) Ø Frames addressed to a multicast address (e. g. , 01: 00: 5 E: 80: 00 01: 00: 5 E: FF: FF (reserved by IANA)), if it is in that multicast group Ø All frames, if it is placed in promiscuous mode. CS 440 Computer Networks 9

MAC Algorithm In the transmitter Ø If it has data to send and the line is busy, it waits for the line to go idle and transmit immediately. Ø At the moment it detects collision, it transmits a 32 -bit jamming sequence and stops transmission. Ø It waits a “certain” amount of time and tries again. It uses binary exponential backoff, delay k 51. 2μs , where k=0… 2 n-1(random selection). CS 440 Computer Networks 10

MAC Algorithm 1 -persistent Vs. p-persistent 1 -persistent protocol (Ethernet): It transmits once the medium is idle p-persistent protocol (Aloha): It transmits with probability p and defers until next empty time with probability q=1 -p. Make the same decision next time. CS 440 Computer Networks 11

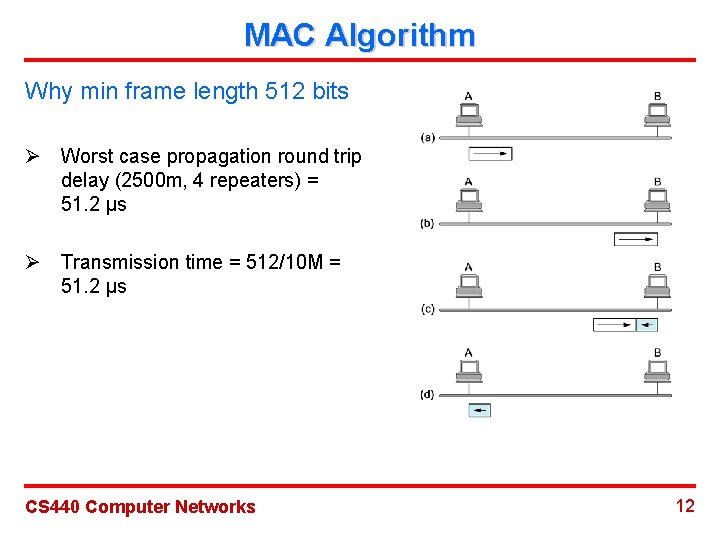
MAC Algorithm Why min frame length 512 bits Ø Worst case propagation round trip delay (2500 m, 4 repeaters) = 51. 2 μs Ø Transmission time = 512/10 M = 51. 2 μs CS 440 Computer Networks 12

Strength and Weakness Strength: Ø Simple: No routing, no switching and very simple MAC protocol. Ø Low Cost: Cheap cables and cheap equipments Weakness: Ø Inefficient in Throughput: Under heavy traffic condition, collisions happen frequently. CS 440 Computer Networks 13