Token Ring Neil Tang 9222008 CS 440 Computer
- Slides: 13

Token Ring Neil Tang 9/22/2008 CS 440 Computer Networks 1

Outline Ø Basic Architecture Ø Physical Properties Ø MAC Protocol CS 440 Computer Networks 2

Token Ring Ø Basic architecture: multiple hosts share a ring. Ø MAC protocol: token passing CS 440 Computer Networks 3

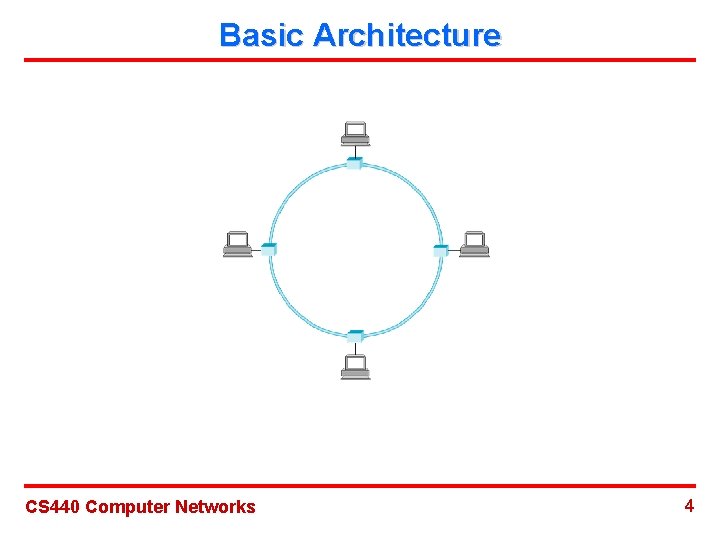
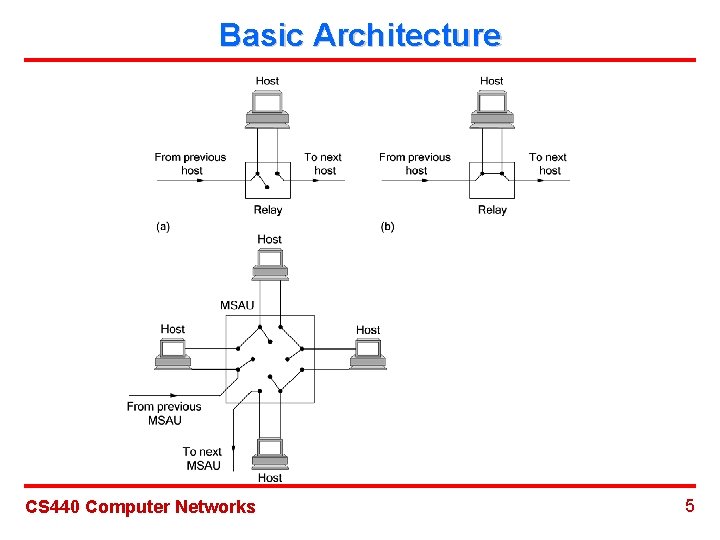
Basic Architecture CS 440 Computer Networks 4

Basic Architecture CS 440 Computer Networks 5

Physical Properties Ø Data flow: It goes along a particular direction around the ring, with each node receiving frames from its upstream neighbor and then forwarding them to its downstream neighbor. Ø Encoding: Manchester Ø Error detection: CRC Ø Max number of hosts: 250 Ø Data rate: 4 Mbps/16 Mbps Ø Cables: Twisted pair cable CS 440 Computer Networks 6

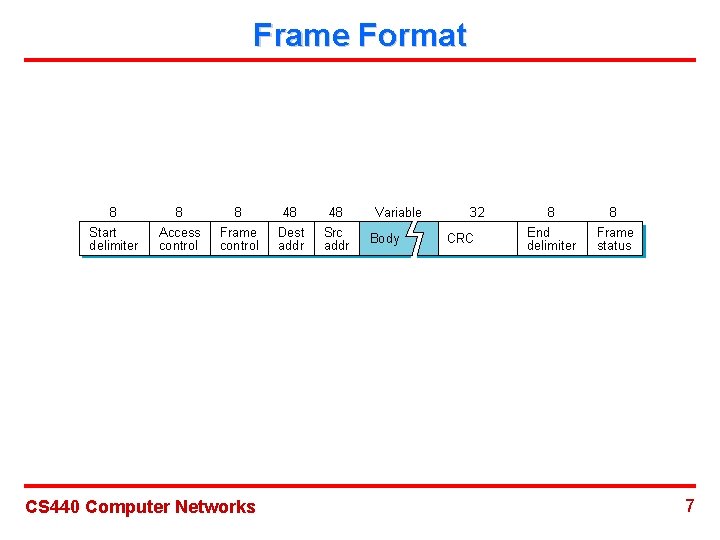
Frame Format 8 8 8 48 48 Start delimiter Access control Frame control Dest addr Src addr CS 440 Computer Networks Variable Body 32 CRC 8 8 End delimiter Frame status 7

MAC Algorithm Basic Idea: Token Passing Ø A token (a special bit sequence) circulates around the ring. Ø Every node forwards it. Ø A node with data to send takes the token off the ring and inserts its frame into the ring. Ø Each node along the way forwards the frame. Ø The destination node save a copy and continue to forward it. Ø The sender removes the frame when it gets back. CS 440 Computer Networks 8

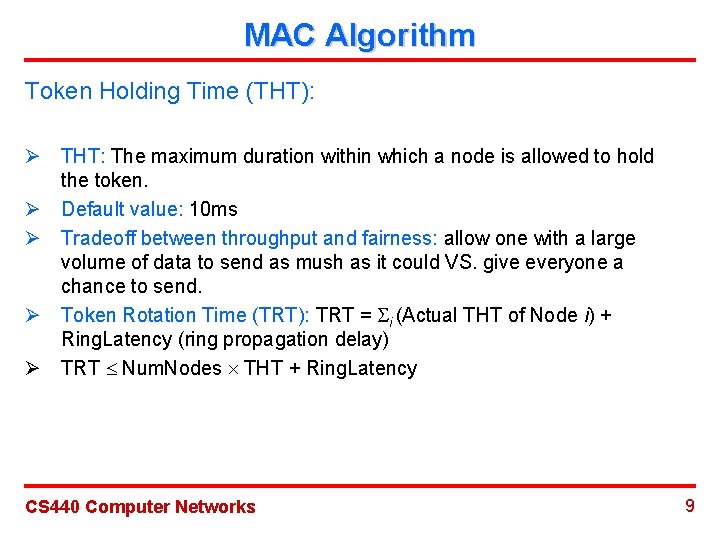
MAC Algorithm Token Holding Time (THT): Ø THT: The maximum duration within which a node is allowed to hold the token. Ø Default value: 10 ms Ø Tradeoff between throughput and fairness: allow one with a large volume of data to send as mush as it could VS. give everyone a chance to send. Ø Token Rotation Time (TRT): TRT = i (Actual THT of Node i) + Ring. Latency (ring propagation delay) Ø TRT Num. Nodes THT + Ring. Latency CS 440 Computer Networks 9

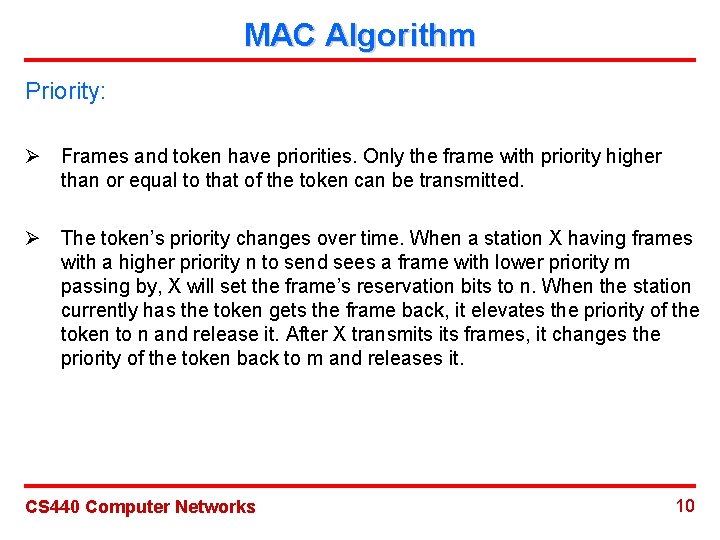
MAC Algorithm Priority: Ø Frames and token have priorities. Only the frame with priority higher than or equal to that of the token can be transmitted. Ø The token’s priority changes over time. When a station X having frames with a higher priority n to send sees a frame with lower priority m passing by, X will set the frame’s reservation bits to n. When the station currently has the token gets the frame back, it elevates the priority of the token to n and release it. After X transmits frames, it changes the priority of the token back to m and releases it. CS 440 Computer Networks 10

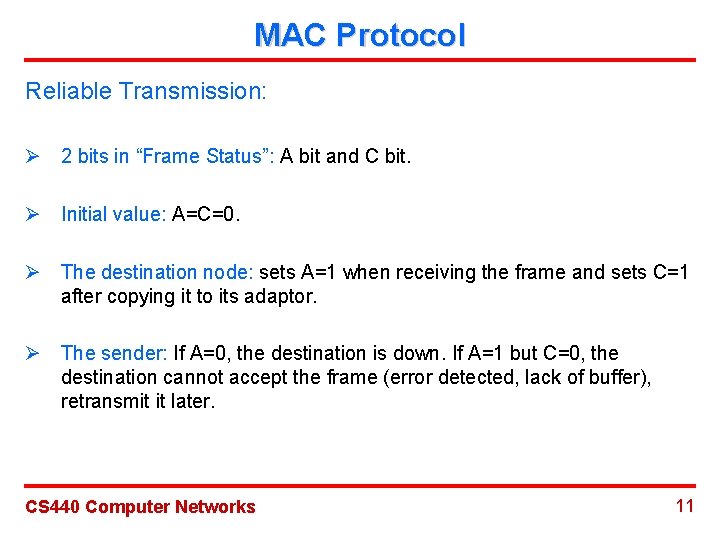
MAC Protocol Reliable Transmission: Ø 2 bits in “Frame Status”: A bit and C bit. Ø Initial value: A=C=0. Ø The destination node: sets A=1 when receiving the frame and sets C=1 after copying it to its adaptor. Ø The sender: If A=0, the destination is down. If A=1 but C=0, the destination cannot accept the frame (error detected, lack of buffer), retransmit it later. CS 440 Computer Networks 11

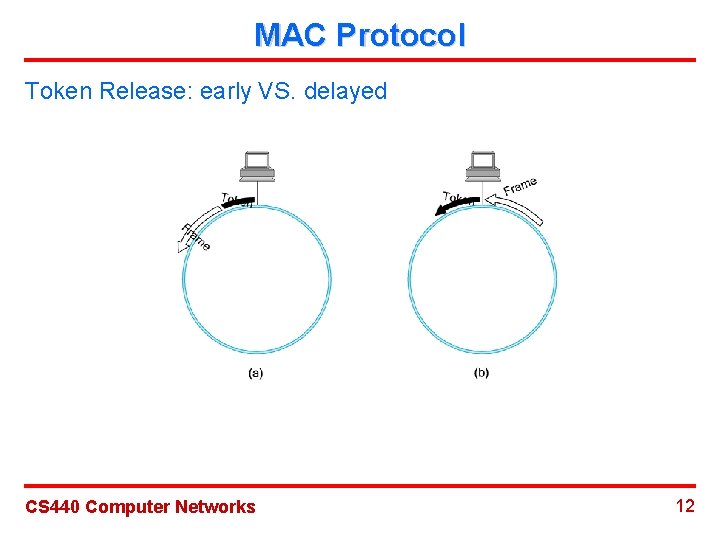
MAC Protocol Token Release: early VS. delayed CS 440 Computer Networks 12

Maintenance A Monitor Station Ø Monitor the token: After a period of (Num. Sation THT+Ring. Latency), if no token comes back, it creates a new token. Ø Monitor the corrupted or orphan (dead sender) frames: It sets “monitor” bit to 1 at the first time the frame passes and get rid of it at the second time. Ø A monitor station will periodically announce its presence by a special control frame. If a station fails to see it for a certain period of time, it transmits a “claim token” frame to announce its intent to become a new monitor. Tie can be broken by “highest address wins” rule if multiple stations compete for this at the same time. CS 440 Computer Networks 13