Detecting DGA malware using Net Flow Author Martin


- Slides: 10

Detecting DGA malware using Net. Flow Author: Martin Grill, Ivan Nikolaev, Veronica Valeros, Martin Rehak Publisher/Conference: 2015 IFIP/IEEE International Symposium on Integrated Network Management (IM) Referenced: 25 Presenter: Yu-Hsiang Lin Date: 2019/01/30 Department of Computer Science and Information Engineering National Cheng Kung University, Taiwan R. O. C.

INTRODUCTION l l Whenever the botmaster wants to send a command to his botnet, he needs to register a new domain that he generated using his own copy of DGA with the same seed as the botnet just before the botnet will try to contact it. Botmasters are trying to expose their C&C servers for the minimum amount of time. Domains are registered and DNS configurations are made just a few minutes before the infected bot is supposed to query the domain, and the C&C servers are shut down and removed immediately afterwards. In this paper we present a new privacy-preserving technique to detect hosts infected by DGA-malware in a large scale networks using only Net. Flow information without reverse engineering a binary or performing Non-Existent Domain (NXDomain) inspection. National Cheng Kung University CSIE Computer & Internet Architecture Lab 2

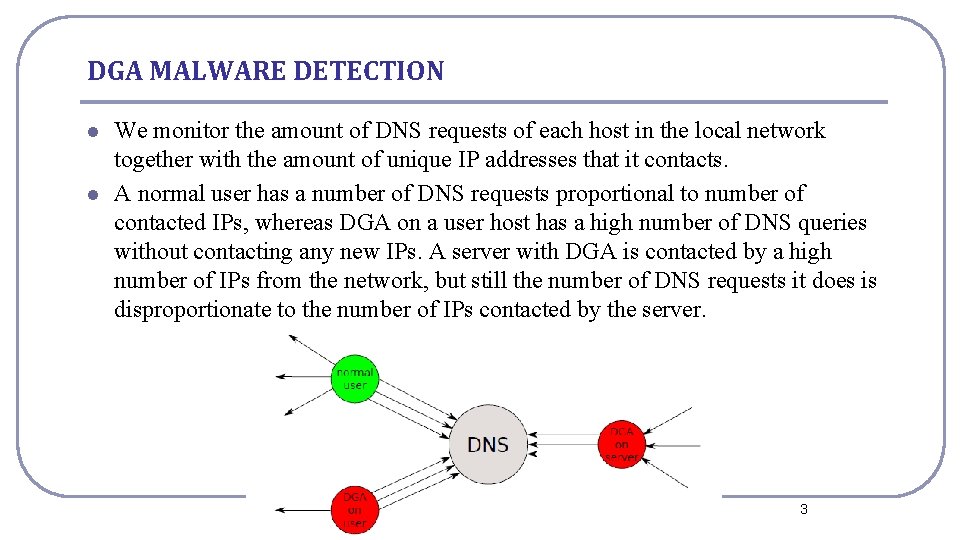
DGA MALWARE DETECTION l l We monitor the amount of DNS requests of each host in the local network together with the amount of unique IP addresses that it contacts. A normal user has a number of DNS requests proportional to number of contacted IPs, whereas DGA on a user host has a high number of DNS queries without contacting any new IPs. A server with DGA is contacted by a high number of IPs from the network, but still the number of DNS requests it does is disproportionate to the number of IPs contacted by the server. National Cheng Kung University CSIE Computer & Internet Architecture Lab 3

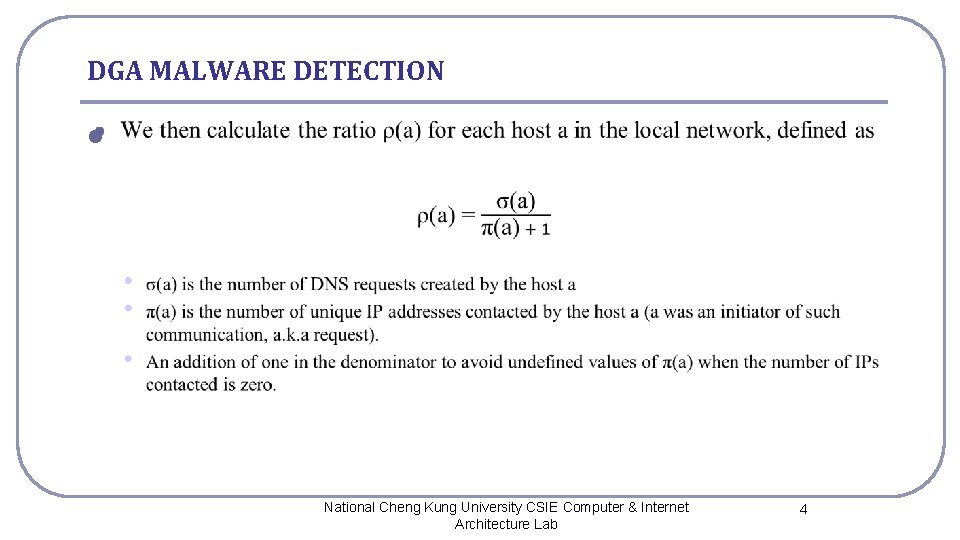
DGA MALWARE DETECTION l National Cheng Kung University CSIE Computer & Internet Architecture Lab 4

Request-response identification l l l In order to be able to correctly calculate the amount of IP addresses that the host contacts and differentiate them from IP addresses that the host is contacted by. Identification with timestamp: Due to the time synchronization problem during Net. Flow probes on the Internet, it’s unreliable. Proposed an algorithm based on the median of number of peers difference. National Cheng Kung University CSIE Computer & Internet Architecture Lab 5

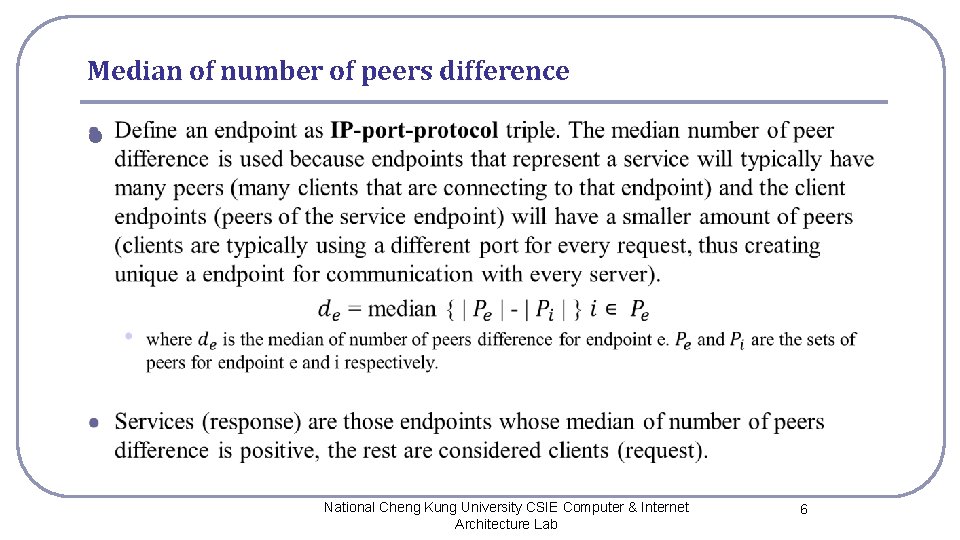
Median of number of peers difference l National Cheng Kung University CSIE Computer & Internet Architecture Lab 6

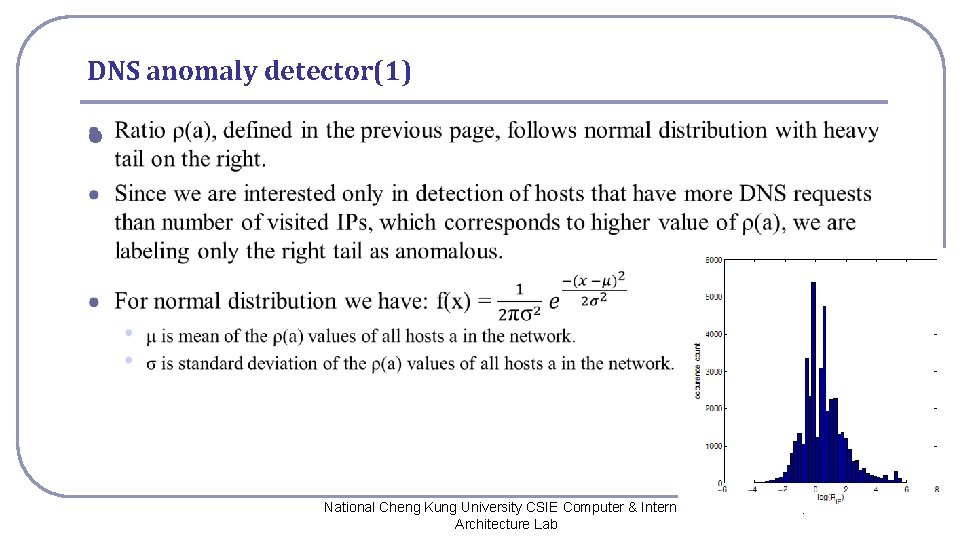
DNS anomaly detector(1) l National Cheng Kung University CSIE Computer & Internet Architecture Lab 7

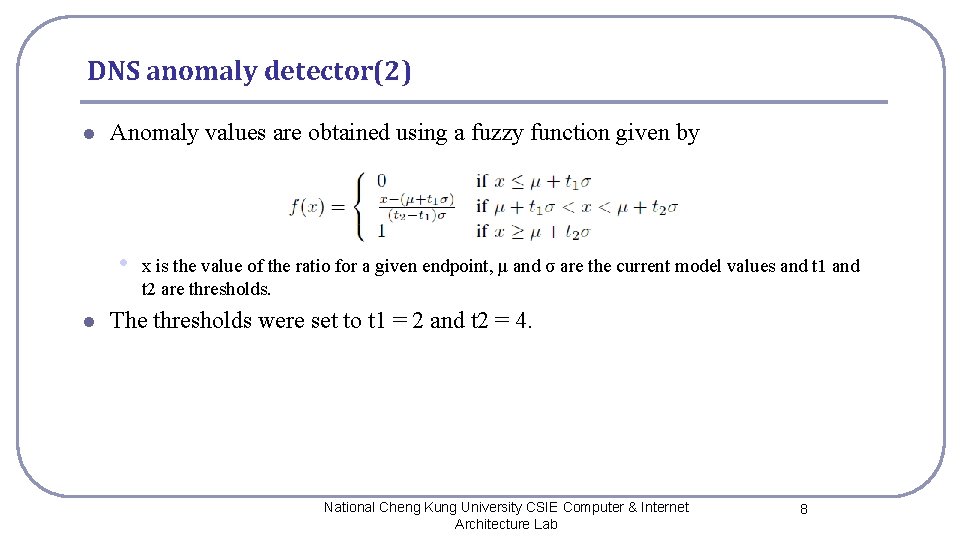
DNS anomaly detector(2) l Anomaly values are obtained using a fuzzy function given by • l x is the value of the ratio for a given endpoint, μ and σ are the current model values and t 1 and t 2 are thresholds. The thresholds were set to t 1 = 2 and t 2 = 4. National Cheng Kung University CSIE Computer & Internet Architecture Lab 8

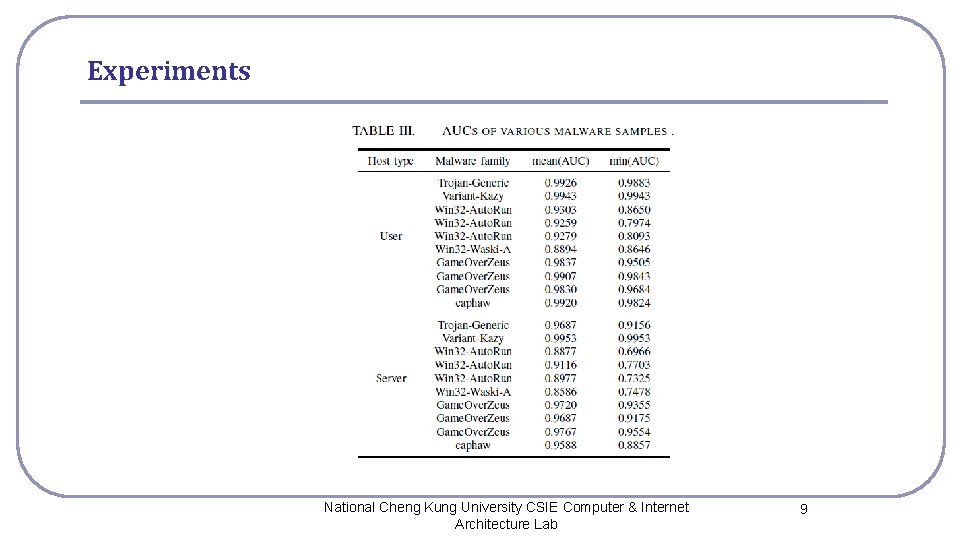
Experiments National Cheng Kung University CSIE Computer & Internet Architecture Lab 9

National Cheng Kung University CSIE Computer & Internet Architecture Lab 10