Computer Engineering Department Islamic University of Gaza ECOM











- Slides: 22

Computer Engineering Department Islamic University of Gaza ECOM 5347 Network Security Undergraduate Course Fall 2013 Prof. Mohammad A. Mikki Room I 215 Tel. Ext. 2876 email: mmikki@iugaza. edu. ps Skype id: mohammad. mikki Homepage: http: //site. iugaza. edu. ps/mmikki/ 1

Lecture 1 Syllabus

Instructor Mohammad A. Mikki Professor of Computer Engineering ECE Department , Faculty of Engineering 3

Where to find me q. My Office: q. Office Hours: q. My Email: q My homepage: q Skype id: q Tel. : q Fax: IT bldg: Room I 215 TBA and by appointment mmikki@iugaza. edu. ps http: //site. iugaza. edu. ps/mmikki/ mohammad. mikki +970 -8 -2860700 Ext. 2876 +970 -8 -2860800 4

TA • Eng. Jihad El-Dahdouh 5

Course Information q Course Code: ECOM 5347 q Course Name: Network Security (Undergraduate Course) q Number of credits: 3 6

Course Description q Principles of practical computer security to enable students to defend themselves against malicious threats. Firewalls, antivirus, secure setup of a wireless access point. Cryptography basics and its application. Embedded devices and related security issues. Network technologies and their vulnerabilities. 7

Course Objectives • All students, and most of the general population, use computers and computer-based systems everyday, and entrust those systems with lifecritical and cost-critical functions. • In spite of the high level of trust placed in computer-based systems, even advanced computer users have little awareness of their exposure to security threats. • The general lack of understanding of basic computer security concepts leads to increased risk and costs involved in using computers. • This course will introduce computer security basics in a practical way and give students the understanding that they need to protect themselves, and their data, from malicious attack. Students will learn about the mechanisms behind most computer attacks and they will learn about standard defense tools including firewalls and anti-virus programs. • The course will provide a practical introduction to a broad range of computer security topics. 8

Course Outcomes At completion of the course students should be able to: q Explain common security threats, including malware. q Analyze security vulnerabilities in computer systems. q Apply authentication and cryptography to secure computer systems. q Use open source tools to improve system security. q Understand the fundamentals of network security. q Describe the processes of auditing and incident response. q Understand ethical and legal considerations encountered when working in information security. 9

Course Website http: //moodle. iugaza. edu. ps q please check this webpage at least once a week for lecture notes, homework assignments, solutions, useful links, supplementary material, announcements 10

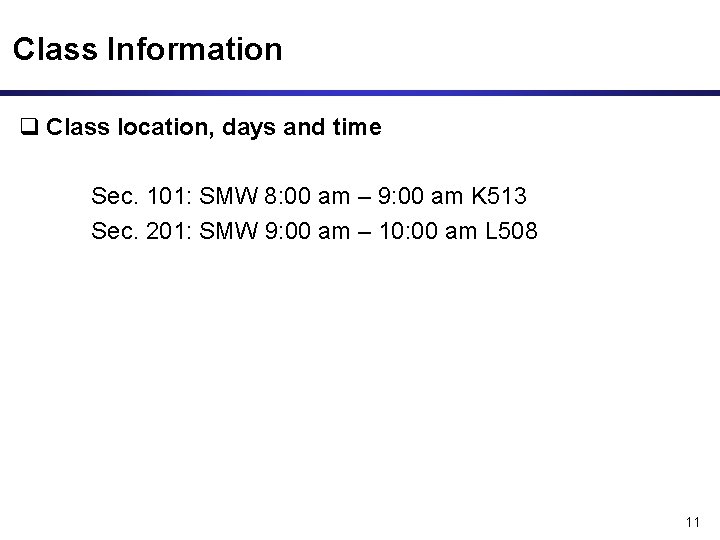
Class Information q Class location, days and time Sec. 101: SMW 8: 00 am – 9: 00 am K 513 Sec. 201: SMW 9: 00 am – 10: 00 am L 508 11

Required Textbook and Material Michael T. Goodrich and Roberto Tamassia, Introduction to Computer Security, Addison. Wesley, 1 edition (October 25, 2010) ISBN-10: 0321512944 ISBN-13: 978 -0321512949 12

Required Textbook (TOC) Table of Content 13

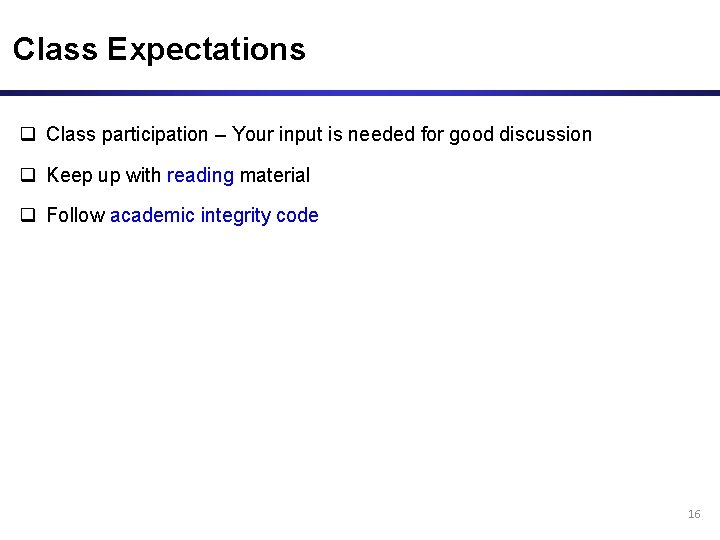
Class Expectations q Class participation – Your input is needed for good discussion q Keep up with reading material q Follow academic integrity code 16

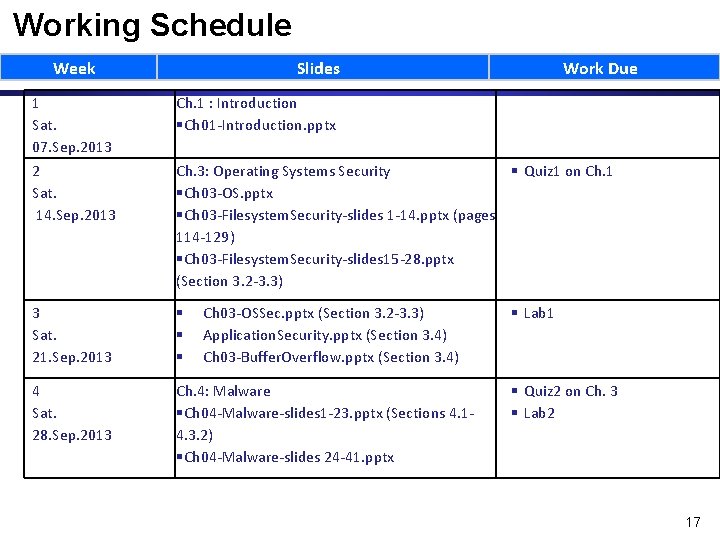
Working Schedule Week Slides 1 Sat. 07. Sep. 2013 2 Sat. 14. Sep. 2013 Ch. 1 : Introduction Ch 01 -Introduction. pptx 3 Sat. 21. Sep. 2013 4 Sat. 28. Sep. 2013 Ch. 4: Malware Ch 04 -Malware-slides 1 -23. pptx (Sections 4. 14. 3. 2) Ch 04 -Malware-slides 24 -41. pptx Work Due Ch. 3: Operating Systems Security Quiz 1 on Ch. 1 Ch 03 -OS. pptx Ch 03 -Filesystem. Security-slides 1 -14. pptx (pages 114 -129) Ch 03 -Filesystem. Security-slides 15 -28. pptx (Section 3. 2 -3. 3) Ch 03 -OSSec. pptx (Section 3. 2 -3. 3) Application. Security. pptx (Section 3. 4) Ch 03 -Buffer. Overflow. pptx (Section 3. 4) Lab 1 Quiz 2 on Ch. 3 Lab 2 17

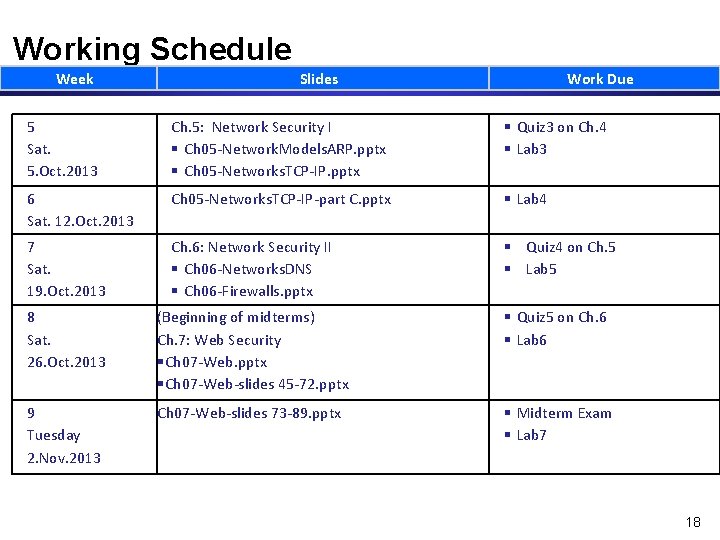
Working Schedule Week Slides Work Due 5 Sat. 5. Oct. 2013 Ch. 5: Network Security I Ch 05 -Network. Models. ARP. pptx Ch 05 -Networks. TCP-IP. pptx Quiz 3 on Ch. 4 Lab 3 6 Sat. 12. Oct. 2013 Ch 05 -Networks. TCP-IP-part C. pptx Lab 4 7 Sat. 19. Oct. 2013 Ch. 6: Network Security II Ch 06 -Networks. DNS Ch 06 -Firewalls. pptx Quiz 4 on Ch. 5 Lab 5 8 Sat. 26. Oct. 2013 (Beginning of midterms) Ch. 7: Web Security Ch 07 -Web. pptx Ch 07 -Web-slides 45 -72. pptx Quiz 5 on Ch. 6 Lab 6 9 Tuesday 2. Nov. 2013 Ch 07 -Web-slides 73 -89. pptx Midterm Exam Lab 7 18

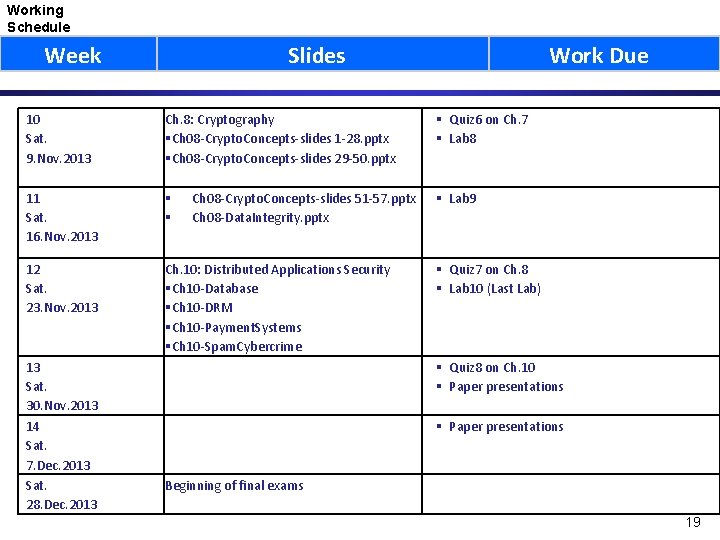
Working Schedule Week Slides 10 Sat. 9. Nov. 2013 Ch. 8: Cryptography Ch 08 -Crypto. Concepts-slides 1 -28. pptx Ch 08 -Crypto. Concepts-slides 29 -50. pptx 11 Sat. 16. Nov. 2013 12 Sat. 23. Nov. 2013 Ch. 10: Distributed Applications Security Ch 10 -Database Ch 10 -DRM Ch 10 -Payment. Systems Ch 10 -Spam. Cybercrime 13 Sat. 30. Nov. 2013 14 Sat. 7. Dec. 2013 Sat. 28. Dec. 2013 Ch 08 -Crypto. Concepts-slides 51 -57. pptx Ch 08 -Data. Integrity. pptx Work Due Quiz 6 on Ch. 7 Lab 8 Lab 9 Quiz 7 on Ch. 8 Lab 10 (Last Lab) Quiz 8 on Ch. 10 Paper presentations Beginning of final exams 19

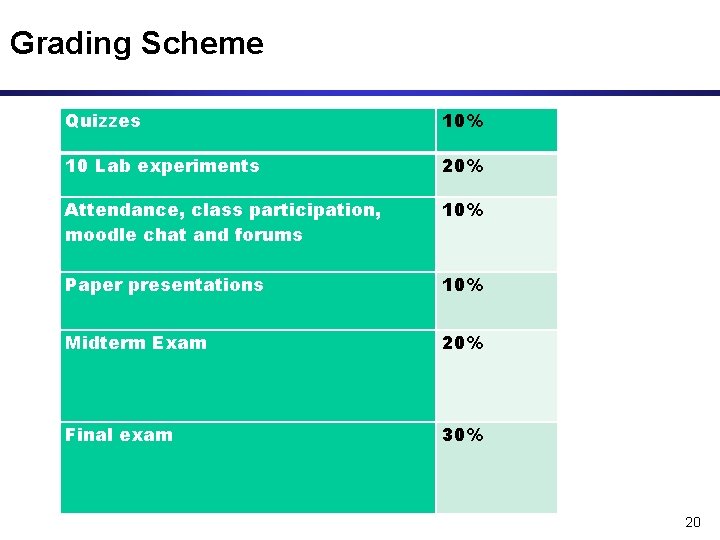
Grading Scheme Quizzes 10% 10 Lab experiments 20% Attendance, class participation, moodle chat and forums 10% Paper presentations 10% Midterm Exam 20% Final exam 30% 20

Research Report (Not required for the undergraduate students) • • • Select a research topic in network security Select 3 -5 recent papers on the topic Summarize these papers in a 10 -15 page report Submit an intermediate report by 8 th week of the semester Submit a final report by 13 th week of the semester Make a 15 minutes presentation in front of the class in weeks 14 and 15 21

Quizzes 8 quizzes Quizzes are given after completion of each textbook chapter. 22

Lab There will be a total of 10 laboratory experiments that will cover the current tools used in computer and network security. The TA will assist in conducting these exps 23

any questions 24
 Vuongxuan.ecom
Vuongxuan.ecom Falco-ecom
Falco-ecom Lser connect ecom
Lser connect ecom Hw ecom
Hw ecom Ecommerce enablers
Ecommerce enablers Bil soruyu bas gaza
Bil soruyu bas gaza Pakimires
Pakimires Bil soruyu bas gaza
Bil soruyu bas gaza Gaza strip map
Gaza strip map Gaza strip map
Gaza strip map Mapa franja de gaza
Mapa franja de gaza Mapa palestina
Mapa palestina Gaza central desalination plant
Gaza central desalination plant Dzsenin
Dzsenin Department of information engineering university of padova
Department of information engineering university of padova Department of information engineering university of padova
Department of information engineering university of padova University of sargodha engineering department
University of sargodha engineering department Tum department of electrical and computer engineering
Tum department of electrical and computer engineering Computer engineering department
Computer engineering department Webnis
Webnis Islamic online university malaysia
Islamic online university malaysia Islamic university college
Islamic university college System procurement process in software engineering
System procurement process in software engineering











































