Asynchronous Cryptology Implementations and Applications Tim Ransom ransomtsemail



- Slides: 8

Asynchronous Cryptology: Implementations and Applications Tim Ransom ransomts@email. appstate. edu James Corsi corsijn@email. appstate. edu Summer Bridge 2013 August 2, 2013

Overview What is Cryptology? Symmetric vs. Asymmetric Public vs. Private Keys What makes them secure? Acknowledgements

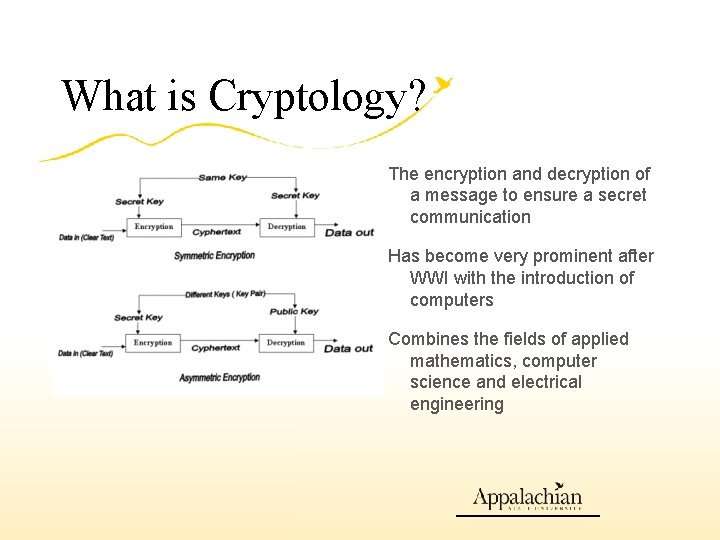
What is Cryptology? The encryption and decryption of a message to ensure a secret communication Has become very prominent after WWI with the introduction of computers Combines the fields of applied mathematics, computer science and electrical engineering

Symmetric vs. Asymmetric Symmetric Advantages: Public Key Advantages: Higher rates of throughput Same keys can be used for long periods of time Keys are relatively short Public keys reduce the total number of keys needed, making management much simpler Simple symmetric keys can be composed to create a stronger cipher Only the private key must be kept secret Symmetric Disadvantages: Public Key Disadvantages: For two parties, both keys must be kept secret Throughput speeds can be very slow Digital signature verifications typically require large keys for public validation No public scheme has been proven secure

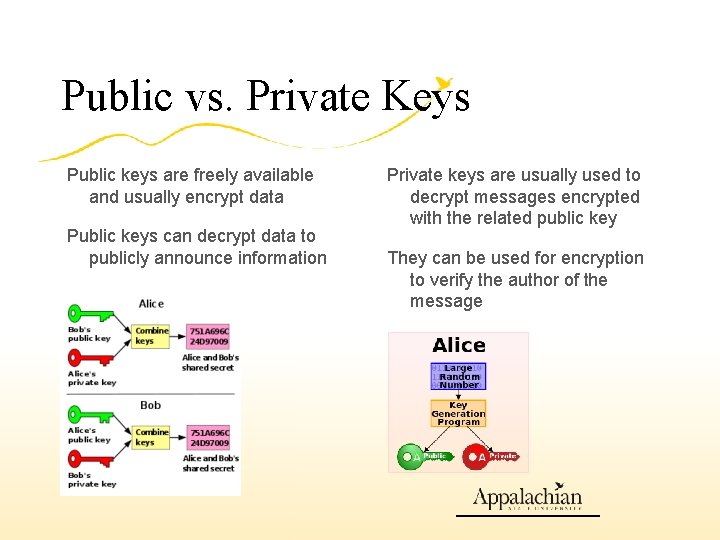
Public vs. Private Keys Public keys are freely available and usually encrypt data Public keys can decrypt data to publicly announce information Private keys are usually used to decrypt messages encrypted with the related public key They can be used for encryption to verify the author of the message

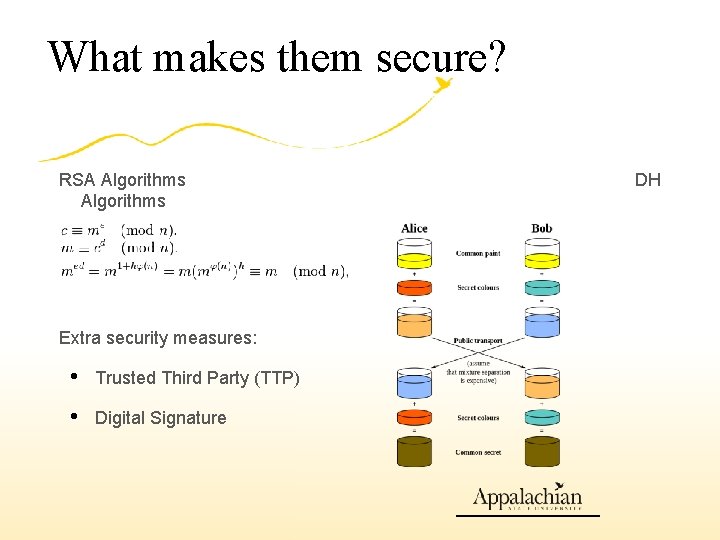
What makes them secure? RSA Algorithms Extra security measures: • Trusted Third Party (TTP) • Digital Signature DH

Acknowledgements Dr. Tashakkori Dr. Norris Appalachian State The National Science Foundation STEP program

References Menezes, Alfred J. , Paul C. van Oorschot, and Scott A. Vanstone. Handbook of Applied Cryptography. Boca Raton: CRC, 1997. Print. Pfleeger, Charles P. , and Shari L. Pfleeger. Security in Computing. 3 rd ed. Upper Saddle River: Prentice Hall, 2003. Print. Pieprzyk, Josef, Thomas Hardjono, and Jennifer Seberry. Fundamentals of Computer Security. New York: Springer-Verlag Berlin Heidelberg, 2003. Print. Garrett, Paul, and Daniel Lieman. Public-key Cryptography: American Mathematical Society Short Course, January 13 -14, 2003, Baltimore, Maryland. Vol. 62. Providence, RI: American Mathematical Society, 2005. Print Abhishek. “Symmetric and Asymmetric Encryption. ” Drawing. Cryptocats. com 27 August 2008. <http: //cryptocrats. com/digital-rights-management/drm-technologies-drm-part-2/> “Public-key-crypto-1” by Kohan. X - CC: BY “Public key shared secret” by David Gothberg - CC: BY “Diffie-Hellman Key Exchange” by Flugaal - CC: BY