www oasisopen org Welcome to OASIS Identity and











- Slides: 18

www. oasis-open. org Welcome to OASIS Identity and Trusted Infrastructure Workshop: Evolutionary Milestones Burton Group Catalyst Conference Europe, Barcelona, October 22, 2007 For information on how to join the OASIS IDtrust Member Section see: http: //www. oasis-idtrust. org/ For more information related to ‘Joining OASIS’ see: http: //www. oasis-open. org/join

www. oasis-open. org OASIS IDtrust and Identity Management Today Abbie Barbir, Ph. D. Nortel, Senior Standards Advisor OASIS IDtrust Steering Committee ITU-T FG Id. M Chairman abbieb@nortel. com

www. oasis-open. org OASIS IDtrust Member Section

www. oasis-open. org OASIS IDtrust Member Section OASIS provides a neutral setting where government agencies, companies, research institutes, and individuals work together to advance the use of trusted infrastructures History PKI Forum migrated to OASIS PKI MS in November 2002 PKI MS transformed into IDtrust MS in 2007 IDtrust expanded its scope to encompass additional standards based identity and trusted infrastructure technologies, policies, and practices Steering Committee Abbie Barbir, Nortel June Leung, Fund. SERV Arshad Noor, Strong. Auth John Sabo, CA, Inc. Ann Terwilliger, Visa International

Strategic Focus Areas Ø Identity and Trusted Infrastructure components Ø Ø Identity and Trust Policies and Enforcement Ø Ø Policies; policy mapping and standardization; assurance; technical validation mechanisms; trust path building and validation Education and Outreach Ø Ø Studies and Projects addressing Identity and Trust models and standards; relevant protocols and standards; trust infrastructures in use; costs, benefits and risk management issues Documenting trust use cases and business case scenarios, best practices and adoption reports and papers; organizing conferences and workshops; and establishing Web-based resources Barriers and Emerging Issues Ø Data privacy issues; interoperability; cross border/ organizational trust; outsourcing; cryptographic issues; application integration; and international issues

IDTrust Summary Current TCs Enterprise Key Management Infrastructure TC PKI Adoption TC Chairs: Arshad Noor, Strong. Auth Chair: Stephen Wilson, Lockstep LLC OASIS Digital Signature Services (DSS) TC Steering Committee developing new work plan for 2007/2008 Many opportunities to get involved We invite you to join OASIS and participate in the IDtrust MS and/or TCs For more information contact Dee Schur: Dee. schur@oasis-open. org

Id. M Today Workshop Drivers Areas of Focus International Mandates and New Identity Management Challenges Emerging approaches to ID Management and Global Collaboration ID Management and Trust Case Studies: Successes and Obstacles

What is Identity is both a “real-world” concept and a digital artifact Digital Identity (“Identity”) refers to “a digital representation of a set of claims made by one party about itself or another data subject” A person may have a number of different identities A digital identity can be a set of identity information (e. g. , an address), as opposed to real-world concept that is tied with a person’s sense of who they are An entity can have a set of digital claims (attributes) including credentials and (public and private) identifiers A Relying party requests from an entity (e. g. , an end-user) a set of claims as a function of context and requested services Source FG IDM Tutorial, September 2007, Geneva

What is Identity Management Identity management (Id. M) is the management of the identity life cycle of entities (subjects or objects) during which: Identity is established, described/defined and destroyed This involves Both technology and process Managing unique IDs, attributes, credentials, entitlements Ability to create manageable lifecycles Scale from internal systems to external applications and processes Goal of IDM is to enable the enforcement of common security policies. Business policies are domain dependent Reduced risk of improper use of systems, devices, privacy or other regulatory violations, redundant security administration Source FG IDM Tutorial, September 2007, Geneva 9

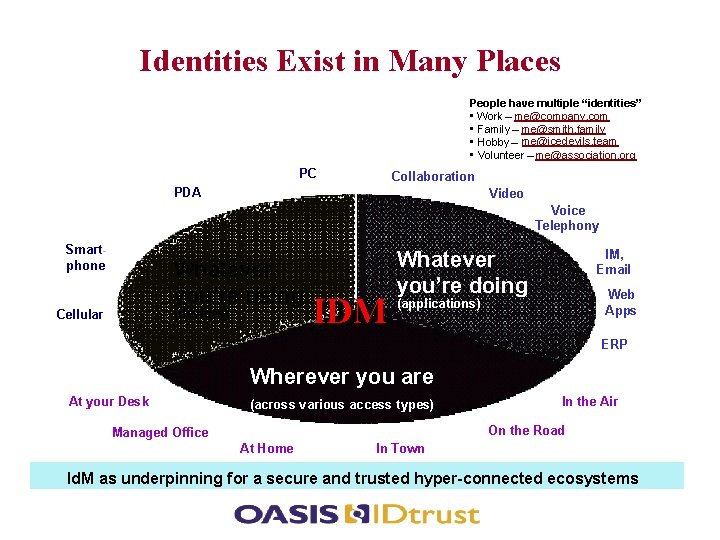
Identities Exist in Many Places People have multiple “identities” • Work – me@company. com • Family – me@smith. family • Hobby – me@icedevils. team • Volunteer – me@association. org PC Collaboration PDA Video Voice Telephony Smartphone Whatever you’re using (devices) Cellular IDM Whatever you’re doing IM, Email Web Apps (applications) ERP Wherever you are At your Desk (across various access types) In the Air On the Road Managed Office At Home In Town Id. M as underpinning for a secure and trusted hyper-connected ecosystems

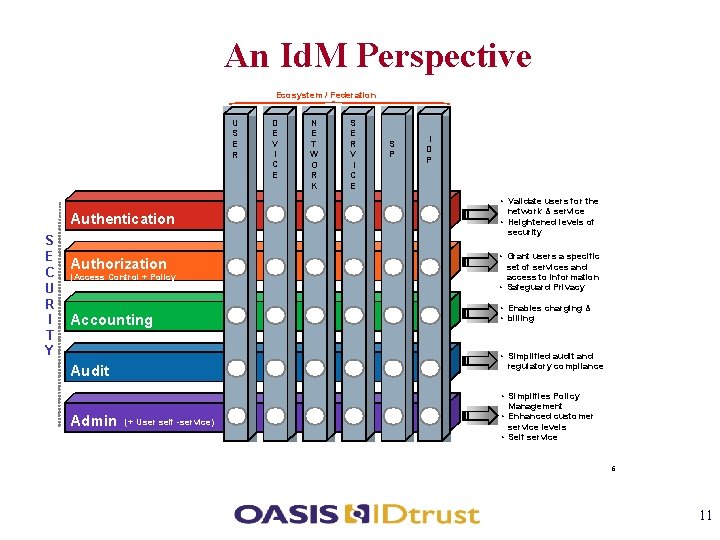
An Id. M Perspective Ecosystem / Federation U S E R Authentication S E C U R I T Y Authorization (Access Control + Policy Accounting N E T W O R K S E R V I C E S P I D P • Validate users for the network & service • Heightened levels of security • Grant users a specific set of services and access to information • Safeguard Privacy • Enables charging & • billing • Simplified audit and regulatory compliance Audit Admin D E V I C E (+ User self -service) • Simplifies Policy Management • Enhanced customer service levels • Self service 6 11

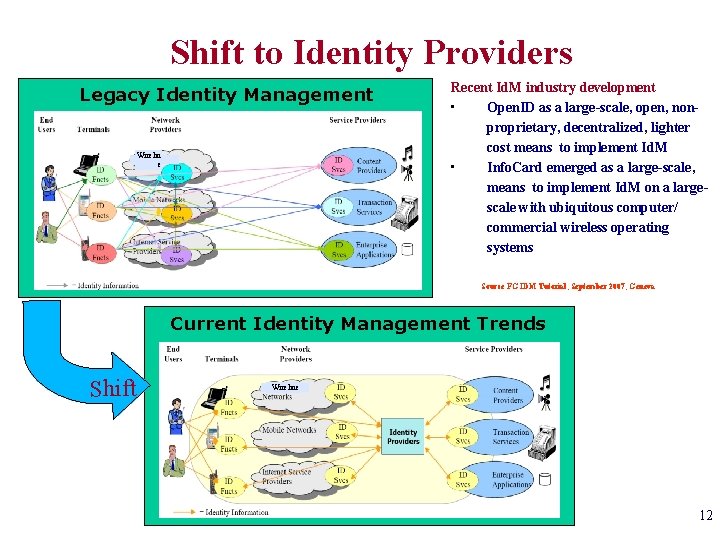
Shift to Identity Providers Legacy Identity Management Wirelin e Recent Id. M industry development • Open. ID as a large-scale, open, nonproprietary, decentralized, lighter cost means to implement Id. M • Info. Card emerged as a large-scale, means to implement Id. M on a largescale with ubiquitous computer/ commercial wireless operating systems Source FG IDM Tutorial, September 2007, Geneva Current Identity Management Trends Shift Wireline 12

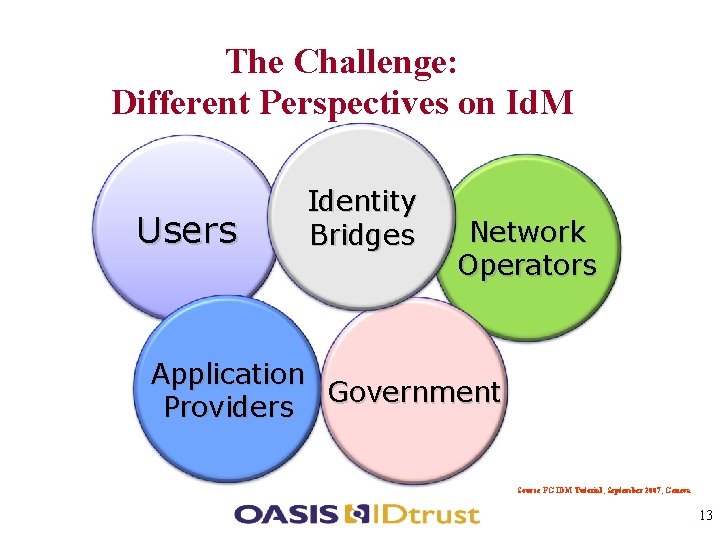
The Challenge: Different Perspectives on Id. M Users Identity Bridges Network Operators Application Government Providers Source FG IDM Tutorial, September 2007, Geneva 13

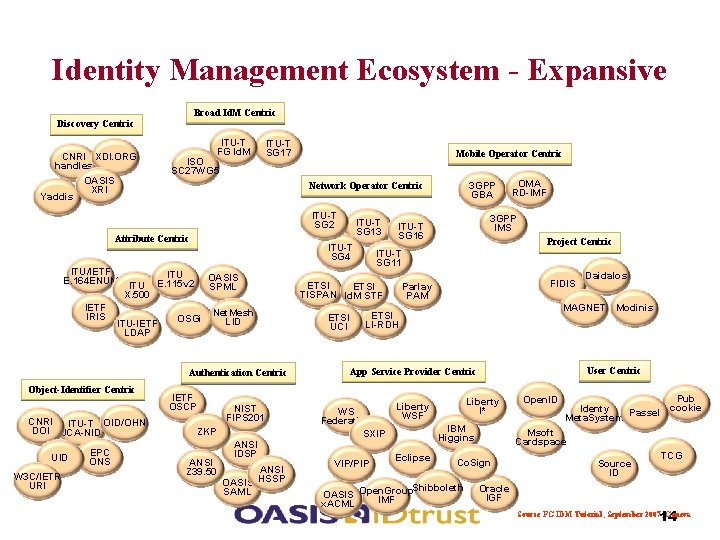
Identity Management Ecosystem - Expansive Broad Id. M Centric Discovery Centric CNRI XDI. ORG handles Yaddis OASIS XRI ITU-T FG Id. M ISO SC 27 WG 5 ITU-T SG 17 Mobile Operator Centric ITU-T SG 2 Attribute Centric ITU/IETF E. 164 ENUM IETF IRIS ITU E. 115 v 2 X. 500 ITU-IETF LDAP Object-Identifier Centric CNRI ITU-T OID/OHN DOI JCA-NID W 3 C/IETR URI EPC ONS ITU-T SG 13 ITU-T SG 4 OASIS SPML OSGi Net. Mesh LID Authentication Centric UID 3 GPP GBA Network Operator Centric IETF OSCP NIST FIPS 201 ZKP ANSI Z 39. 50 ANSI IDSP ANSI OASIS HSSP SAML 3 GPP IMS ITU-T SG 16 Project Centric ITU-T SG 11 ETSI TISPAN Id. M STF ETSI UCI OMA RD-IMF FIDIS Parlay PAM MAGNET Modinis ETSI LI-RDH User Centric App Service Provider Centric WS Federation SXIP VIP/PIP Liberty I* Liberty WSF IBM Higgins Eclipse Daidalos Pub cookie Identy Passel Meta. System Msoft Cardspace Co. Sign Shibboleth OASIS Open. Group IMF x. ACML Open. ID Source ID TCG Oracle IGF 14 Source FG IDM Tutorial, September 2007, Geneva

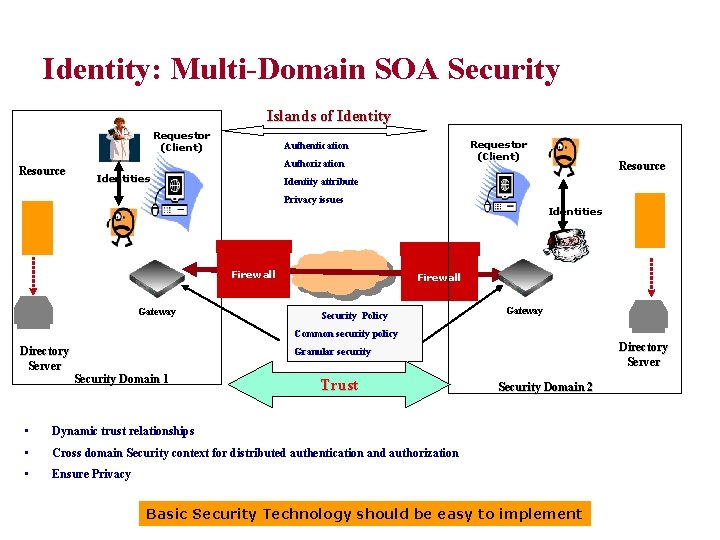
Identity: Multi-Domain SOA Security Islands of Identity Requestor (Client) Resource Requestor (Client) Authentication Authorization Identities Identity attribute Privacy issues Firewall Gateway Resource Identities Firewall Security Policy Gateway Common security policy Directory Server Granular security Security Domain 1 Trust • Dynamic trust relationships • Cross domain Security context for distributed authentication and authorization • Ensure Privacy Security Domain 2 Basic Security Technology should be easy to implement

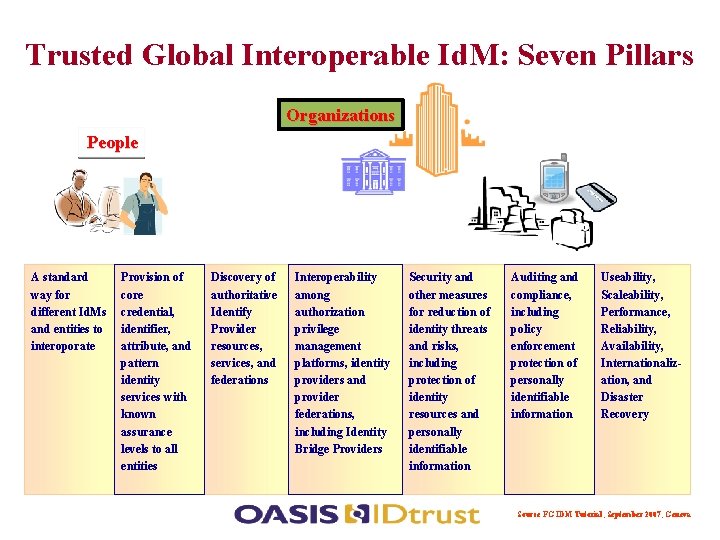
Trusted Global Interoperable Id. M: Seven Pillars Organizations People A standard way for different Id. Ms and entities to interoporate Provision of core credential, identifier, attribute, and pattern identity services with known assurance levels to all entities Discovery of authoritative Identify Provider resources, services, and federations Interoperability among authorization privilege management platforms, identity providers and provider federations, including Identity Bridge Providers Security and other measures for reduction of identity threats and risks, including protection of identity resources and personally identifiable information Auditing and compliance, including policy enforcement protection of personally identifiable information Useability, Scaleability, Performance, Reliability, Availability, Internationalization, and Disaster Recovery Source FG IDM Tutorial, September 2007, Geneva

Workshop Ø Ø Ø Thank you for you participation Our Keynote Speaker: Andre Durand, Ping Identity Chairman and CEO 'Unlocking the potential of identity federation' Ø Ø Founder, Chairman and CEO of Ping Identity, leading provider of federated Id. M software for enabling secure Internet single sign-on Co-founder and co-chair of Digital ID World, the digital identity industry conference operated in connection with CSO/CIO media Founded Jabber, Inc. , a leading global provider of in instant messaging and presence management solutions serving both the carrier and enterprise markets Founded Durand Communications, a provider of client/server solutions for online databases and applications. 17

Acknowledgement Ø Some slides were based on ITU-T SG 17 FG Id. M September 19 -28 tutorials by Ray Singh (Telecordia), Tony Rutkowski (Veri. Sign), Anthony Nadalin (IBM) and Sergio Fiszman (Nortel) 18
 A desert herder who traveled from oasis to oasis
A desert herder who traveled from oasis to oasis Oasis-open.org
Oasis-open.org Maps identity
Maps identity Welcome welcome this is our christmas story
Welcome welcome this is our christmas story Tosca cloud
Tosca cloud Oasis soa
Oasis soa Regine coolen
Regine coolen Oasis lleva tilde
Oasis lleva tilde Current oasis 7
Current oasis 7 Oasis nextgen
Oasis nextgen Oasis svt
Oasis svt Heidelberg oasis
Heidelberg oasis P
P How does an oasis form
How does an oasis form Acquiescence bias definition
Acquiescence bias definition Cvjećarske spužve
Cvjećarske spužve Oasis virtio
Oasis virtio Frases de oasis
Frases de oasis Ecfmg i644
Ecfmg i644



































