SDN and NFV Security SDN Security Dr Dijiang



- Slides: 11

SDN and NFV Security SDN Security Dr. Dijiang Huang Arizona State University

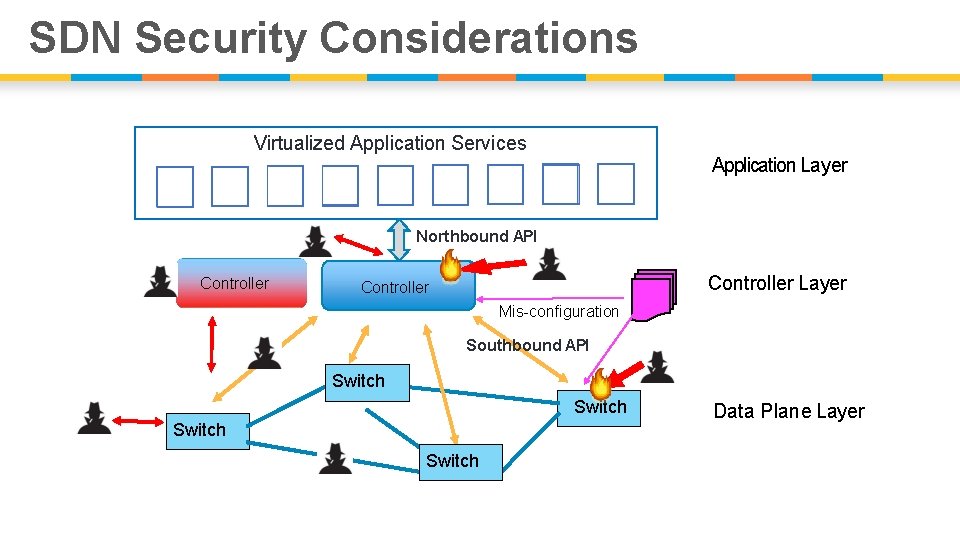
SDN Security Considerations Virtualized Application Services Application Layer Northbound API Controller Layer Controller Mis-configuration Southbound API Switch Data Plane Layer

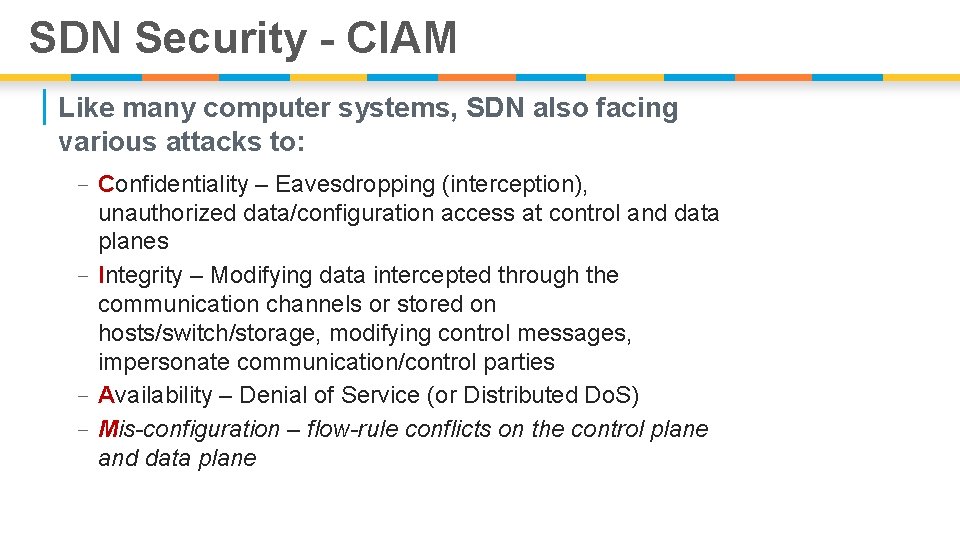
SDN Security - CIAM | Like many computer systems, SDN also facing various attacks to: - Confidentiality – Eavesdropping (interception), unauthorized data/configuration access at control and data planes - Integrity – Modifying data intercepted through the communication channels or stored on hosts/switch/storage, modifying control messages, impersonate communication/control parties - Availability – Denial of Service (or Distributed Do. S) - Mis-configuration – flow-rule conflicts on the control plane and data plane

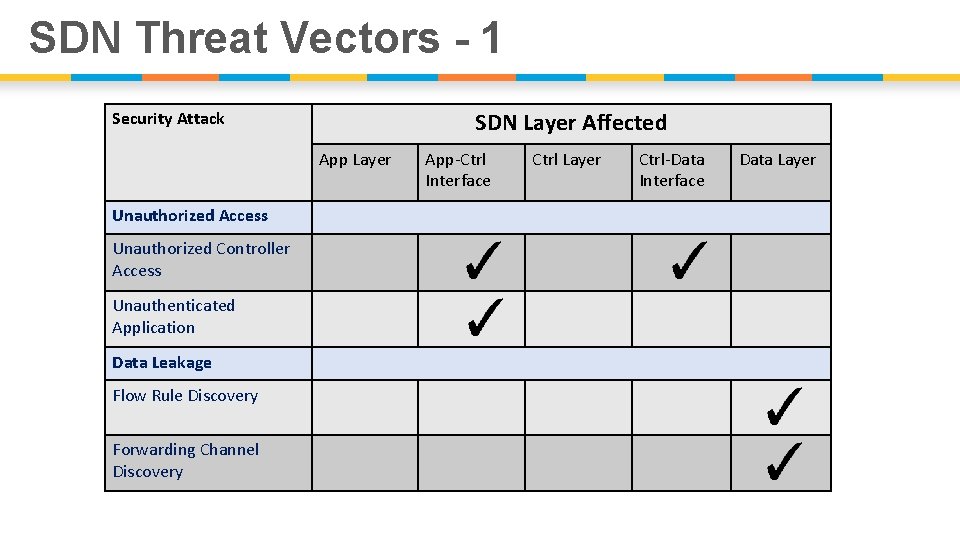
SDN Threat Vectors - 1 SDN Layer Affected Security Attack App Layer Unauthorized Access Unauthorized Controller Access Unauthenticated Application Data Leakage Flow Rule Discovery Forwarding Channel Discovery App-Ctrl Interface Ctrl Layer Ctrl-Data Interface Data Layer

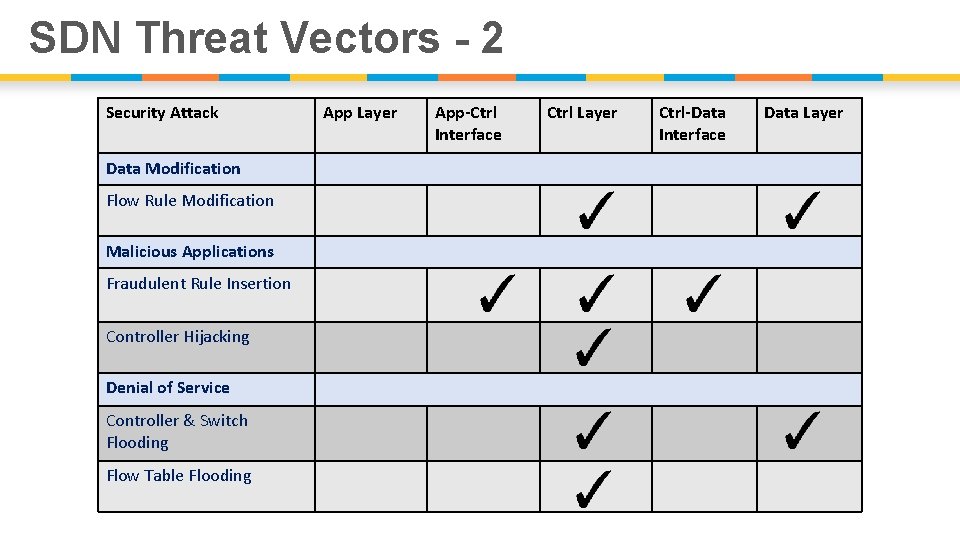
SDN Threat Vectors - 2 Security Attack Data Modification Flow Rule Modification Malicious Applications Fraudulent Rule Insertion Controller Hijacking Denial of Service Controller & Switch Flooding Flow Table Flooding App Layer App-Ctrl Interface Ctrl Layer Ctrl-Data Interface Data Layer

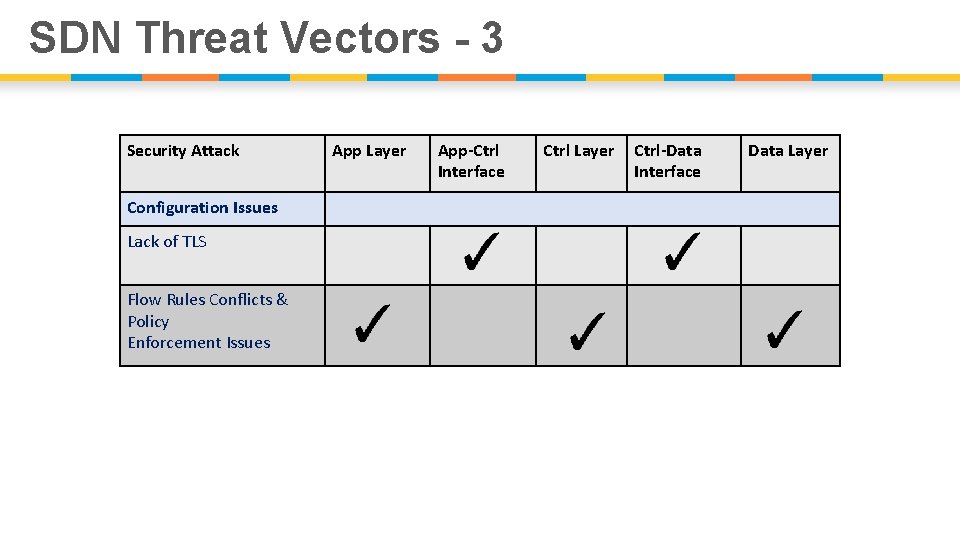
SDN Threat Vectors - 3 Security Attack Configuration Issues Lack of TLS Flow Rules Conflicts & Policy Enforcement Issues App Layer App-Ctrl Interface Ctrl Layer Ctrl-Data Interface Data Layer

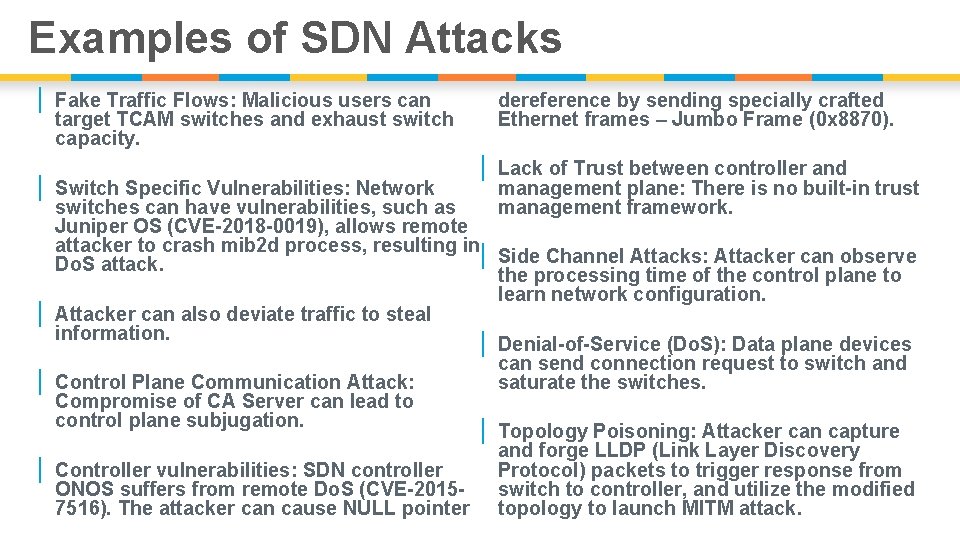
Examples of SDN Attacks | Fake Traffic Flows: Malicious users can target TCAM switches and exhaust switch capacity. | Switch Specific Vulnerabilities: Network | | | dereference by sending specially crafted Ethernet frames – Jumbo Frame (0 x 8870). | Lack of Trust between controller and management plane: There is no built-in trust management framework. switches can have vulnerabilities, such as Juniper OS (CVE-2018 -0019), allows remote attacker to crash mib 2 d process, resulting in | Side Channel Attacks: Attacker can observe Do. S attack. the processing time of the control plane to learn network configuration. Attacker can also deviate traffic to steal information. | Denial-of-Service (Do. S): Data plane devices can send connection request to switch and Control Plane Communication Attack: saturate the switches. Compromise of CA Server can lead to control plane subjugation. | Topology Poisoning: Attacker can capture and forge LLDP (Link Layer Discovery Controller vulnerabilities: SDN controller Protocol) packets to trigger response from ONOS suffers from remote Do. S (CVE-2015 switch to controller, and utilize the modified 7516). The attacker can cause NULL pointer topology to launch MITM attack.

Strategies of SDN Security Solutions 1. Replication at application plane and control plane can help in dealing with high-traffic volume. (PKI) can be used for trust management. The behavior of device (normal or anomalous) can also be considered while establishing trust. 2. Diversity of controller software improves 6. Controller-App Plane Trust using mutual trust, robustness and intrusion tolerance. Since there are only a few intersecting vulnerabilities between diverse software, common security issues can be reduced using this technique. 3. Automated Recovery using efficient proactive and reactive security mechanism such as alternate versions of controller in an event of failure providing similar functionality. 4. Dynamic Device Association can help in automatically shifting to alternate controller in an event of failure. This also helps in providing efficient load-balancing. 5. Controller-Switch Trust using whitelisting of trusted switches and public-key infrastructure delegated-trust (3 rd party CA) can help in preventing authentication and authorization violation attacks. 7. Security Domains can help in segmenting network into trust boundaries and quarantining the threat only to the infected network segment or trust domain. 8. SDN-based Distributed Firewall, security policy conflict checking, etc.

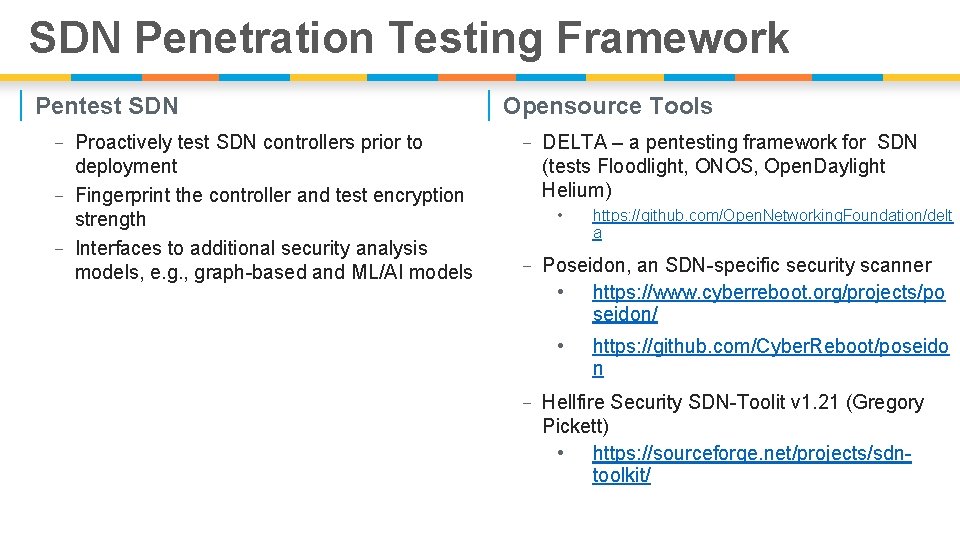
SDN Penetration Testing Framework | Pentest SDN - Proactively test SDN controllers prior to deployment - Fingerprint the controller and test encryption strength - Interfaces to additional security analysis models, e. g. , graph-based and ML/AI models | Opensource Tools - DELTA – a pentesting framework for SDN (tests Floodlight, ONOS, Open. Daylight Helium) • https: //github. com/Open. Networking. Foundation/delt a - Poseidon, an SDN-specific security scanner • https: //www. cyberreboot. org/projects/po seidon/ • https: //github. com/Cyber. Reboot/poseido n - Hellfire Security SDN-Toolit v 1. 21 (Gregory Pickett) • https: //sourceforge. net/projects/sdntoolkit/

STIGs for SDN | Security Technical Implementation Guides (STIGs) SDN Controller security requirements guide - https: //www. stigviewer. com/stig/sdn_controller_security_requirements_g uide/ | Industry effort - VMware NSX meets STIG for DOD - VMware NSX® Security Technical Implementation Guide (STIG), version 1, 2016

Wrap-Up