PREVIOUS GNEWS Patch Tuesday Patches Critical CVEs Affected











- Slides: 14

PREVIOUS GNEWS

Patch • • Tuesday ? Patches – ? Critical – ? CVEs Affected – ? Other updates, MSRT, Defender Definitions, Junk Mail Filter

Holes / Patches • Oracle, 128 fixes – 42 just for Java • Adobe – none • Apple, – Safari 6. 0. 4 – Java • Cisco – – – Unified Communications, multiple Prime Central, multiple NX-OS, multiple IOS, multiple ASA, multiple

Holes / Patches • IE • Apache

Hacking • car chargers • bing for malware • FB Home, it's inevitable • FAA denies airplane hack could work • NJ Senator calls for investigation • apple pirate store • anonymous news site • google glass jail broken

Corp • Can we get a desktop please • malwarebytes screws the pooch • Japan asks ISPs to block tor • Avast launches bug bounty program • NASA sponsored global hackathon • Criagslist • eff star chart • google big data on wheels

Corp • EA Games mines all your bit coins • FTC calls for andriod patch investigation • Mc. Afee to buy stonesoft • Bittorrent Sync

Legal • CISPA ammendment approved in house • CISPA killed in senate • CFAA stalled for now • pirate bay founder on theft / hacking charges • WIPO broadcast treaty • no hacking • force taps • dutch my open door for cop hack back

Papers • Snort OSSIM integration • http: //blog. snort. org/2013/04/integrating-snort-and-alienvault-ossim. html • analyzing h 323 traffic. • https: //www. sans. org/reading_room/whitepapers/protocols/analyzing-polycom-video-conference-traffic_34167 • exploiting soho routers • http: //securityevaluators. com//content/case-studies/routers/soho_router_hacks. jsp • use of IOC • https: //www. sans. org/reading_room/whitepapers/incident/ioc-indicators-compromise-malware-forensics_34200 • Firewall review • https: //www. sans. org/reading_room/whitepapers/auditing/methodology-firewall-reviews-pci-compliance_34195 • MS intell report • http: //www. microsoft. com/security/sir/default. aspx • verizon data breach report • http: //www. verizonenterprise. com/DBIR/2013/

Papers • Symantec threat report • https: //www. symantec. com/security_response/publications/threatreport. jsp • NIST Update Special Publication 800 -53, Revision 4: Security and Privacy Controls for Federal Information Systems and Organizations • http: //nvlpubs. nist. gov/nistpubs/Special. Publications/NIST. SP. 800 -53 r 4. pdf • UEFI hacking • https: //www. sans. org/reading_room/whitepapers/services/analysis-building-blocks-attack-vectors-unifiedextensible-firmware_34215 • mobile malware lab • http: //resources. infosecinstitute. com/portable-malware-lab-for-beginners/ • bitcoin 101 • http: //resources. infosecinstitute. com/how-to-profit-illegally-from-bitcoin-cybercrime-and-much-more/ • search engine hacking • http: //resources. infosecinstitute. com/search-engine-hacking-manual-and-automation/rr

tools pentesting http: //it. toolbox. com/blogs/securitymonkey/excellent-web-pentesting-education-materials-and-free 55541? rss=1 google inactive account manager http: //nakedsecurity. sophos. com/2013/04/15/google-data-after-you-die disconnect 2 https: //disconnect. me/ lynis http: //www. unixmen. com/audit-the-security-of-your-unixlinux-systems-using-lynis/ windows debugg http: //www. smidgeonsoft. prohosting. com/software. html REMnux http: //zeltser. com/remnux/ ibm homo encryption http: //news. hitb. org/content/ibm-takes-big-new-step-cryptography-practical-homomorphic-encryption debian 7. 0

WTF • Ooops

CON Events carolina con http: //it. toolbox. com/blogs/securitymon key/macgyveresque-weaponbuilding-in-airports-55540? rss=1 shmoo vids http: //it. toolbox. com/blogs/securitymon key/did-you-miss-shmoocon-2013 videos-are-online-55539? rss=1 HITB Amsterdam http: //conference. hitb. org/hitbsecconf 2 013 ams/materials/FB 0 auth http: //news. hitb. org/content/story-9500 -bug-facebook-oauth-20 http: //conference. hitb. org/hitbsecconf 2 013 ams/materials/D 2 T 1%20%20 Andrey%20 Labunets%20 and

All images scavenged without permission
 What is inflation in ansys
What is inflation in ansys Critical semi critical and non critical instruments
Critical semi critical and non critical instruments Critical semi critical and non critical instruments
Critical semi critical and non critical instruments Gary gnu images
Gary gnu images Vmsa-2017-0021
Vmsa-2017-0021 Breast imperceptible newborn
Breast imperceptible newborn American legion riders patch rules
American legion riders patch rules Malt tonsils
Malt tonsils Badges borduren
Badges borduren Strijk patches maken
Strijk patches maken Ileocecal reflex
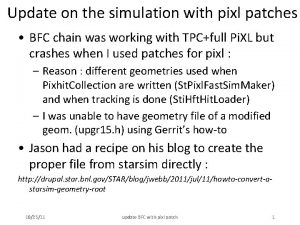
Ileocecal reflex Pixl patches
Pixl patches Composition of lymph
Composition of lymph Hassall's corpuscle
Hassall's corpuscle Compare non-critical readers with critical readers.
Compare non-critical readers with critical readers.