NDIA SECURITY EXPO 2003 MISSION CRITICAL PROCESSING Presentation


- Slides: 10

NDIA SECURITY EXPO - 2003 MISSION CRITICAL PROCESSING Presentation Daniel Skret © 2002 Vindicator Technologies, Inc SECURITY SOLUTIONS FOR DEMANDING APPLICATIONS

© 2002 Vindicator Technologies Mission Critical Processing q Enforcing Security Policy q Situational Awareness q Automatic Behaviors q Systems Integration SECURITY SOLUTIONS FOR DEMANDING APPLICATIONS

© 2002 Vindicator Technologies Mission Execution q Reduce PC’s Role to User Interface q Perform Mission via Security Appliances SECURITY SOLUTIONS FOR DEMANDING APPLICATIONS

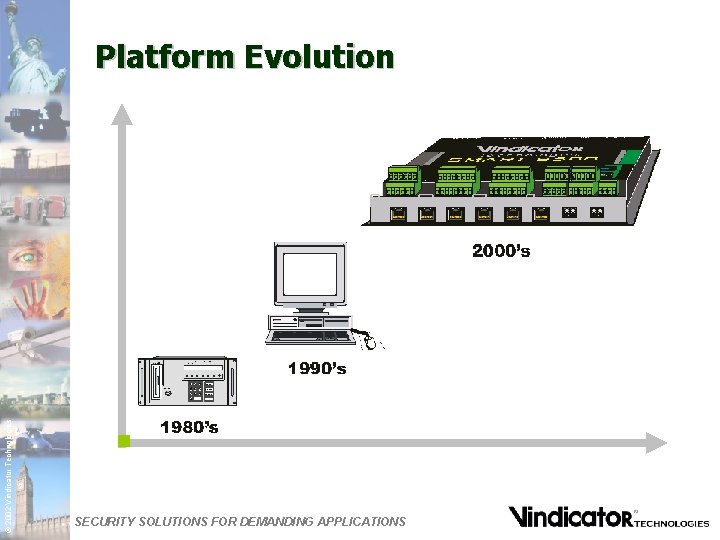
© 2002 Vindicator Technologies Platform Evolution SECURITY SOLUTIONS FOR DEMANDING APPLICATIONS

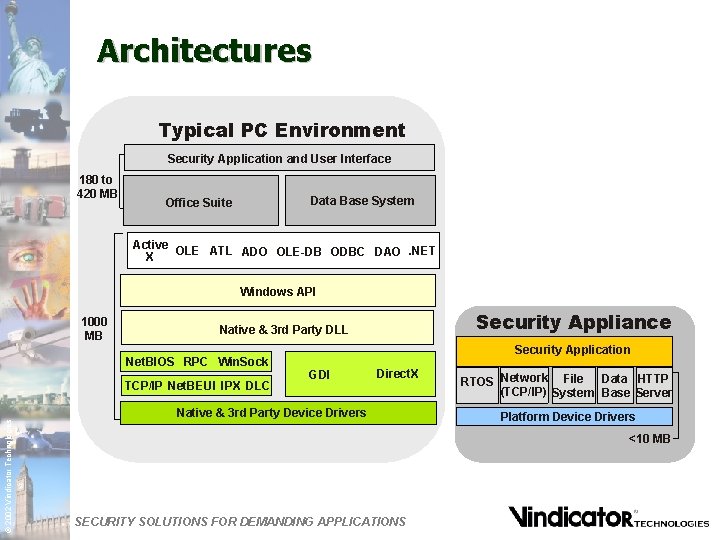
Architectures Typical PC Environment Security Application and User Interface 180 to 420 MB Data Base System Office Suite Active OLE ATL ADO OLE-DB ODBC DAO. NET X Windows API 1000 MB Net. BIOS RPC Win. Sock TCP/IP Net. BEUI IPX DLC © 2002 Vindicator Technologies Security Appliance Native & 3 rd Party DLL Security Application GDI Direct. X Native & 3 rd Party Device Drivers RTOS Network File Data HTTP (TCP/IP) System Base Server Platform Device Drivers <10 MB SECURITY SOLUTIONS FOR DEMANDING APPLICATIONS

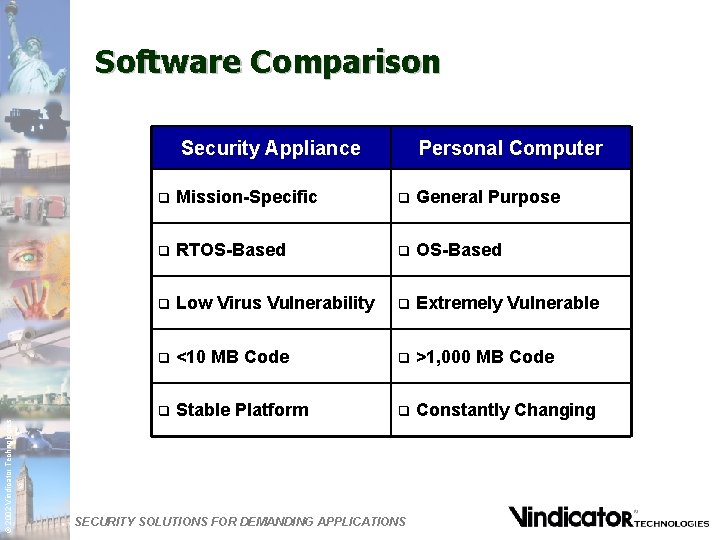
Software Comparison © 2002 Vindicator Technologies Security Appliance Personal Computer q Mission-Specific q General Purpose q RTOS-Based q Low Virus Vulnerability q Extremely Vulnerable q <10 MB Code q >1, 000 MB Code q Stable Platform q Constantly Changing SECURITY SOLUTIONS FOR DEMANDING APPLICATIONS

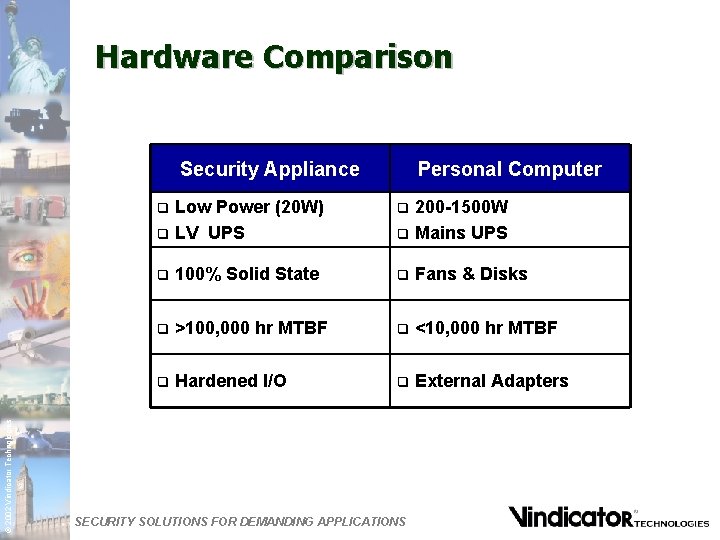
Hardware Comparison Security Appliance Low Power (20 W) q LV UPS © 2002 Vindicator Technologies q Personal Computer 200 -1500 W q Mains UPS q q 100% Solid State q Fans & Disks q >100, 000 hr MTBF q <10, 000 hr MTBF q Hardened I/O q External Adapters SECURITY SOLUTIONS FOR DEMANDING APPLICATIONS

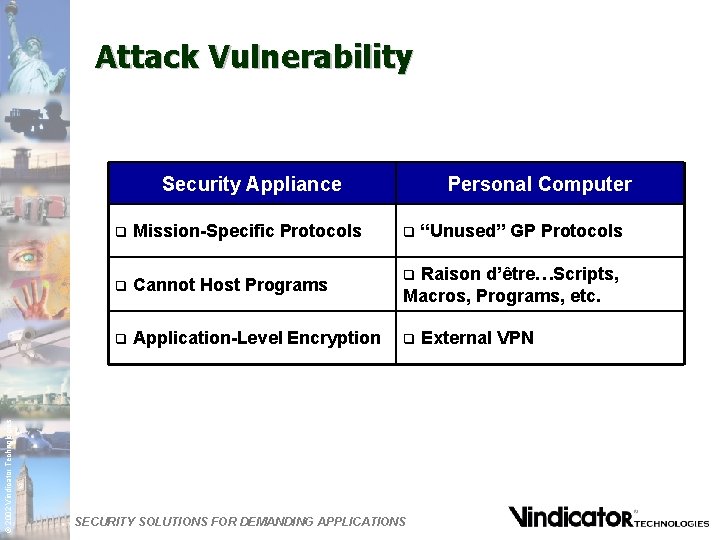
Attack Vulnerability © 2002 Vindicator Technologies Security Appliance q Mission-Specific Protocols q Cannot Host Programs q Application-Level Encryption Personal Computer q “Unused” GP Protocols Raison d’être…Scripts, Macros, Programs, etc. q q SECURITY SOLUTIONS FOR DEMANDING APPLICATIONS External VPN

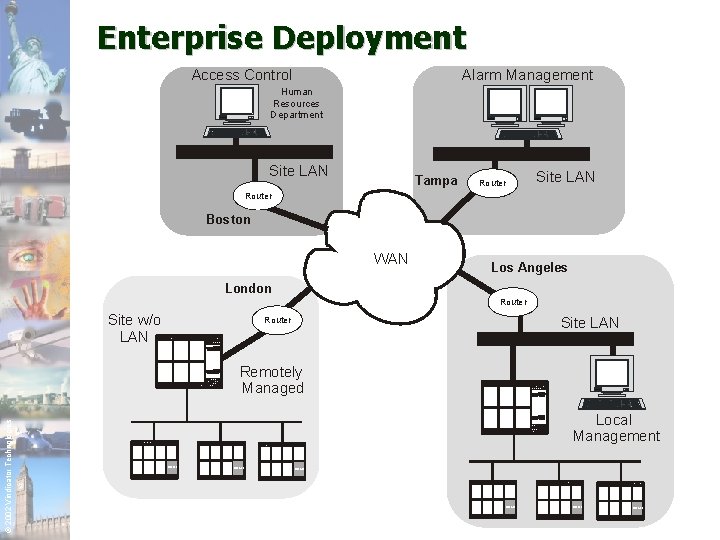
Enterprise Deployment Alarm Management Access Control Human Resources Department Site LAN Tampa Router Site LAN Router Boston WAN Los Angeles London Router Site w/o LAN Site LAN Router © 2002 Vindicator Technologies Remotely Managed Local Management RS-485 SECURITY SOLUTIONS FOR DEMANDING APPLICATIONS RS-485

© 2002 Vindicator Technologies Systems Summary q Core Processing via Appliances q PC’s for User Interface + Clerical Work q Questions? Daniel Skret 512 -301 -8428 skret@vintec. com SECURITY SOLUTIONS FOR DEMANDING APPLICATIONS