JINI An Authentication and Authorization Architecture for Jini








- Slides: 10

JINI An Authentication and Authorization Architecture for Jini Services

An ICSI Story • Clients needs services ICSI newcomers need a flat • Services needs clients Landlords want to lease their flats • Marketplace needed Home Finders Bulletin (or ask Diane) • How to find marketplace Yellow Pages

An ICSI Story, Part 2 • Communication marketplace -> Specify preferences -> List of offerings, + Tel-No. • Client-Server communication -> ICSI newcomer calls a landlord • Problems -> List out of date • Solution -> Landlord must lease entry in list, renewal, otherwise remove from list

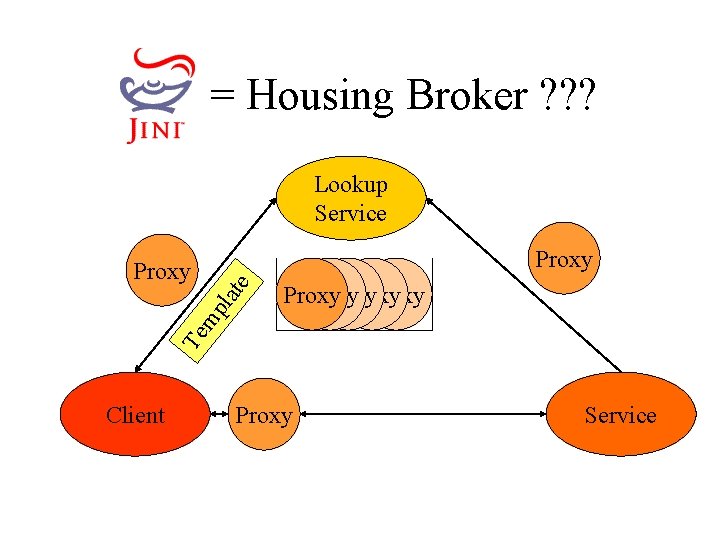
= Housing Broker ? ? ? Lookup Service Proxy Proxy Te mp lat e Proxy Client Proxy Service

Jini Concepts • • Discovery (Yellow Pages) Lookup (Home Finders Bulletin) Leasing (Leasing of list entry) Remote Events – ICSI newcomers receives new offers • Transaction – Key exchange at HFB: Key Money

Home Environment • TV service + Storage service = VCR service • lawn sprinkler + weather service • defect -> maintenance service -> appointment service • general: leasing appropriate for spontaneous networking • PDA -> conference room -> printer access

Why Security? • Only subscribers should get offers – authentication needed • Different packages are offered: standard $30, premium $50; restricted access – authorization required • Internet communication insecure: data can be read, altered or replayed – Integrity, Confidentiality required

Secure Communication • Proxies are signed (Integrity + Identity) • All communication is encrypted using a secret session key (Confidentiality) • Message Authentication Code (Integrity) • Transaction Numbers (Replay attacks)

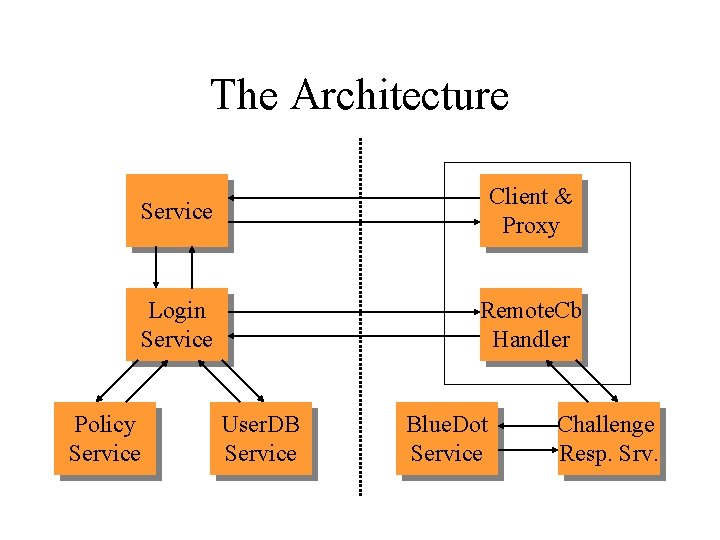
The Architecture Policy Service Client & Proxy Login Service Remote. Cb Handler User. DB Service Blue. Dot Service Challenge Resp. Srv.

Highlights • • Uses standard Java technology Transparency for the client Minimal Overhead at server side Powerful login policies First Prototype up and running Internal Java Authorizations mechanisms Well adapted for home services: TV, fridge