ITU Workshop on ICT Security Standardization for Developing





- Slides: 7

ITU Workshop on “ICT Security Standardization for Developing Countries” (Geneva, Switzerland, 15 -16 September 2014) ITU-T SG 17 Identity management (Id. M) Progress Report Abbie Barbir Ph. D. , ITU-T Study Group 17 Q 10/17 (Identity Management) Rapporteur Abbie. Barbir@ties. itu. int Geneva, Switzerland, 15 -16 September 2014

Q 10/17 Identity management (Id. M) Motivation Question is dedicated to vision setting and the coordination and organization of entire range of Id. M activities within ITU-T Focus on global trust and interoperability Focus on leveraging and building on existing solutions Coordination with all key players in Id. M (JCA-Id. M) Some examples of current focus include: 2 Developing of Identity Roadmap Work with OASIS Enhancing Trust and step up authentication Work on Identity Based Attestation and Open Exchange Protocol Developing identity in cloud uses cases and security requirements from a Telecom prospective (Auth as a Service) Mechanisms for the discovery of identifiers in large distributed systems Exposing of network level Authentication to Higher level Applications Id. M taxonomy and Ontology SCIM for telecom use cases

Coordination and Collaboration 3

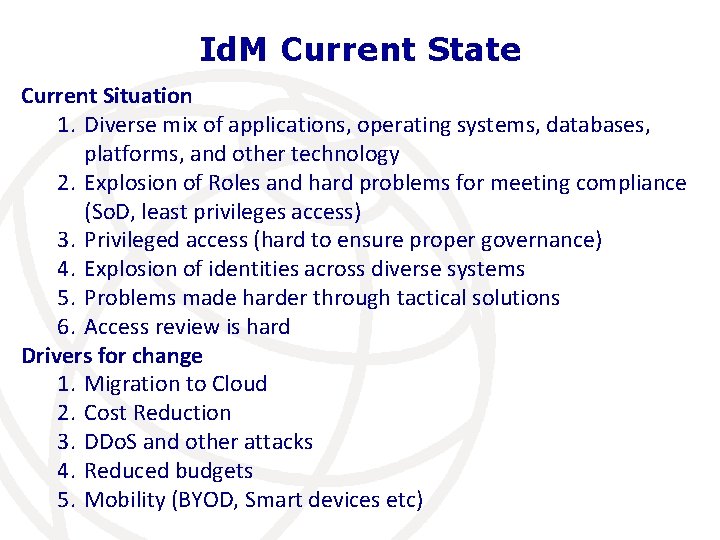
Id. M Current State Current Situation 1. Diverse mix of applications, operating systems, databases, platforms, and other technology 2. Explosion of Roles and hard problems for meeting compliance (So. D, least privileges access) 3. Privileged access (hard to ensure proper governance) 4. Explosion of identities across diverse systems 5. Problems made harder through tactical solutions 6. Access review is hard Drivers for change 1. Migration to Cloud 2. Cost Reduction 3. DDo. S and other attacks 4. Reduced budgets 5. Mobility (BYOD, Smart devices etc)

Drivers for Future Direction Desired Future State 1. Risk reduction Risk and behavioral driven, business centric 2. User experience Clear business language for informed decision making SSO with enhancements to the user login flow and session management 3. Operational efficiency Standardized and integrated operations 4. Governance and business enablement Clear and consistent standards End-to-end governance structure with effective metrics and controls Consistent authentication operating model that provides a one-stop security service solution

Towards Strong Identity and Enhanced Trust Need for Better Identity Assurance and Trust Frameworks Technology Standards and Guidelines Business and Privacy Guidelines An Ecosystem of Interoperable Products & Services Identity Assurance Framework & Assessors Assurance

Future focus Passwords are Dead Industry is taking notice FIDO specifications maturing Step up authentication is gaining steam Mobility is a driver Mobile SSO need to mature Mobile Ass. S need to mature Mobile payments. Q 10 will work with key industry leaders in this area Geneva, Switzerland, 15 -16 September 2014 7