HIPAA WHAT IS HIPAA In 1996 the Health















- Slides: 16

HIPAA

WHAT IS HIPAA? In 1996, the Health Insurance Portability and Accountability Act or the HIPAA was endorsed by the U. S. Congress. The HIPAA Privacy Rule, also called the Standards for Privacy of Individually Identifiable Health Information, provided the first nationallyrecognizable regulations for the use/disclosure of an individual's health information. Essentially, the Privacy Rule defines how covered entities use individually-identifiable health information or the PHI (Personal Health Information). 'Covered entities' is a term often used in HIPAA-compliant guidelines. This definition of a covered entity is specified by [45 CFR § 160. 102] of the Privacy Rule. A covered entity can be a:

WHAT IS HIPAA? CONT. A covered entity can be a : • Health plan • Healthcare clearinghouse • Healthcare provider

OVERVIEW OF PRIVACY LAW • Gives patients control over the use of their health information • Defines boundaries for the use/disclosure of health records by covered entities • Establishes national-level standards that healthcare providers must comply with • Helps to limit the use of PHI and minimizes chances of its inappropriate disclosure • Strictly investigates compliance-related issues and holds violators accountable with civil or criminal penalties for violating the privacy of an individual's PHI • Supports the cause of disclosing PHI without individual consent for individual healthcare needs, public benefit and national interests

FOUR RULES OF HIPAA Privacy Rule HIPAA Security Rule HIPAA Enforcement Rule HIPAA Breach Notification Rule

PROTECTED HEALTH INFORMATION (PHI) You will hear this term non-stop when dealing with applications that can store health information. It’s typically called PHI although some parts of the law refer to digitallystored PHI as e. PHI. We’ll stick with PHI for consistency. PHI is any information in a medical record that can be used to identify an individual, and that was created, used, or disclosed in the course of providing a health care service, such as a diagnosis or treatment. In other words, PHI is information in your medical records, including conversations between your doctors and nurses about your treatment. PHI also includes your billing information and any medical information in your health insurance company’s computer system. Some examples of PHI: Billing information of program Members Program members Diagnosis Program members name and any information contained in program members case records.

ADDITIONAL STAKEHOLDERS A covered entity is anyone who provides treatment, payment and operations in healthcare. All care providers for this agency are a covered entity. Simply put, a Business Associate is a vendor or subcontractor who has access to PHI.

THREE PARTS TO THE HIPAA SECURITY RULE Administrative Safeguards Technical Safeguards Physical Safeguards

ADMINISTRATIVE SAFEGUARDS The administrative components are really important when implementing a HIPAA compliance program; you are required to: Assign a privacy officer Complete a risk assessment annually Implement employee training Review policies and procedures Execute Business Associate Agreements (BAAs) with all partners who handle protected health information (PHI)

TECHNICAL SAFEGUARDS Technical safeguards outline what your application must do while handling PHI. Access Control Requirements Unique User Identification (required): Assign a unique name and/or number for identifying and tracking user identity. Emergency Access Procedure (required): Establish (and implement as needed) procedures for obtaining necessary e. PHI during an emergency. Automatic Logoff (addressable): Implement electronic procedures that terminate an electronic session after a predetermined time of inactivity. Authentication (required): Implement procedures to verify that a person or entity seeking access to e. PHI is the one claimed. Encryption and Decryption (addressable): Implement a mechanism to encrypt and decrypt e. PHI.

PHYSICAL SAFEGUARDS The Physical Safeguards really have to do with who has access to PHI data and how that access is managed. Much of the Physical Safeguard requirements that developers need to worry about are handled by HIPAA compliant hosting companies (such as True. Vault, AWS, Firehost and Rackspace). Contingency Operations (addressable): Establish (and implement as needed) procedures that allow facility access in support of data restoration under the disaster recovery and emergency operations plan in the event of an emergency. Facility Security Plan (addressable): Implement policies and procedures to safeguard the facility and the equipment therein from unauthorized physical access, tampering, and theft. Maintenance Records (addressable): Implement policies and procedures to document repairs and modifications to thephysical components of a facility which are related to security (e. g. hardware, walls, doors, and locks).

PHYSICAL SAFEGUARDS CONT. Device and Media Controls Disposal (required): Implement policies and procedures to address the final disposition of e. PHI, and/or the hardware or electronic media on which it is stored. Media Re-Use (required): Implement procedures for removal of e. PHI from electronic media before the media are made available for re-use. Accountability (addressable): Maintain a record of the movements of hardware and electronic media and any person responsible therefore. Data Backup and Storage (addressable): Create a retrievable, exact copy of e. PHI, when needed, before movement of equipment. Workstation Security (required): Implement physical safeguards for all workstations that access e. PHI, to restrict access to authorized users. Workstation Use (required): Implement policies and procedures that specify the proper functions to be performed, the manner in which those functions are to be performed, and the physical attributes of the surroundings of a specific workstation or class of workstation that can access e. PHI.

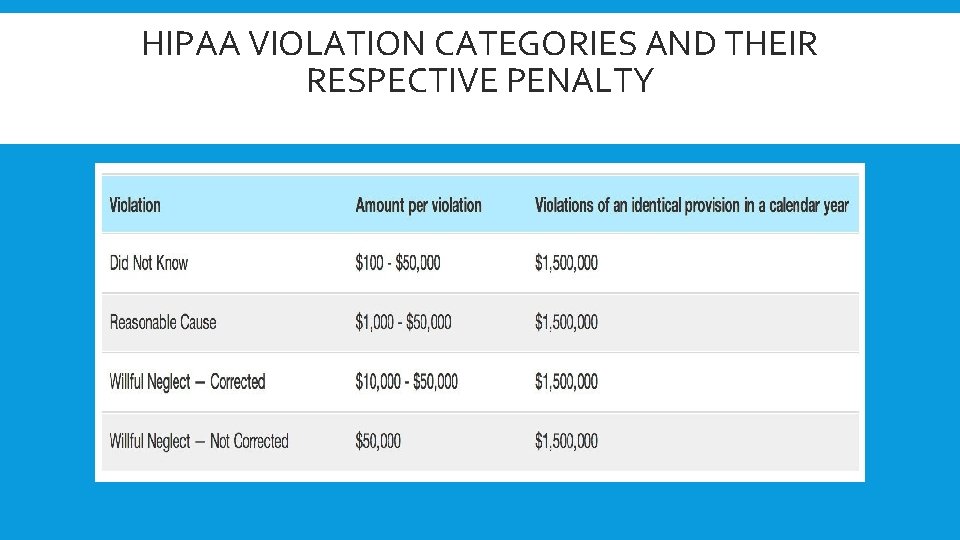
HIPAA VIOLATION CATEGORIES AND THEIR RESPECTIVE PENALTY

TYPES OF BREACHES Unencrypted Data While encryption is an addressable (rather than required) specification, it does not mean optional. The vast majority of data breaches are due to stolen or lost data that was unencrypted. When in doubt, you should implement the addressable implementation specifications of the Security Rule. Most of them are best practices. Employee Error Breaches can occur when employees lose unencrypted portable devices, mistakenly send PHI to vendors who post that information online, and disclose personally identifiable, sensitive information on social networks. Data Stored on Devices Almost half of all data breaches are the result of theft. When laptops, smartphones, etc. are unencrypted the risk of a breach increases considerably. Almost two-thirds of data breaches involved a business associate. Meaning that you delegated a covered function or activity to someone, and that someone messed up. So pick your partners carefully.

How To Access Your Privacy Officer totto o Access You Privacy Officer H The Privacy Officer for COHF, Inc. is Erika Travinski You may contact her for an appointment at any time. • Phone: 508 -764 -4085 ext. 677. • E-mail: etravinski@thecenterofhope. org • Leaving a message in her mailbox located in the main office. How to File a Complaint All privacy complaints will be directed to Erika Travinski, Privacy Officer, for proper processing and handling. The privacy officer will review the complaint, investigate it, and report the results of the investigation to the appropriate individuals. How to Access more Information on HIPAA You may find additional HIPAA information in the Training Department office. You may also find information on the web at www. hipaa. org. The Center of Hope Privacy notice are posted in all programs and through-out the agency.

SUMMARY We are considered a medical facility and we must all be HIPAA compliant. You have now completed your HIPAA training. For further information contact your Human Resource or the Training Department. Please proceed to the testing portion and complete the follow-up test. Upon completion results will be sent to the training office where you will be notified of your status of Pass or Fail. Accommodations will be made for any staff who is not able to complete the online testing. Please notify your supervisor.
 Kitabu cha mulokozi 2017
Kitabu cha mulokozi 2017 Carta di lussemburgo 1996
Carta di lussemburgo 1996 1996 xxxi
1996 xxxi 1996 xxxi
1996 xxxi Married persons equality act 1 of 1996
Married persons equality act 1 of 1996 Ottawa declaration 1996
Ottawa declaration 1996 1996 centennial olympics button
1996 centennial olympics button Resolucion 2343 de 1996
Resolucion 2343 de 1996 Os caçadores de tesouros 1996
Os caçadores de tesouros 1996 Osha 1996
Osha 1996 Telecommunications act of 1996
Telecommunications act of 1996 Panchayati raj
Panchayati raj Cimah
Cimah Modelo de hax (1992)
Modelo de hax (1992) Feldman & gracon 1996
Feldman & gracon 1996 Decreto 1791 del 4 de octubre de 1996
Decreto 1791 del 4 de octubre de 1996 Teknologi informasi menurut haag dan keen
Teknologi informasi menurut haag dan keen































