Grid Security Risks Mike Surridge msitinnovation soton ac








- Slides: 11

Grid Security Risks Mike Surridge ms@it-innovation. soton. ac. uk GGF 12, 20 Sep 2004, Brussels

Grid Security Risks • Connecting to Grids is a risky business – – your machine could be cracked your data may be intercepted or corrupted your credentials may be compromised to protect against all this may be too expensive • On the other hand – using any computer network is risky – using Grids can be very advantageous • How can we benefit while managing risks?

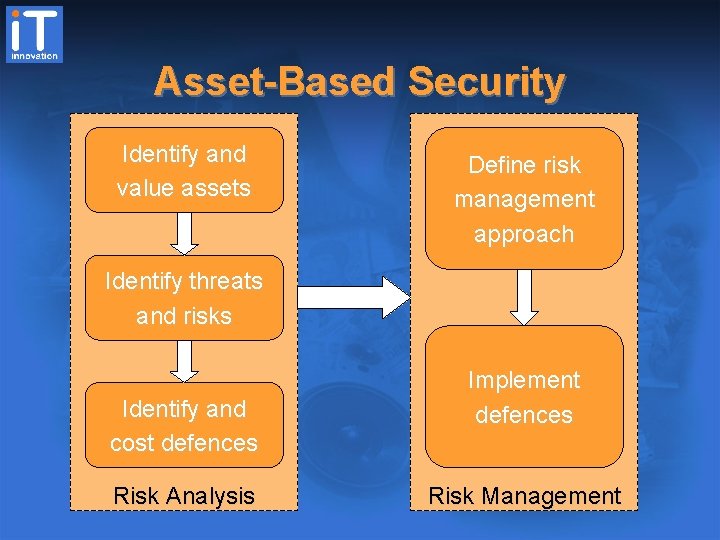
Asset-Based Security Identify and value assets Define risk management approach Identify threats and risks Identify and cost defences Risk Analysis Implement defences Risk Management

Risk Analysis • Value assets based on impact of compromise – high: likely to cause total business failure – med: serious but not fatal impact – low: irritating but not serious • Threats based on likelihood of attack – high: attacks will definitely take place – med: attacks may occur from time to time – low: attacks are unlikely • Analyse risks based on likelihood of success – taking account of existing defences

Risk Management • Determine appropriate response to threats – acceptance: live with the potential consequences – reduction: introduce defences – avoidance: don’t use the system • Leads to cost-effective security – as much security as you need – not more than you can afford • Application to Grids pioneered by UK STF – A. Sasse, H. Chivers, M. Surridge, etc

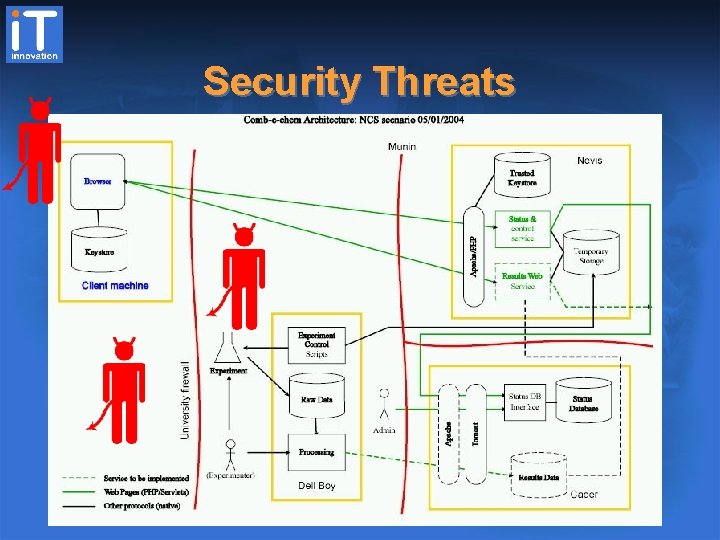
Case Study: Comb-e-Chem • National Crystallography Service – providing access to experimental steering – delivering data for Grid-based computations • Assets: medium or high value – campus system and network integrity (high) – sample tracking data (med) – experimental result data (low/med) • Threats: high likelyhood – system attacks from outside campus (high) – system attacks from inside campus (med) – compromise of remote user credentials (med)

Security Threats

Case Study: GEMSS • Grid-enabled Medical Simulation Services – for clinical and non-clinical applications • Assets: high or medium value – – – hospital network and system integrity (high) privacy of personal data - cf EU D 95/46 or D 2002/58 (high) hospital reputation (med) • Threats: high or medium likelyhood – compromise of remote systems (high) – interception of personal data (high) • Defences: – operate in accordance with legal constraints – architect against too much dependency

Grid Proxies and Trust

Conclusion • Grid risks can be managed at reasonable cost – asset-based risk assessment – appropriate defences (sometimes risk acceptance) • Most security compromises are not Grid-specific – systems compromised by other means – failure to use best practice in network management • Some problems are Grid-related – risk propagation and inter-site dependencies • Mitigation often involves – – – conservative Grid architecture conventional defences response planning and user training

Grid Security Risks Mike Surridge ms@it-innovation. soton. ac. uk GGF 12, 20 Sep 2004, Brussels