Fraud Examination 3 E Chapter 9 Conversion Investigation






![[RM 1]Comp: Right align numbers, align $, and use single and double rules as [RM 1]Comp: Right align numbers, align $, and use single and double rules as](https://slidetodoc.com/presentation_image_h2/db24e557255dc292c3605405bd90244a/image-10.jpg)
- Slides: 10

Fraud Examination, 3 E Chapter 9: Conversion Investigation Methods

Learning Objectives • Explain why finding out how perpetrators convert and spend their stolen funds is important. • Understand how federal, state, and local public records can assist in following the financial “tracks” of suspected perpetrators. • Access information via the Internet to assist in the investigation of a suspected fraud perpetrator. 2

Learning Objectives • Perform net worth calculations on suspected fraud perpetrators and understand how net worth calculations are effective in court and in obtaining confessions. 3

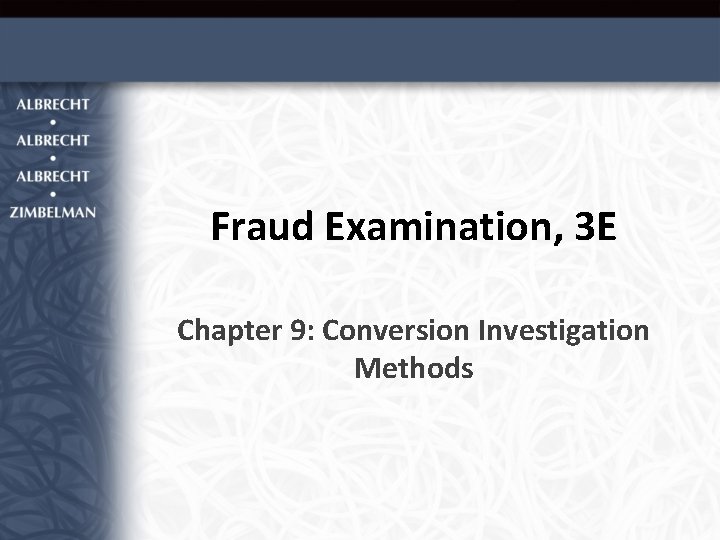
Conversion Searches Performed for two reasons: (1) to determine the extent of embezzlement (2) to gather evidence that can be used in interrogations to obtain a confession 4

Conversion Searches Information can be gleaned from: (1) federal, state, and local agencies and other organizations (2) private sources of information (3) online sources of information (4) using the net worth method of analyzing spending information 5

Conversion Searches Public Records Government Federal State Local 6 Private Sources Utility Records Previous Acquaintances Trash Cover Credit Agencies Financial Institutions Online Databases Subscription Per-search Fee Free Internet Searches Google Alta. Vista Etc.

Private Sources of Information • Utility records (gas, electric, water, garbage, and sewer • Private Acquaintances • “Trashing” • Shredded documents • Original files on computers **Be sure you have the legal rights to gather and use the information 7

Online Databases 8 Examples: • Accurint • Auto. Track. XP • Black Book Online • Choice. Point • EBSCO Publishing • Public. Data • Public Record Finder • SEC’s EDGAR Database • Web Detective

The Net Worth Method Assets – Liabilities = Net Worth – Prior Year’s Net Worth = Net Worth Increase + Living Expenses = Income 9 Income – Funds from Known Sources = Funds from Unknown Sources
![RM 1Comp Right align numbers align and use single and double rules as [RM 1]Comp: Right align numbers, align $, and use single and double rules as](https://slidetodoc.com/presentation_image_h2/db24e557255dc292c3605405bd90244a/image-10.jpg)
[RM 1]Comp: Right align numbers, align $, and use single and double rules as shown. Financial Data for Helen Weeks The Net Worth Method Helen Week’s Example (from Chapter 2) End Year 1 End Year 3 Total assets $206, 000 $212, 000 $246, 000 Total liabilities $100, 000 $ 50, 000 $— Net worth $106, 000 $162, 000 $246, 000 Net worth increase $ 56, 000 $ 84, 000 Plus total expenses 30, 800 32, 800 $ 86, 800 $116, 800 40, 000 42, 000 $ 46, 800 $ 74, 800 Total Income Less known income Income from unknown sources 10 End Year 2