Duke Systems Pocket Hypervisors Opportunities and Challenges Landon







- Slides: 19

Duke Systems Pocket Hypervisors: Opportunities and Challenges Landon Cox Duke University Peter Chen University of Michigan Duke Systems

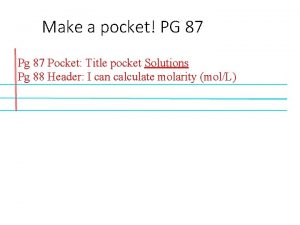
Conventional organization Process Operating System Duke Systems

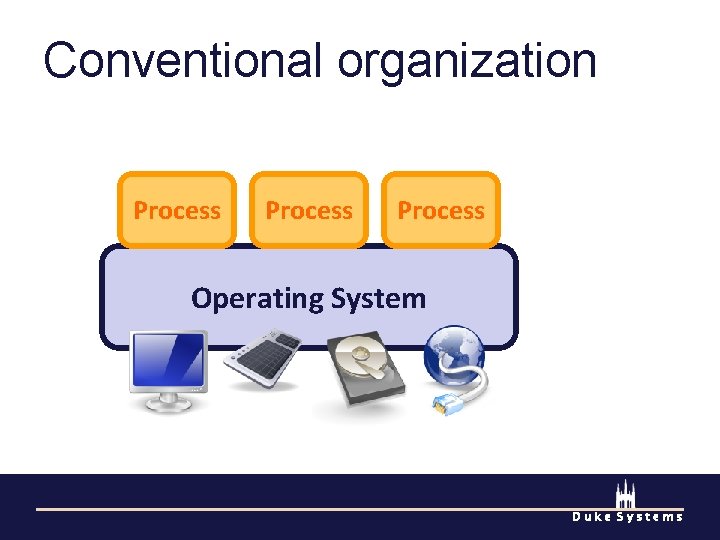
Hypervisor organization Process Guest OS Hypervisor Encapsulation Mediation Isolation Duke Systems

Recent interest in hypervisors Lots of papers/companies the past five years ê Xen, VMware, Re. Virt, Potemkin, etc. On mobile devices? Not so much. ê Some uses of encapsulation (ISR, Soul. Pad) ê No uses of mediation or isolation Why? Hypervisors have been considered impractical ê Insufficient hardware support ê Prohibitive performance overhead Duke Systems

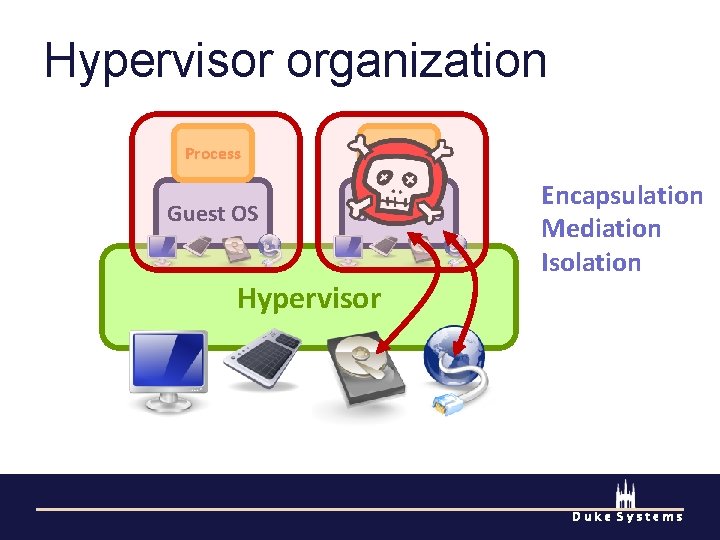
Pocket hypervisors are practical and useful. Hardware support Privilege modes MMU Moore’s Law Security Opportunistic services Duke Systems

Securing commodity devices With PC functions come PC problems ê Mobile malware already exists (Cabir, Skulls) ê Blue. Tooth exploits (Blue. Bug, SNARF) Poses new kinds of threats ê Conversation eavesdropping ê Location privacy compromises ê Gain access to telecom resources trifinite. org, bluestumbler. org Duke Systems

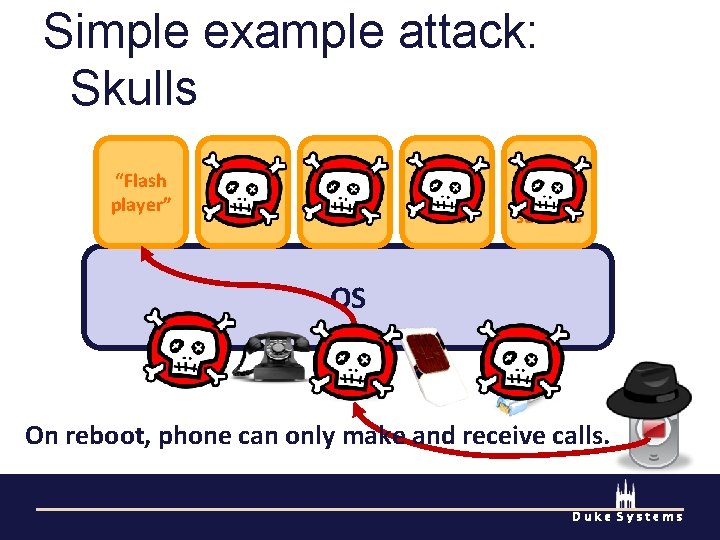
Simple example attack: Skulls “Flash player” Address book Camera Mobile Antivirus Blue Tooth services OS On reboot, phone can only make and receive calls. Duke Systems

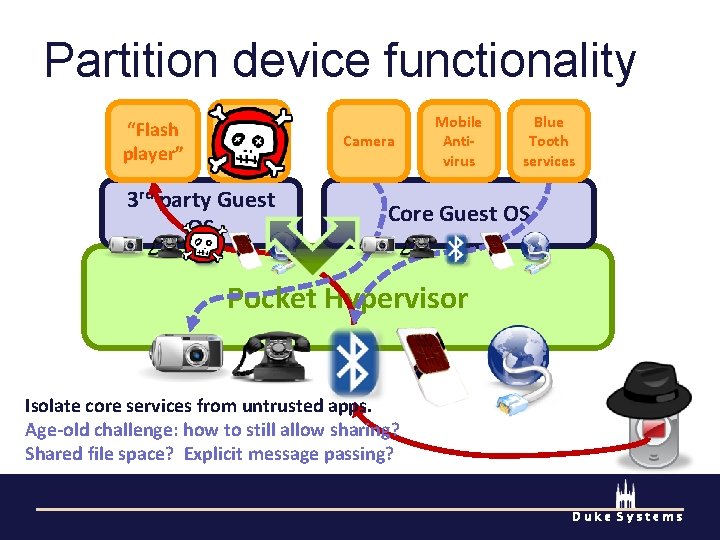
Partition device functionality “Flash player” Blue Tooth services 3 rd party Guest OS Camera Mobile Antivirus Blue Tooth services Core Guest OS Pocket Hypervisor Isolate core services from untrusted apps. Age-old challenge: how to still allow sharing? Shared file space? Explicit message passing? Duke Systems

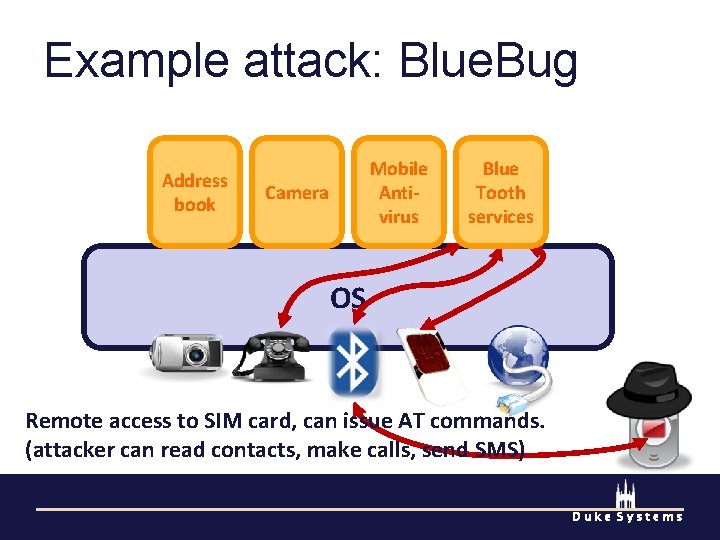
Example attack: Blue. Bug Address book Mobile Antivirus Camera Blue Tooth services OS Remote access to SIM card, can issue AT commands. (attacker can read contacts, make calls, send SMS) Duke Systems

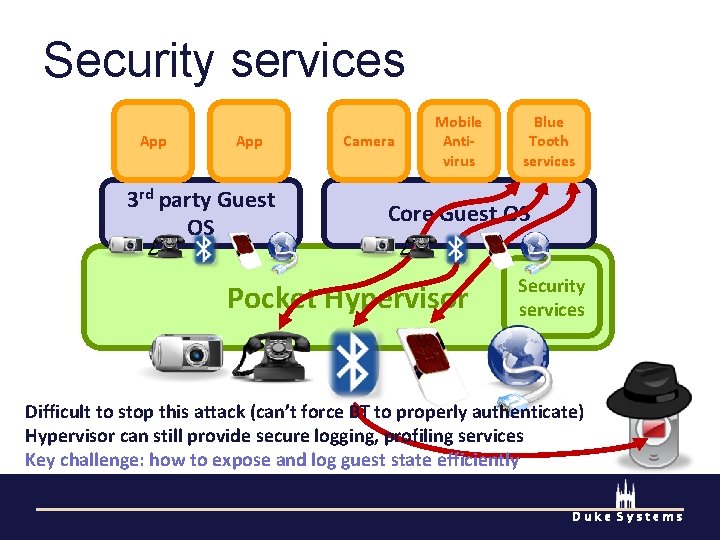
Security services App 3 rd party Guest OS Camera Mobile Antivirus Blue Tooth services Core Guest OS Pocket Hypervisor Security services Difficult to stop this attack (can’t force BT to properly authenticate) Hypervisor can still provide secure logging, profiling services Key challenge: how to expose and log guest state efficiently Duke Systems

Pocket hypervisors are practical and useful. Hardware support Security Opportunistic services Duke Systems

Sensor networks Expose information about environment ê Light, pressure, temperature readings Expands vantage point of owner ê Hundreds of observation points ê Streamed/aggregated to central location Mote price-performance ratio ê Cheap nodes allow large deployments ê (cover large area, overcome failures) ê Powerful nodes allow complex applications Duke Systems

Mobile phones as sensors Expose information about environment ê Network events, MAC addresses, ESSIDs Expands vantage point of owner ê Hundreds of observation points ê Streamed/aggregated to central location Phone price-performance ratio ê Cheap nodes allow large deployments ê (cover large area, overcome mobility) ê Powerful nodes allow complex applications Duke Systems

Opportunistic services COPSE (new project at Duke) ê Concurrent opportunistic sensor environment ê “A thicket of small trees cut for economic purposes. ” Allow execution of untrusted service instances ê Enables mobile testbeds, opportunistic sensor nets ê Hypervisor ensures isolation (performance, energy) Key tension ê Encourage volunteers to participate ê Support useful services Duke Systems

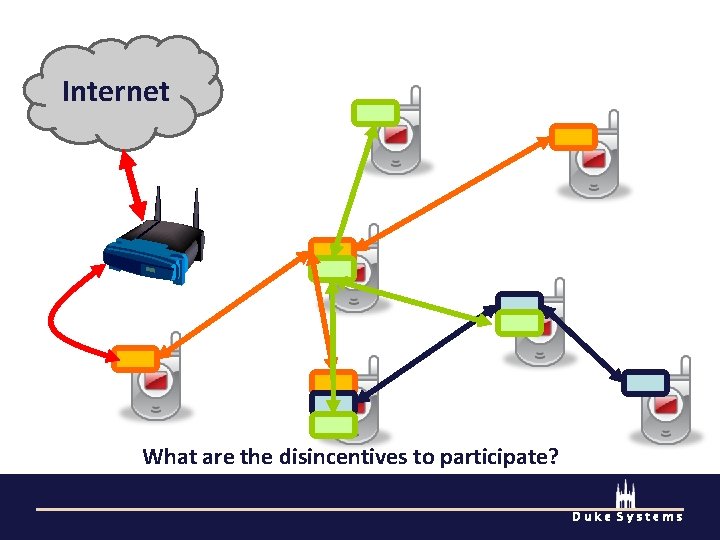
Internet What are the disincentives to participate? Duke Systems

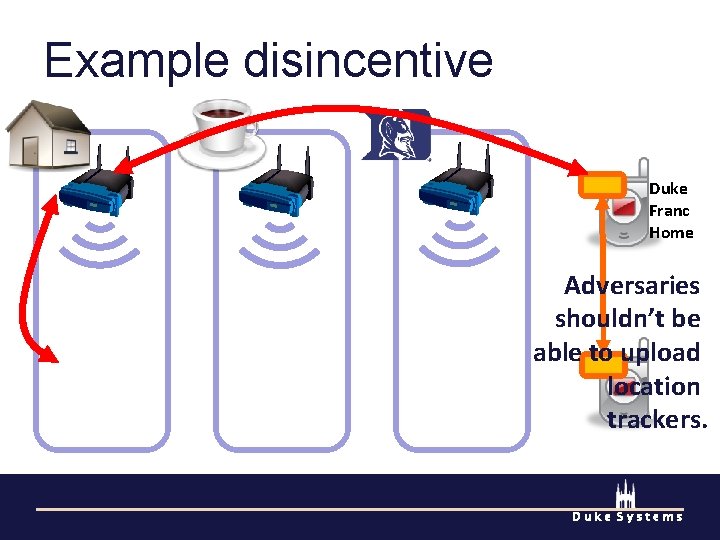
Example disincentive Duke Franc Home Adversaries shouldn’t be able to upload Duke location Franc Home trackers. Duke Systems

Location privacy Could enforce execution regions ê Only execute guests within a physical region ê Requires access to a location service Could “scrub” MAC addresses ê Hypervisor manages device namespace ê Translate names between VM and network Duke Systems

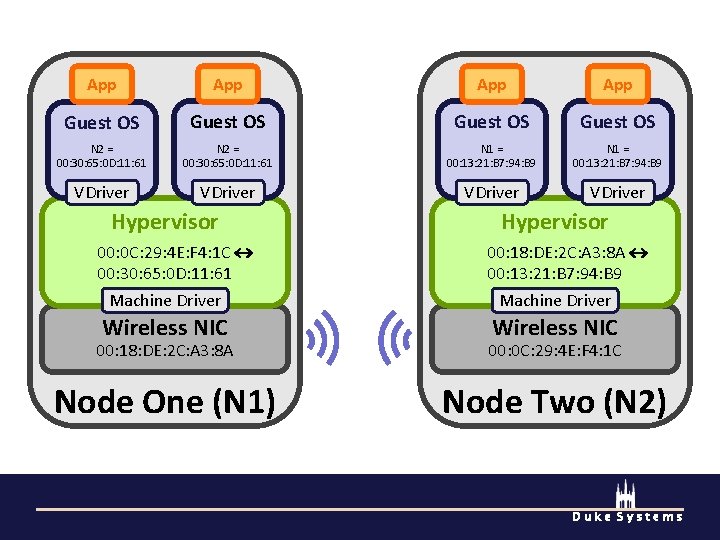
App App Guest OS N 2 = 00: 30: 65: 0 D: 11: 61 N 1 = 00: 13: 21: B 7: 94: B 9 VDriver Hypervisor 00: 0 C: 29: 4 E: F 4: 1 C 00: 30: 65: 0 D: 11: 61 Machine Driver 00: 18: DE: 2 C: A 3: 8 A 00: 13: 21: B 7: 94: B 9 Machine Driver Wireless NIC 00: 18: DE: 2 C: A 3: 8 A 00: 0 C: 29: 4 E: F 4: 1 C Node One (N 1) Node Two (N 2) Duke Systems

Conclusions Pocket hypervisors are practical and useful Practicality ê Commodity devices support for virtualization ê Devices resources are becoming more plentiful Usefulness ê Device security ê Opportunistic services Duke Systems
 Suprabony vs infrabony pocket
Suprabony vs infrabony pocket Risk and challenges of media and information
Risk and challenges of media and information Greater bay area opportunities and challenges
Greater bay area opportunities and challenges Cathy landon
Cathy landon Global management information system
Global management information system Challenges in embedded system
Challenges in embedded system Challenges of emerging trends in operating systems
Challenges of emerging trends in operating systems Cause and effect contents of the dead man's pocket
Cause and effect contents of the dead man's pocket Contents of the dead man's pocket questions and answers
Contents of the dead man's pocket questions and answers How does huck know when his father is back in town
How does huck know when his father is back in town Decision support systems and intelligent systems
Decision support systems and intelligent systems Minecraft pocket edition xbox
Minecraft pocket edition xbox Pocketvna
Pocketvna Oregon nordic club
Oregon nordic club Horizontal
Horizontal Louisiana ppm 49
Louisiana ppm 49 Nfdrs pocket cards
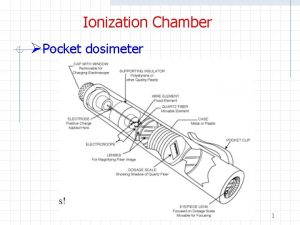
Nfdrs pocket cards Pocket ion chamber
Pocket ion chamber Caldwell technique vestibuloplasty
Caldwell technique vestibuloplasty Suprabony vs infrabony pocket
Suprabony vs infrabony pocket