Do SResilient Secure Aggregation Queries in Sensor Networks

![Previous Work and Our Goal § [Chan’ 06, Chan’ 07, Yang’ 06] § Enables Previous Work and Our Goal § [Chan’ 06, Chan’ 07, Yang’ 06] § Enables](https://slidetodoc.com/presentation_image_h2/a3b797c8630bc74886a245668284c580/image-3.jpg)
- Slides: 5

Do. S-Resilient Secure Aggregation Queries in Sensor Networks Haifeng Yu National University of Singapore http: //www. comp. nus. edu. sg/~yuhf Haifeng Yu (National University of Singapore)

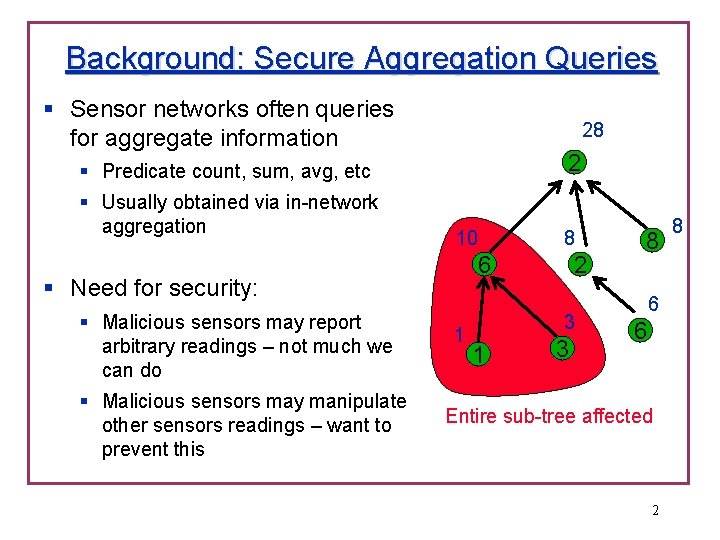
Background: Secure Aggregation Queries § Sensor networks often queries for aggregate information 28 2 § Predicate count, sum, avg, etc § Usually obtained via in-network aggregation 10 6 § Need for security: § Malicious sensors may report arbitrary readings – not much we can do § Malicious sensors may manipulate other sensors readings – want to prevent this 8 1 2 3 1 3 8 6 6 Entire sub-tree affected 2 8
![Previous Work and Our Goal Chan 06 Chan 07 Yang 06 Enables Previous Work and Our Goal § [Chan’ 06, Chan’ 07, Yang’ 06] § Enables](https://slidetodoc.com/presentation_image_h2/a3b797c8630bc74886a245668284c580/image-3.jpg)
Previous Work and Our Goal § [Chan’ 06, Chan’ 07, Yang’ 06] § Enables the detection of an incorrect result – user will then reject the result § But, attacker can keep corrupting the result and cause result to be rejected Do. S attack! § Analogy: Safety without liveness … § Our goal: Secure and highly-available aggregation queries § Tolerate the attacker instead of just detect it § This talk will use predicate count as an example… Haifeng Yu (National University of Singapore) 3

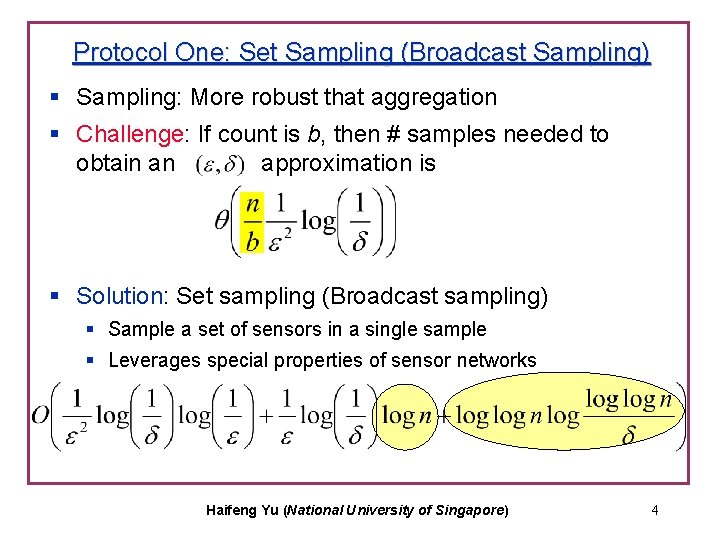
Protocol One: Set Sampling (Broadcast Sampling) § Sampling: More robust that aggregation § Challenge: If count is b, then # samples needed to obtain an approximation is § Solution: Set sampling (Broadcast sampling) § Sample a set of sensors in a single sample § Leverages special properties of sensor networks Haifeng Yu (National University of Singapore) 4

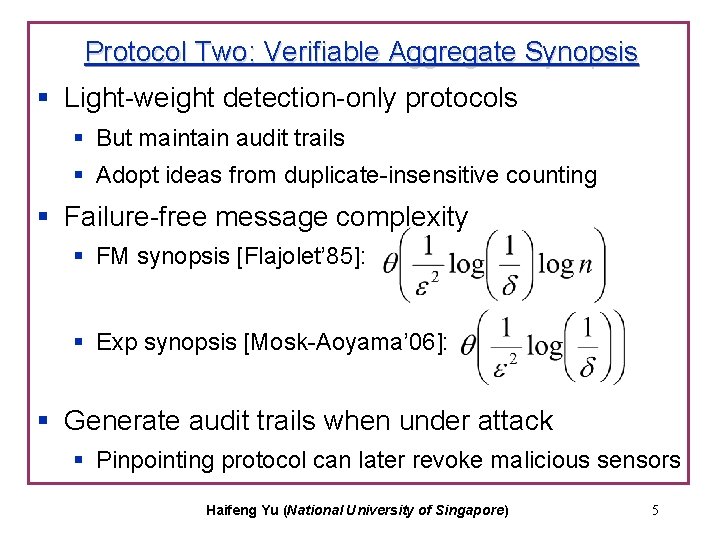
Protocol Two: Verifiable Aggregate Synopsis § Light-weight detection-only protocols § But maintain audit trails § Adopt ideas from duplicate-insensitive counting § Failure-free message complexity § FM synopsis [Flajolet’ 85]: § Exp synopsis [Mosk-Aoyama’ 06]: § Generate audit trails when under attack § Pinpointing protocol can later revoke malicious sensors Haifeng Yu (National University of Singapore) 5