CSE 331 Introduction to Networks and Security Lecture













- Slides: 17

CSE 331: Introduction to Networks and Security Lecture 15 Fall 2002

Announcements • Midterm graded – Average: 65 – Solutions available on the web – Pick up after class or during office hours Today • Introduction Computer Security CSE 331 Fall 2002 2

Real World Security • Value: what is being protected? – Things that have worth • Locks, walls, safes, fences, … – Scaled for what they’re protecting against (threats) – Minimal interference (or else they aren’t used) • Police & Courts – Follow up after an attack/violation – Perhaps most important! CSE 331 Fall 2002 3

Real World: Risk Managment • People pay for security based on perceived needs • Trade off security vs. – – Convenience / ease of use Functionality Efficiency Cost • Security is holistic: – Attacks go for the weakest link CSE 331 Fall 2002 4

Security Terminology • Vulnerability – Weakness that can be exploited in a system • Attack – Method for exploiting vulnerability • Threat – A motivated, capable adversary that would mount attacks CSE 331 Fall 2002 5

Example Vulnerabilities • Poorly chosen passwords • Software bugs – unchecked array access (buffer overflow attacks) • Automatically running active content: macros, scripts, Java programs • Open ports: telnet, mail • Incorrect configuration – file permissions – administrative privileges • • Untrained users/system administrators Trap doors (intentional security holes) Unencrypted communication Limited Resources (i. e. TCP connections) CSE 331 Fall 2002 6

Example Attacks • Password Crackers • Viruses: – ILove. You (VBscript virus), Melissa (Word macro virus) • Worms – Code Red: Port 80 (HTTP), Buffer overflow in IIS (Internet/Indexing Service) • Trojan Horses • Root kits, Back Orifice, SATAN • Social Engineering: – “Hi, this is Joe from systems, can you tell me your password? ” • Packet sniffers: Ethereal • Denial of service: TCP SYN packet floods CSE 331 Fall 2002 7

Range of Threats • Concerted Attack by a Foreign Government – Money & Resources – Strong Motivation • … • Teenage Hacker – No money – ? Motivation • Note: the range above doesn’t necessarily represent a range of sophistication! CSE 331 Fall 2002 8

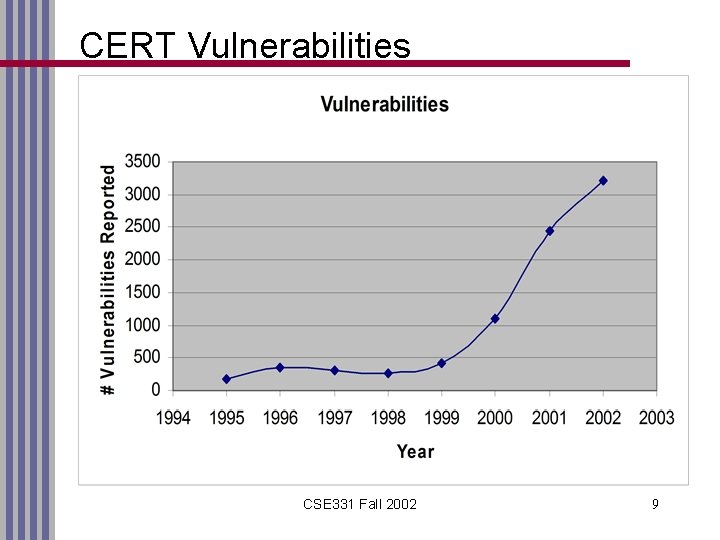
CERT Vulnerabilities CSE 331 Fall 2002 9

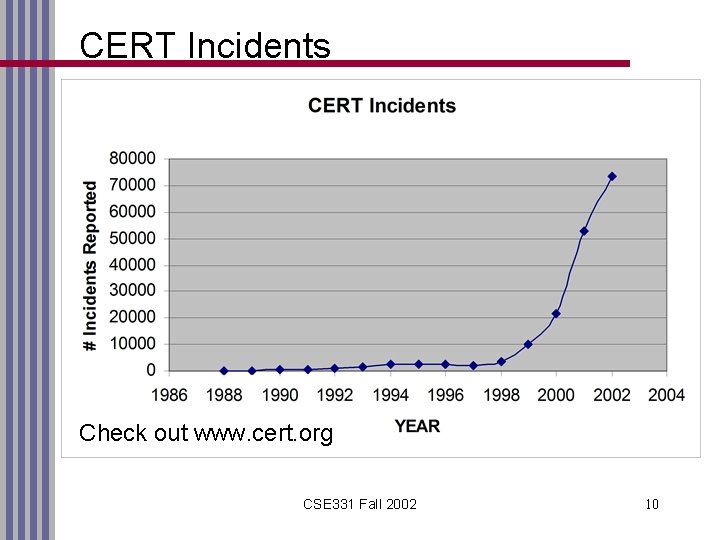
CERT Incidents Check out www. cert. org CSE 331 Fall 2002 10

Questions for Computer Security • What are we protecting? – What has value? – What are its characteristics? • What tools do we have to use? – Hardware – Software – Knowledge • How do we effectively use those tools? – What principles apply? – How do we know what we want to achieve? – How do we know what we’ve done? CSE 331 Fall 2002 11

Quality 1: Confidentiality Data • Keep data or actions secret. • Related to: Privacy, Anonymity, Secrecy • Examples: – – Pepsi secret formula Medical information Personal records (e. g. credit card information) Military secrets CSE 331 Fall 2002 12

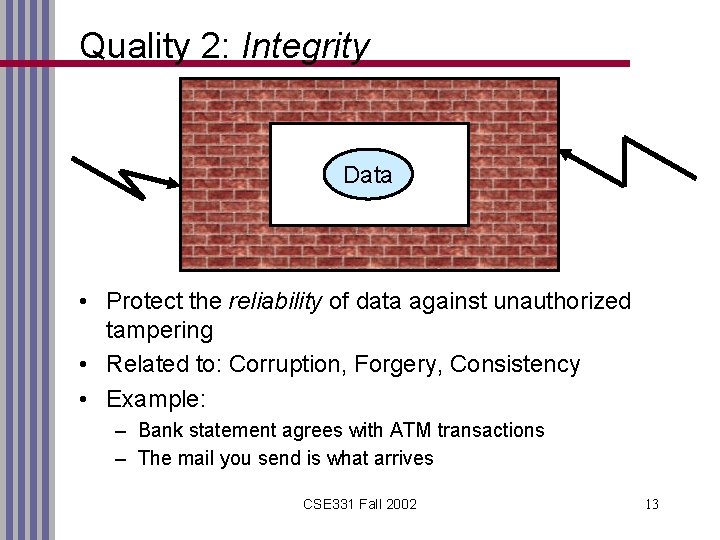
Quality 2: Integrity Data • Protect the reliability of data against unauthorized tampering • Related to: Corruption, Forgery, Consistency • Example: – Bank statement agrees with ATM transactions – The mail you send is what arrives CSE 331 Fall 2002 13

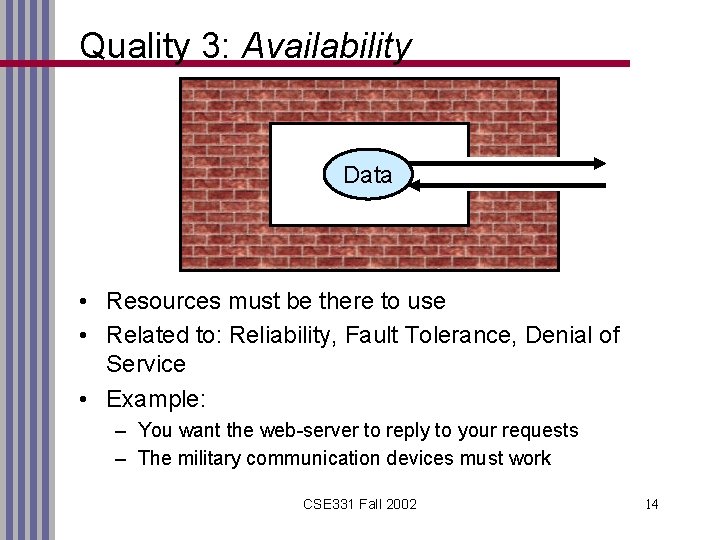
Quality 3: Availability Data • Resources must be there to use • Related to: Reliability, Fault Tolerance, Denial of Service • Example: – You want the web-server to reply to your requests – The military communication devices must work CSE 331 Fall 2002 14

What tools are there? • Authorization mechanisms – Access control – Specifies who is allowed to do what. • Authentication mechanisms – A principal is an entity that has a stake in the security of a system – Authentication identifies principals – Examples: User identifiers & Passwords, secret keys • Audit mechansisms – Monitoring, or logging security-relevant activities – Permits follow-up after a security breech • Au = Aurum = “Gold standard” CSE 331 Fall 2002 15

Example tools • Cryptography – Protects confidentiality & Integrity – Can be used for authentication • Firewalls, access control monitors – Authorization mechanisms • OS Kernels – Resource allocation/monitoring • Replication – Provides fault tolerance • Java bytecode verifier – Protects against faulty/malicious code CSE 331 Fall 2002 16

Security Policy • Set of security requirements for a system – Takes into account trade-offs of value vs. functionality – Changes over time – Depends on context • Varying degrees of formality – Informal: Don’t reveal my credit card information. – Formal: Government’s “Orange Book” • National Computer Security Center (1988) • Trusted Computer System Evaluation Criteria (TCSEC) • Classes D –- A 1 CSE 331 Fall 2002 17