CSCE 548 Secure Software Development Use Cases Misuse










- Slides: 11

CSCE 548 Secure Software Development Use Cases Misuse Cases

Reading Required: – Mc. Graw: Chapter 8 – I. Alexander, Misuse Cases: Use Cases with Hostile Intent, IEEE Software, vol. 20, no. 1, pp. 58 -66, Jan. /Feb. 2003. http: //www. computer. org/portal/web/csdl/doi/10. 1109/MS. 2003. 11 59030 Recommended” – Pauli and Xu, Misuse Case-Based Design and Analysis of Secure Software Architecture, http: //cs. ndsu. edu/~dxu/publications/paulixu-ITCC 05. pdf – Steven and Peterson, Defining Misuse within the Development Process, http: //csdl. computer. org/dl/mags/sp/2006/06/j 6081. pdf l Next lecture: – Reliability CSCE 548 - Farkas 2

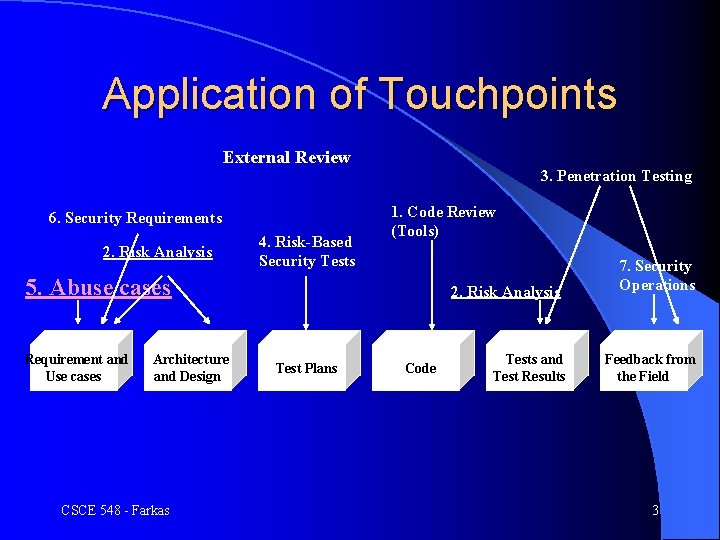
Application of Touchpoints External Review 6. Security Requirements 2. Risk Analysis 4. Risk-Based Security Tests 3. Penetration Testing 1. Code Review (Tools) 5. Abuse cases Requirement and Use cases Architecture and Design CSCE 548 - Farkas 2. Risk Analysis Test Plans Code Tests and Test Results 7. Security Operations Feedback from the Field 3

Misuse Cases Software development: making software do something – Describe features and functions – Everything goes right l Need: security, performance, reliability – Service level agreement – legal binding l How to model non-normative behavior in use cases? – Think like a bad guy l CSCE 548 - Farkas 4

Software Vendor Accountability SLA for specific, measurable criteria: l Proper implementation of security features l Looking for known security flaws and confirming that they are not present l Passing third party validation and verification l Use of source code analysis tools CSCE 548 - Farkas 5

Checking for Known Vulnerabilities l Need tool l Possible attacks and attack types l How the software behaves if something goes WRONG l What motivates an attacker? CSCE 548 - Farkas 6

Misuse Cases l Extends use case diagrams l Represent actions the system should prevent l Represent together – Desired functionalities – Undesired actions emergent property must be built in from the ground up l Making explicit trade offs l Security: CSCE 548 - Farkas 7

Misuse Cases l Analyze system design – Assumptions – Failure of assumptions – Attack patterns l Software and requirements that is used also going to be attacked l What can a bad guy do and how to react to malicious use CSCE 548 - Farkas 8

Misuse Case Development Team work – software developers and security experts l Identifying and documenting threats l Creating anti-requirements: how the system can be abused l Creating attack model l – Select attack pattern relevant to the system – Include anyone who can gain access to the system CSCE 548 - Farkas 9

l Link to slides on Ian Alexander’s paper on Misuse Cases: Use Cases with Hostile Intent, www. cse. msstate. edu/~allen/cse 8990 sp 07/Lectures/Presentations/cln 11_021507. ppt CSCE 548 - Farkas 10

Next Class l Software Reliability l B. Littlewood, P. Popov, L. Strigini, "Modelling software design diversity - a review", ACM Computing Surveys, Vol. 33, No. 2, June 2001, pp. 177 -208, http: //portal. acm. org/citation. cfm? doid=384 192. 384195 CSCE 548 - Farkas 11