Certificate Revocation and Certificate Update Source IEEE Journal









- Slides: 11

Certificate Revocation and Certificate Update • Source: IEEE Journal on Selected Areas in Communications, Vol. 18, No. 4, April. 2000. • Authors: Moni Naor and Kobbi Nissim • Date: 2001/6/21 • Speaker: Chi-Yien Chung 1

The Model • Three main types of parties involved 1. Certification Authority (CA) --- A trusted party, responsible for certificate issuing and updating --- CA may revoke a certificate prior to its expiration date 2

The Model 2. Directory: --- serves as a database efficiently accessible by users 3. Users: --- could query the validity of other users’ certificates 3

Related Work • Certificate Revocation List (CRL) --- contains : 1. Serial number 2. Timestamp 3. CA’s signature --- simplicity --- need great efforts to manage 4

The Proposed Scheme 1. CA operations: a. Creating certificates b. Initialization --- the CA creates the 2 -3 tree, the leaves are the set of initially revoked certificates; internal node value are the hash value of its children 5

The Proposed Scheme --- CA sends to the directory: 1. The sorted list of revoked certificates serial numbers 2. The tree root value 3. The tree height 4. A time stamp 6

The Proposed Scheme c. Updating: --- inserting/ deleting certificates --- CA sends a list of serial numbers of the updated certificates, new root value, tree height, and time stamp to directory. 7

The Proposed Scheme 2. Directory Operations: a. Initialization: --- reconstruct the 2 -3 tree --- verify the root value, time stamp, tree height, and CA’s signature b. Response to CA’s update 8

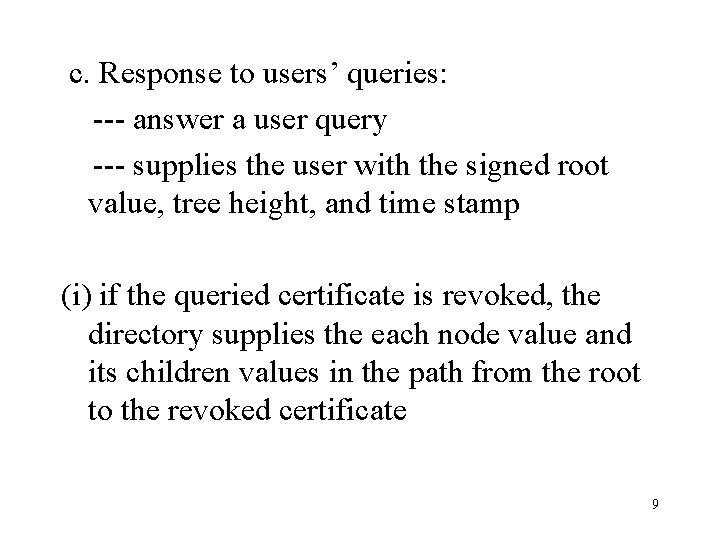
c. Response to users’ queries: --- answer a user query --- supplies the user with the signed root value, tree height, and time stamp (i) if the queried certificate is revoked, the directory supplies the each node value and its children values in the path from the root to the revoked certificate 9

(ii) if the queried certificate is not revoked, the directory provides the user the paths to two neighboring leaves, l 1 and l 2 , s. t l 1 < s < l 2 3. The user operations --- Verify the query results by applying the hash function 10

Evaluation • Easy to check and prove whether a certain certificate is revoked. • Low communication costs for list updates. • The path serves as a proof for the certificate validity. 11