You need Secure Auditor if You are facing












- Slides: 14


You need Secure Auditor if ! • You are facing compliance challenges like PCI-DSS, HIPPA, SOX, GLBA, FISMA, Visa and Master Card standards etc. • You are following SANS, CIS, and ISACA guidelines. • You are assessing risk and want to prioritize threats according to their associated risk level. • You believe that Vulnerabilities, Passwords, Denial of Service Issues, Patches, Configurations and Fine Grained Auditing are extremely critical issues for an organization. • You want to get maximum return on your each dollar consumed.

Secure Auditor is a Unified Digital Risk Management Solution

Secure Auditor offers 45 free Embedded Security Tools Free Scanning & Asset Identification Automated Database Audit Automated Windows Audit Automated Cisco Routers Audit Log & Inventory Management Audit Scheduler 80 plus Embedded Reports

Secure Auditor offers 4 modules

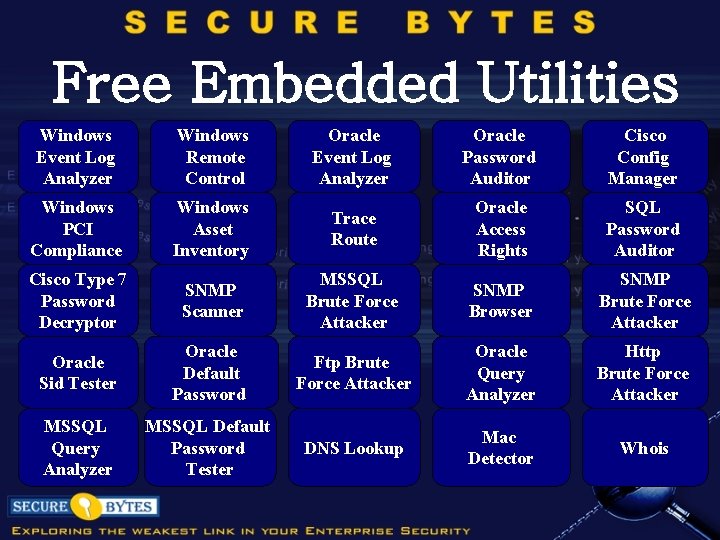
Free Embedded Utilities Windows Event Log Analyzer Windows Remote Control Oracle Event Log Analyzer Oracle Password Auditor Cisco Config Manager Windows PCI Compliance Windows Asset Inventory Trace Route Oracle Access Rights SQL Password Auditor Cisco Type 7 Password Decryptor SNMP Scanner MSSQL Brute Force Attacker SNMP Browser SNMP Brute Force Attacker Oracle Sid Tester Oracle Default Password Ftp Brute Force Attacker Oracle Query Analyzer Http Brute Force Attacker MSSQL Query Analyzer MSSQL Default Password Tester DNS Lookup Mac Detector Whois

Secure Auditor performs Security Assessment in 5 easy steps

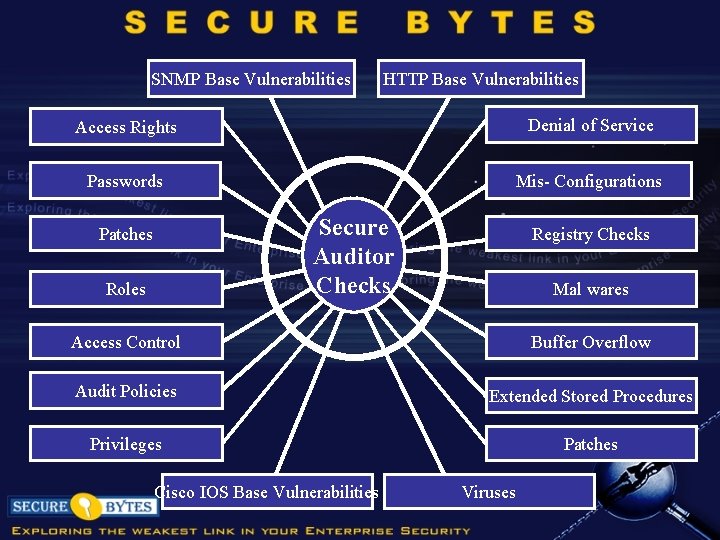
SNMP Base Vulnerabilities HTTP Base Vulnerabilities Access Rights Denial of Service Passwords Mis- Configurations Secure Auditor Checks Patches Roles Registry Checks Mal wares Access Control Buffer Overflow Audit Policies Extended Stored Procedures Privileges Patches Cisco IOS Base Vulnerabilities Viruses

Secure Auditor delivers! Convenience Ease of Use Vulnerability Specification Digital Risk Management

Customer Earn! Satisfaction Productivity Economies of Scale Highest Return on Investment

User Requirements • Operating System Windows XP and above • Processor Intel® Core™ i 3 and above • Memory Ram 1 GB and above

Support • Online Support through Text messages, Web ex, Email. • Our technical representatives are always available for your queries via telephone. • User Guides, Manuals, Interactive Demos, Tutorials etc.

Contact Information Visit our website URL: http: //www. secure-bytes. com For Sales Inquires please contact E mail: sales@secure-bytes. com For Partner Inquires please contact E mail: partner@secure-bytes. com For further Information please contact E mail: info@secure-bytes. com

Thank You