XORed visual secret sharing scheme with robust and

XOR-ed visual secret sharing scheme with robust and meaningful shadows based on QR codes Source: Multimedia Tools and Applications, vol. 79, no. 910, pp. 5719 -5741, 2019. Authors: Tan, Longdan. Lu, Yuliang. Yan, Xuehu. Liu, Lintao. Zhou, Xuan Speaker: Huang Peng-Cheng Date: 9/5/2021 1

Outline • Introduction • Related works • Proposed scheme • Simulation results • Conclusions • Comments 2
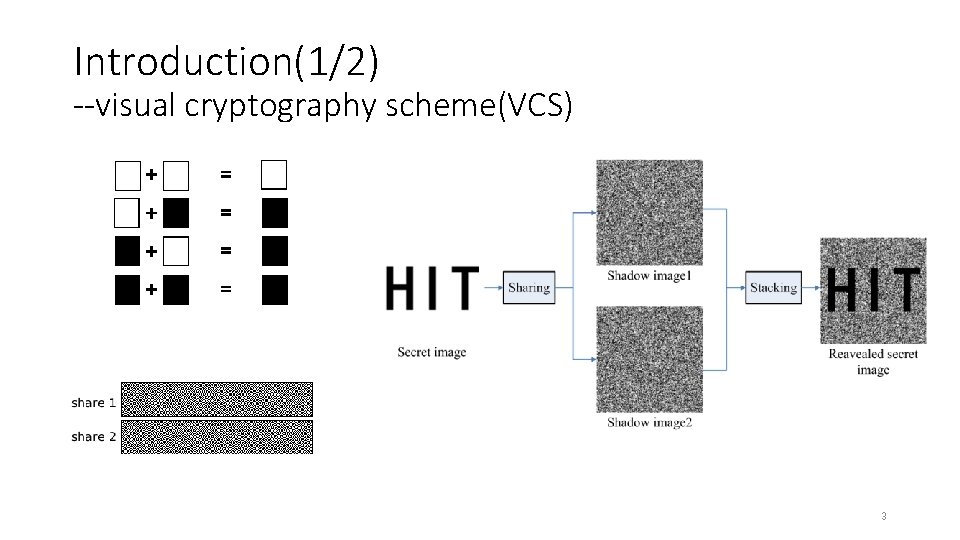
Introduction(1/2) --visual cryptography scheme(VCS) 3
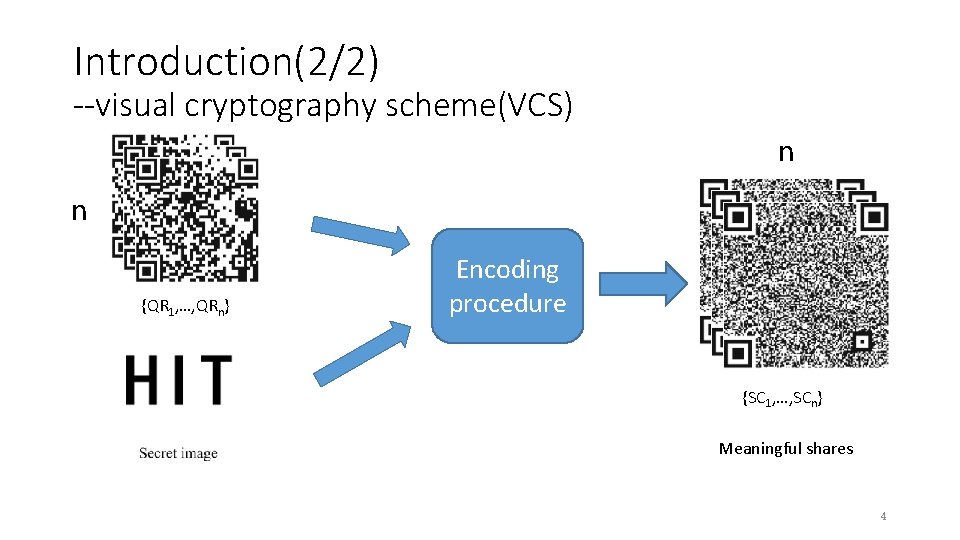
Introduction(2/2) --visual cryptography scheme(VCS) n n {QR 1, …, QRn} Encoding procedure {SC 1, …, SCn} Meaningful shares 4
Related works(1/6) –Wang et al. ’s scheme Wang, G. , Liu, F. , Yan, W. Q. : 2 D barcodes for visual cryptography. Multimed. Tools Appl. 75, 1– 19 (2016)
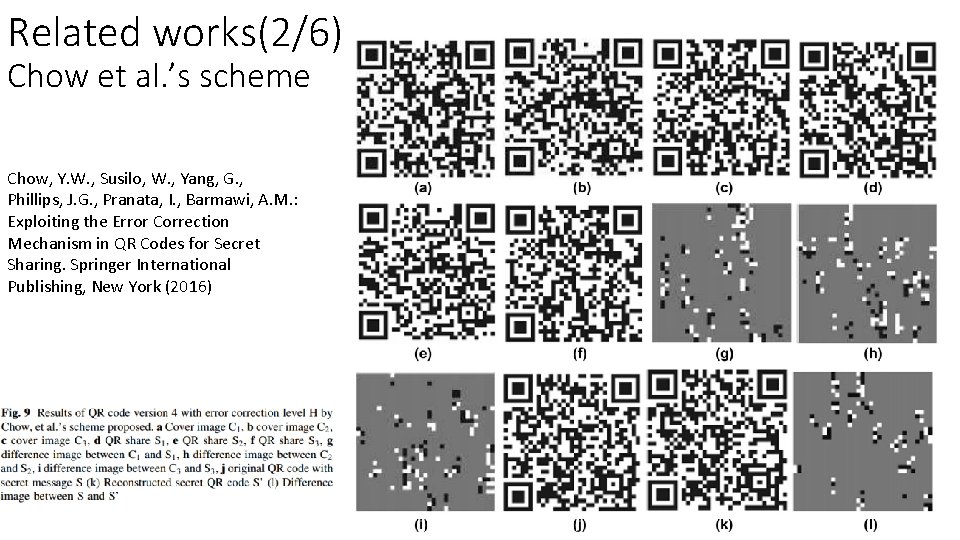
Related works(2/6) Chow et al. ’s scheme Chow, Y. W. , Susilo, W. , Yang, G. , Phillips, J. G. , Pranata, I. , Barmawi, A. M. : Exploiting the Error Correction Mechanism in QR Codes for Secret Sharing. Springer International Publishing, New York (2016)
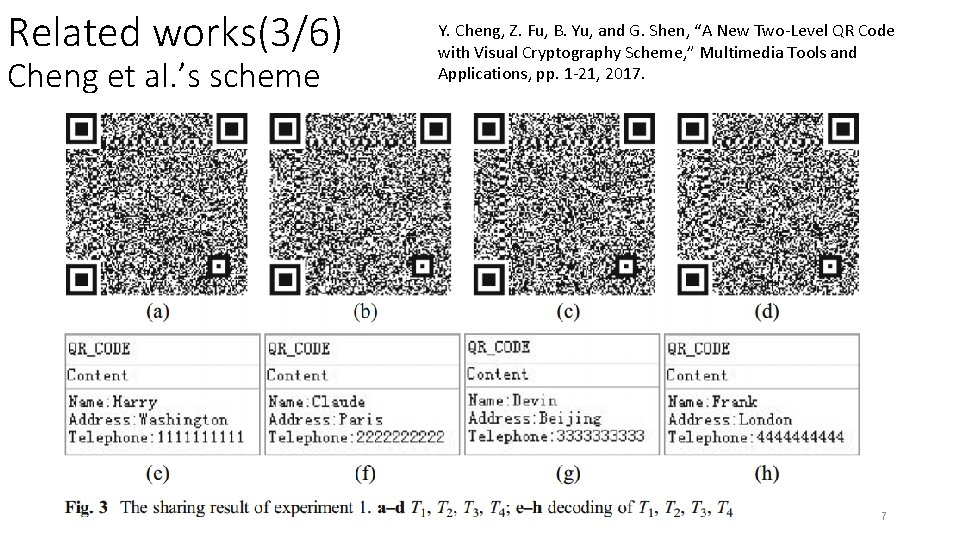
Related works(3/6) Cheng et al. ’s scheme Y. Cheng, Z. Fu, B. Yu, and G. Shen, “A New Two-Level QR Code with Visual Cryptography Scheme, ” Multimedia Tools and Applications, pp. 1 -21, 2017. 7
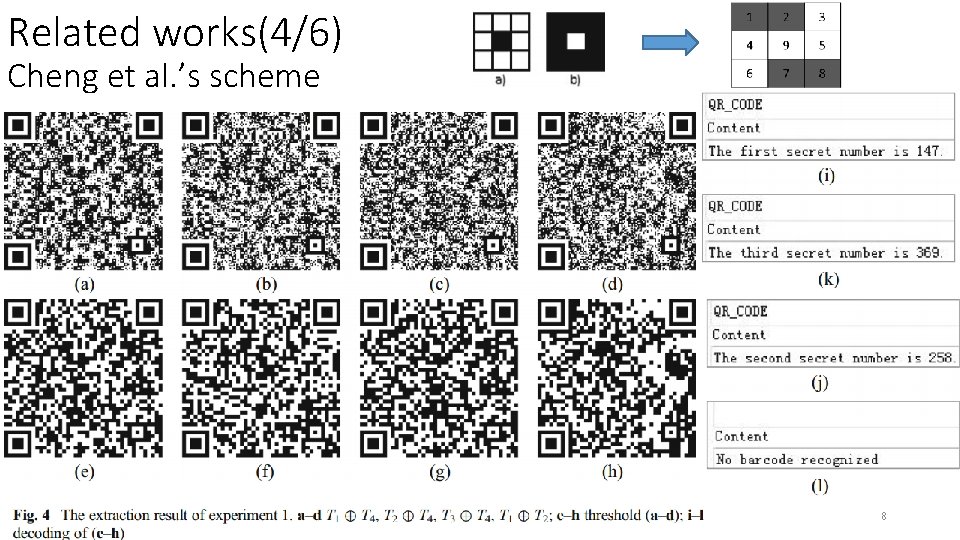
Related works(4/6) Cheng et al. ’s scheme 8
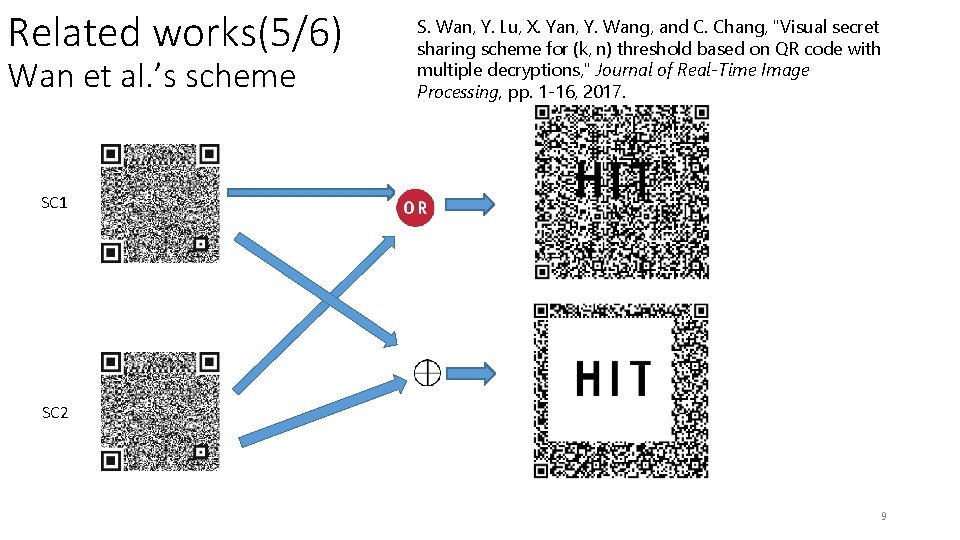
Related works(5/6) Wan et al. ’s scheme S. Wan, Y. Lu, X. Yan, Y. Wang, and C. Chang, "Visual secret sharing scheme for (k, n) threshold based on QR code with multiple decryptions, " Journal of Real-Time Image Processing, pp. 1 -16, 2017. SC 1 SC 2 9
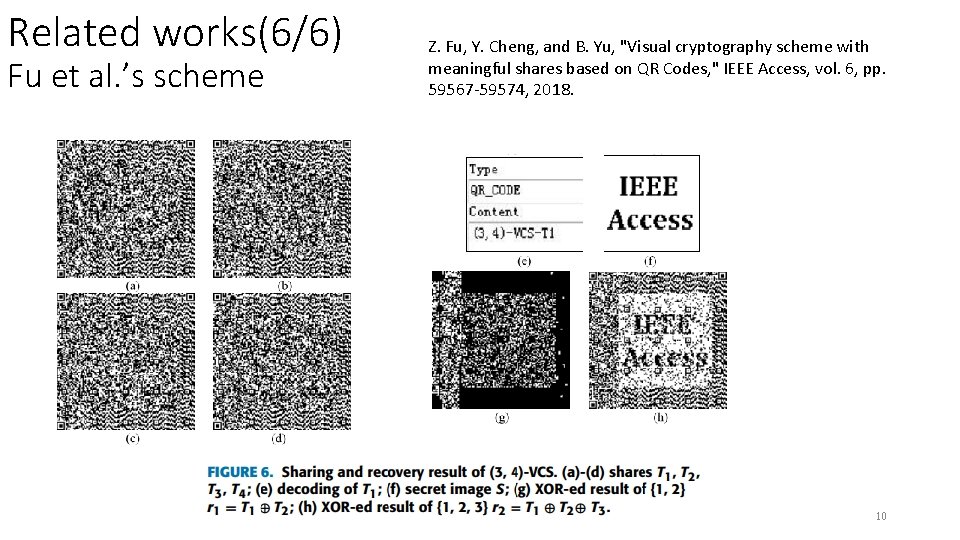
Related works(6/6) Fu et al. ’s scheme Z. Fu, Y. Cheng, and B. Yu, "Visual cryptography scheme with meaningful shares based on QR Codes, " IEEE Access, vol. 6, pp. 59567 -59574, 2018. 10
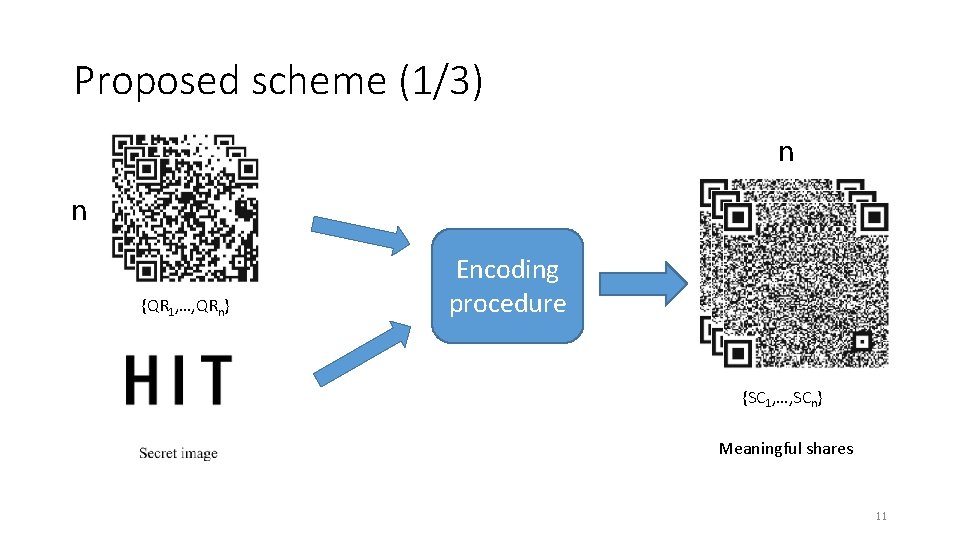
Proposed scheme (1/3) n n {QR 1, …, QRn} Encoding procedure {SC 1, …, SCn} Meaningful shares 11
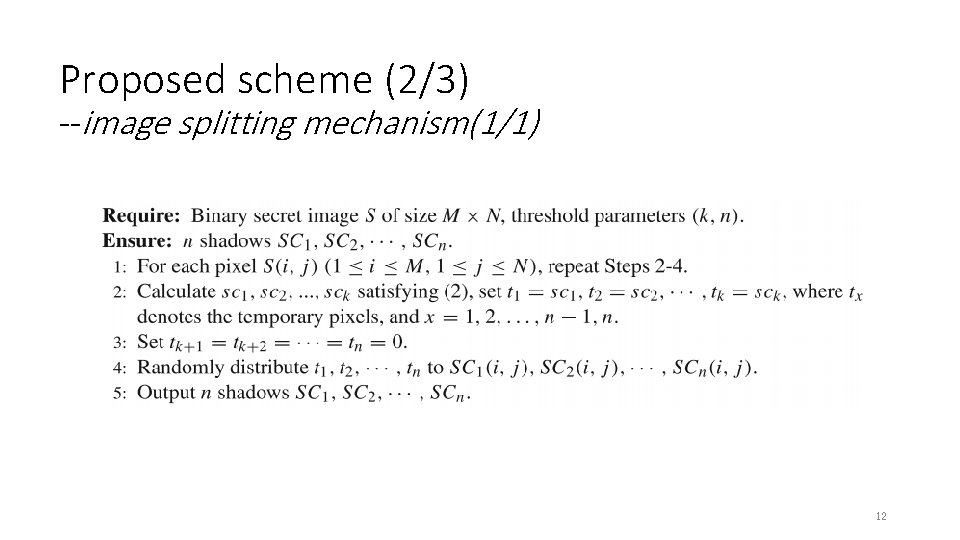
Proposed scheme (2/3) --image splitting mechanism(1/1) 12
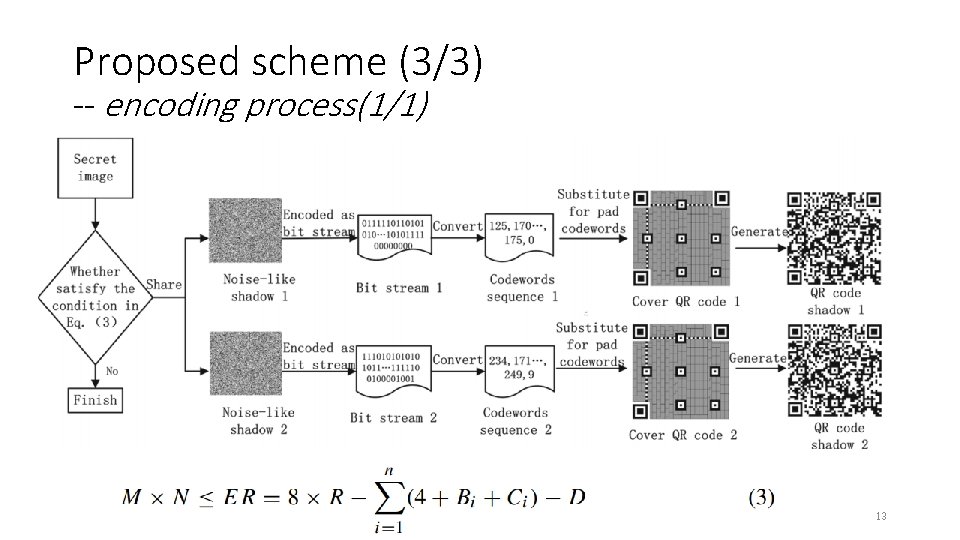
Proposed scheme (3/3) -- encoding process(1/1) 13
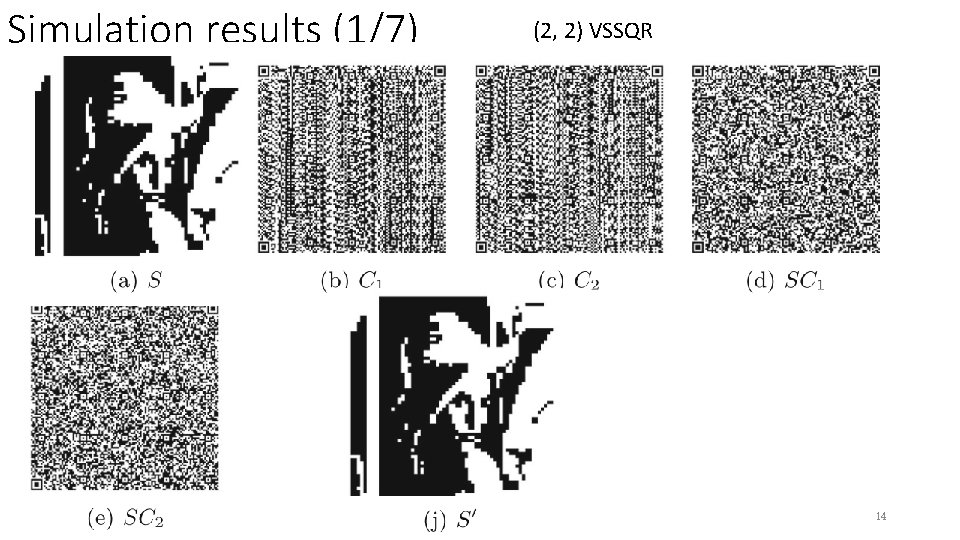
Simulation results (1/7) (2, 2) VSSQR 14
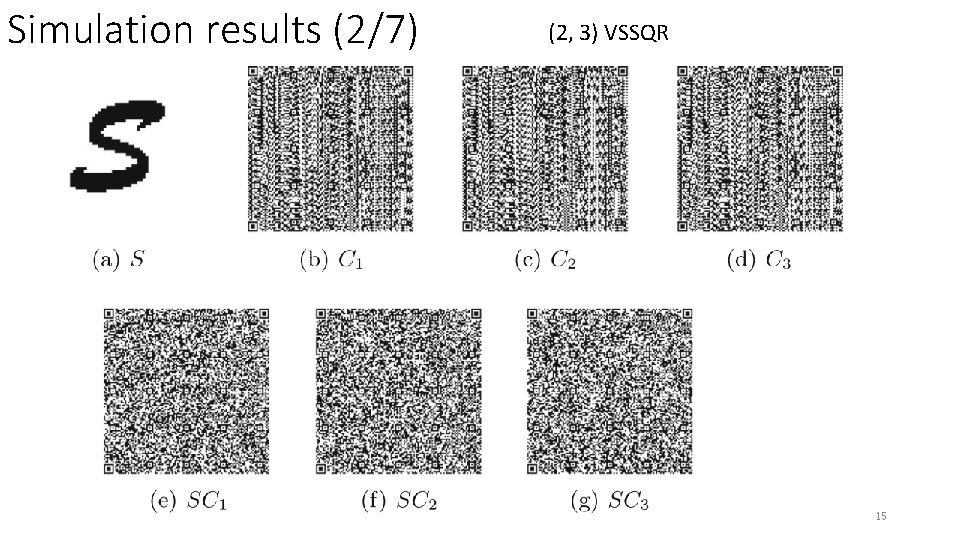
Simulation results (2/7) (2, 3) VSSQR 15
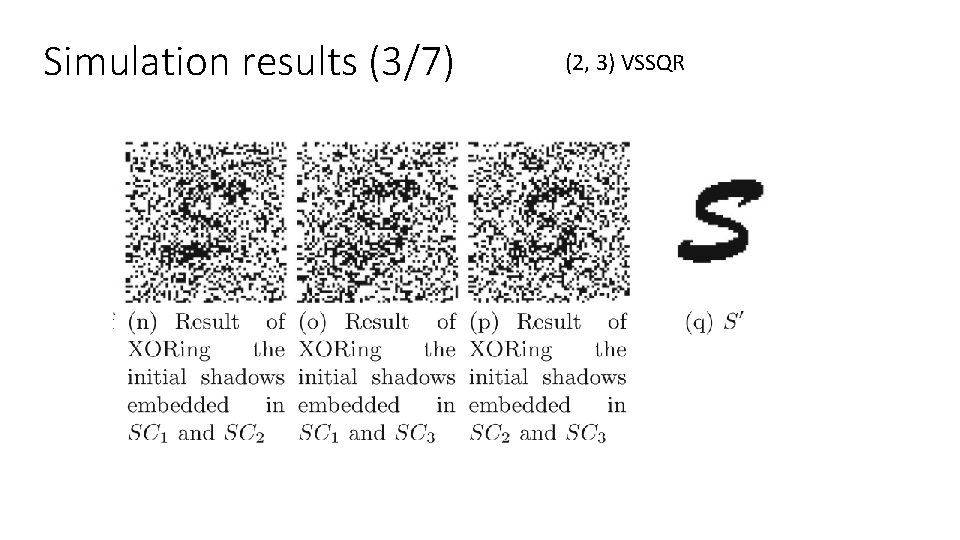
Simulation results (3/7) (2, 3) VSSQR
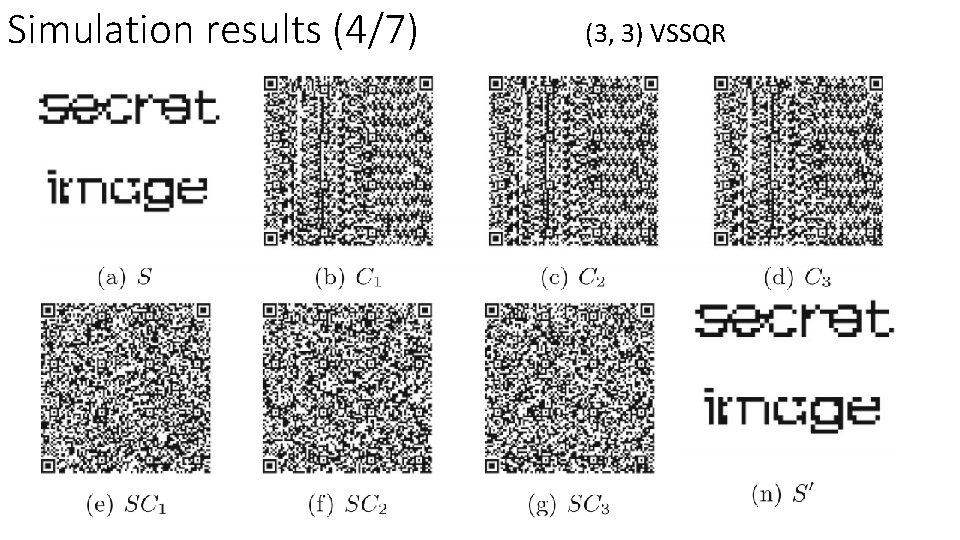
Simulation results (4/7) (3, 3) VSSQR 17

Simulation results (5/7) Robustness test(1/2)
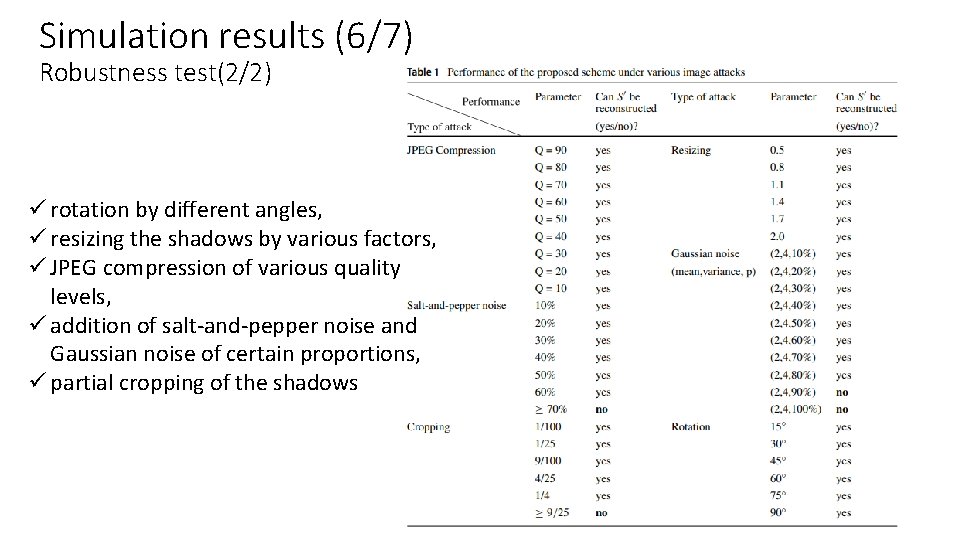
Simulation results (6/7) Robustness test(2/2) ü rotation by different angles, ü resizing the shadows by various factors, ü JPEG compression of various quality levels, ü addition of salt-and-pepper noise and Gaussian noise of certain proportions, ü partial cropping of the shadows
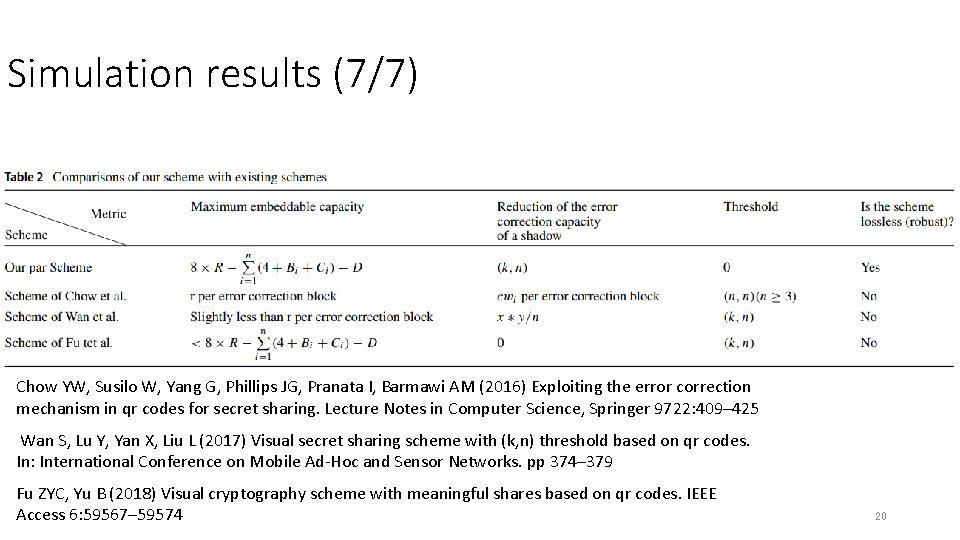
Simulation results (7/7) Chow YW, Susilo W, Yang G, Phillips JG, Pranata I, Barmawi AM (2016) Exploiting the error correction mechanism in qr codes for secret sharing. Lecture Notes in Computer Science, Springer 9722: 409– 425 Wan S, Lu Y, Yan X, Liu L (2017) Visual secret sharing scheme with (k, n) threshold based on qr codes. In: International Conference on Mobile Ad-Hoc and Sensor Networks. pp 374– 379 Fu ZYC, Yu B (2018) Visual cryptography scheme with meaningful shares based on qr codes. IEEE Access 6: 59567– 59574 20

Conclusions • Meaningful shares => the decodable of QR code. • High robustness • Error correction capacity is preserved. 21

Comments(1/1) • It is not a traditional way to reveal the secret image. 22
- Slides: 22