XIA Network Deployments Dave Andersen David Eckhardt Sara








- Slides: 22

XIA: Network Deployments Dave Andersen, David Eckhardt, Sara Kiesler, Jon Peha, Adrian Perrig, Srini Seshan, Marvin Sirbu, Peter Steenkiste, Hui Zhang Carnegie Mellon University Aditya Akella, University of Wisconsin John Byers, Boston University FIA PI Meeting March 2013, Salt Lake City 1

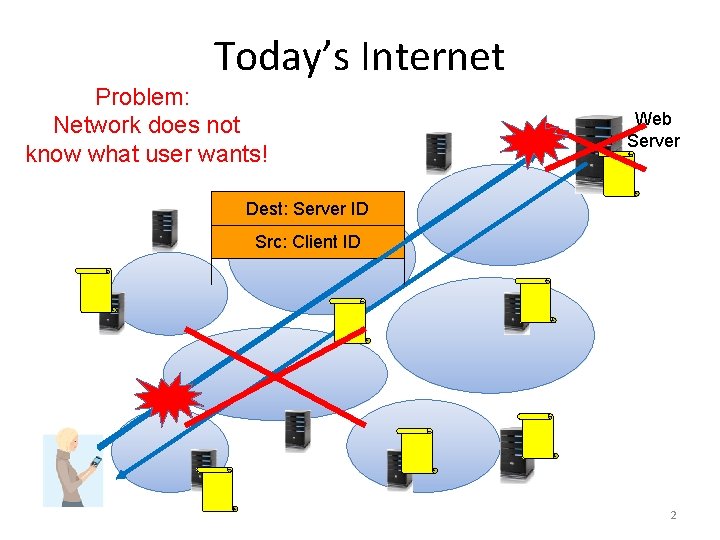
Today’s Internet Problem: Network does not know what user wants! Web Server Dest: Server ID Src: Client ID 2

Today’s Internet S S 3

XIA Vision We envision a future Internet that: • Is trustworthy – Security broadly defined is a compelling research challenge • Supports long-term evolution of usage models – Including host-host, content retrieval, services, … • Supports long term technology evolution – Not just for link technologies, but also for storage and computing capabilities in the network and end-points • Provides benefits for a multiplicity of stakeholders – Despite differences in roles, goals and incentives 4

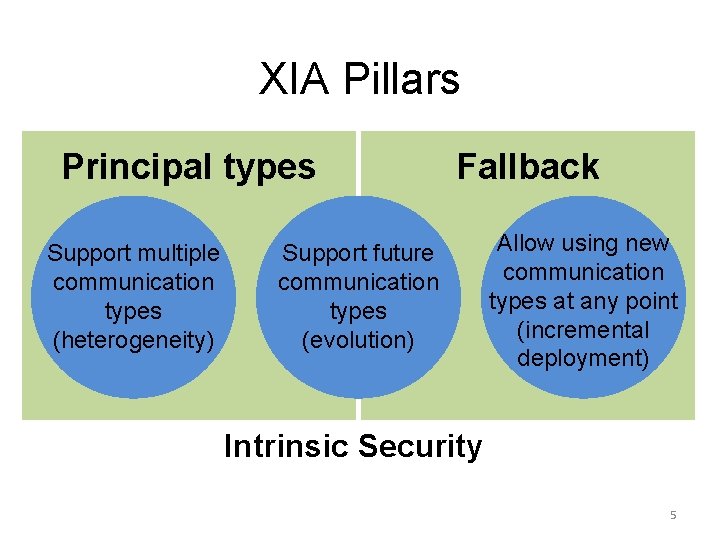
XIA Pillars Principal types Support multiple communication types (heterogeneity) Fallback Support future communication types (evolution) Allow using new communication types at any point (incremental deployment) Intrinsic Security 5

XIA Design: Expressiveness • Principal Types – Defines the format of the address • And its semantics, including security semantics – And what the address means – And what processing can be done – Key: Much more intentful than today’s addresses. • Use ours: Host. Service. Content. 4 ID. AD. • Or, {roll your own}

XIA Design: Intrinsic Security • XIA uses self-certifying identifiers that guarantee security properties for communication operation – Host ID is a hash of the host’s public key – accountability – Content ID is a hash of the content – correctness – Does not rely on external configurations • Intrinsic security is specific to the principal type • Example: retrieve content using … – Content XID: content is verifiably/unspoofably correct – Service XID: the correct ASP provided the service – Host XID: content was delivered from intended host 7

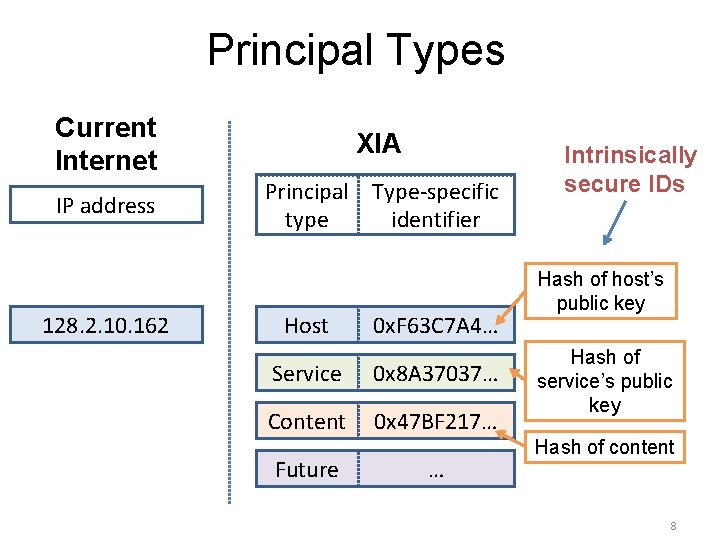
Principal Types Current Internet IP address 128. 2. 10. 162 XIA Principal Type-specific type identifier Host 0 x. F 63 C 7 A 4… Service 0 x 8 A 37037… Content 0 x 47 BF 217… Future … Intrinsically secure IDs Hash of host’s public key Hash of service’s public key Hash of content 8

XIA Design: Deployability • Fallback addressing – Allows you to use tomorrow’s principal type today – “If I can’t go directly to X, use Y. . . ” • Example 1: – Ultimate intent: retrieve CONTENT (CID) – Fallback: contact HOST (HID) • Example 2: – Next hop not XIA-capable? Use (4 ID) in address: Fallback to IPv 4 encapsulation: contact IPv 4(HID) • Admits incremental deployment – Not just of new ID types within XIA, but of XIA itself.

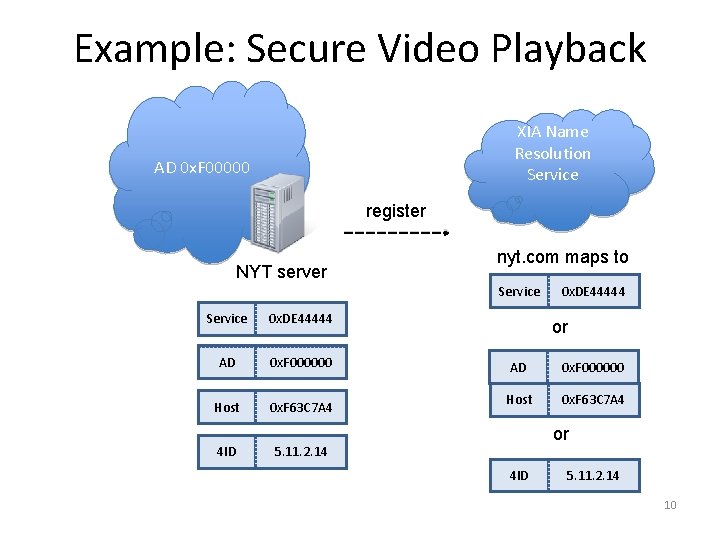
Example: Secure Video Playback XIA Name Resolution Service AD 0 x. F 00000 register NYT server nyt. com maps to Service 0 x. DE 44444 AD 0 x. F 000000 Host 0 x. F 63 C 7 A 4 4 ID 0 x. DE 44444 or AD 0 x. F 000000 Host 0 x. F 63 C 7 A 4 or 5. 11. 2. 14 4 ID 5. 11. 2. 14 10

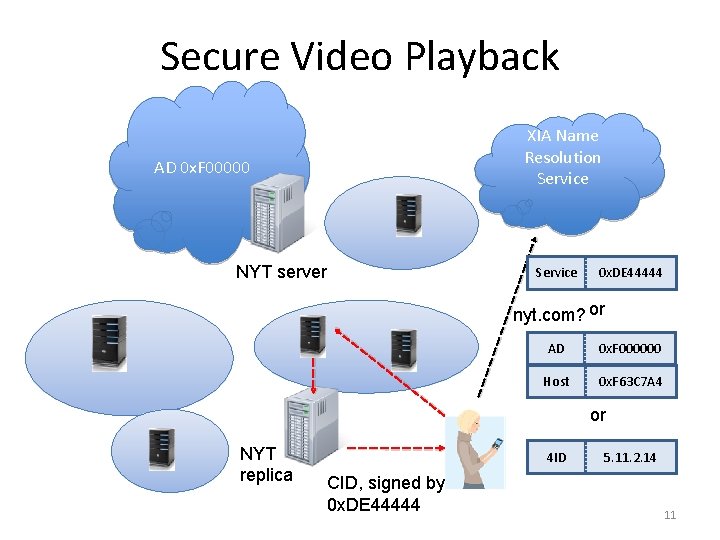
Secure Video Playback XIA Name Resolution Service AD 0 x. F 00000 S NYT server Service 0 x. DE 44444 nyt. com? or AD 0 x. F 000000 Host 0 x. F 63 C 7 A 4 or NYT replica 4 ID CID, signed by 0 x. DE 44444 5. 11. 2. 14 11

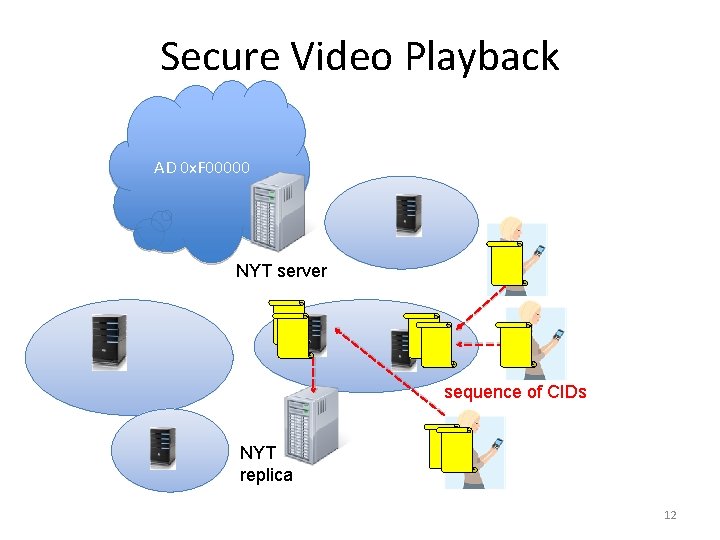
Secure Video Playback AD 0 x. F 00000 S NYT server sequence of CIDs NYT replica 12

XIA top-down view • What does an XIA network look like to various stakeholders? • Who benefits from new features and why? • Who bears the costs of deployment? • Stakeholders we consider (not exhaustive): – Network operators: from testbeds to ISPs – Application providers / service providers – Application developers – End-users 13

Benefits to Network Operators • Increased potential for value-added services (without resorting to deep-packet inspection) – Simpler middlebox deployment – On-path caching or route redirection – Principal types aligned with economic incentives • Risk mitigation via incremental deployment • More choice regarding trust domains – SCION route control 14

Benefits to Service Providers • Added expressivity: customizable principals – Built-in support for binding, scoping, mobility. – Intrinsic security guarantees. • Access control, accounting, accountability, counter-measures for Do. S • Making use of in-network optimizations furnished by network operators. • Similar benefits accrue to application developers. 15

Benefits to End-Users • Increased choice and flexibility regarding intent: – Choice of XID principal type, i. e. how a given communication operation performed – Rich address formats add flexibility: fallback, services. – Scion offers control via edge-directed routing • Support for mobile users • Trickle-down benefits derived from better apps. • Intrinsic security: – Qualitative benefits of security guarantees is a central focus of our user studies. 16

Costs of Deployment • New XIA protocol stack network-wide – Prototype status update next slide – Incremental deployment possible, advisable. • Management and processing overhead – Packet processing; flat address space – Tracking revisions for multiple principal types – Implications for switches, interconnect, H/W. • Additional opportunities present added complexity, new optimization problems. 17

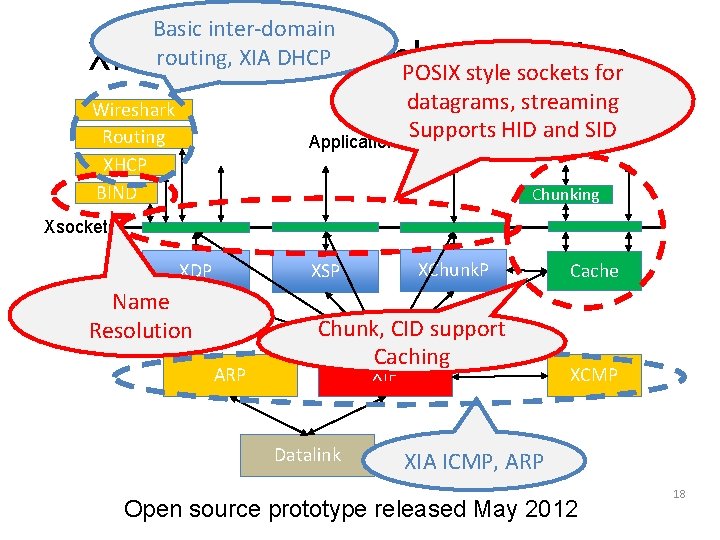
Basic inter-domain routing, XIA DHCP XIP Prototype Implementation POSIX style sockets for datagrams, streaming Supports HID and SID Applications Wireshark Routing XHCP BIND Chunking Xsockets XDP XChunk. P XSP Name Resolution ARP Chunk, CID support Caching XIP Datalink Cache XCMP XIA ICMP, ARP Open source prototype released May 2012 18

Extra slides, possible candidate slides follow 19

Planned Prototype Enhancements • Prototype is available on Github – Latest release includes support for 4 ID • Near term: IP application porting help, better transport protocols, permanent XIP network • Next: mobility support, expanded support for intrinsic security and accountability • Later: Scion integration, more services and applications 20

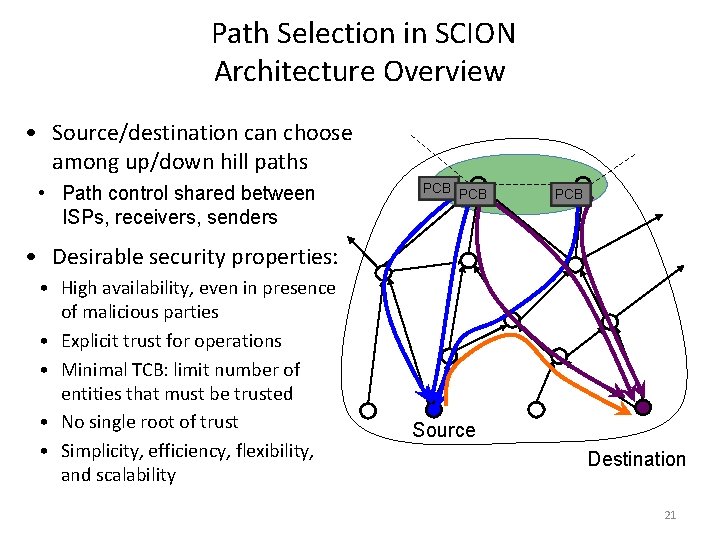
Path Selection in SCION Architecture Overview • Source/destination can choose among up/down hill paths • Path control shared between ISPs, receivers, senders PCB PCB • Desirable security properties: • High availability, even in presence of malicious parties • Explicit trust for operations • Minimal TCB: limit number of entities that must be trusted • No single root of trust • Simplicity, efficiency, flexibility, and scalability Source Destination 21

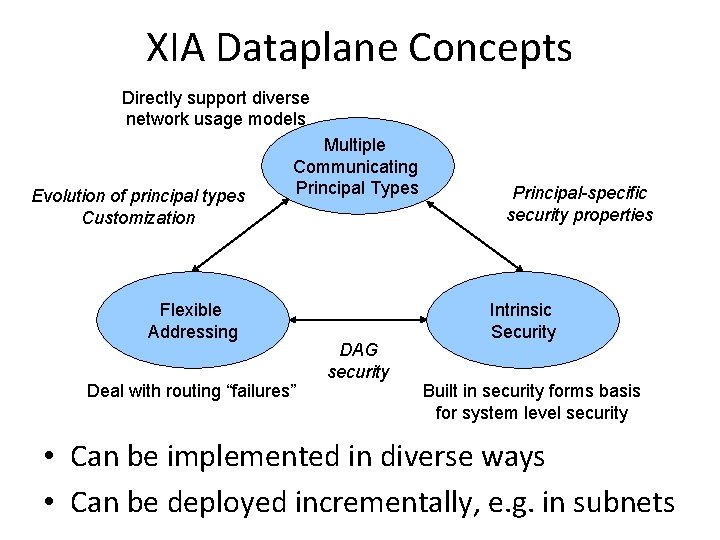
XIA Dataplane Concepts Directly support diverse network usage models Evolution of principal types Customization Multiple Communicating Principal Types Flexible Addressing Deal with routing “failures” DAG security Principal-specific security properties Intrinsic Security Built in security forms basis for system level security • Can be implemented in diverse ways • Can be deployed incrementally, e. g. in subnets