www hume vt edu humevt edu Ted and






- Slides: 12

www. hume. vt. edu hume@vt. edu Ted and Karyn Hume Center for National Security and Technolog (Talent and Technology for) Critical Infrastructure Protection against Cyberattacks Mark L. Goodwin Deputy Director and COO STEM Education Signals Intelligence Electronic Warfare Cybersecurity and Analytics Aerospace Systems

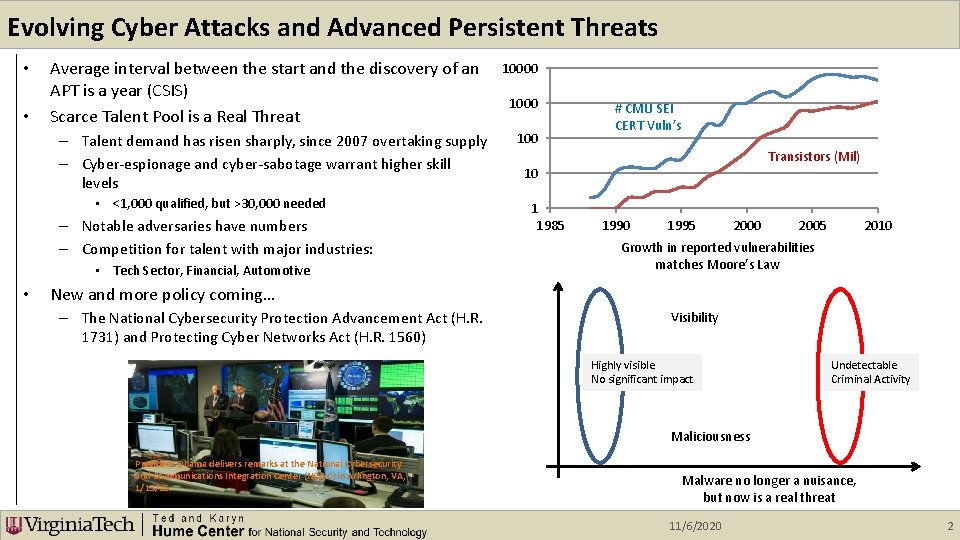
Evolving Cyber Attacks and Advanced Persistent Threats • • Average interval between the start and the discovery of an APT is a year (CSIS) Scarce Talent Pool is a Real Threat – Talent demand has risen sharply, since 2007 overtaking supply – Cyber-espionage and cyber-sabotage warrant higher skill levels • <1, 000 qualified, but >30, 000 needed – Notable adversaries have numbers – Competition for talent with major industries: • Tech Sector, Financial, Automotive • 10000 100 # CMU SEI CERT Vuln’s Transistors (Mil) 10 1 1985 1990 1995 2000 2005 2010 Growth in reported vulnerabilities matches Moore’s Law New and more policy coming… – The National Cybersecurity Protection Advancement Act (H. R. 1731) and Protecting Cyber Networks Act (H. R. 1560) Visibility Highly visible No significant impact Undetectable Criminal Activity Maliciousness President Obama delivers remarks at the National Cybersecurity and Communications Integration Center (NCCIC) in Arlington, VA, 1/13/15. Malware no longer a nuisance, but now is a real threat 11/6/2020 2

Malware and APT’s Know No Bounds e. g. Aurora, Regin, etc. • Regin: Backdoor-type Trojan nation of state technical competence – More dangerous than either Stuxnet or Duqu – Targeting victims in Russia, Saudi Arabia, Ireland Mexico – 1 st infections 2008 -11, then disappeared before new version surfaced 2013 • Cyber attack platform deployed in victim networks for total remote control at all levels (Kaspersky Lab) – Customizable extensive range of capabilities depending on the target • Controllers gain mass surveillance frame-work for spying operations – – – Government organizations Infrastructure operators Businesses Researchers Private individuals Source: Symantec 11/6/2020 3

Critical Infrastructure Security and Resilience (PPD-21) Chemical Information Technology Food and Agriculture Communications Transportation Systems Healthcare and Public Health Dams Commercial Facilities Nuclear Reactors, Materials, and Waste Emergency Services Critical Manufacturing Water and Wastewater Systems Financial Services Defense Industrial Government Facilities Energy Presidential Policy Directive 21 (PPD-21) Defined Sectors VT/Hume Center Foci 11/6/2020 4

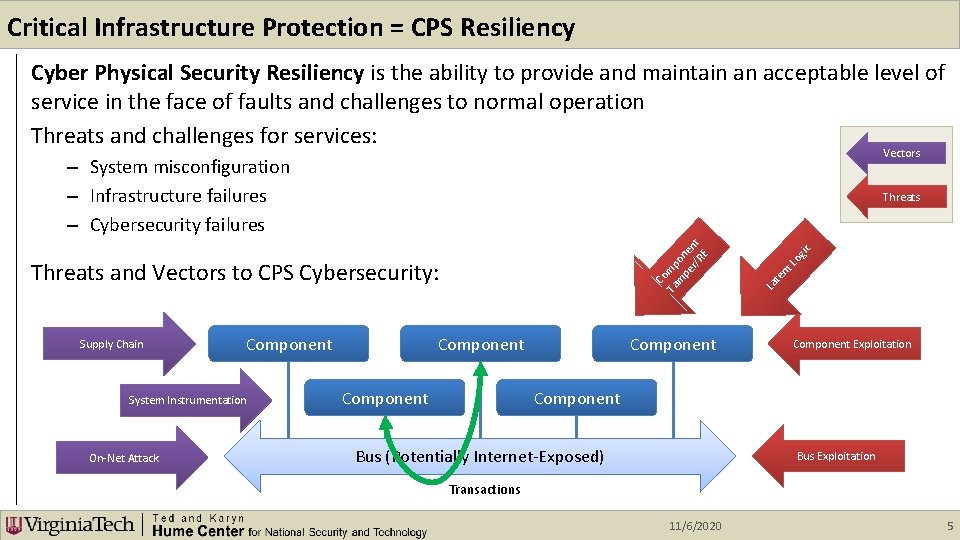
Critical Infrastructure Protection = CPS Resiliency Cyber Physical Security Resiliency is the ability to provide and maintain an acceptable level of service in the face of faults and challenges to normal operation Threats and challenges for services: Vectors – System misconfiguration – Infrastructure failures – Cybersecurity failures Supply Chain Component System Instrumentation On-Net Attack Component gic Lo nt te Threats and Vectors to CPS Cybersecurity: La Co Ta mp m on pe e r/ nt RE Threats Component Exploitation Component Bus (Potentially Internet-Exposed) Bus Exploitation Transactions 11/6/2020 5

Cyber-Physical System Security • Emphasis on security challenges with increasingly interconnected “smart” cyber-physical systems • Focusing on securing embedded platforms and assuring network and bus transactions UAV Cybersecurity Kill Chain Containerization and Segmentation of Embedded Software Industrial Control Systems February 2015 6

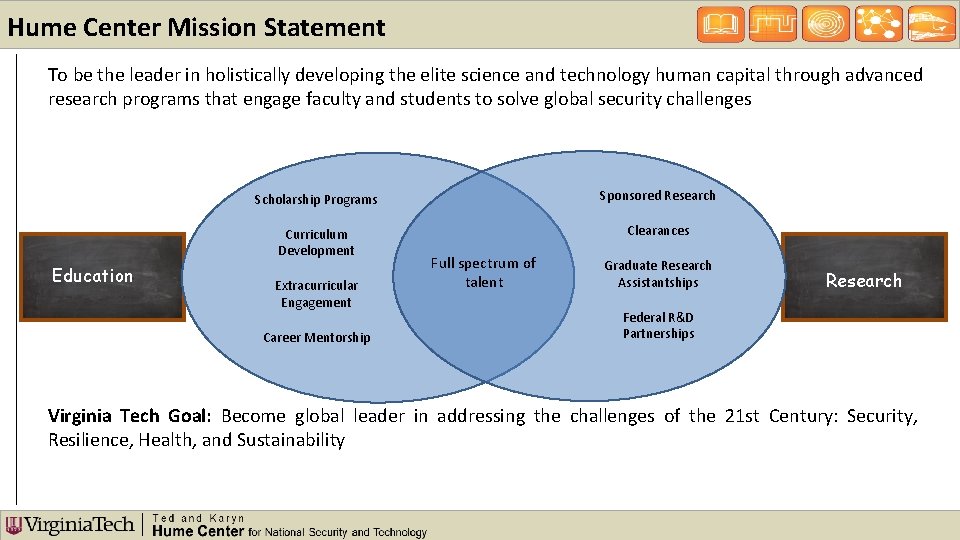
Hume Center Mission Statement To be the leader in holistically developing the elite science and technology human capital through advanced research programs that engage faculty and students to solve global security challenges Education Scholarship Programs Sponsored Research Curriculum Development Clearances Extracurricular Engagement Career Mentorship Full spectrum of talent Graduate Research Assistantships Research Federal R&D Partnerships Virginia Tech Goal: Become global leader in addressing the challenges of the 21 st Century: Security, Resilience, Health, and Sustainability

Hume Center Program Overview • Founded to address critical workforce shortfalls of US citizens entering careers in national security – Undergraduate Students: develop curriculum in critical areas; provide extracurricular activities and career mentorship; focus on internship opportunities that gain students clearances – Graduate Students: provide opportunities for students to conduct classified research as a part of their graduate studies STEM Education Current Sponsor Profile IC S&T Signals Intelligence NSF DOD S&T Industry Electronic Warfare Major Industry Sponsors Cybersecurity and Analytics Aerospace Systems March 2015 8

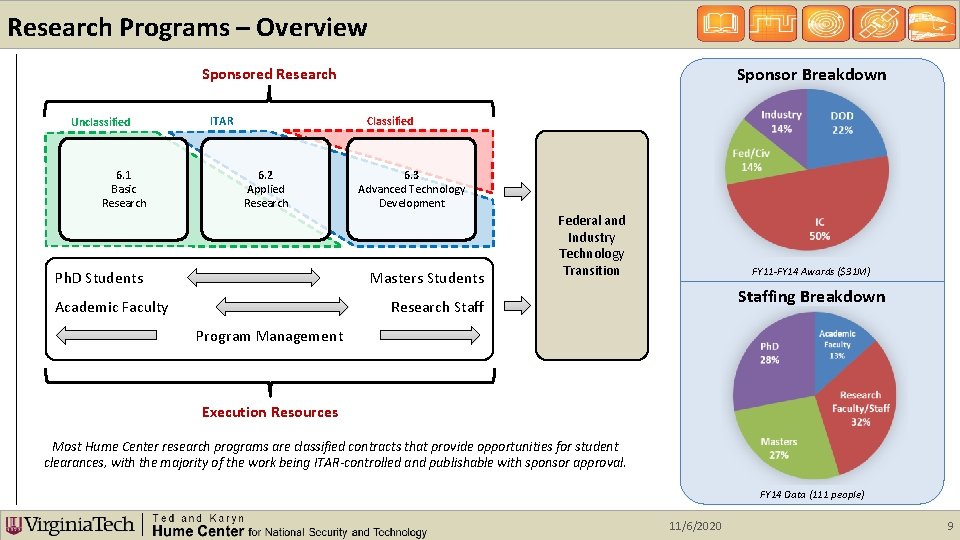
Research Programs – Overview Sponsor Breakdown Sponsored Research Unclassified 6. 1 Basic Research ITAR Classified 6. 2 Applied Research Ph. D Students 6. 3 Advanced Technology Development Masters Students Academic Faculty Federal and Industry Technology Transition FY 11 -FY 14 Awards ($31 M) Staffing Breakdown Research Staff Program Management Execution Resources Most Hume Center research programs are classified contracts that provide opportunities for student clearances, with the majority of the work being ITAR-controlled and publishable with sponsor approval. FY 14 Data (111 people) 11/6/2020 9

Research Opportunities • Opportunities to invest differ depending on the technology maturity • Engage early on to have biggest influence on pipeline $200 K to bootstrap new Ph. D-level research professor position Capacity Building Investment in Human Capital TRL 1 TRL 2 $75 K/student/year to fund graduate student researchers (fully-burdened rate includes IPR) Applied Research Investment in Technologies TRL 3 Basic Research Investment in Invention $40 K/student/year to fund seed-stage R&D through consortium programs (pre-competitive R&D) TRL 4 TRL 5 Engineering Investment in Tech Transition ~$200 K/FTE to fund university staff engineers to mature technologies TRL = Technology Readiness Level Measure of technology maturity from fundamental science (TRL 1) through operational deployed system (TRL 9) 10

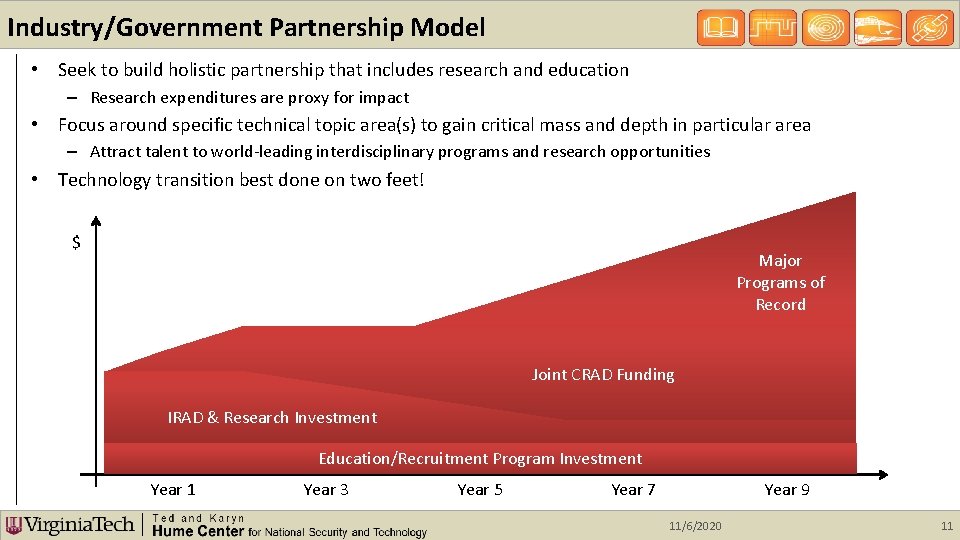
Industry/Government Partnership Model • Seek to build holistic partnership that includes research and education – Research expenditures are proxy for impact • Focus around specific technical topic area(s) to gain critical mass and depth in particular area – Attract talent to world-leading interdisciplinary programs and research opportunities • Technology transition best done on two feet! $ Major Programs of Record Joint CRAD Funding IRAD & Research Investment Education/Recruitment Program Investment Year 1 Year 3 Year 5 Year 7 Year 9 11/6/2020 11

Conclusion The defensive tools, procedures and other controls commonly put in place to handle commodity security threats are often ineffective against targeted APT-style attacks. This is because the actors behind the intrusion are focused on a specific target and are able to customize and adapt their Tactics, Techniques and Procedures (TTP) to predict and circumvent security controls and standard incident response practices. As a result, developing an effective and efficient defense strategy requires good situational awareness and understanding. This requires specialized talent and technology. Mark L. Goodwin Deputy Director and COO mlgood 3@vt. edu 540 -231 -7376 11/6/2020 12
 Enamel rods in gingival third of primary teeth
Enamel rods in gingival third of primary teeth Mount and hume classification
Mount and hume classification Locke berkeley and hume
Locke berkeley and hume Dentistry
Dentistry Gj mount classification
Gj mount classification Forward caries and backward caries
Forward caries and backward caries Liquefaction foci dentin
Liquefaction foci dentin Hume contexto historico
Hume contexto historico Hume's bundle theory
Hume's bundle theory Hume rothery rules
Hume rothery rules Klasyfikacja mounta i huma
Klasyfikacja mounta i huma Hume's fork examples
Hume's fork examples Something beautiful
Something beautiful























