Working SetBased Access Control for Network File Systems

Working Set-Based Access Control for Network File Systems Stephen Smaldone, Vinod Ganapathy, and Liviu Iftode Disco. Lab - Department of Computer Science Rutgers, The State University of New Jersey { smaldone, vinodg, iftode }@cs. rutgers. edu
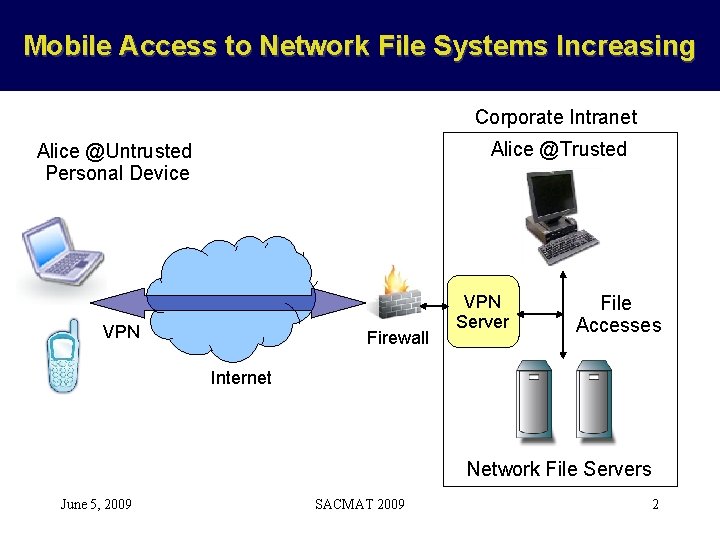
Mobile Access to Network File Systems Increasing Corporate Intranet Alice @Trusted Alice @Untrusted Personal Device VPN Firewall VPN Server File Accesses Internet Network File Servers June 5, 2009 SACMAT 2009 2
The Working Set Concept • The working set of a process is the collection of information referenced by the process during a time interval. [Denning 1968] – Temporal locality of a process’ memory accesses – Memory pages to keep resident in memory to optimize performance now and in the near future – Informs memory page replacement algorithms to avoid thrashing June 5, 2009 SACMAT 2009 3

WSBAC: Working Set-Based Access Control • Setting – Trusted Devices vs. Untrusted Devices • Applies the working set principle to network file system security (access control) – Learn working set during trusted accesses – Enforce working set during untrusted accesses June 5, 2009 SACMAT 2009 4
Contributions • Working Set-Based Access Control (WSBAC) – Novel access control technique that estimates per-user file access working sets and enforces during access from untrusted devices • Prototype Implementation of WSBAC for Network File Systems – POLEX: Working set policy extraction – POLEN: Working set policy enforcement • Evaluation using Real-World Network File System Traces – Experimental evaluation of WSBAC using real-world NFS traces, which suggests that WSBAC is feasible and highly-effective June 5, 2009 SACMAT 2009 5

Outline • • Introduction WSBAC Architecture File. Wall WSBAC Design and Implementation Evaluation and Results Related Work Conclusions and Future Work June 5, 2009 SACMAT 2009 6
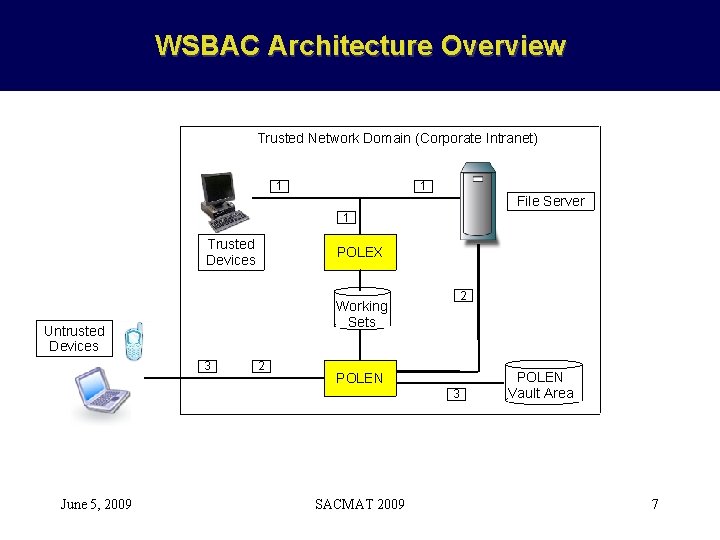
WSBAC Architecture Overview Trusted Network Domain (Corporate Intranet) 1 1 File Server 1 Trusted Devices POLEX 2 Working Sets Untrusted Devices 3 2 POLEN 3 June 5, 2009 SACMAT 2009 POLEN Vault Area 7
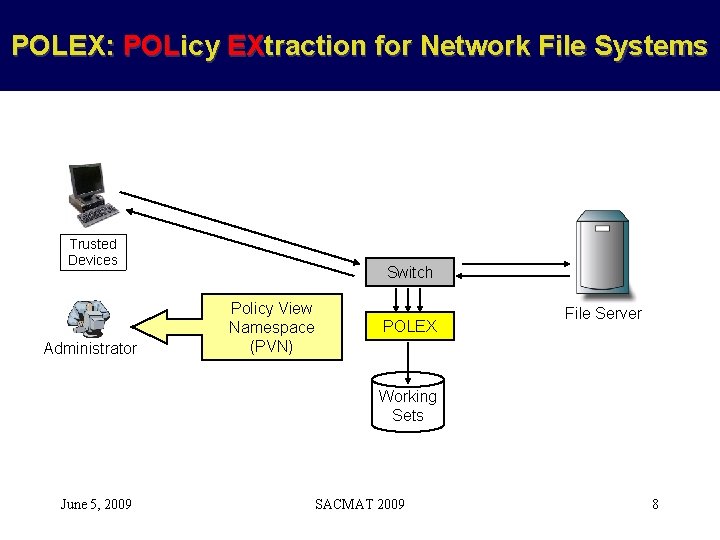
POLEX: POLicy EXtraction for Network File Systems Trusted Devices Administrator Switch Policy View Namespace (PVN) POLEX File Server Working Sets June 5, 2009 SACMAT 2009 8
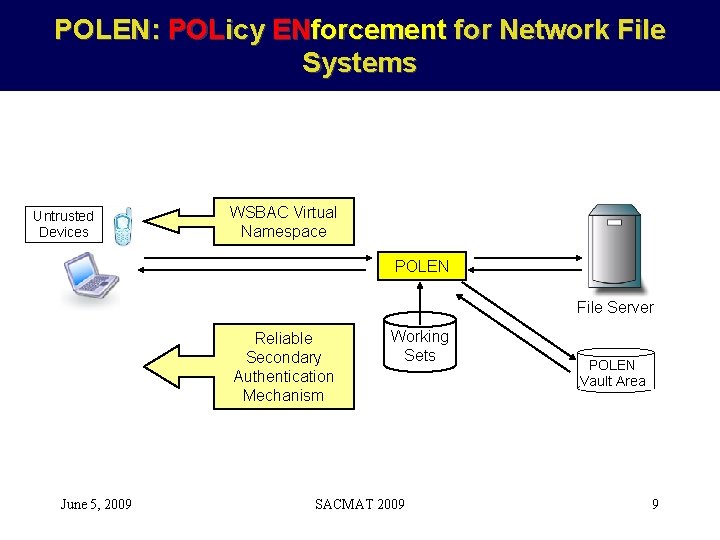
POLEN: POLicy ENforcement for Network File Systems Untrusted Devices WSBAC Virtual Namespace POLEN File Server Reliable Secondary Authentication Mechanism June 5, 2009 Working Sets SACMAT 2009 POLEN Vault Area 9
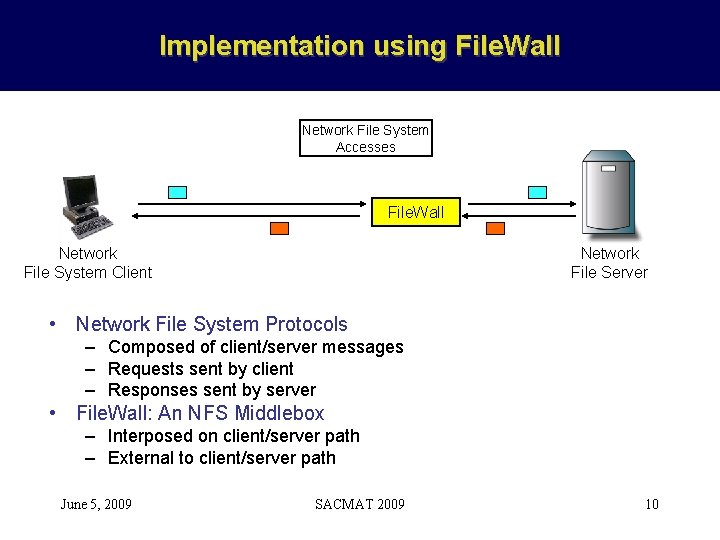
Implementation using File. Wall Network File System Accesses File. Wall Network File System Client Network File Server • Network File System Protocols – Composed of client/server messages – Requests sent by client – Responses sent by server • File. Wall: An NFS Middlebox – Interposed on client/server path – External to client/server path June 5, 2009 SACMAT 2009 10
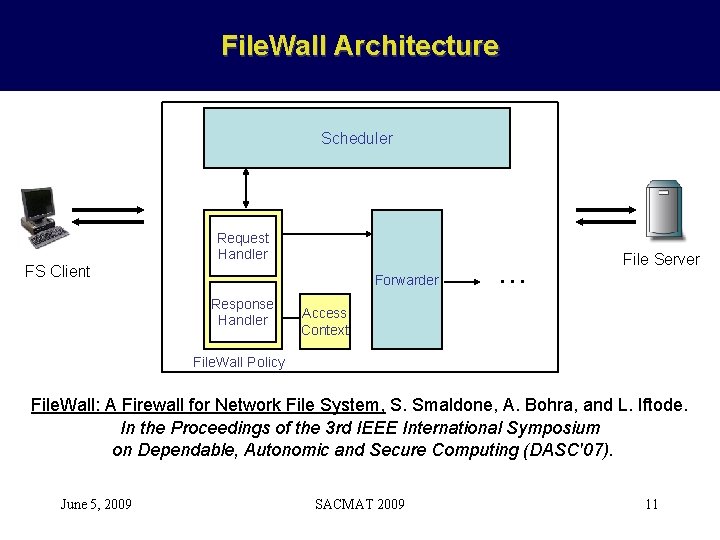
File. Wall Architecture Scheduler Request Handler FS Client Forwarder Response Handler … File Server Access Context File. Wall Policy File. Wall: A Firewall for Network File System, S. Smaldone, A. Bohra, and L. Iftode. In the Proceedings of the 3 rd IEEE International Symposium on Dependable, Autonomic and Secure Computing (DASC'07). June 5, 2009 SACMAT 2009 11
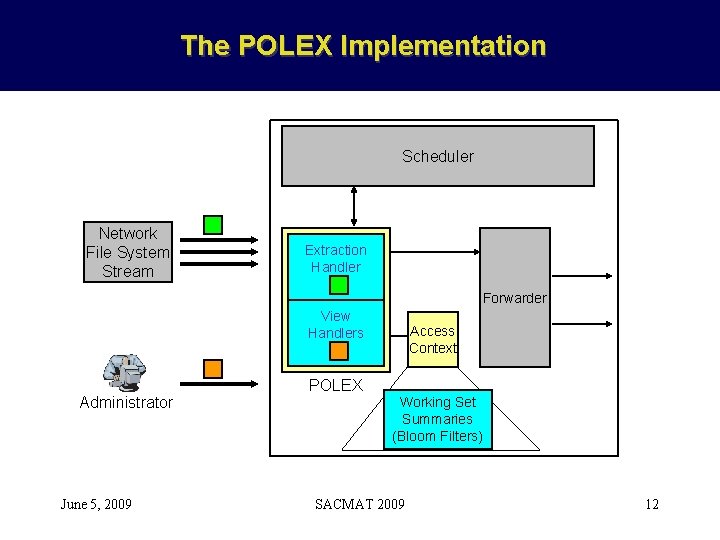
The POLEX Implementation Scheduler Network File System Stream Extraction Handler Forwarder View Handlers Administrator June 5, 2009 Access Context POLEX Working Set Summaries (Bloom Filters) SACMAT 2009 12
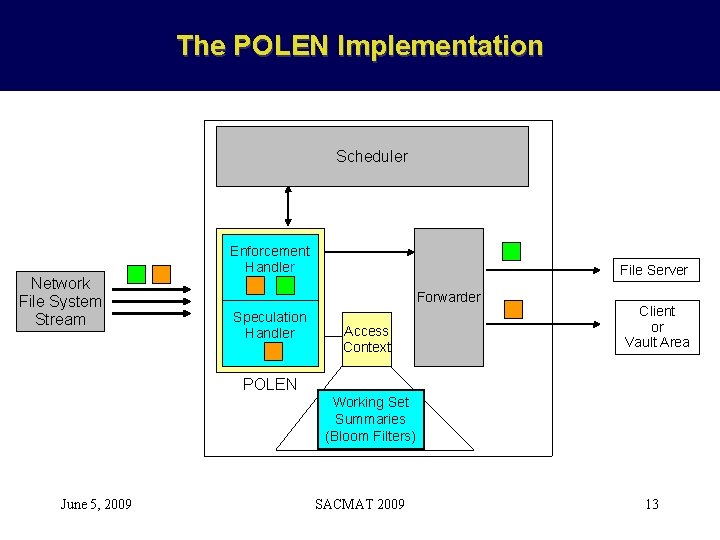
The POLEN Implementation Scheduler Network File System Stream Enforcement Handler File Server Forwarder Speculation Handler Access Context Client or Vault Area POLEN Working Set Summaries (Bloom Filters) June 5, 2009 SACMAT 2009 13

Outline • • Introduction WSBAC Architecture File. Wall WSBAC Design and Implementation Evaluation and Results Related Work Conclusions June 5, 2009 SACMAT 2009 14
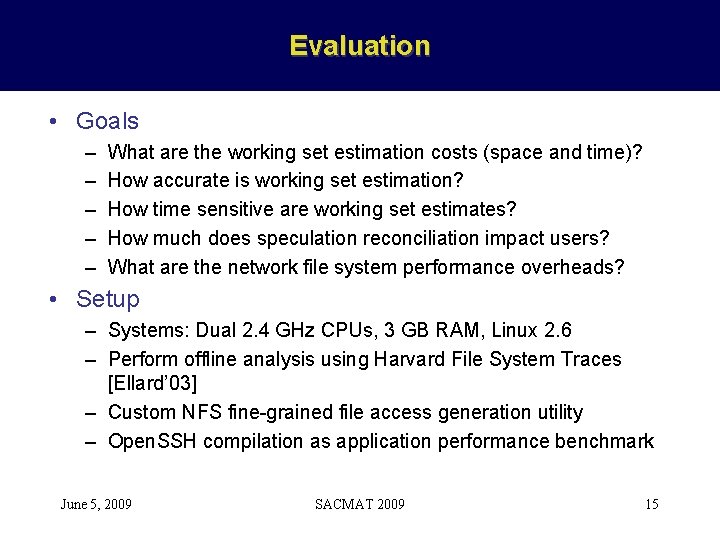
Evaluation • Goals – – – What are the working set estimation costs (space and time)? How accurate is working set estimation? How time sensitive are working set estimates? How much does speculation reconciliation impact users? What are the network file system performance overheads? • Setup – Systems: Dual 2. 4 GHz CPUs, 3 GB RAM, Linux 2. 6 – Perform offline analysis using Harvard File System Traces [Ellard’ 03] – Custom NFS fine-grained file access generation utility – Open. SSH compilation as application performance benchmark June 5, 2009 SACMAT 2009 15
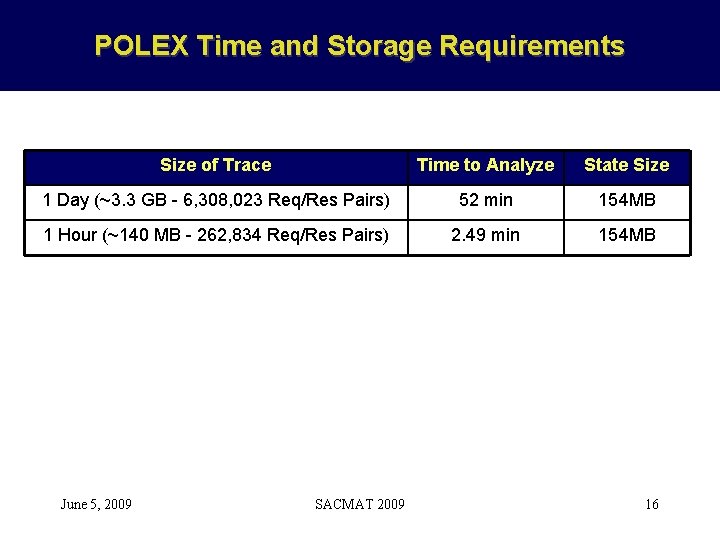
POLEX Time and Storage Requirements Size of Trace Time to Analyze State Size 1 Day (~3. 3 GB - 6, 308, 023 Req/Res Pairs) 52 min 154 MB 1 Hour (~140 MB - 262, 834 Req/Res Pairs) 2. 49 min 154 MB June 5, 2009 SACMAT 2009 16
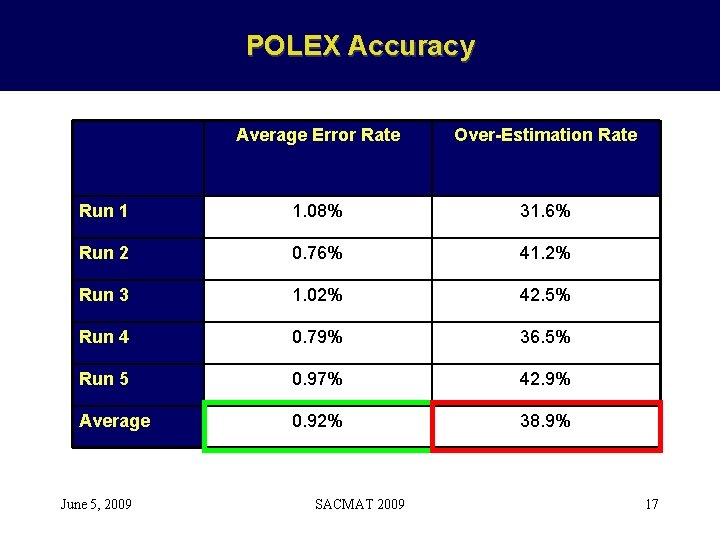
POLEX Accuracy Average Error Rate Over-Estimation Rate Run 1 1. 08% 31. 6% Run 2 0. 76% 41. 2% Run 3 1. 02% 42. 5% Run 4 0. 79% 36. 5% Run 5 0. 97% 42. 9% Average 0. 92% 38. 9% June 5, 2009 SACMAT 2009 17
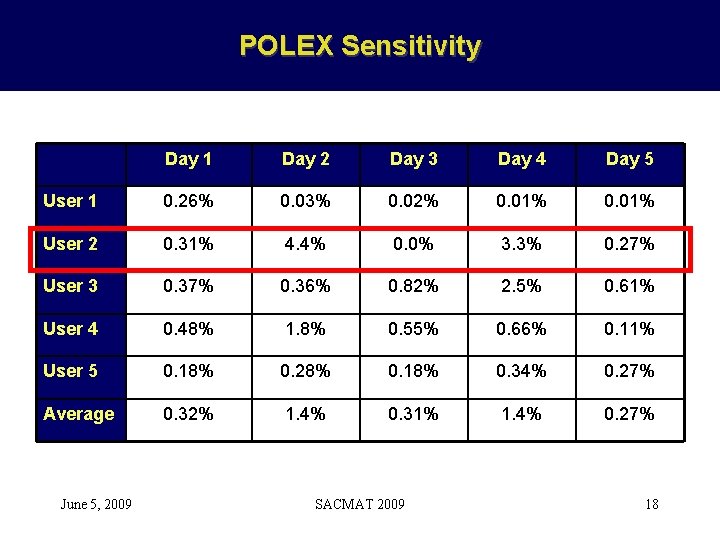
POLEX Sensitivity Day 1 Day 2 Day 3 Day 4 Day 5 User 1 0. 26% 0. 03% 0. 02% 0. 01% User 2 0. 31% 4. 4% 0. 0% 3. 3% 0. 27% User 3 0. 37% 0. 36% 0. 82% 2. 5% 0. 61% User 4 0. 48% 1. 8% 0. 55% 0. 66% 0. 11% User 5 0. 18% 0. 28% 0. 18% 0. 34% 0. 27% Average 0. 32% 1. 4% 0. 31% 1. 4% 0. 27% June 5, 2009 SACMAT 2009 18
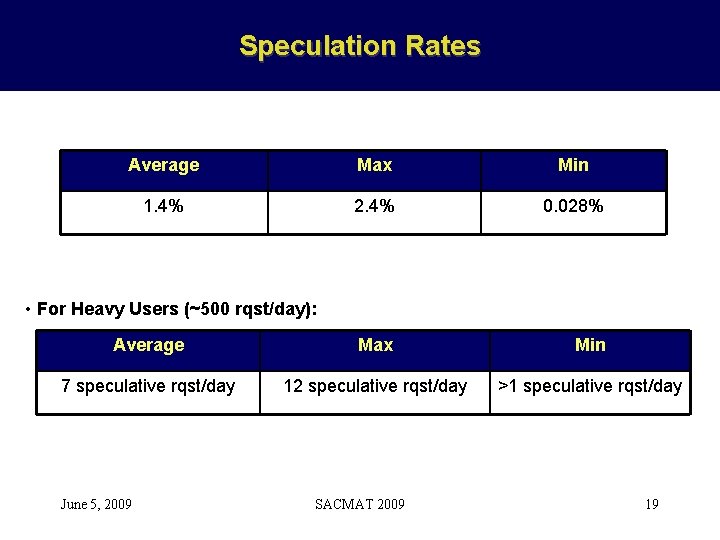
Speculation Rates Average Max Min 1. 4% 2. 4% 0. 028% Average Max Min 7 speculative rqst/day 12 speculative rqst/day >1 speculative rqst/day • For Heavy Users (~500 rqst/day): June 5, 2009 SACMAT 2009 19
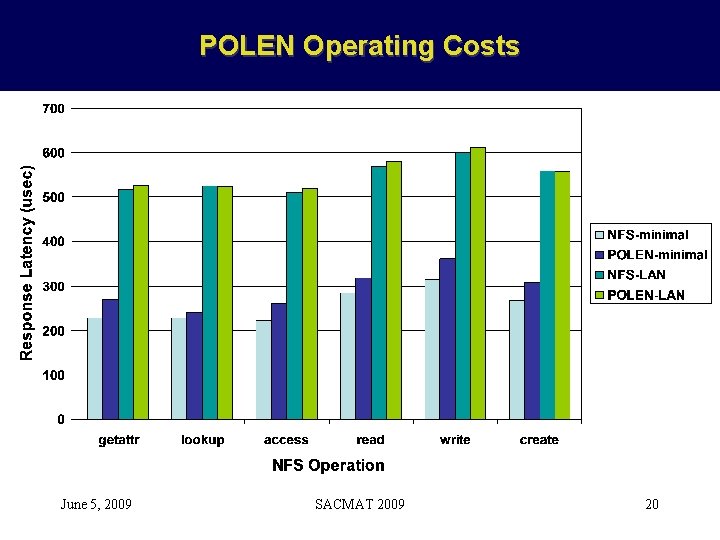
POLEN Operating Costs June 5, 2009 SACMAT 2009 20
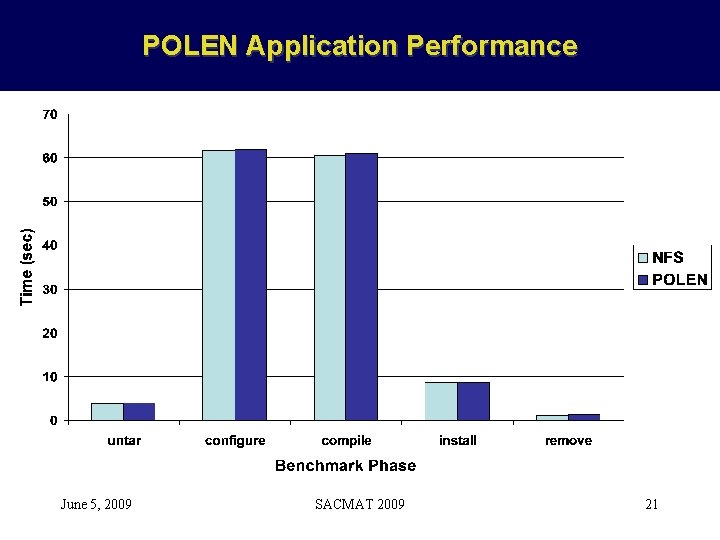
POLEN Application Performance June 5, 2009 SACMAT 2009 21

Related Work • Policy Extraction and Inference – RBAC Role Mining [Kuhlmann’ 03, Schlegelmilch’ 05] – XACML AC Property Inference [Anderson’ 04, Martin’ 06] – Firewall Policy Inference [Golnabi’ 06, Tongaonkar’ 07] – Gray-Box Systems [Arpaci-Dusseau’ 01] • Context-Aware Access Control – Secure Collaborations in Mobile Computing [Toninelli’ 06] – Ubiquitous Services [Corradi’ 04, Yokotama’ 06] – Ad-Hoc Networks [Saidane’ 07] – Web Services [Bhatti’ 05, Kapsalis’ 06] June 5, 2009 SACMAT 2009 22
Conclusions and Future Work • WSBAC: Working Set-Based Access Control for Network File Systems – Access control technique that estimates per-user working sets to formulate access control policy for accesses from untrusted devices – Prototype design and implementation of POLEX and POLEN – Experimental evaluation suggests that WSBAC is highly effective, exhibiting low error rates • Future Work: Real-World Deployment and User Study – Study qualitative impact on users (usability) – Produce better network file system traces for future access control studies June 5, 2009 SACMAT 2009 23

Thank You! http: //discolab. rutgers. edu
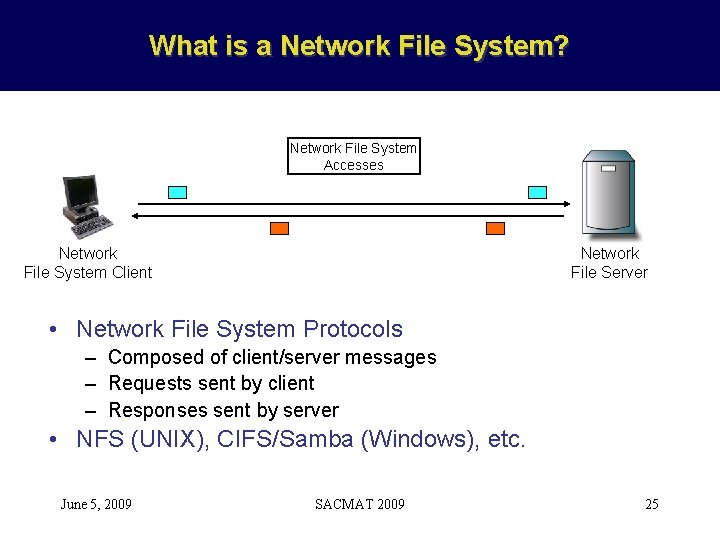
What is a Network File System? Network File System Accesses Network File System Client Network File Server • Network File System Protocols – Composed of client/server messages – Requests sent by client – Responses sent by server • NFS (UNIX), CIFS/Samba (Windows), etc. June 5, 2009 SACMAT 2009 25
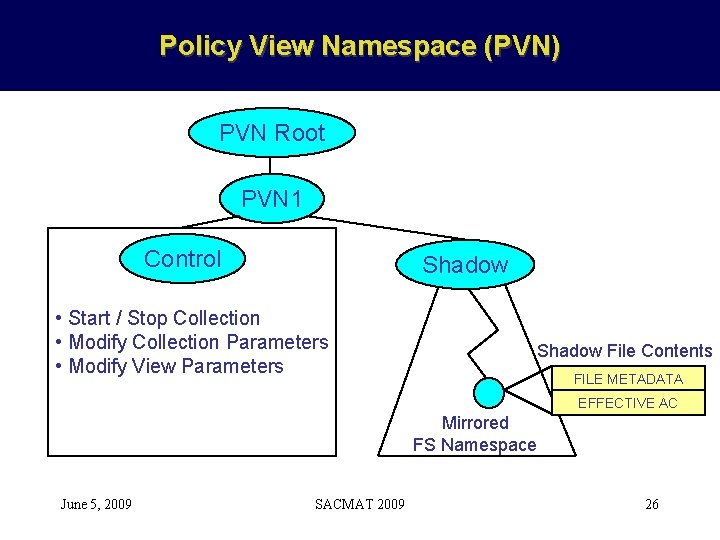
Policy View Namespace (PVN) PVN Root PVN 1 Control Shadow • Start / Stop Collection • Modify Collection Parameters • Modify View Parameters Shadow File Contents FILE METADATA EFFECTIVE AC Mirrored FS Namespace June 5, 2009 SACMAT 2009 26
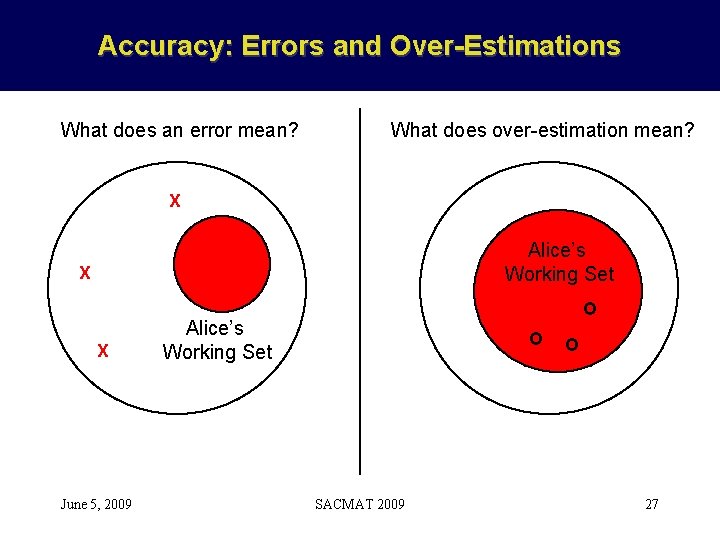
Accuracy: Errors and Over-Estimations What does an error mean? What does over-estimation mean? X Alice’s Working Set X X June 5, 2009 O Alice’s Working Set O SACMAT 2009 O 27
- Slides: 27