WIRELESS SECURITY 802 1 x EAP Authentication Protocols




- Slides: 12

WIRELESS SECURITY 802. 1 x EAP Authentication Protocols

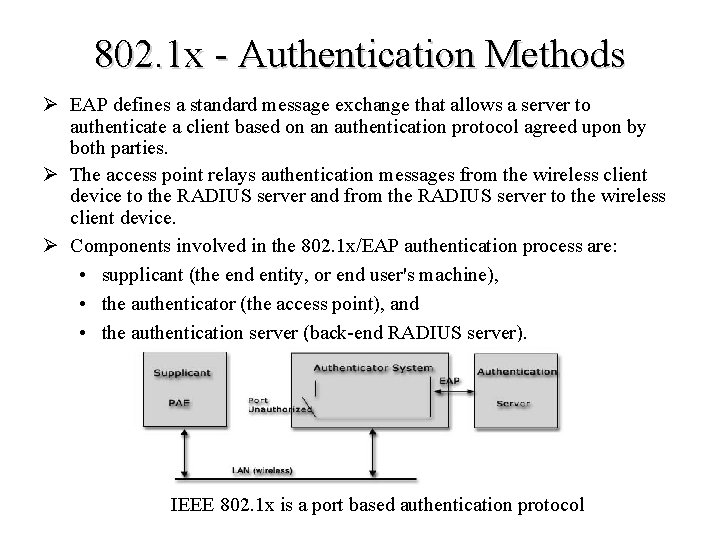
802. 1 x - Authentication Methods Ø EAP defines a standard message exchange that allows a server to authenticate a client based on an authentication protocol agreed upon by both parties. Ø The access point relays authentication messages from the wireless client device to the RADIUS server and from the RADIUS server to the wireless client device. Ø Components involved in the 802. 1 x/EAP authentication process are: • supplicant (the end entity, or end user's machine), • the authenticator (the access point), and • the authentication server (back-end RADIUS server). IEEE 802. 1 x is a port based authentication protocol

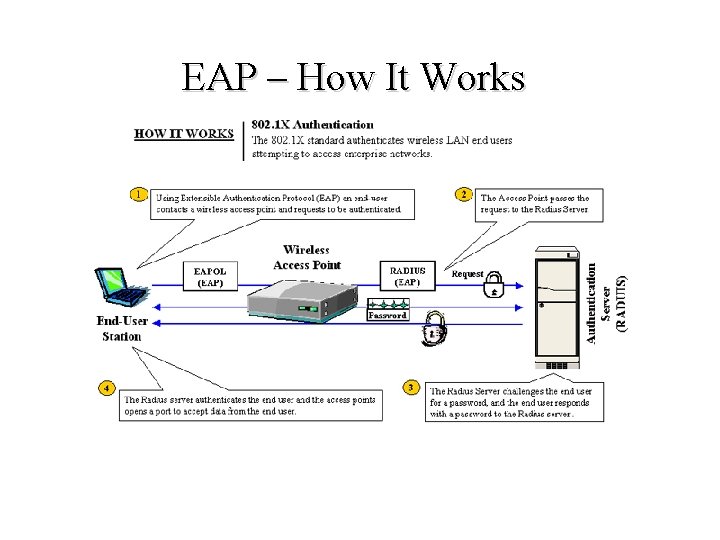
EAP – How It Works

802. 1 x EAP – Authentication Types Ø A specific EAP authentication scheme is known as an EAP type. Ø Both the remote access client and the authenticator must support the same EAP type for successful authentication to occur. Ø The access point has to support the 802. 1 x/EAP authentication process. (The access point is not aware of the EAP authentication protocol type. ) Ø The different EAP-Types are : • EAP-Transport Layer Security (EAP-TLS) • Tunneled Transport Layer Security (TTLS) • Cisco Light Weighted EAP (LEAP) • Protected EAP (PEAP).

EAP – TLS and its Disadvantages Ø In EAP-TLS, certificates are used to provide authentication in both directions. Ø The server presents a certificate to the client, and, after validating the server's certificate the client presents a client certificate. Ø Requires each user to have a certificate. Ø Imposes substantial administrative burden in operating a certificate authority to distribute, revoke and manage user certificates

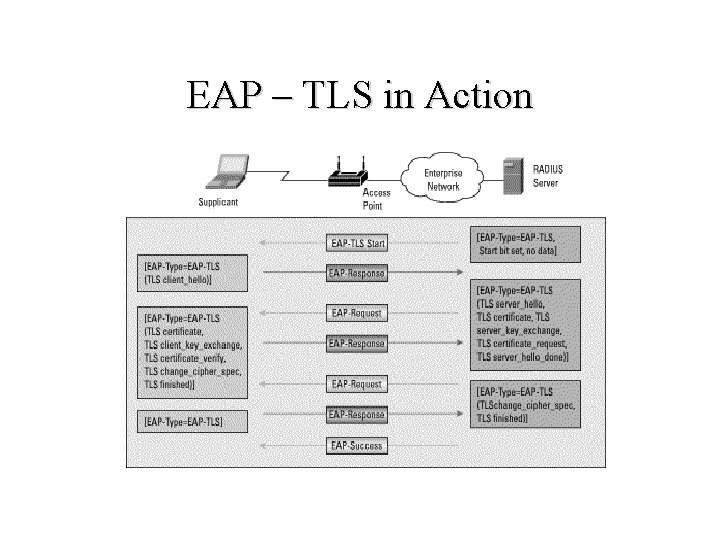
EAP – TLS in Action

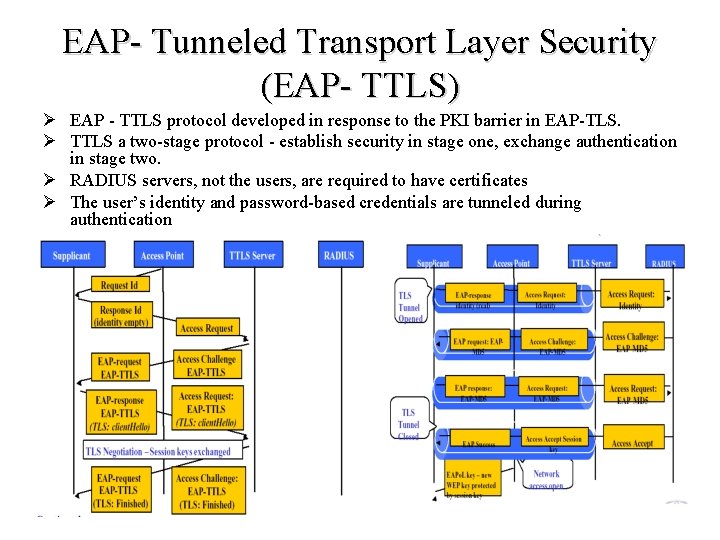
EAP- Tunneled Transport Layer Security (EAP- TTLS) Ø EAP - TTLS protocol developed in response to the PKI barrier in EAP-TLS. Ø TTLS a two-stage protocol - establish security in stage one, exchange authentication in stage two. Ø RADIUS servers, not the users, are required to have certificates Ø The user’s identity and password-based credentials are tunneled during authentication

Advantages of Using EAP – TTLS Ø Users to be authenticated with existing password credentials, and, using strong public/private key cryptography Ø Prevents dictionary attacks, man-in-the-middle attacks, and hijacked connections by wireless eavesdroppers. Ø Does not require the use of client certificates. Ø Requires little additional administration unlike EAP-TLS Ø Dynamic per-session keys are generated to encrypt the wireless connection and protect data privacy

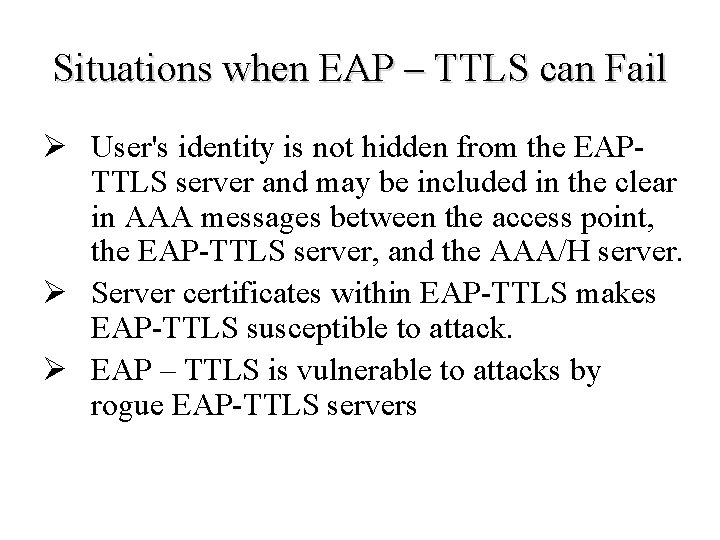
Situations when EAP – TTLS can Fail Ø User's identity is not hidden from the EAPTTLS server and may be included in the clear in AAA messages between the access point, the EAP-TTLS server, and the AAA/H server. Ø Server certificates within EAP-TTLS makes EAP-TTLS susceptible to attack. Ø EAP – TTLS is vulnerable to attacks by rogue EAP-TTLS servers

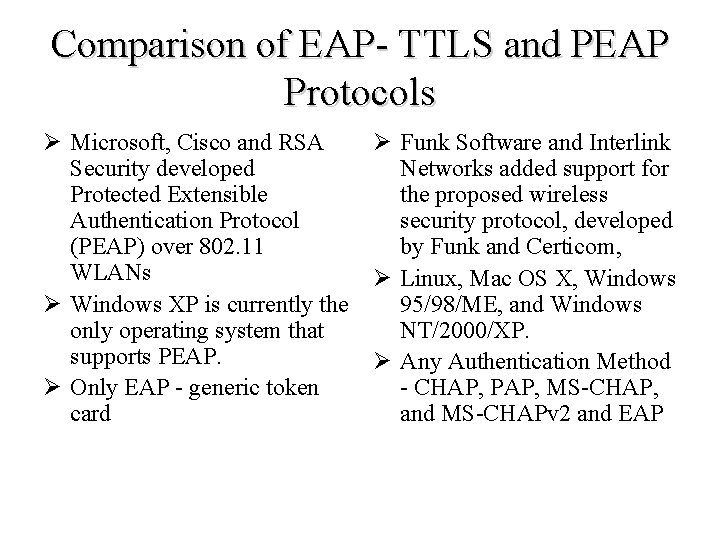
Comparison of EAP- TTLS and PEAP Protocols Ø Microsoft, Cisco and RSA Security developed Protected Extensible Authentication Protocol (PEAP) over 802. 11 WLANs Ø Windows XP is currently the only operating system that supports PEAP. Ø Only EAP - generic token card Ø Funk Software and Interlink Networks added support for the proposed wireless security protocol, developed by Funk and Certicom, Ø Linux, Mac OS X, Windows 95/98/ME, and Windows NT/2000/XP. Ø Any Authentication Method - CHAP, PAP, MS-CHAP, and MS-CHAPv 2 and EAP

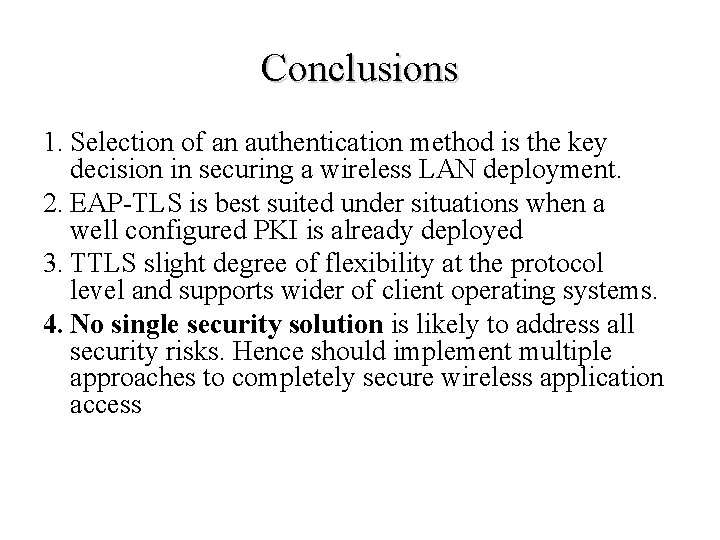
Conclusions 1. Selection of an authentication method is the key decision in securing a wireless LAN deployment. 2. EAP-TLS is best suited under situations when a well configured PKI is already deployed 3. TTLS slight degree of flexibility at the protocol level and supports wider of client operating systems. 4. No single security solution is likely to address all security risks. Hence should implement multiple approaches to completely secure wireless application access

References Ø www. ietf. org/internet-drafts/draft-ietf-pppext-eap-ttls 02. txt Ø http: //www. nwfusion. com/research/2002/0506 ilabwla n. html Ø http: //www. oreillynet. com/pub/a/wireless/2002/10/17 /peap. html Ø http: //www. nwfusion. com/news/2002/1111 funk. html Ø http: //www. nwfusion. com/news/2002/0923 peap. html Ø http: //www. mtghouse. com