Wireless MAC Protocol Outline design challenges for wireless









- Slides: 14

Wireless MAC Protocol Outline: • design challenges for wireless MAC – hidden/exposed stations – flexible control for Qo. S support • two design paradigms – multiple access based – token based • rationale for design choices 9/25/2020 1

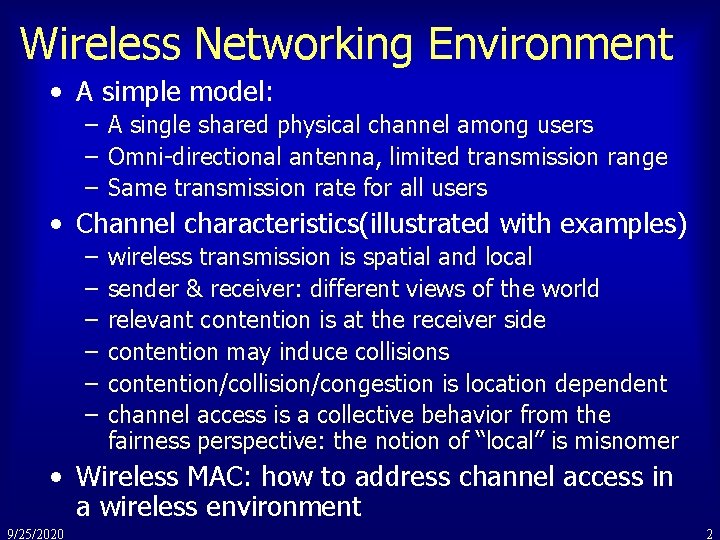
Wireless Networking Environment • A simple model: – A single shared physical channel among users – Omni-directional antenna, limited transmission range – Same transmission rate for all users • Channel characteristics(illustrated with examples) – – – wireless transmission is spatial and local sender & receiver: different views of the world relevant contention is at the receiver side contention may induce collisions contention/collision/congestion is location dependent channel access is a collective behavior from the fairness perspective: the notion of “local” is misnomer • Wireless MAC: how to address channel access in a wireless environment 9/25/2020 2

Design Goals for Wireless MAC • Requirements for a wireless MAC protocol: – robustness – efficiency – fairness – support for priority and Qo. S – support for multicast 9/25/2020 3

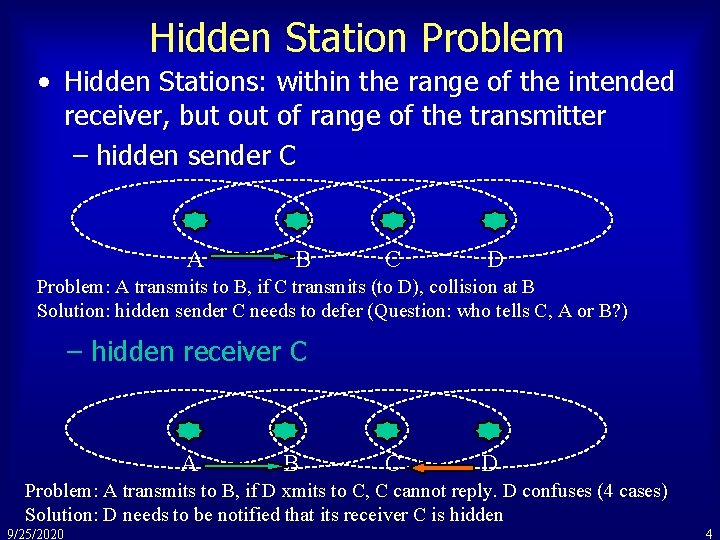
Hidden Station Problem • Hidden Stations: within the range of the intended receiver, but of range of the transmitter – hidden sender C A B C D Problem: A transmits to B, if C transmits (to D), collision at B Solution: hidden sender C needs to defer (Question: who tells C, A or B? ) – hidden receiver C A B C D Problem: A transmits to B, if D xmits to C, C cannot reply. D confuses (4 cases) Solution: D needs to be notified that its receiver C is hidden 9/25/2020 4

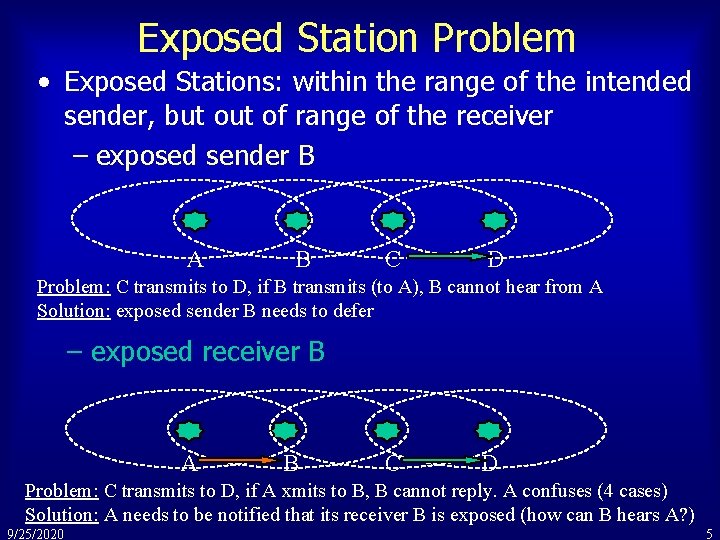
Exposed Station Problem • Exposed Stations: within the range of the intended sender, but of range of the receiver – exposed sender B A B C D Problem: C transmits to D, if B transmits (to A), B cannot hear from A Solution: exposed sender B needs to defer – exposed receiver B A B C D Problem: C transmits to D, if A xmits to B, B cannot reply. A confuses (4 cases) Solution: A needs to be notified that its receiver B is exposed (how can B hears A? ) 9/25/2020 5

Summary of hidden and exposed station problem • Receiver’s perception of a clean/collided packet is critical • Hidden/exposed senders need to defer their transmissions • Hidden/exposed receivers need to notify their senders about their status 9/25/2020 6

MAC Protocol Resolve channel contention & access: • Channel access arbitration – know who are there – allocate the channel among multiple senders & receivers who share the channel • Collision avoidance – multiple access based – token based • Collision resolution – backoff based 9/25/2020 7

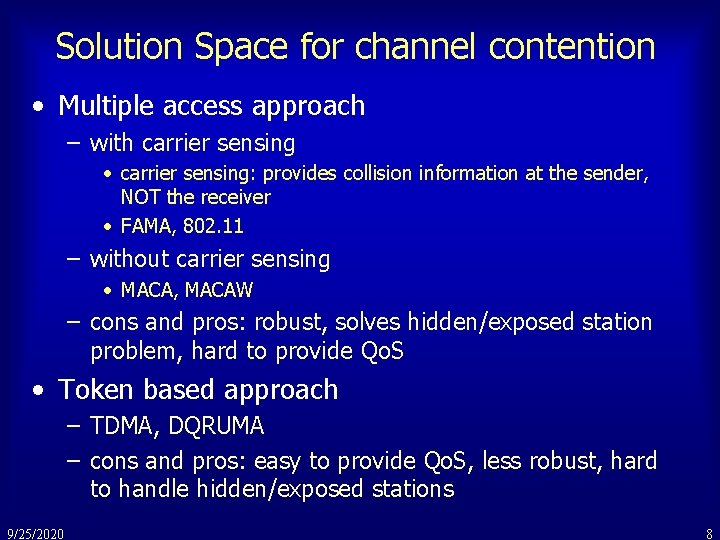
Solution Space for channel contention • Multiple access approach – with carrier sensing • carrier sensing: provides collision information at the sender, NOT the receiver • FAMA, 802. 11 – without carrier sensing • MACA, MACAW – cons and pros: robust, solves hidden/exposed station problem, hard to provide Qo. S • Token based approach – TDMA, DQRUMA – cons and pros: easy to provide Qo. S, less robust, hard to handle hidden/exposed stations 9/25/2020 8

Collision Avoidance • Basic approach: when a station needs to send, – listens to the channel – if it overhears an ongoing transmission, waits until it completes before re-executing the channel access – otherwise, it initiates a control packet handshake – after successful handshake, starts data transmission • RTS-CTS-DS-Data-ACK sequence – draw the basic handshake sequence – explain why they are necessary – deferral: • exposed sender: defers 2 slots to hear DS when sees RTS – not hearing DS, cease to defer – hearing DS, defers (m+1) slots to let the sender receives ACK • hidden sender: defers (m+1) slots when sees CTS – solves hidden/exposed sender problem 9/25/2020 9

Collision Avoidance (contd) • How to solve hidden/exposed receiver problem ? – Hidden receiver: needs to send an out-of-band signal – exposed receiver: needs to receive the initial control packet in the presence of ongoing data traffic – one solution: dual (data and control) channel + NCTS packet 9/25/2020 10

Collision Resolution • Backoff algorithms: BEB and MILD – BEB: unfair in the sense that it favors the last transmitter to aggressively contend for the channel again – MILD: still favors a successful transmitter, better than BEB • What is the definition of fairness ? – per station versus per flow – (spatial congestion) independent versus dependent • techniques for collision resolution – collision measurement for spatial congestion • most collisions are contention-related if CA is effective – backoff advertisement • since contention is spatial, advertising backoff values helps neighbors to share information & make collective decisions. 9/25/2020 11

Multiple Tokens Approach • Someone controls the distribution of tokens, only those with tokens are allowed to send • Effective in cellular environment • Two major components – distribution of tokens • provides an instrument for Qo. S support • interact with higher layer scheduling – identification of transmitters • adding new comers: periodically initiating an identification phase • deleting leaving/idle/sleeping transmitters: indicating whether you have more to send when transmitting. 9/25/2020 12

Integrating multiple access with multiple tokens • How to put these two together – remember only the stations with tokens can transmit – define several token types: unicast, broadcast – unicast token: pure token-based allocation – broadcast token: use multiple access 9/25/2020 13

Further Issues • Two channels ? • Multicast ? – How do multiple receivers ack ? – How to solve hidden/exposed stations ? • Fairness ? – AIMD in congestion control to MAC contention • Energy efficiency issue – RTS-CTS-DATA-ACK keeps the interface on all the time • Performance evaluation 9/25/2020 14