WIRELESS LAN SECURITY Using EAP TTLS Security In











- Slides: 14

WIRELESS LAN SECURITY Using EAP - TTLS

Security - In the Broad Sense Ø Focuses on network security, system security, information security, and physical security Ø Made up of a suite of multiple technologies that solve authentication, information integrity, and identification problems. Ø Includes technologies – firewalls, authentication servers, biometrics, cryptography, intrusion detection, virus protection, and VPNs.

Wireless Network Security Issues Ø Security is an even greater problem for wireless networks Ø Use radio frequency (RF) technology, to transmit and receive data over the air Ø Authentication of network users is not strong Ø Unauthorized users can access network resources. Ø Traffic encryption is also weak, so attackers are able to recover transmissions

IEEE 802. 11 Standard Ø Wired Equivalent Privacy (WEP) Ø Static WEP Key Ø Open and Shared Authentication Ø MAC address matches an address in an authentication table used by the access point. It can be forged or NIC stolen Ø One Way Authentication (Client to AP) Ø 15 min to crack a 40 -bits key (45 min to crack 128 -bits)

802. 1 x - Authentication Methods Ø EAP defines a standard message exchange that allows a server to authenticate a client based on an authentication protocol agreed upon by both parties. Ø The access points defer to the Remote Authentication Dial-In User Service (RADIUS) server to authenticate users and to support particular EAP authentication types.

802. 1 x EAP – Authentication Types Ø EAP-Transport Layer Security (EAP-TLS) Ø Tunneled Transport Layer Security (TTLS) Ø Cisco Light Weighted EAP (LEAP) Ø Protected EAP (PEAP).

EAP – TLS and its Disadvantages Ø In EAP-TLS, certificates are used to provide authentication in both directions. Ø The server presents a certificate to the client, and, after validating the server's certificate the client presents a client certificate. Ø Requires each user to have a certificate. Ø Imposes substantial administrative burden in operating a certificate authority to distribute, revoke and manage user certificates

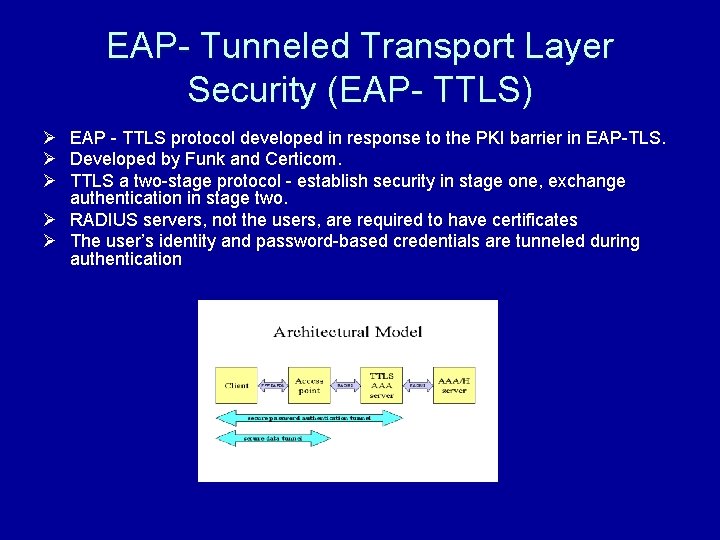
EAP- Tunneled Transport Layer Security (EAP- TTLS) Ø EAP - TTLS protocol developed in response to the PKI barrier in EAP-TLS. Ø Developed by Funk and Certicom. Ø TTLS a two-stage protocol - establish security in stage one, exchange authentication in stage two. Ø RADIUS servers, not the users, are required to have certificates Ø The user’s identity and password-based credentials are tunneled during authentication

Advantages of Using EAP – TTLS Ø Users to be authenticated with existing password credentials, and, using strong public/private key cryptography Ø Prevents dictionary attacks, man-in-the-middle attacks, and hijacked connections by wireless eavesdroppers. Ø Does not require the use of client certificates. Ø Requires little additional administration unlike EAP-TLS Ø Dynamic per-session keys are generated to encrypt the wireless connection and protect data privacy

Situations when EAP – TTLS can Fail Ø User's identity is not hidden from the EAP -TTLS server and may be included in the clear in AAA messages between the access point, the EAP-TTLS server, and the AAA/H server. Ø Server certificates within EAP-TTLS makes EAP-TTLS susceptible to attack. Ø EAP – TTLS is vulnerable to attacks by rogue EAP-TTLS servers

Comparison of EAP- TTLS and PEAP Protocols Ø Microsoft, Cisco and RSA Security developed Protected Extensible Authentication Protocol (PEAP) over 802. 11 WLANs Ø Windows XP is currently the only operating system that supports PEAP. Ø Only EAP - generic token card Ø Funk Software and Interlink Networks added support for the proposed wireless security protocol, developed by Funk and Certicom, Ø Linux, Mac OS X, Windows 95/98/ME, and Windows NT/2000/XP. Ø Any Authentication Method - CHAP, PAP, MS-CHAP, and MSCHAPv 2 and EAP

Conclusions Ø Selection of an authentication method is the key decision in securing a wireless LAN deployment. Ø EAP-TLS is best suited under situations when a well configured PKI is already deployed Ø TTLS slight degree of flexibility at the protocol level and supports wider of client operating systems. Ø No single security solution is likely to address all security risks. Hence should implement multiple approaches to completely secure wireless application access

Future Areas of Research Ø Ø Ø Implement TTLS in a Wireless LAN. Develop test benches to compare the two 802. 1 x standards EAP-TTLS and PEAP. Implement PEAP for other operating systems other than Windows – XP. Develop ways to protect security between the access point, the EAP-TTLS server, and the AAA/H server by implementing firewalls or other such viable security techniques. Alternative ways to protect the private key in EAP – TTLS servers as they are susceptible to attacks in the case where the EAP-TTLS certificates are lost or are to be compromised.

References Ø www. ietf. org/internet-drafts/draft-ietf-pppext-eapttls-02. txt Ø http: //www. nwfusion. com/research/2002/0506 ila bwlan. html Ø http: //www. oreillynet. com/pub/a/wireless/2002/1 0/17/peap. html Ø http: //www. nwfusion. com/news/2002/1111 funk. h tml Ø http: //www. nwfusion. com/news/2002/0923 peap. html