Wireless LAN Security Hackerproof Your Wireless LAN Kevin







- Slides: 27

Wireless LAN Security: Hacker-proof Your Wireless LAN Kevin Mc. Caffrey Director, Mid-Atlantic Region kmccaffrey@airdefense. net Copyright © 2002 -2005 Air. Defense Proprietary and Confidential.

Unsecured Wireless Networks can be Devastating! Wireless Networks Improve Productivity…They Also Open Backdoors, Making Security Investments Obsolete Copyright © 2002 -2005 Air. Defense Proprietary and Confidential.

Air. Defense Snapshot Focus Pioneered Advanced Wireless Intrusion Prevention Innovation 15 Patents pending; Deep Differentiated Technology with Best Detection and Protection Against the Most Sophisticated Attacks Leadership One of the Fastest Growing Companies; Absolute Market Leadership - 75%+ Market Share Customers Selected by over 400 Customers including Market Leaders in all Major Industries and Government Partners Selected by Industry Leaders e. g. Cisco, IBM, CSC and others Awards Won Numerous Industry Awards for Innovation and Recommended by Industry Analysts Copyright © 2002 -2005 Air. Defense Proprietary and Confidential.

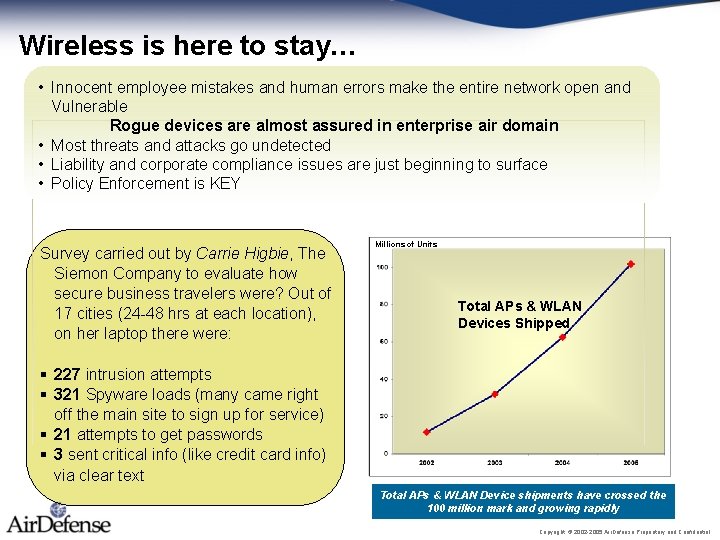
Wireless is here to stay… • Innocent employee mistakes and human errors make the entire network open and Vulnerable Rogue devices are almost assured in enterprise air domain • Most threats and attacks go undetected • Liability and corporate compliance issues are just beginning to surface • Policy Enforcement is KEY Survey carried out by Carrie Higbie, The Siemon Company to evaluate how secure business travelers were? Out of 17 cities (24 -48 hrs at each location), on her laptop there were: Millions of Units Total APs & WLAN Devices Shipped § 227 intrusion attempts § 321 Spyware loads (many came right off the main site to sign up for service) § 21 attempts to get passwords § 3 sent critical info (like credit card info) via clear text Total APs & WLAN Device shipments have crossed the 100 million mark and growing rapidly Copyright © 2002 -2005 Air. Defense Proprietary and Confidential.

Wireless LAN Risks are Real and Occurring Daily… Identity thieves can lurk at Wi-Fi spots "Wireless networks are wide open, " says Steve Lewack, director of technology services for Columbus Regional Medical Center in Columbus, Ga. Wireless Mischief Hackers, Thieves Use Laptops, Other Wi-Fi Devices to Access Corporate Computer Systems 5 Tips: Keeping your Wi-Fi use private NEW YORK (CNN/Money) - With more than 20, 000 hot spots just in the U. S. , it's no wonder everyone has gone Double Jeopardy But falling prey to an evil twin isn't just a problem for personal users. Spencer Parker, a director of Making Sense of Wireless IPS How Lehman Brothers Overcame Its Wireless Fears Air. Defense’s wireless IDS performs preliminary data analysis and cleaning at the sensor before forwarding NEW YORK - If you think that wireless applications have become completely ubiquitous in corporate LONDON, England -- "Evil twins" are the latest menace to threaten the security of Internet users, experts in the UK are warning. A Latte with a Side of Identity Theft What you need to know before your next visit to your favorite coffee shop? Wi-Fi Security stories quadrupled since last year Copyright © 2002 -2005 Air. Defense Proprietary and Confidential.

What is Driving Evolution of Wireless Security? § Drivers § Increased business dependency on Wireless § Increasing user base § At home and Hotspot use § Evolving Standards and newer technologies § VOIP § One simple issue can expose the whole corporate network § Security issues § Recreational hacker -> activist -> organized crime -> industrial espionage § Greater proliferation of viruses § Increased tooling to exploit vulnerabilities § Internal vs. external threats § Malicious intent vs. accidental Secure Wireless & Policy Compliance are keys to Successful Deployment Copyright © 2002 -2005 Air. Defense Proprietary and Confidential.

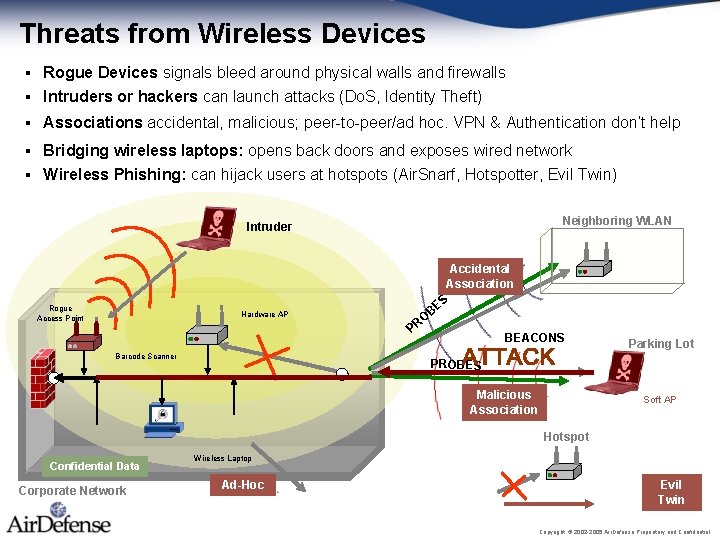
Threats from Wireless Devices Rogue Devices signals bleed around physical walls and firewalls § Intruders or hackers can launch attacks (Do. S, Identity Theft) § § Associations accidental, malicious; peer-to-peer/ad hoc. VPN & Authentication don’t help Bridging wireless laptops: opens back doors and exposes wired network § Wireless Phishing: can hijack users at hotspots (Air. Snarf, Hotspotter, Evil Twin) § Neighboring WLAN Intruder Rogue Access Point Hardware AP Barcode Scanner Accidental Association ES B O PR BEACONS Parking Lot PROBES Malicious Association Soft AP Hotspot Confidential Data Corporate Network Wireless Laptop Ad-Hoc Evil Twin Copyright © 2002 -2005 Air. Defense Proprietary and Confidential.

Tools & Trends for the Hacker Wannabe Scanners • • • • Net. Stumbler and Mini. Stumbler Kismet THC-War. Drive Prism. Stumbler Mac. Stumbler Mognet Wellenreiter Wave. Stumbler Stumbverter AP Scanner SSID Sniff Wavemon Wireless Security Auditor Air. Traf • War. Linux • Knopix www. test. com • LSAKnopix Exploit Tools • Pong “GSTsearch” • Ittra Denial of Service Wi. GLE. net • • Sniffers • • Bootable CDRom Airo. Peek NAI Wireless Sniffer Etherea VPNmonitorl Hunter_Killer VOID • FATAjack • Micheal Multi-use Tools • Air. Jack • THC-RUT • Ettercap WEP Tools § § § WEPCrack Air. Snort Wepwegie Soft AP’s § § Host. AP Cqure. AP Disk. AP Coyete Other Tools § § Fake AP Monkey. Jack Airsnarff WINPCAP Connected to www. test. com Copyright © 2002 -2005 Air. Defense Proprietary and Confidential.

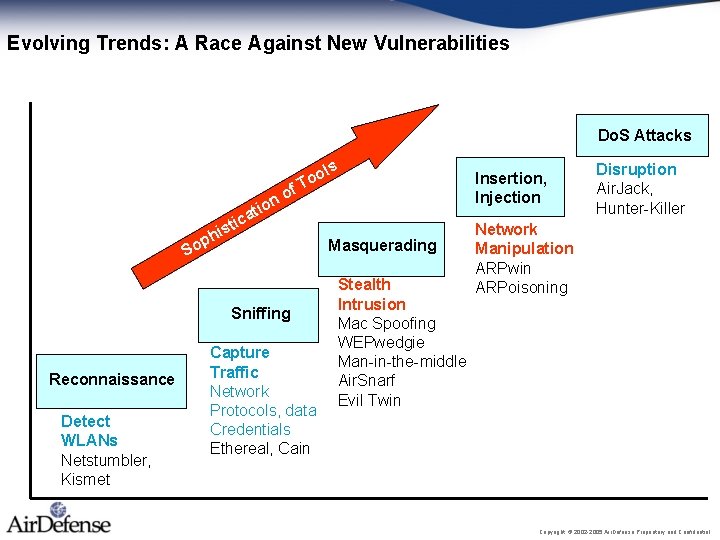
Evolving Trends: A Race Against New Vulnerabilities Do. S Attacks f o ion ols o T at tic s i h p So Sniffing Reconnaissance Detect WLANs Netstumbler, Kismet Capture Traffic Network Protocols, data Credentials Ethereal, Cain Masquerading Stealth Intrusion Mac Spoofing WEPwedgie Man-in-the-middle Air. Snarf Evil Twin Insertion, Injection Disruption Air. Jack, Hunter-Killer Network Manipulation ARPwin ARPoisoning Copyright © 2002 -2005 Air. Defense Proprietary and Confidential.

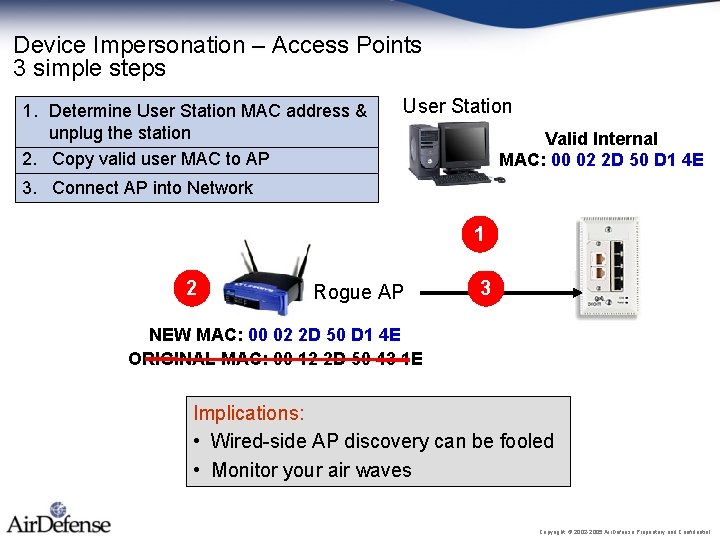
Device Impersonation – Access Points 3 simple steps 1. Determine User Station MAC address & unplug the station 2. Copy valid user MAC to AP User Station Valid Internal MAC: 00 02 2 D 50 D 1 4 E 3. Connect AP into Network 1 2 Rogue AP 3 NEW MAC: 00 02 2 D 50 D 1 4 E ORIGINAL MAC: 00 12 2 D 50 43 1 E Implications: • Wired-side AP discovery can be fooled • Monitor your air waves Copyright © 2002 -2005 Air. Defense Proprietary and Confidential.

Soft AP: Make any Laptop an AP Freeware: Host. AP http: //hostap. epitest. fi/ RPM install for 8. 0 and 9. 0 of Redhat http: //www. cat. pdx. edu/~baera/redhat_hostap/ § No special firmware required for the wireless LAN card § Supports normal laptop in Infrastructure and Ad hoc § Soft APs come and go Bootable Floppy disk http: //ap. cqure. net/ , http: //www. coyotelinux. com/ Monitor for Soft APs Copyright © 2002 -2005 Air. Defense Proprietary and Confidential.

Now Coming to a Windows LAPTOP Near YOU! http: //www. pctel. com/prod. Seg. Sam. html http: //www. quetec. net Copyright © 2002 -2005 Air. Defense Proprietary and Confidential.

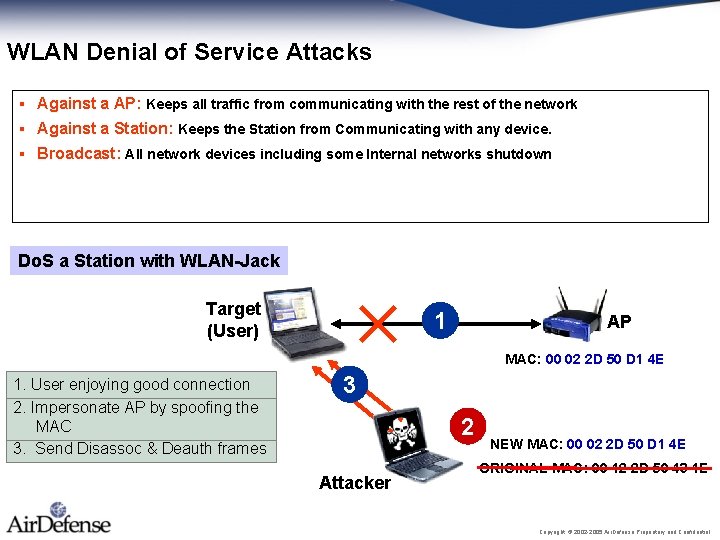
WLAN Denial of Service Attacks § Against a AP: Keeps all traffic from communicating with the rest of the network § Against a Station: Keeps the Station from Communicating with any device. § Broadcast: All network devices including some Internal networks shutdown Do. S a Station with WLAN-Jack Target (User) 1 AP MAC: 00 02 2 D 50 D 1 4 E 1. User enjoying good connection 2. Impersonate AP by spoofing the MAC 3. Send Disassoc & Deauth frames 3 2 Attacker NEW MAC: 00 02 2 D 50 D 1 4 E ORIGINAL MAC: 00 12 2 D 50 43 1 E Copyright © 2002 -2005 Air. Defense Proprietary and Confidential.

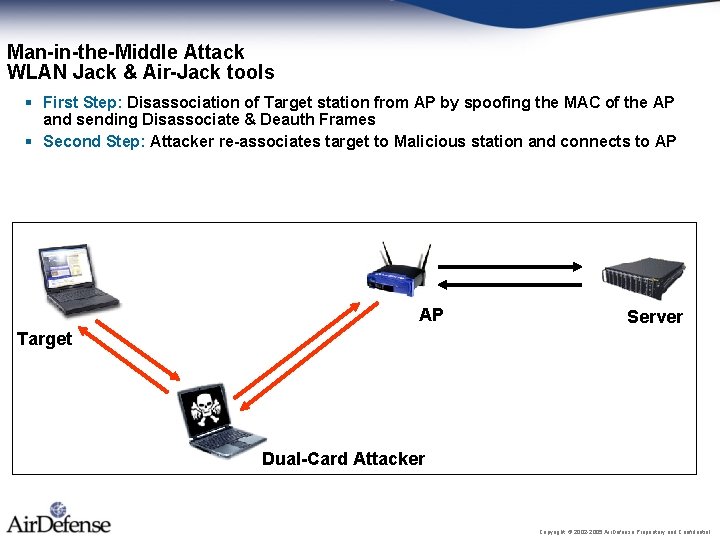
Man-in-the-Middle Attack WLAN Jack & Air-Jack tools § First Step: Disassociation of Target station from AP by spoofing the MAC of the AP and sending Disassociate & Deauth Frames § Second Step: Attacker re-associates target to Malicious station and connects to AP AP Server Target Dual-Card Attacker Copyright © 2002 -2005 Air. Defense Proprietary and Confidential.

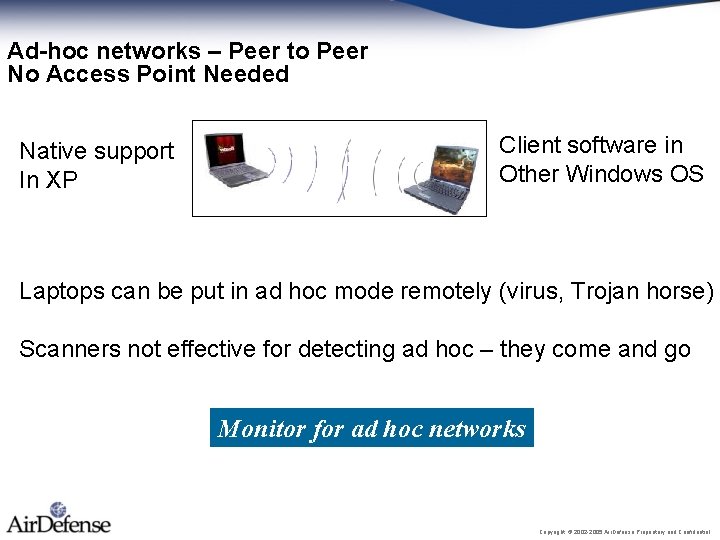
Ad-hoc networks – Peer to Peer No Access Point Needed Native support In XP Client software in Other Windows OS Laptops can be put in ad hoc mode remotely (virus, Trojan horse) Scanners not effective for detecting ad hoc – they come and go Monitor for ad hoc networks Copyright © 2002 -2005 Air. Defense Proprietary and Confidential.

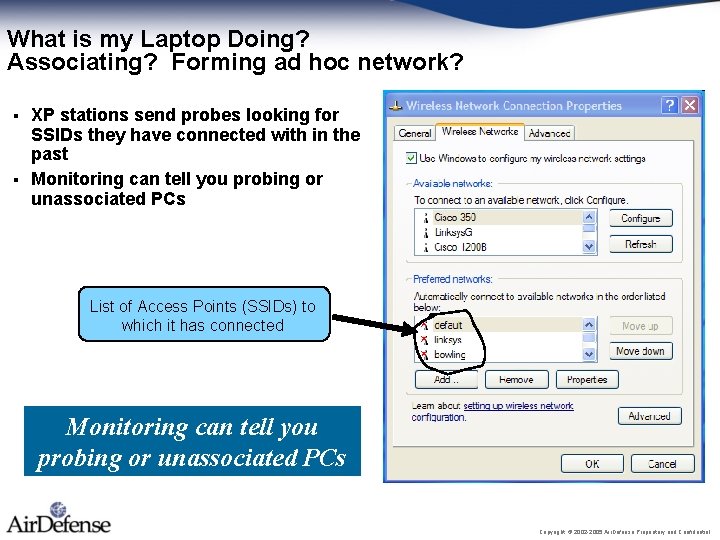
What is my Laptop Doing? Associating? Forming ad hoc network? XP stations send probes looking for SSIDs they have connected with in the past § Monitoring can tell you probing or unassociated PCs § List of Access Points (SSIDs) to which it has connected Monitoring can tell you probing or unassociated PCs Copyright © 2002 -2005 Air. Defense Proprietary and Confidential.

Wireless LANs: End-to-End Security Wireless Monitoring & IPS System Layered Approach to Security Copyright © 2002 -2005 Air. Defense Proprietary and Confidential.

Handheld Scanners What it does: § Manually Used to Troubleshoot Issues in Specific Areas § Used for War driving & periodic site surveys Pros: Cons: § Inexpensive tool; expensive labor and risks § Single Snapshot in time: ONLY sees what is present at time of survey § Uncorrelated Information § Not cost effective “Current radio frequency scanning tools such as Sniffer and Air. Magnet are limited in their ability to perform scalable and repeatable audits. ” META Group, September 2002 § Need Personnel resources per site § Not scalable for large organizations § Distributed enterprises become difficult to monitor with regularity § Lacks central manageability and operations § Reporting and analysis is manual § ONLY sees what is present at time of survey Copyright © 2002 -2005 Air. Defense Proprietary and Confidential.

Purpose-built Monitoring & IDS/IPS What it does: § Enterprise-Wide 24 x 7 Full-Time Monitoring and Reporting Pros: Cons: § Comprehensive Enterprise View for APs and all WLAN devices § Highest security level § Most detailed reporting § Enhanced operational support § Requires additional infrastructure Copyright © 2002 -2005 Air. Defense Proprietary and Confidential.

Expert Opinion on Wireless Monitoring “Through 2006, 70 % of successful WLAN attacks will be because of the misconfiguration of APs or client software. ” “Wireless devices create backdoors for hackers and can render firewalls, IDS and VPNs useless. ” Incorrectly set-up WLANs put the wired LAN as risk as well” “Unmanaged WLANs can jeopardize entire enterprise network, data and operations” WLAN security monitoring is necessary to keep your enterprise secure “New sophisticated security risks continue to emerge as wireless matures” “The signature, correlation and behavior analysis that Air. Defense brings to the table is best in class ” “Best all around wireless IDS solution in our lab tests” Copyright © 2002 -2005 Air. Defense Proprietary and Confidential.

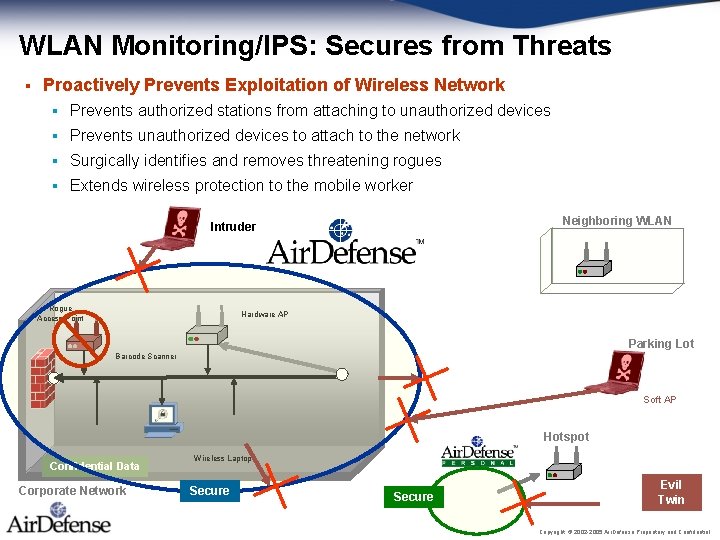
WLAN Monitoring/IPS: Secures from Threats § Proactively Prevents Exploitation of Wireless Network § Prevents authorized stations from attaching to unauthorized devices § Prevents unauthorized devices to attach to the network § Surgically identifies and removes threatening rogues § Extends wireless protection to the mobile worker Neighboring WLAN Intruder Rogue Access Point Hardware AP Parking Lot Barcode Scanner Soft AP Hotspot Confidential Data Corporate Network Wireless Laptop Secure Evil Twin Copyright © 2002 -2005 Air. Defense Proprietary and Confidential.

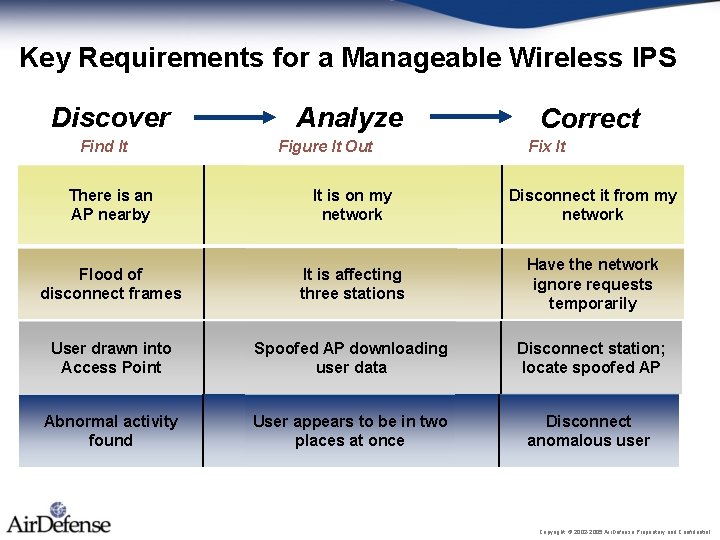
Key Requirements for a Manageable Wireless IPS Discover Find It Analyze Figure It Out Correct Fix It There is an AP nearby It is on my network Disconnect it from my network Flood of disconnect frames It is affecting three stations Have the network ignore requests temporarily User drawn into Access Point Spoofed AP downloading user data Disconnect station; locate spoofed AP Abnormal activity found User appears to be in two places at once Disconnect anomalous user Copyright © 2002 -2005 Air. Defense Proprietary and Confidential.

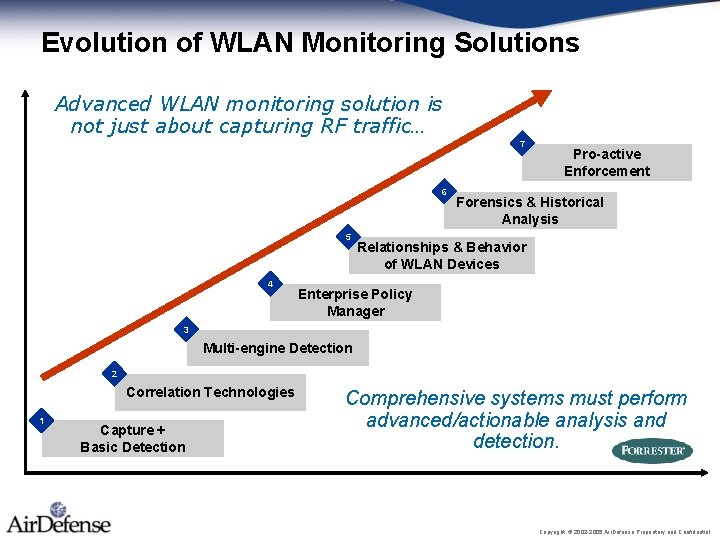
Evolution of WLAN Monitoring Solutions Advanced WLAN monitoring solution is not just about capturing RF traffic… 7 6 5 4 Pro-active Enforcement Forensics & Historical Analysis Relationships & Behavior of WLAN Devices Enterprise Policy Manager 3 Multi-engine Detection 2 Correlation Technologies 1 Capture + Basic Detection Comprehensive systems must perform advanced/actionable analysis and detection. Copyright © 2002 -2005 Air. Defense Proprietary and Confidential.

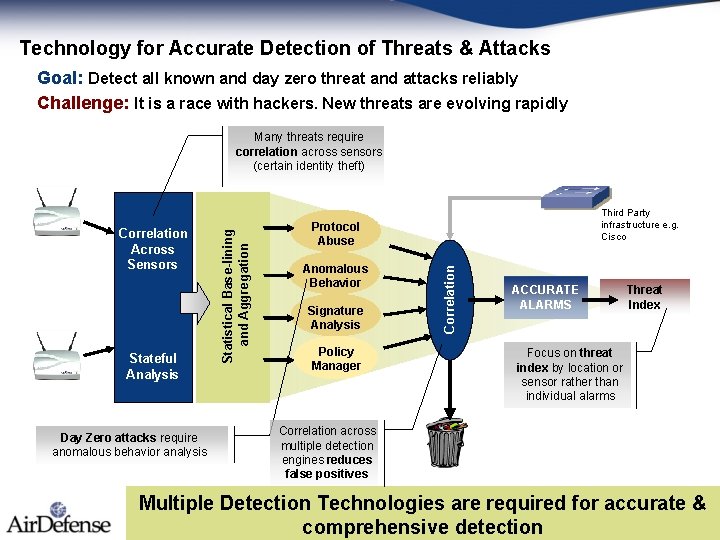
Technology for Accurate Detection of Threats & Attacks Goal: Detect all known and day zero threat and attacks reliably Challenge: It is a race with hackers. New threats are evolving rapidly Stateful Analysis Day Zero attacks require anomalous behavior analysis Third Party infrastructure e. g. Cisco Protocol Abuse Anomalous Behavior Signature Analysis Policy Manager Correlation Across Sensors Statistical Base-lining and Aggregation Many threats require correlation across sensors (certain identity theft) ACCURATE ALARMS Threat Index Focus on threat index by location or sensor rather than individual alarms Correlation across multiple detection engines reduces false positives Multiple Detection Technologies are required for accurate & comprehensive detection Copyright © 2002 -2005 Air. Defense Proprietary and Confidential.

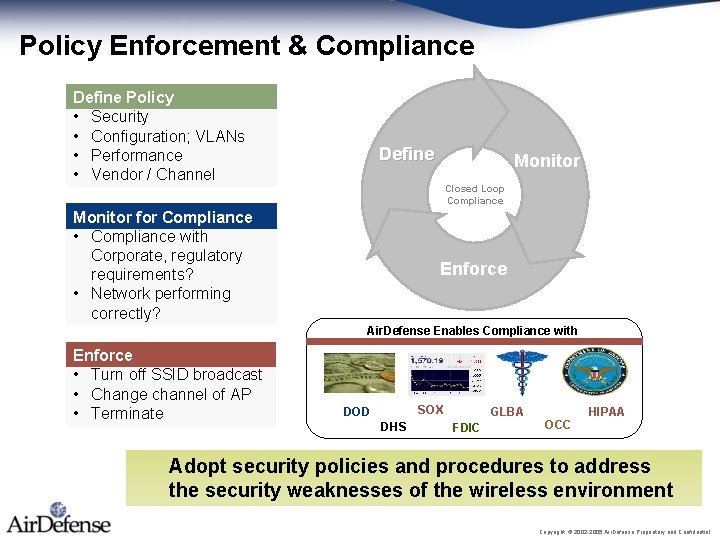
Policy Enforcement & Compliance Define Policy • Security • Configuration; VLANs • Performance • Vendor / Channel Define Monitor Closed Loop Compliance Monitor for Compliance • Compliance with Corporate, regulatory requirements? • Network performing correctly? Enforce Air. Defense Enables Compliance with Enforce • Turn off SSID broadcast • Change channel of AP • Terminate SOX DOD DHS GLBA FDIC HIPAA OCC Adopt security policies and procedures to address the security weaknesses of the wireless environment Copyright © 2002 -2005 Air. Defense Proprietary and Confidential.

Misconceptions of Security Don’t get caught with a false sense of security. Monitor your air domain for threats and policy compliance. Secured Area Copyright © 2002 -2005 Air. Defense Proprietary and Confidential.

Summary: Wireless LAN can be Secured 1. 2. 3. 4. 5. 6. WLAN Risks are Significant Due to § Shared Broadcast Media Every Organization has WLANs (rogue and/or sanctioned) § Check out wigle. net Probing Laptops are Serious & Often Ignored Threat § Employee use of wireless at home is pervasive WLAN Policy Enforcement is Required § Define > Monitor > Enforce When deploying, use layered security approach § Encryption > Authentication > 24 X 7 RF Monitoring Have Control over your Air Domain § Assets > Relationships > Behavior Copyright © 2002 -2005 Air. Defense Proprietary and Confidential.