Wireless LAN Security Daniel Reichle Seminar Security Protocols













![References • • • [1] Nikita Borisov, Ian Goldberg, David Wagner: Intercepting Mobile Communications: References • • • [1] Nikita Borisov, Ian Goldberg, David Wagner: Intercepting Mobile Communications:](https://slidetodoc.com/presentation_image_h/9e65e7aa54a8af36155bb6d0236be328/image-22.jpg)
- Slides: 22

Wireless LAN Security Daniel Reichle Seminar Security Protocols and Applications SS 2003 Wireless LAN Security

Threats against WLANS • Same threats as against wired LANs (eavesdropping, message modification, unauthorized access, denial of service) • Access to shared medium is easy • Dangerous configuration of WLANS Wireless LAN Security 2

Wireless LAN Security 3

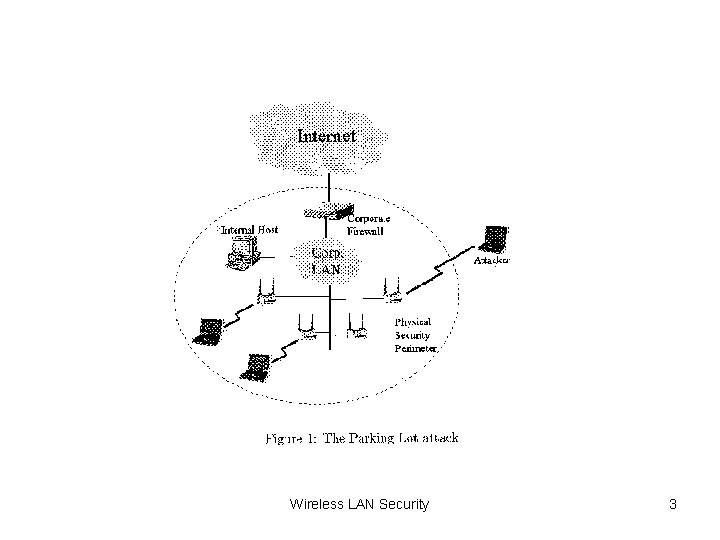
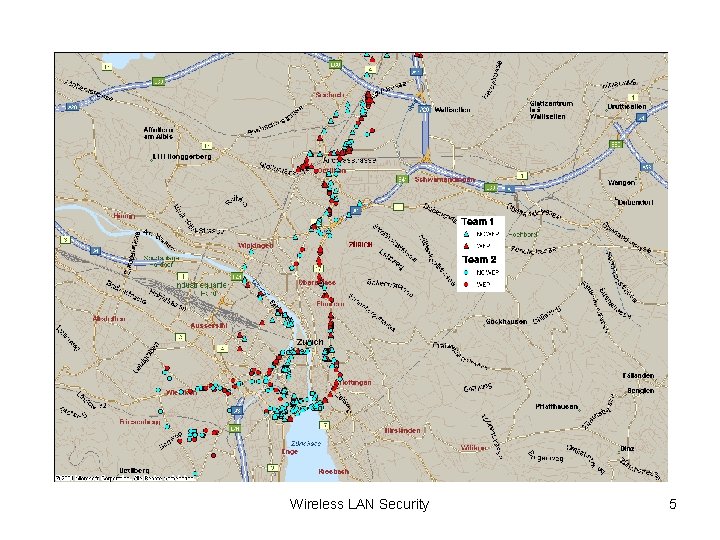
Threats against WLANS (2) • Finding WLANs is easy • Wardriving: search for access points and publishing unprotected WLANs Wireless LAN Security 4

Wireless LAN Security 5

IEEE 802. 11 • • Actual version 802. 11 b Layer 2 standard Peer-to-peer / via access point Similar to 802. 3 (Ethernet) Open System Authentication Shared Key Authentication Wired Equivalent Privacy Wireless LAN Security 6

Wired Equivalent Privacy (WEP) • Should provide an equivalent level of access control and protection of data on the WLAN as in wired networks • Main security goals: confidentiality, access control, data integrity Wireless LAN Security 7

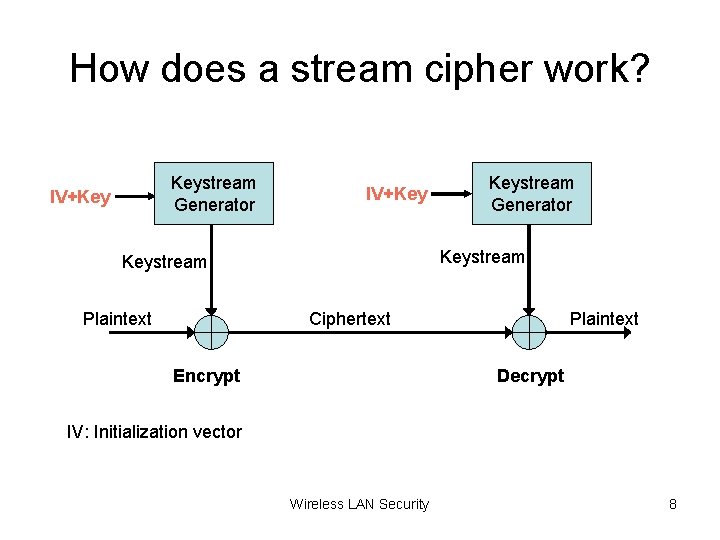
How does a stream cipher work? Keystream Generator IV+Key Keystream Plaintext Keystream Generator Ciphertext Encrypt Plaintext Decrypt IV: Initialization vector Wireless LAN Security 8

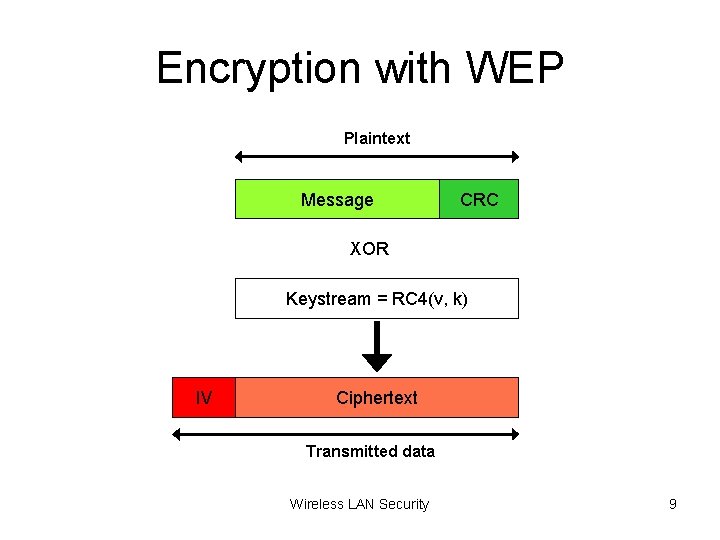
Encryption with WEP Plaintext Message CRC XOR Keystream = RC 4(v, k) IV Ciphertext Transmitted data Wireless LAN Security 9

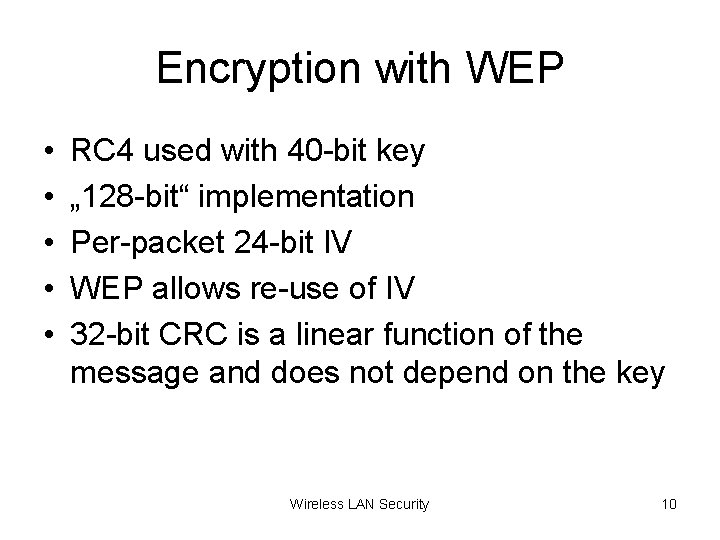
Encryption with WEP • • • RC 4 used with 40 -bit key „ 128 -bit“ implementation Per-packet 24 -bit IV WEP allows re-use of IV 32 -bit CRC is a linear function of the message and does not depend on the key Wireless LAN Security 10

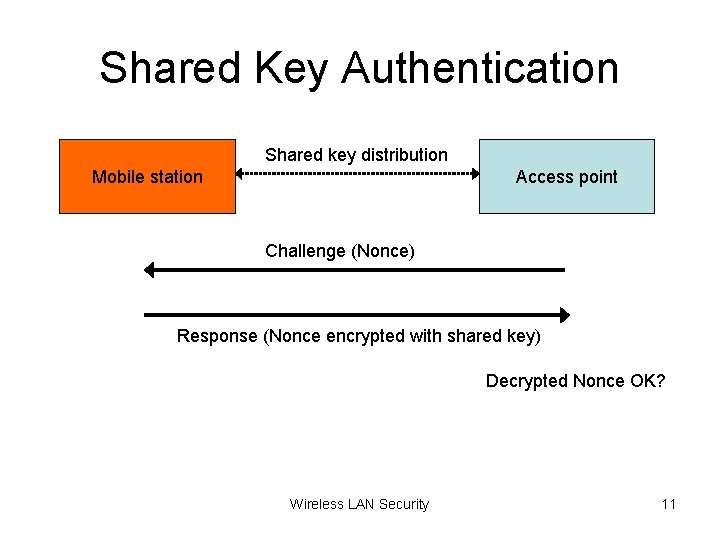
Shared Key Authentication Shared key distribution Mobile station Access point Challenge (Nonce) Response (Nonce encrypted with shared key) Decrypted Nonce OK? Wireless LAN Security 11

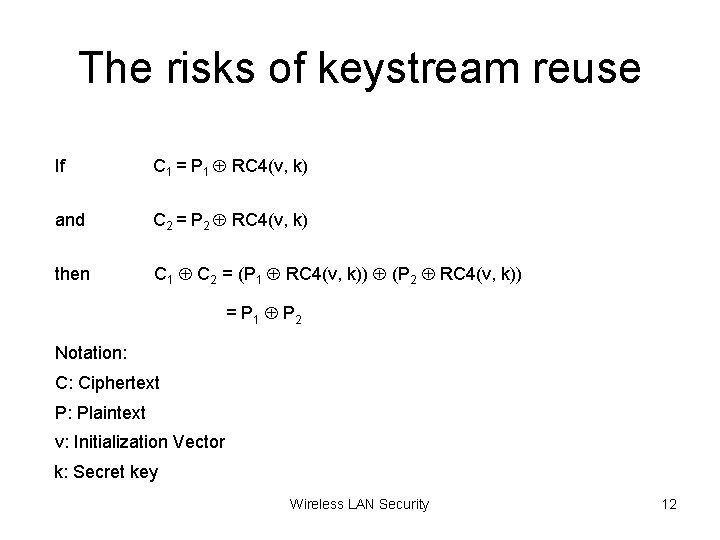
The risks of keystream reuse If C 1 = P 1 RC 4(v, k) and C 2 = P 2 RC 4(v, k) then C 1 C 2 = (P 1 RC 4(v, k)) (P 2 RC 4(v, k)) = P 1 P 2 Notation: C: Ciphertext P: Plaintext v: Initialization Vector k: Secret key Wireless LAN Security 12

The risk of keystream reuse (2) • WEP uses per-packet IV to prevent these attacks • Change of IV after every packet recommended (not required!) • 24 -bit IV nearly guaranteeing the same IV to be reused for multiple messages • Bad handling of IV selection in some implementations Wireless LAN Security 13

Exploiting keystream reuse • Find two packets, encrypted with same IV (Birthday paradoxon: 50% chance of a collision after only 4823 packets) • Plaintext of one of the messages has to be known • Provoke known plaintext to be transmitted • Decryption dictionaries Wireless LAN Security 14

Message modification • WEP checksum is a linear function CRC(x y) = CRC(x) CRC(y) • Scenario: we have intercepted a message C = RC 4(v, k) <M, CRC(M)> • Is it possible to find a new ciphertext C‘ that decrypts to M‘, where M‘ = M ? ( arbitrarily chosen) Wireless LAN Security 15

Message modification (2) • How to get C‘ from C C = RC 4(v, k) <M, CRC(M)> M‘ = M C‘ = C < , CRC( )> = RC 4(v, k) <M, CRC(M)> < , CRC( )> = RC 4(v, k) <M , CRC(M) CRC( )> = RC 4(v, k) <M‘, CRC(M‘)> Wireless LAN Security 16

Authentication spoofing • Observe an legitimate authentication sequence • Known plaintext/ciphertext pair enables us to derive the used keystream: RC 4(v, k) = C P • Use keystream to encrypt any subsequent challenge • Authentication is possible without knowledge of the key Wireless LAN Security 17

Decryption via IP redirection • Idea: sniff a encrypted packet, modify the destination IP address, send it to the WEP access point → AP will send us the decrypted packet • Figuring out what the original IP address was is easy • New checksum has to be correct Wireless LAN Security 18

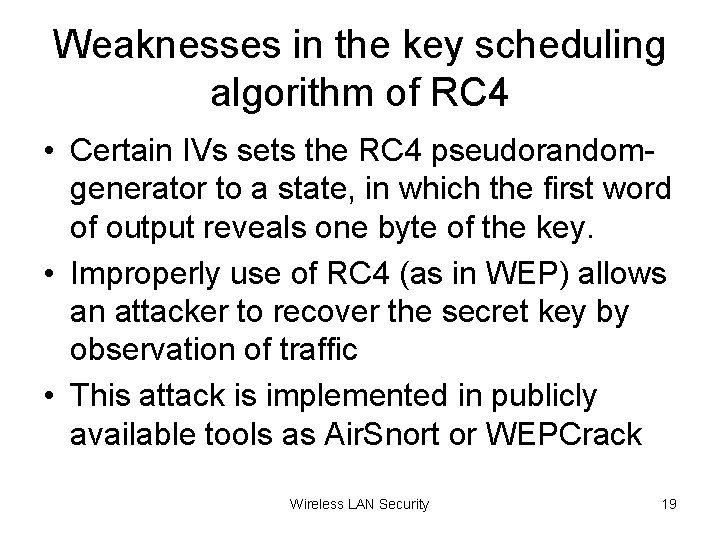
Weaknesses in the key scheduling algorithm of RC 4 • Certain IVs sets the RC 4 pseudorandomgenerator to a state, in which the first word of output reveals one byte of the key. • Improperly use of RC 4 (as in WEP) allows an attacker to recover the secret key by observation of traffic • This attack is implemented in publicly available tools as Air. Snort or WEPCrack Wireless LAN Security 19

IEEE 802. 11 in the future • 802. 11 X as an enhancement of the today‘s standard • Features: authentication via an authentication server, use of digital certificates, dynamic distribution of keys • New IEEE standard 802. 11 i will include 802. 11 X and strong encryption (AES) Wireless LAN Security 20

Solutions for today‘s WLANs • Treat link layer as insecure • Usage of higher level security protocols (IPsec, SSL, SSH) • Access points outside the firewall Wireless LAN Security 21
![References 1 Nikita Borisov Ian Goldberg David Wagner Intercepting Mobile Communications References • • • [1] Nikita Borisov, Ian Goldberg, David Wagner: Intercepting Mobile Communications:](https://slidetodoc.com/presentation_image_h/9e65e7aa54a8af36155bb6d0236be328/image-22.jpg)
References • • • [1] Nikita Borisov, Ian Goldberg, David Wagner: Intercepting Mobile Communications: The Insecurity of 802. 11, In Proceedings of 7 th International Conference on Mobile Computing and Networking 2001 (Mobicom 2001). [2] Bill Arbaugh's Web Page über viele bekannte Sicherheitsschwächen von 802. 11. [3] Scott Fluhrer, Martin Itsik, Adi Shamir: Weaknesses in the Key Scheduling Algorithm of RC 4. In Proceedings of 8 th Annual Workshop on Selected Areas in Cryptography (August 2001). [4] Adam Stubblefield, John Ioannidis, Aviel Rubin: Using the Fluhrer, Mantin, and Shamir Attack to Break WEP. AT&T Labs Technical Report TD-4 ZCPZZ, Revision 2, August 21, 2001. [5] William A. Arbaugh, Narendar Shankar, Y. C. Justin Wan: Your 802. 11 Wireless Network has No Clothes. Department of Computer Science, University of Maryland, College Park, Maryland 20742, March 30, 2001 Wireless LAN Security 22