Wireless Guest Access Solutions Overview and Positioning Why
























- Slides: 45

Wireless Guest Access Solutions Overview and Positioning

Why this presentation? WLC CMX EMSP ISE https: //isepb. cisco. com © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 2

What we will not cover ISG – Intelligent Services Gateway http: //www. cisco. com/c/en/us/products/collateral/ios-nx-os-software/intelligent-services-gateway-isg/prod_bulletin 0900 aecd 804 a 2 c 70. html More dedicated to SP scenarios. In some use cases it might be used as an alternative to the presented solutions, in case scalability limits are hit. © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 3

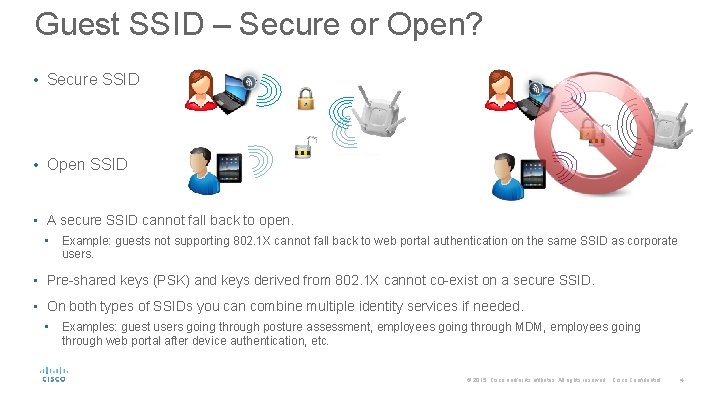
Guest SSID – Secure or Open? • Secure SSID • Open SSID • A secure SSID cannot fall back to open. • Example: guests not supporting 802. 1 X cannot fall back to web portal authentication on the same SSID as corporate users. • Pre-shared keys (PSK) and keys derived from 802. 1 X cannot co-exist on a secure SSID. • On both types of SSIDs you can combine multiple identity services if needed. • Examples: guest users going through posture assessment, employees going through MDM, employees going through web portal after device authentication, etc. © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 4

To PSK or not to PSK? • Q: Can I deploy PSK on top of web auth? A: Yes. But… • It is not much more secure than Open, since all users will anyway share the same key. • It adds extra burden to the end users, who would need to ask for the PSK to the helpdesk. • PSK + LWA has always been supported. PSK + CWA is supported starting from Aire. OS 8. 3. • Q: Hey Cisco, why don’t you deploy a guest portal at Cisco Live? A: We cannot / don’t want to because: • The WLC has a limitation of up to 2, 000 clients in the WEBAUTH_REQD run state (i. e. , being redirected to the web portal and not yet fully authorized). • For such a big event with thousands of users, we prefer to avoid passersby to connect to the Cisco Live network from the street and to add even more clients. © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 5

WLC native guest © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 6

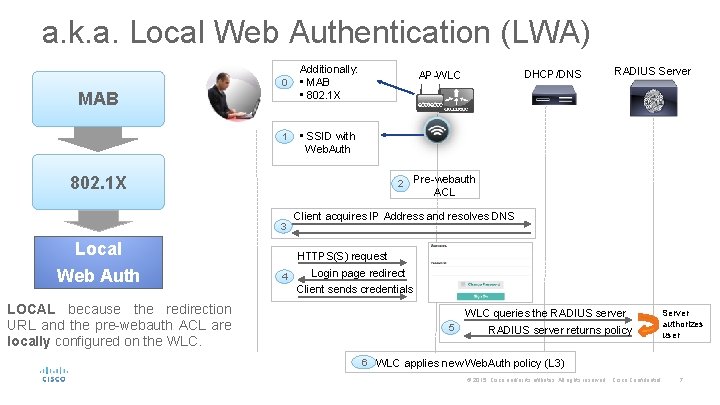
a. k. a. Local Web Authentication (LWA) 0 MAB 1 Additionally: • MAB • 802. 1 X 2 Local Web Auth RADIUS Server • SSID with Web. Auth 802. 1 X 3 DHCP/DNS AP-WLC Pre-webauth ACL Client acquires IP Address and resolves DNS HTTPS(S) request 4 Login page redirect Client sends credentials LOCAL because the redirection URL and the pre-webauth ACL are locally configured on the WLC queries the RADIUS server 5 RADIUS server returns policy Server authorizes user 6 WLC applies new Web. Auth policy (L 3) 7 © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 7

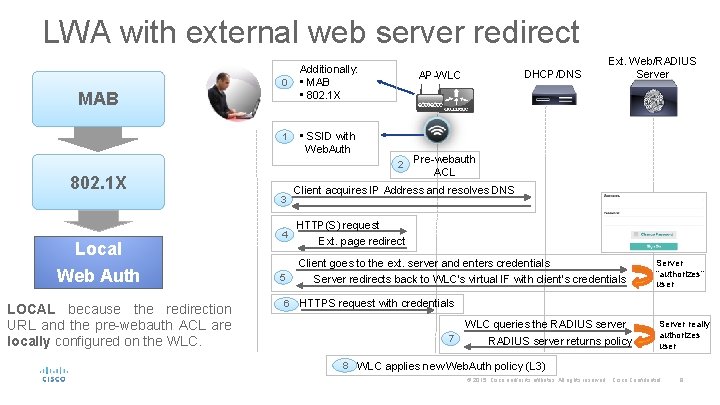
LWA with external web server redirect 0 MAB 1 Additionally: • MAB • 802. 1 X • SSID with Web. Auth 2 802. 1 X 3 Local Web Auth LOCAL because the redirection URL and the pre-webauth ACL are locally configured on the WLC. 4 5 6 DHCP/DNS AP-WLC Ext. Web/RADIUS Server Pre-webauth ACL Client acquires IP Address and resolves DNS HTTP(S) request Ext. page redirect Client goes to the ext. server and enters credentials Server redirects back to WLC’s virtual IF with client’s credentials Server “authorizes” user HTTPS request with credentials WLC queries the RADIUS server 7 RADIUS server returns policy Server really authorizes user 8 WLC applies new Web. Auth policy (L 3) © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 8

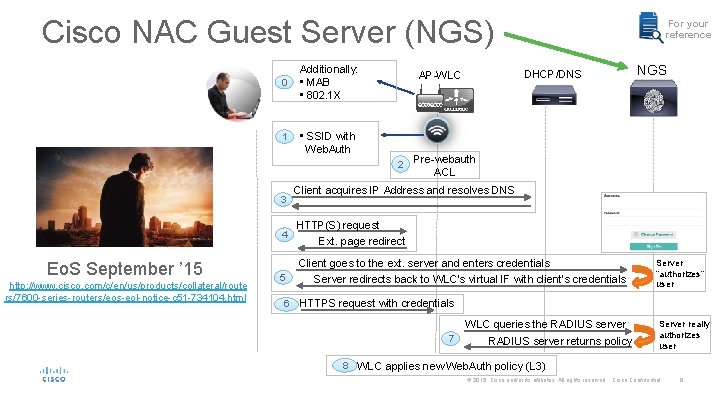
Cisco NAC Guest Server (NGS) 0 1 Additionally: • MAB • 802. 1 X 2 3 4 Eo. S September ’ 15 http: //www. cisco. com/c/en/us/products/collateral/route rs/7600 -series-routers/eos-eol-notice-c 51 -734104. html 5 6 DHCP/DNS AP-WLC • SSID with Web. Auth For your reference NGS Pre-webauth ACL Client acquires IP Address and resolves DNS HTTP(S) request Ext. page redirect Client goes to the ext. server and enters credentials Server redirects back to WLC’s virtual IF with client’s credentials Server “authorizes” user HTTPS request with credentials WLC queries the RADIUS server 7 RADIUS server returns policy Server really authorizes user 8 WLC applies new Web. Auth policy (L 3) © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 9

LWA – configuration example For your reference http: //www. cisco. com/c/en/us/support/docs/wireless-mobility/wlan-security/115951 -web-auth-wlc-guide-00. html © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 10 10

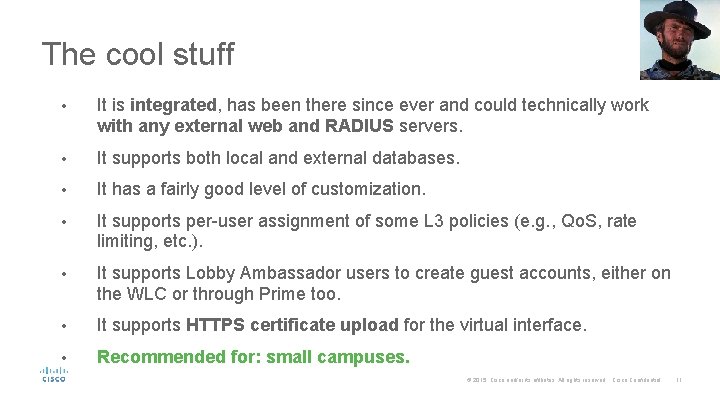
The cool stuff • It is integrated, has been there since ever and could technically work with any external web and RADIUS servers. • It supports both local and external databases. • It has a fairly good level of customization. • It supports per-user assignment of some L 3 policies (e. g. , Qo. S, rate limiting, etc. ). • It supports Lobby Ambassador users to create guest accounts, either on the WLC or through Prime too. • It supports HTTPS certificate upload for the virtual interface. • Recommended for: small campuses. © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 11

Let’s be aware that… • The local database is limited to 2048 entries max. • It is not as easy as ISE or CMX to customize. • The Lobby Ambassador interface is not customizable and has limited options (e. g. , no SMS support). • The WLC’s web engine is limited to ~150 logins/sec and 2, 000 clients in the WEBAUTH_REQD run state. • With external portals, we’d need to trust 2 different certificates: the WLC virtual interface’s and the external web server’s. © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 12

Some more options with Prime © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 13

CMX Connect © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 14

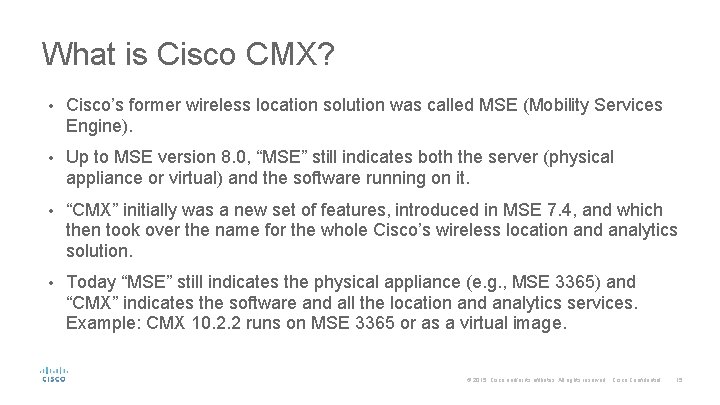
What is Cisco CMX? • Cisco’s former wireless location solution was called MSE (Mobility Services Engine). • Up to MSE version 8. 0, “MSE” still indicates both the server (physical appliance or virtual) and the software running on it. • “CMX” initially was a new set of features, introduced in MSE 7. 4, and which then took over the name for the whole Cisco’s wireless location and analytics solution. • Today “MSE” still indicates the physical appliance (e. g. , MSE 3365) and “CMX” indicates the software and all the location and analytics services. Example: CMX 10. 2. 2 runs on MSE 3365 or as a virtual image. © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 15

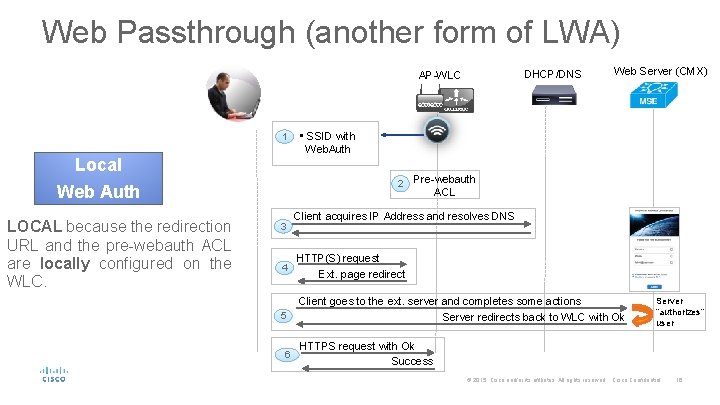
Web Passthrough (another form of LWA) DHCP/DNS AP-WLC 1 Local • SSID with Web. Auth 2 Web Auth LOCAL because the redirection URL and the pre-webauth ACL are locally configured on the WLC. 3 4 5 6 Web Server (CMX) Pre-webauth ACL Client acquires IP Address and resolves DNS HTTP(S) request Ext. page redirect Client goes to the ext. server and completes some actions Server redirects back to WLC with Ok Server “authorizes” user HTTPS request with Ok Success © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 16

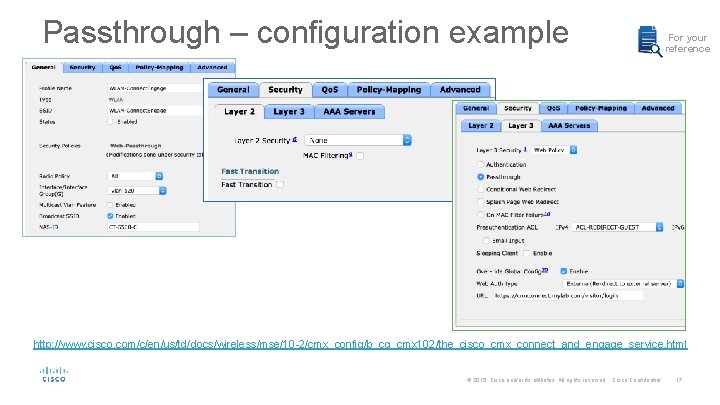
Passthrough – configuration example For your reference http: //www. cisco. com/c/en/us/td/docs/wireless/mse/10 -2/cmx_config/b_cg_cmx 102/the_cisco_cmx_connect_and_engage_service. html © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 17 17

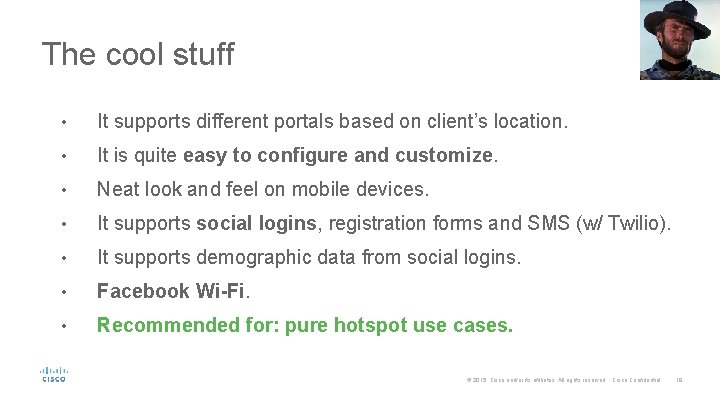
The cool stuff • It supports different portals based on client’s location. • It is quite easy to configure and customize. • Neat look and feel on mobile devices. • It supports social logins, registration forms and SMS (w/ Twilio). • It supports demographic data from social logins. • Facebook Wi-Fi. • Recommended for: pure hotspot use cases. © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 18

Let’s be aware that… • No integration with external SIEM solutions for guest logging. For such a need, a FW/proxy should be used. • It does not support dynamic L 2/L 3 policies assignment. • Customization is limited (e. g. , pre-canned elements, no native multi-language support, etc. ). • It is still limited by the WLC’s ~150 logins/sec. and 2, 000 clients in the WEBAUTH_REQD run state. © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 19

Enterprise Mobility Services Platform (EMSP) © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 20

Web Passthrough (kind of LWA) DHCP/DNS AP-WLC 1 Local • SSID with Web. Auth 2 Web Auth LOCAL because the redirection URL and the pre-webauth ACL are locally configured on the WLC. 3 4 5 6 Web Server (EMSP) Pre-webauth ACL Client acquires IP Address and resolves DNS HTTP(S) request Ext. page redirect Client goes to the ext. server and completes some actions Server redirects back to WLC with Ok Server “authorizes” user HTTPS request with Ok Success © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 21

Passthrough – configuration example For your reference Internal only: http: //iwe. cisco. com/web/view-post/-/posts? post. Id=775600122 © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 22 22

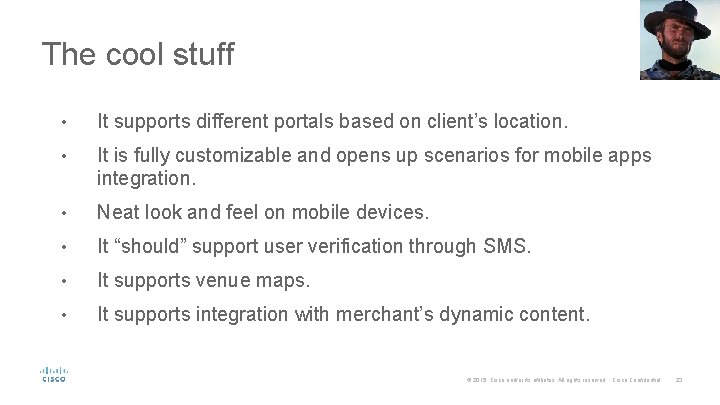
The cool stuff • It supports different portals based on client’s location. • It is fully customizable and opens up scenarios for mobile apps integration. • Neat look and feel on mobile devices. • It “should” support user verification through SMS. • It supports venue maps. • It supports integration with merchant’s dynamic content. © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 23

The less cool stuff • It does not support login/password, hence no external databases, Sponsor/Lobby Ambassador, etc. • It does not support L 2/L 3 policies assignment. • Full customization may become quite complex for casual users. • It becomes very cumbersome to centralize users information for guest traffic logging. • It is still limited by the WLC’s ~150 logins/sec. and 2000 clients in the WEBAUTH_REQD run state. • It is technically sold as a SW product, but AS might quickly become necessary. © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 24

For more details http: //www. cisco. com/c/en/us/support/wireless/enterprise-mobilityservices-platform/tsd-products-support-series-home. html and http: //www. cisco. com/c/dam/en/us/td/docs/solutions/Enterprise/Mobilit y/Mobility_Services/EMSP/emsp-3 -0/Cisco-Wi. Fi-Engage-with-CUWNConfiguration-Guide. pdf It’s a Cisco cloud based solution, usually purchased by partners, and which can then be proposed as a service to end customers. © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 25

ISE Guest Portal © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 26

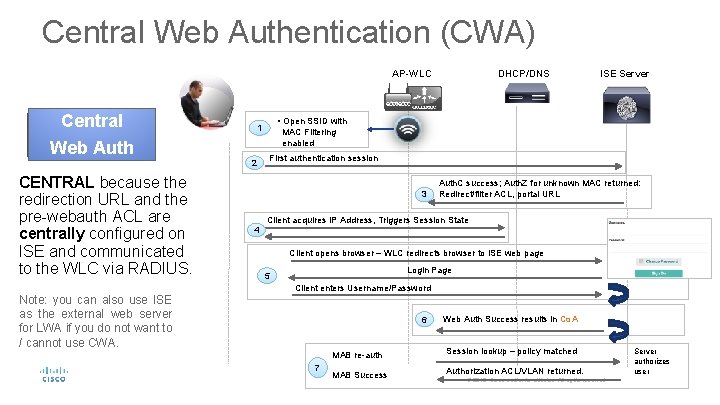
Central Web Authentication (CWA) AP-WLC Central 2 CENTRAL because the redirection URL and the pre-webauth ACL are centrally configured on ISE and communicated to the WLC via RADIUS. Note: you can also use ISE as the external web server for LWA if you do not want to / cannot use CWA. ISE Server • Open SSID with 1 Web Auth DHCP/DNS MAC Filtering enabled First authentication session 3 Auth. C success; Auth. Z for unknown MAC returned: Redirect/filter ACL, portal URL Client acquires IP Address, Triggers Session State 4 Client opens browser – WLC redirects browser to ISE web page Login Page 5 Client enters Username/Password 6 7 Web Auth Success results in Co. A MAB re-auth Session lookup – policy matched MAB Success Authorization ACL/VLAN returned. 27 Server authorizes user © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 27

CWA – configuration example For your reference http: //www. cisco. com/c/en/us/support/docs/security/identity-services-engine/115732 -central-web-auth-00. html © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 28

The cool stuff • It has the most complete set of options for guest access verification (self-service, SMS, email, common code, etc. ). • It is fully customizable, even with the Portal builder on Cisco cloud: https: //isepb. cisco. com • It’s the only solution supporting assignment of both L 2 and L 3 policies. • It supports both internal and external databases. • It supports up to 1 M local guest accounts, different portals based on client’s location and certificate(s) on ISE only. © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 33

The less cool stuff • CWA does not work with non-Cisco network devices nowadays (it should be addressed in ISE 2. 0). • The admin needs to be familiar with access control solutions and techniques (e. g. , LWA vs. CWA). • Even if there are dedicated “portal admins” using the Portal Builder, it is up to the “ISE admin” to configure portal policies. • The guest database cannot be exported/backed up. • Guest portals are limited to ~150 logins/sec per PSN (3495). You can still load balance between PSN’s. • It does not support social logins (yet). © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 34

How about Meraki? © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 35

It’s not all just about guests… • Usually customers choose Cloud vs. On Premise based on other major needs, rather than guest. • In case the customer chose Meraki, the major features for guests would be: o Easy portal customization. o Internal and external database support for RADIUS o o o authentication. SMS authentication with Twilio. Integration with a billing system. Integration with Meraki’s MDM. Some Sponsor/Lobby Ambassador options. Support for ISE CWA. © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 36

What customers also ask for © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 37

How can I support payments by credit card? You should have hurried up and bought the previous NAC Guest Server solution (Eo. S Sept. ‘ 15) Support for a single provider. Not too many asks. http: //www. cisco. com/c/en/us/td/docs/security/nac/guestserver/configuration_guide/21/nacguestserver/g_hotspots. html#wp 1068767 © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 38

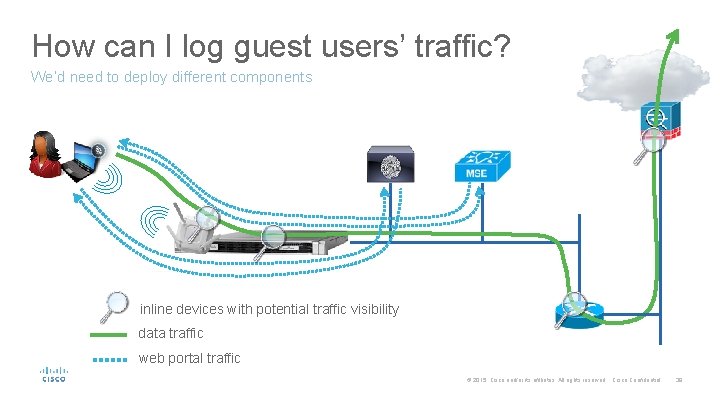
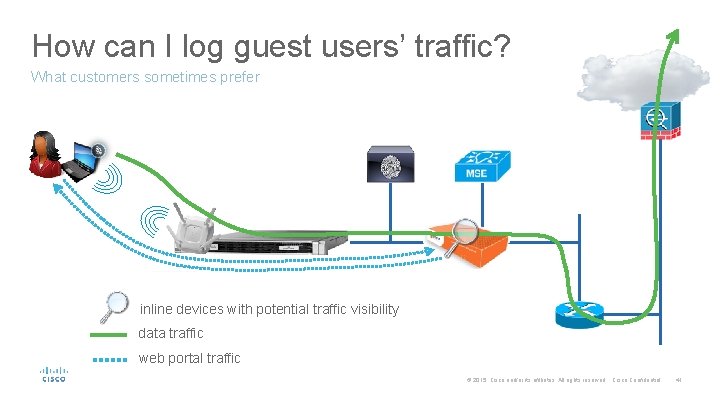
How can I log guest users’ traffic? We’d need to deploy different components inline devices with potential traffic visibility data traffic web portal traffic © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 39

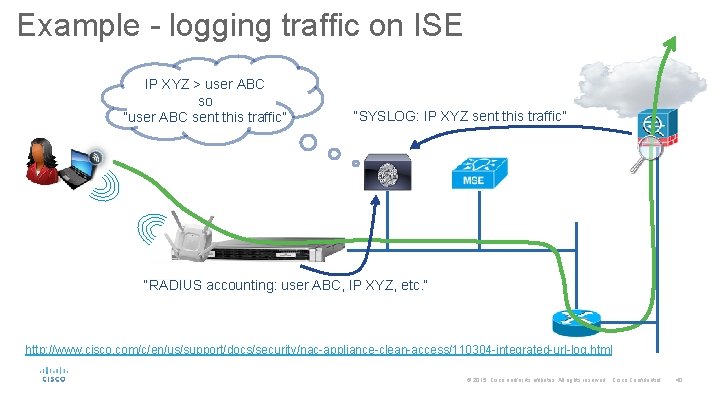
Example - logging traffic on ISE IP XYZ > user ABC so “user ABC sent this traffic” “SYSLOG: IP XYZ sent this traffic” “RADIUS accounting: user ABC, IP XYZ, etc. ” http: //www. cisco. com/c/en/us/support/docs/security/nac-appliance-clean-access/110304 -integrated-url-log. html © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 40

How can I log guest users’ traffic? What customers sometimes prefer inline devices with potential traffic visibility data traffic web portal traffic © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 41

Some quick and dirty positioning examples © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 42

Small Campus Typical needs: • Basic guest account creation options and customization. • Support for sponsor/lobby administrator. • Few locations. Positioning: • Native WLC’s guest portal with customizable web auth bundle: https: //software. cisco. com/download/release. html? mdfid=282600534&flowid=7012&softwareid=282791507&release=1. 0. 2&rel ind=AVAILABLE&rellifecycle=&reltype=latest • Some additional options (e. g. , email sending) through Prime. • ISE Express could be a valuable entry level solution too: http: //www. cisco. com/c/en/us/products/collateral/security/identity-services-engine/qa_c 67 -736030. html © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 43

Medium/Large Campus Typical needs: • Differentiated guest account creation options and customization. • Support for multiple sponsor groups and privileges. • Multiple locations with 802. 1 X most likely already in place. Positioning: • ISE with the latest guest/sponsor features. • Extended customization, with guest and sponsor management. • Support for differentiating portals based on locations (e. g. , AP location, AP group, Flex. Connect group, etc. ). • ISE Portal Builder: https: //isepb. cisco. com © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 44

Public Hotspot (retail, healthcare, events, etc. ) Typical needs: • Mass guest logins management for hotspot only, not for employees. • Simple fill-in forms or social login. • Multiple locations with quick customization and advertisement options. Positioning: • CMX Connect (or even EMSP). • For very large venues (e. g. , stadiums) going beyond the 2, 000 WEBAUTH_REQD clients limit, an SP-based solution might be needed (e. g. , Cisco ISG or similar). • Very quick customization options and no guest database management needed. © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 45

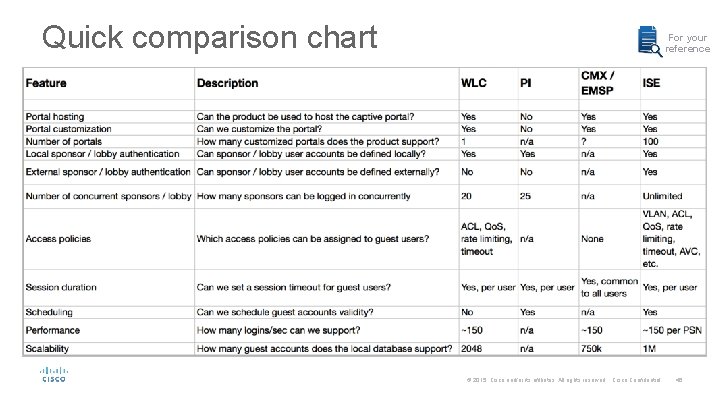
Quick comparison chart For your reference © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 46

It’s never too late to read the full book… https: //communities. cisco. com/docs/DOC-68732

Key Takeaways It’s all about the customers’ needs: • If they ask for guest accounts creation support at a low budget, native guest on the WLC could be a valid option. • If they prefer something very basic, without the need for managing guest accounts, native guest on the WLC or CMX Connect could be good entry levels. • If they want advanced guest options and customization, even if without social logins for the time being, ISE could be the right choice. © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 48
