Wireless Authentication Using Remote Passwords Authors Andrew Harding




- Slides: 10

Wireless Authentication Using Remote Passwords Authors: Andrew Harding, Timothy W. van der Horst, and Kent E. Seamons Source: Proceedings of the first ACM conference on Wireless network security, 2008, pp. 24 -29 Presenter: Jung-wen Lo (駱榮問)

Outline n Introduction ¡ ¡ ¡ n n n Simple Authentication for the Web, 2007 Secure Remote Password, 1998 Surrogate SRP (s. SRP) Wireless Authentication Using Remote Passwords (WARP) Threat analysis Conclusion & Comment 2

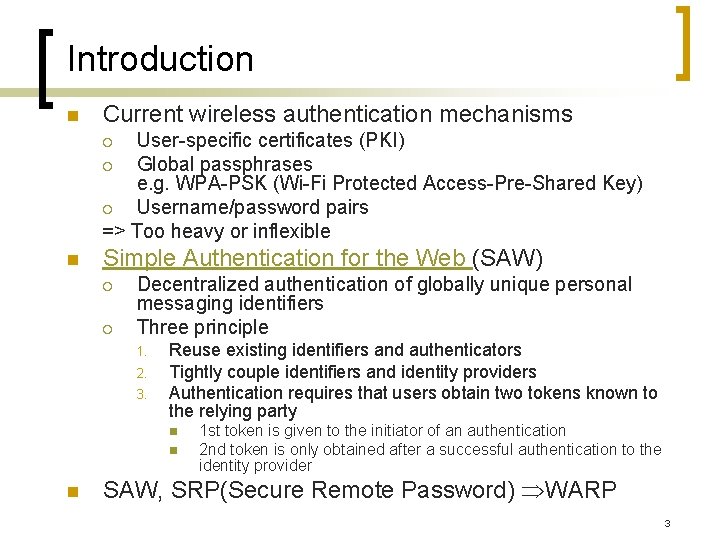
Introduction n Current wireless authentication mechanisms User-specific certificates (PKI) ¡ Global passphrases e. g. WPA-PSK (Wi-Fi Protected Access-Pre-Shared Key) ¡ Username/password pairs => Too heavy or inflexible ¡ n Simple Authentication for the Web (SAW) ¡ ¡ Decentralized authentication of globally unique personal messaging identifiers Three principle 1. 2. 3. Reuse existing identifiers and authenticators Tightly couple identifiers and identity providers Authentication requires that users obtain two tokens known to the relying party n n n 1 st token is given to the initiator of an authentication 2 nd token is only obtained after a successful authentication to the identity provider SAW, SRP(Secure Remote Password) WARP 3

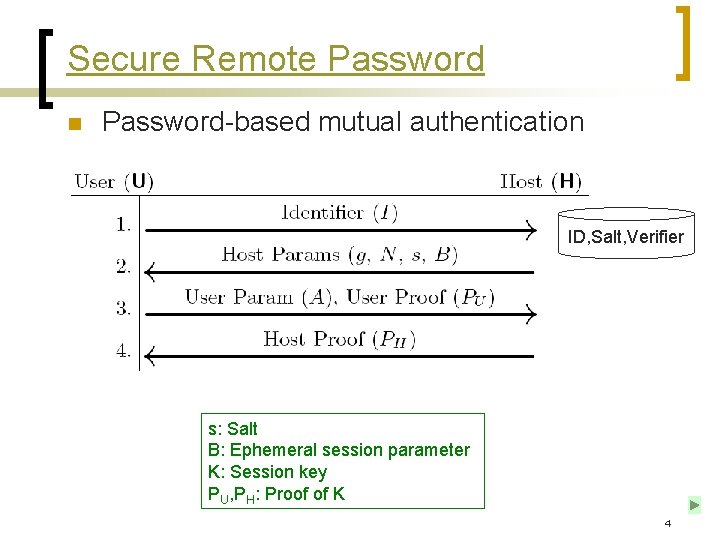
Secure Remote Password n Password-based mutual authentication ID, Salt, Verifier s: Salt B: Ephemeral session parameter K: Session key PU, PH: Proof of K 4

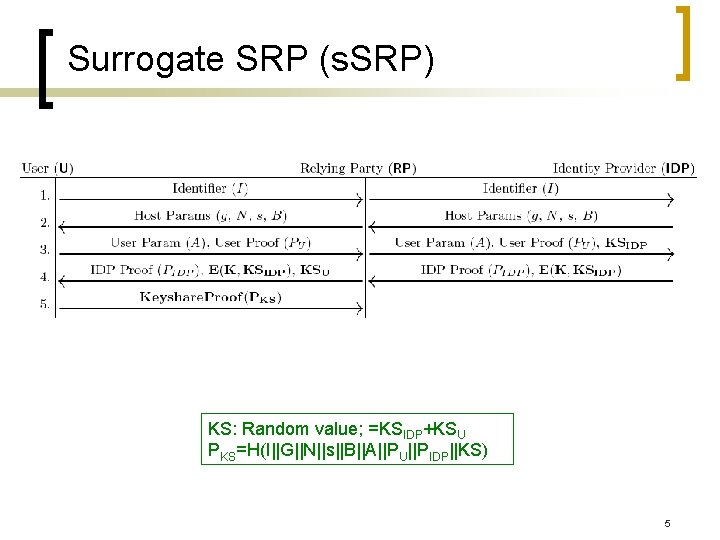
Surrogate SRP (s. SRP) KS: Random value; =KSIDP+KSU PKS=H(I||G||N||s||B||A||PU||PIDP||KS) 5

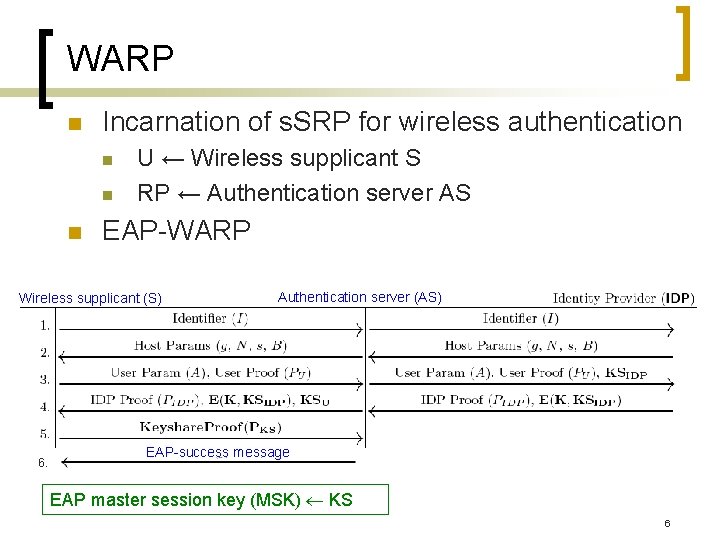
WARP n Incarnation of s. SRP for wireless authentication n U ← Wireless supplicant S RP ← Authentication server AS EAP-WARP Wireless supplicant (S) 6. Authentication server (AS) EAP-success message EAP master session key (MSK) KS 6

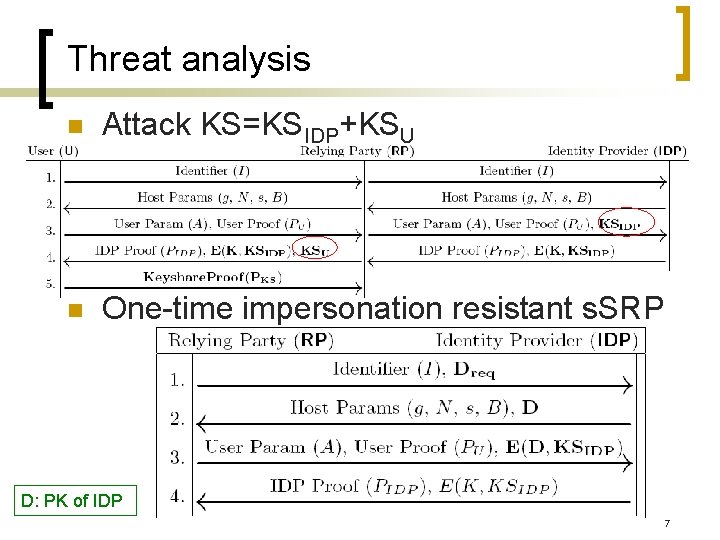
Threat analysis n Attack KS=KSIDP+KSU n One-time impersonation resistant s. SRP D: PK of IDP 7

Conclusion & Comment n Conclusion ¡ ¡ ¡ n SRP enable to authenticate using existing identifier s. SRP replace the use of email in the original SAW protocol for website logins WARP is a convenient and secure wireless authentication mechanism Comment ¡ Eliminate the PKI-based approaches 8

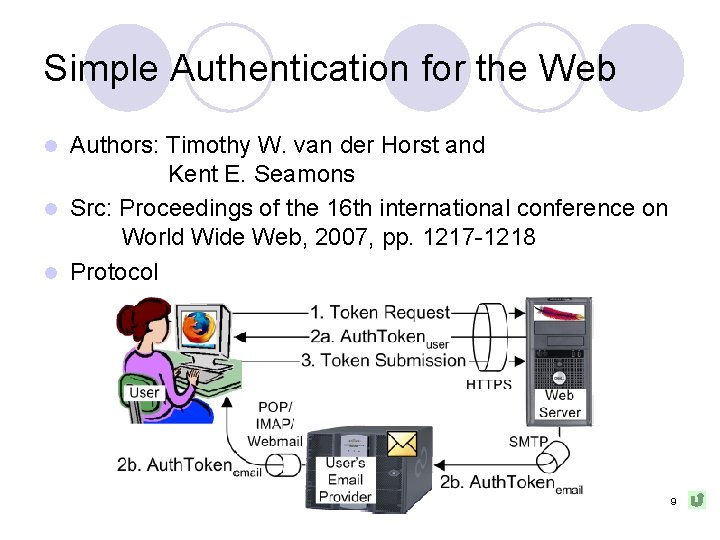
Simple Authentication for the Web Authors: Timothy W. van der Horst and Kent E. Seamons l Src: Proceedings of the 16 th international conference on World Wide Web, 2007, pp. 1217 -1218 l Protocol l 9

Secure Remote Password Protocol, 1998 l Initiation l Protocol Carol Salt s x=H(s, P) v=gx Steve C, s, v s: salt v: Verifier P: password a, b, u: Random # 10