Wireless Application Protocol GSM Architecture Development of the

































- Slides: 54

Wireless Application Protocol GSM Architecture

Development of the GSM Standard 1982: Groupe Spécial Mobile (GSM) created l 1985: List of recommendations are settled and intensely supported by the industry. 1987: Initial aside the drafting of technical specifications was signed by network operators of 13 countries: • time-scales for the procurement and deployment, • compatibly of numbering and routing plans, • tariff principles and definition of accounting. 1990: • The GSM specifications for the 900 MHz are frozen. • Specifications start for the 1800 MHz GSM systems. • GSM stands as "Global System for Mobile communications"

Development of the GSM Standard l l l l 1991: First system trial are running. 1992: Official commercial launch of GSM service in Europe. 1993: - The GSM-Mo. U has 62 signatories in 39 countries worldwide. In addition 32 applicants in 19 others countries. - GSM network are operational in Europe. - First commercial services also start outside Europe. - One million subscribers to GSM networks. 1995: Specification of GSM phase 2 are frozen.

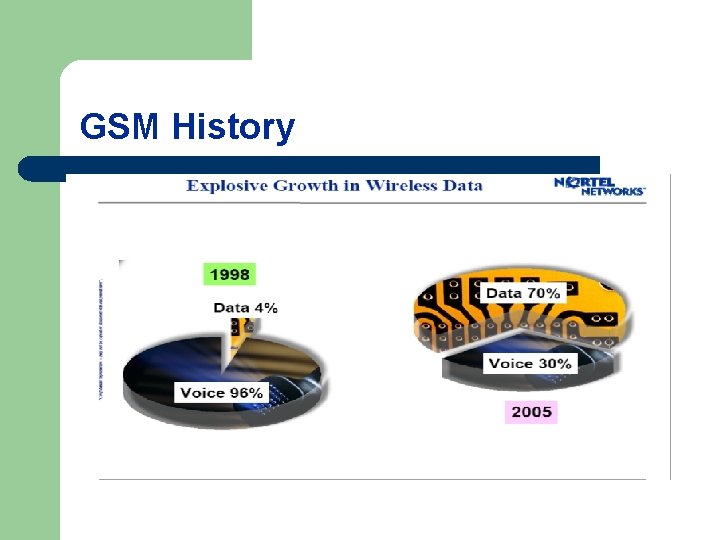
GSM History

GSM History

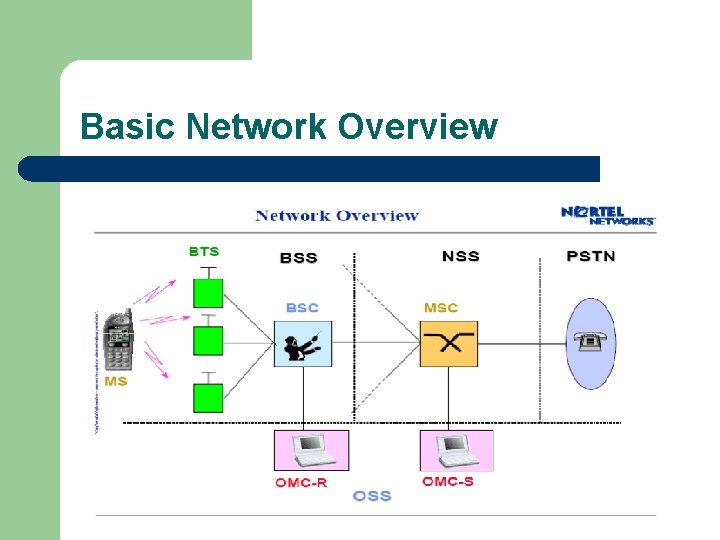
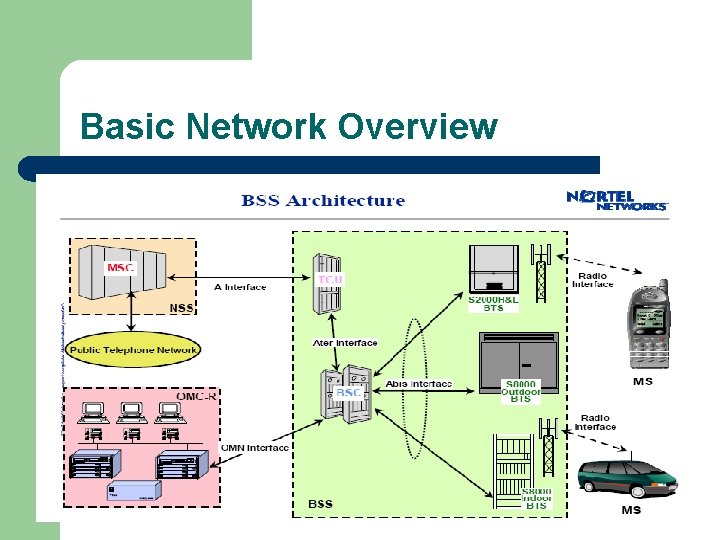
Basic Network Overview l A GSM system is basically designed as a combination of three major subsystems: l Network Sub. System (NSS) Base station Sub. System (BSS), Operation Sub. System (OSS). l l

Basic Network Overview

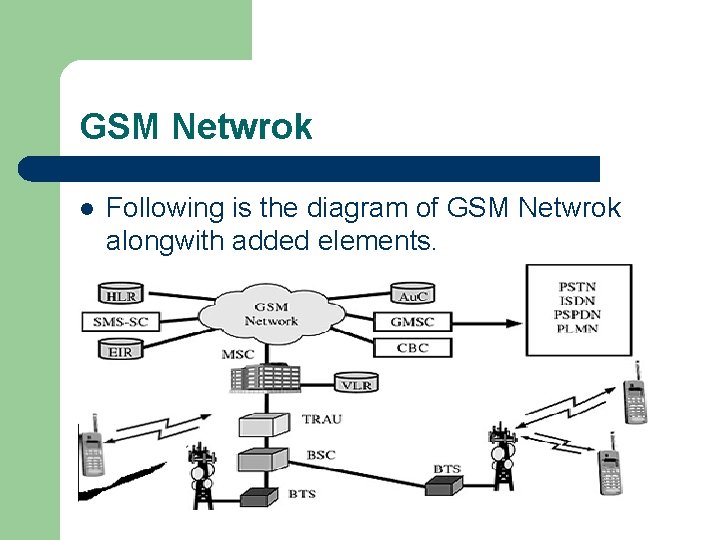
The GSM network is divided into three major systems l Network switching system (SS) l – base station system (BSS), l – is responsible for performing call processing and subscriberrelated functions. All radio-related functions are performed in the BSS, which consists of base station controllers (BSCs) and the base transceiver stations (BTSs). operation and support system (OSS). l l the functional entity from which the network operator monitors and controls the system. To offer the customer cost-effective support for centralized, regional, and local operational and maintenance activities that are required for a GSM network.

Basic Network Overview

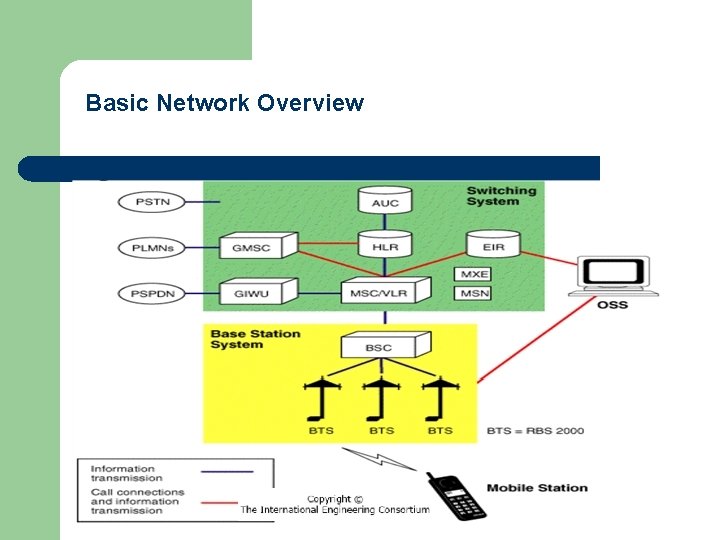
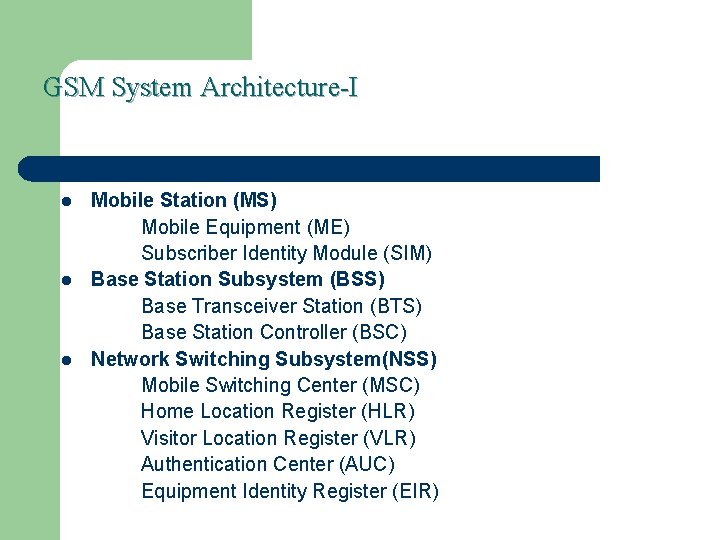
GSM System Architecture-I l l l Mobile Station (MS) Mobile Equipment (ME) Subscriber Identity Module (SIM) Base Station Subsystem (BSS) Base Transceiver Station (BTS) Base Station Controller (BSC) Network Switching Subsystem(NSS) Mobile Switching Center (MSC) Home Location Register (HLR) Visitor Location Register (VLR) Authentication Center (AUC) Equipment Identity Register (EIR)

Basic Network Overview

System Architecture Mobile Station (MS) Mobile Equipment l l l Portable, vehicle mounted, hand held device Uniquely identified by an IMEI (International Mobile Equipment Identity) Voice and data transmission Monitoring power and signal quality of surrounding cells for optimum handover Power level : 0. 8 W – 20 W 160 character long SMS.

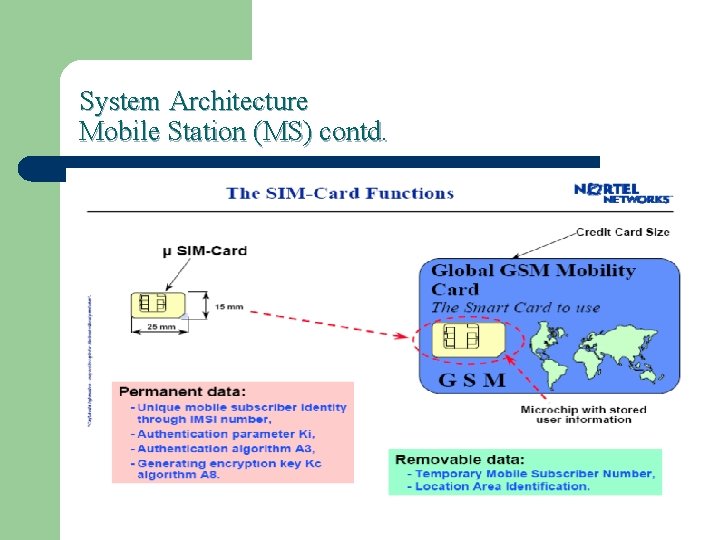
System Architecture Mobile Station (MS) contd. Subscriber Identity Module (SIM) l l l Smart card contains the International Mobile Subscriber Identity (IMSI) Allows user to send and receive calls and receive other subscribed services Encoded network identification details - Key Ki, Kc and A 3, A 5 and A 8 algorithms Protected by a password or PIN Can be moved from phone to phone – contains key information to activate the phone

System Architecture Mobile Station (MS) contd.

System Architecture Mobile Station (MS) contd. l l Each mobile station has an International Mobile Equipment Identity (IMEI) that is permanently stored in the mobile unit. Upon request, the MS sends this number over the signaling channel to the network. The IMEI is used to identify mobile units that are reported stolen or operating incorrectly. The SIM-Card is a removable smart card, the size of a credit card, and contains an integrated circuit chip with a microprocessor, random access memory, and read-only memory.

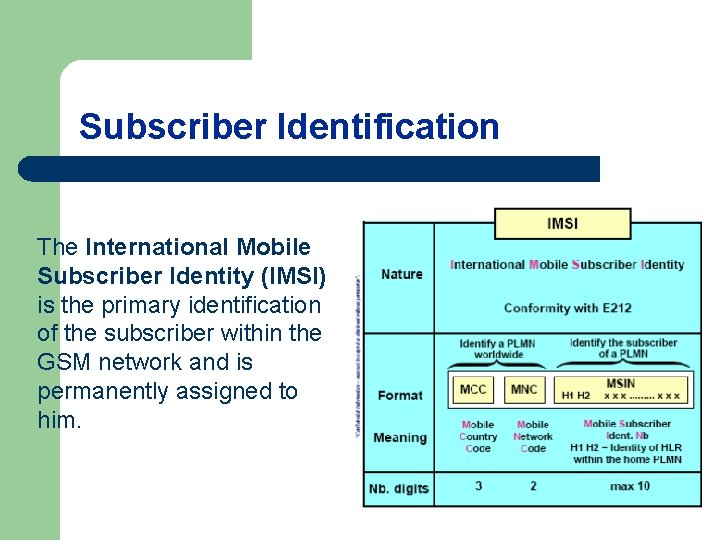
Subscriber Identification The International Mobile Subscriber Identity (IMSI) is the primary identification of the subscriber within the GSM network and is permanently assigned to him.

Basic Network Overview

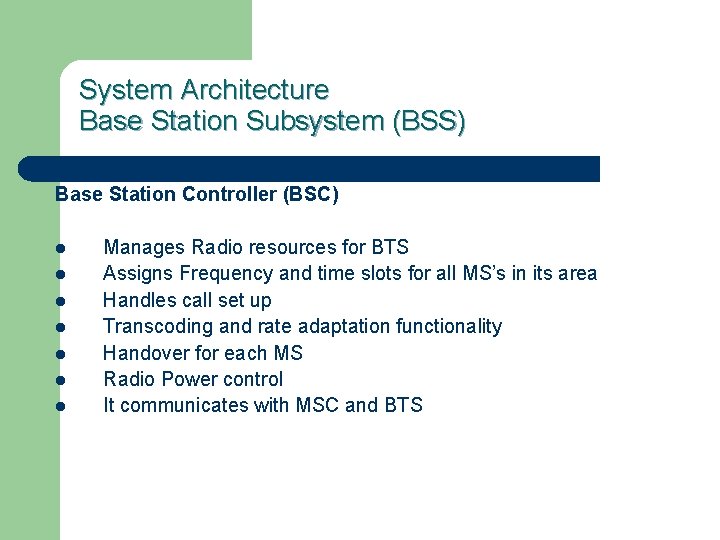
System Architecture Base Station Subsystem (BSS) Base Station Subsystem is composed of two parts that communicate across the standardized Abis interface allowing operation between components made by different suppliers 1. 2. Base Transceiver Station (BTS) Base Station Controller (BSC)

System Architecture Base Station Subsystem (BSS) Base Station Controller (BSC) l l l l Manages Radio resources for BTS Assigns Frequency and time slots for all MS’s in its area Handles call set up Transcoding and rate adaptation functionality Handover for each MS Radio Power control It communicates with MSC and BTS

System Architecture Base Station Subsystem (BSS) Base Transceiver Station (BTS): l l Encodes, encrypts, multiplexes, modulates and feeds the RF signals to the antenna. Frequency hopping Communicates with Mobile station and BSC Consists of Transceivers (TRX) units

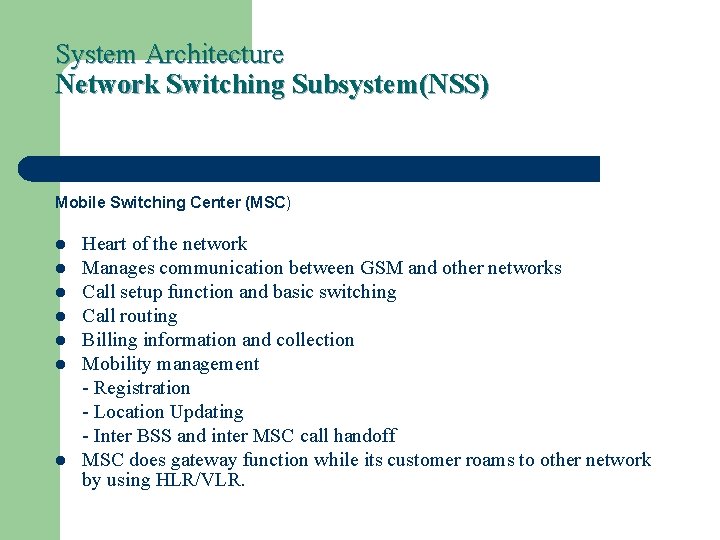
System Architecture Network Switching Subsystem(NSS) Mobile Switching Center (MSC) l l l l Heart of the network Manages communication between GSM and other networks Call setup function and basic switching Call routing Billing information and collection Mobility management - Registration - Location Updating - Inter BSS and inter MSC call handoff MSC does gateway function while its customer roams to other network by using HLR/VLR.

Basic Network Overview

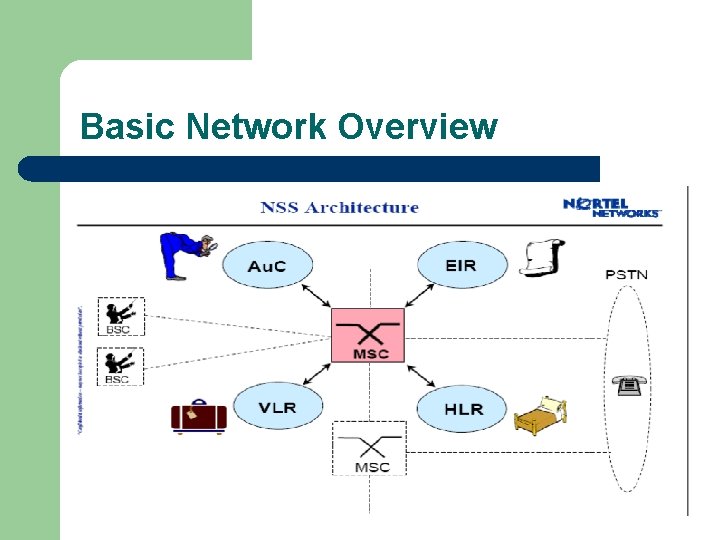
NSS Architecture l Home Location Register (HLR) – – – A database used for storage and management of subscriptions. data about subscribers, including a subscriber's service profile, location information, and activity status. When an individual buys a subscription, he or she is registered in the HLR of that operator.

NSS Architecture l Visitor Location Register (VLR) – – A database that contains temporary information about subscribers that is needed by the MSC in order to service visiting subscribers. The VLR is always integrated with the MSC. For roaming user, VLR connected to that MSC will request data about the mobile station from the HLR through MSC. The Visitor Location Register (VLR) memorizes information about the subscribers physically present in a geographic area. If a subscriber leaves this area, this information is stored in the VLR of another MSC.

System Architecture Network Switching Subsystem l Authentication Center (AUC) - – Protects against intruders in air interface Maintains authentication keys and algorithms and provides security triplets ( RAND, SRES, Kc) Generally associated with HLR Provides authentication and encryption parameters that verify the user's identity and ensure the confidentiality of each call.

System Architecture Network Switching Subsystem Equipment Identity Register (EIR) l - Database that is used to track handsets using the IMEI (International Mobile Equipment Identity) - Made up of three sub-classes: The White List, The Black List and the Gray List - Only one EIR per PLMN A database that contains information about the identity of mobile equipment that prevents calls from stolen, unauthorized, or defective mobile stations

GSM Netwrok l Following is the diagram of GSM Netwrok alongwith added elements.

GSM network areas l l l l In a GSM network, the following areas are defined: Cell is the basic service area: one BTS covers one cell. Each cell is given a Cell Global Identity (CGI), a number that uniquely identifies the cell. Location Area: A group of cells form a Location Area. This is the area that is paged when a subscriber gets an incoming call. Each Location Area is assigned a Location Area Identity (LAI). Each Location Area is served by one or more BSCs. When the MS is in Idle mode, the network do not knows the cell but only the Location Area where the MS is located. Area in which a MS moves freely with updating its current location. MSC/VLR Service Area: The area covered by one MSC is called the MSC/VLR service area. PLMN: The area covered by one network operator is called PLMN. A PLMN can contain one or more MSCs.

Call from Mobile Phone to PSTN: l 1. 2. 3. 4. 5. 6. 7. When a mobile subscriber makes a call to a PSTN telephone subscriber, the following sequence of events takes place: The MSC/VLR receives the message of a call request. The MSC/VLR checks if the mobile station is authorized to access the network. If so, the mobile station is activated. If the mobile station is not authorized, service will be denied. MSC/VLR analyzes the number and initiates a call setup with the PSTN. MSC/VLR asks the corresponding BSC to allocate a traffic channel (a radio channel and a time slot). The BSC allocates the traffic channel and passes the information to the mobile station. The called party answers the call and the conversation takes place. The mobile station keeps on taking measurements of the radio channels in the present cell and neighboring cells and passes the information to the BSC. The BSC decides if handover is required, if so, a new traffic channel is allocated to the mobile station and the handover is performed. If handover is not required, the mobile station continues to transmit in the same frequency.

Call from PSTN to Mobile Phone: l 1. 2. 3. 4. 5. 6. 7. When a PSTN subscriber calls a mobile station, the sequence of events is as follows: The Gateway MSC receives the call and queries the HLR for the information needed to route the call to the serving MSC/VLR. The GMSC routes the call to the MSC/VLR. The MSC checks the VLR for the location area of the MS. The MSC contacts the MS via the BSC through a broadcast message, that is, through a paging request. The MS responds to the page request. The BSC allocates a traffic channel and sends a message to the MS to tune to the channel. The MS generates a ringing signal and, after the subscriber answers, the speech connection is established. Handover, if required, takes place,


Handoff Strategies l l l The subscriber transitions from one radio channel to another as he moves from one cell to another while engaged in a conversation. It means in mobile communication handovers is refer to the transformation of an ongoing call or data from one channel to another which are connected to the core network. It enables the users of cellular technology to receive their calls anywhere and at any time so this process provides the mobility to the users, making it possible to the users to roam seamlessly from one cell to another cell.

Handoff Strategies l During an ongoing communication of a user when the user crosses the cell boundary it is better to use the radio resources of the new cell also called the target cell because the strength of signal in the preceding cell is weaker than the next one that is the target-cell. Now the whole process of the terminating of connection of user from previous cell and establishing the new connection to target cell is called handover

Why need of handovers ? l l The handover process is needed when the following situations occurs. ü When the motion of the MS is very fast. üThe movement of the MS from one cell to another during an ongoing session. üThe experience of interference phenomenon by the user’s equipment from the near cell.

Handover

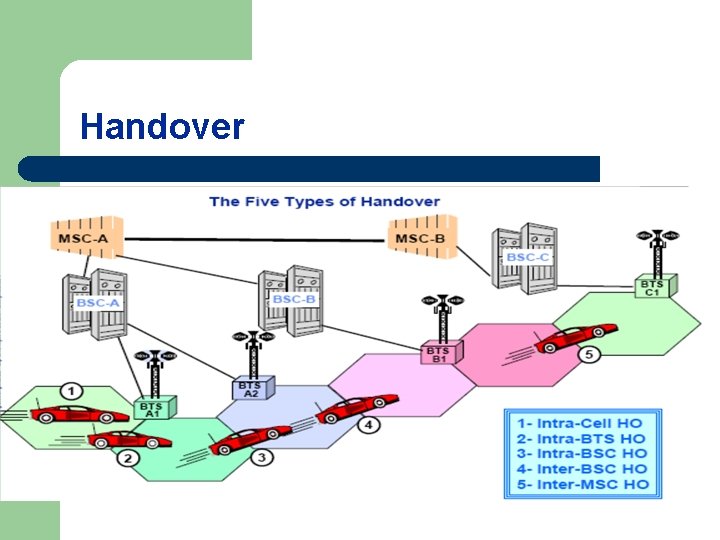
The Five Types of Handover l l l 1 - Intra-Cell Handover: the MS is handed over to another channel on the same cell, under the same BTS. 2 - Intra-BTS Handover: the MS is handed over to another channel on a different cell, under the control of the same BTS. 3 - Intra-BSC Handover: the MS is handed over to another channel on a different cell, under the control of a different BTS of the same BSC. 4 - Inter-BSC Handover: the MS is handed over to another channel on a different cell, under the control of a different BSC of the same MSC. 5 - Inter-MSC Handover: the MS is handed over to another channel on different cell, under another MSC of the same PLMN.

Types of Handover l Hard Handoff: In hard handoff process the channel in the source cell is release before connecting to the target cell. It is also known as (brake-before make). As in hard handoff the connection is break before connecting to other channel is a disadvantage but it is one channel at a time is the advantage, other advantage Is the hardware have no need to be compatible of receiving two or more channels

Types of Handover l l Soft Handoff: In Soft Handoff the channel in the target cell ins connected before releasing the source channel. The user is connected with both channels for a while. It is known as make before break. The time for which both channels are used in parallel is short. The advantage of soft handoff Is the chance of call termination is very low as it is make before break.

Handover Preparation

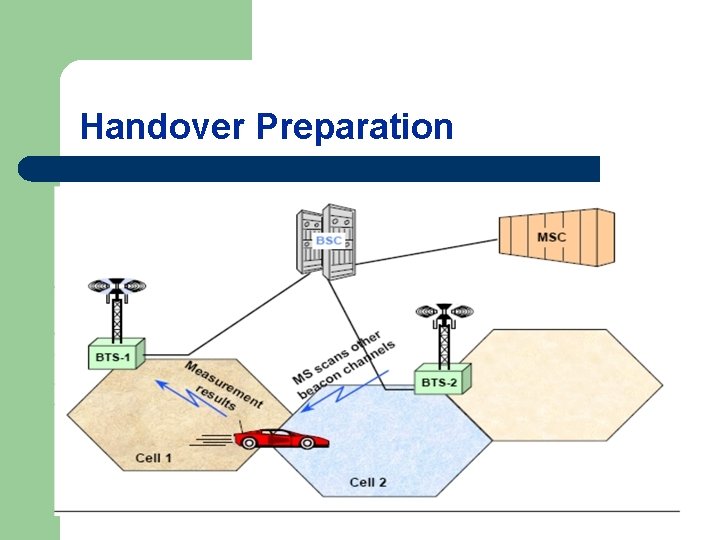
Handover Procedure l l l To avoid losing a call in progress, when the Mobile Station leaves the radio coverage of the cell in charge. Procedure: Three steps: • Handover decision (based on measurements results). • Choice of the target cell. • Handover execution.

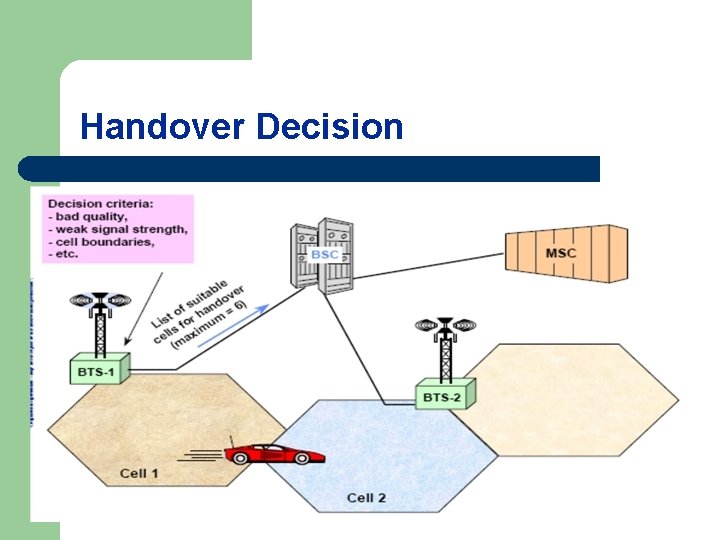
Handover Decision l l l An algorithm is use to select a set of criteria to divide when and which best network to handover Handover is initiated by the network based on radio subsystem criteria (RF level, quality, distance) as well as network directed criteria (current traffic loading per cell, maintenance requests, etc. ). In order to determine if a handover is required, due to RF criteria, the MS shall take radio measurements from neighboring cells; these measurements are reported to the serving cell on a regular basis.

Handover Decision

Handover Execution

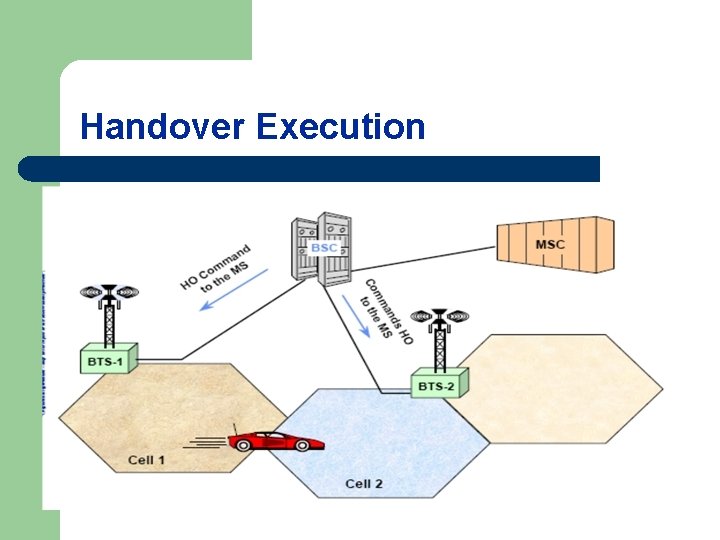
Handover Execution l In this last phase of handoff procedure messages are exchanged between the two networks for rerouting the user call to the new network. The preplanned approach is used for handoff execution all the three processes are for both the horizontal and vertical handoff.

Functions of the Radio Interface

Functions of the Radio Interface l l l The radio interface in the GSM system is responsible for maintaining communication between the fixed network and mobile subscribers. The radio interface serves two major functions in the GSM system. • To transport user information, both speech and data: . • To exchange signaling messages between the mobile station and the network (e. g. call in progress indication and preparation and execution of handovers).


Control Channels l l l l Control channels are intended to carry signaling or synchronization data. Three are defined: Broadcast Channels (BCHs), Common Control Channels (CCCHs), Dedicated Control Channels (DCCHs). Broadcast channels are point to multipoint unidirectional (downlink) control channels from the fixed subsystem to the mobile telephone. • First, BCHs include a Frequency Control Channel (FCCH) that allows an MS to accurately tune to a Base Transceiver Station (BTS). • Then BCHs contain the Synchronization Channel (SCH), which provide TDMA frame oriented synchronization data to a MS. • Last, BCHs include the Broadcast Control Channel (BCCH) intended to broadcast a variety of information to MSs, including cues necessary for the MS to register in the network.

Control Channels l l l Common Control Channels (CCCHs) are point to multipoint channels that is primarily intended to carry signaling information for access handling functions. The CCCHs include: Paging Channel (PCH), which is down channel used to page (call terminating) MSs. • Access Grant Channel (AGCH) that is a downlink channel used to assign a MS to a specific Dedicated Control Channel (DCCH). • Cell Broadcast Channel (CBCH), which is down channel used to broadcast miscellaneous short messages to the MSs. • Random Access Control Channel (RACH) is an uplink channel which allows MS to initiate a call.

Control Channels l l l Dedicated Control Channels are point to point, bi-directional control channel. Two types of DCCHs are used: • Stand-alone Dedicated Control Channels (SDCCH) whose allocation is not linked to the assignment of a traffic channel (TCH). It bears information about authentication, location updates, and assignment to traffic channels (TCHs). • Otherwise, Associated Control Channels are linked to the allocation of a traffic channel (TCH). The Fast Associated Control Channel (FACCH) or burst stealing is a control channel obtained by preemptive dynamic multiplexing on a TCH. The Slow Associated Control Channel (SACCH), also know as a continue data stream, is allocated together with a TCH or a SDCCH.

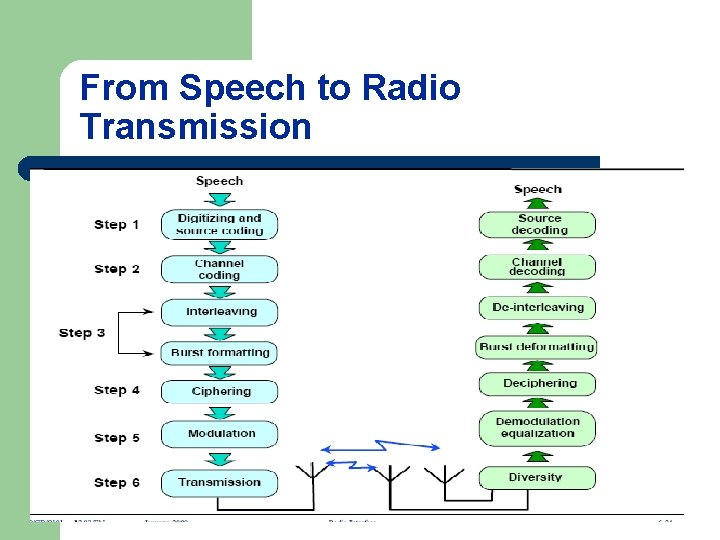
From Speech to Radio Transmission

From Speech to Radio Transmission l l l From speech to radio signal, several operations are performed. The reverse transformations are performed on the receiver side. Main operations are the following: Digitizing: Speech blocks are first digitized to obtain digital blocks: 20 ms speech = 260 bits. Source coding uses low bit rate code for air interface. Channel coding uses codes enabling detection and correction of signals errors. The result is a flow of code words (456 bits long). • Interleaving and burst formatting spread the bits of several code words to expand data of the same block in different bursts. The results is a succession of blocks, one block for each channel burst.

From Speech to Radio Transmission l l • Ciphering modifies the contents of these block through a "secret recipe" known only by the mobile telephone and the Base Transceiver Station, thus protecting data from eavesdropping. • Modulation transforms the binary signal into an analog signal at the right frequency and moment using Gaussian Minimum Shift Keying (GMSK). • Transmission amplifies and radiates the resulting signal as radio waves via an antenna.

From Speech to Radio Transmission l l l • Diversity are different techniques used to provide the reception quality. • Demodulation: From the radio waves captured by the antenna, the portion of the received signal which is of interest to the receiver is demodulated. • Deciphering reverses the encryption "secret recipe". • Burst de-formatting and de-interleaving puts the bits of the different burst back in order to rebuild the code words. • Channel Decoding reconstructs the source information from the output of the demodulator using added redundancy to detect or correct possible errors. • Speech decoding operates as suitable filters receiving the voice parameters, then performs them out analog speech.