Windows Vista User Account Protection Securing Your Application

















- Slides: 28

Windows Vista: User Account Protection Securing Your Application with Least Privilege User Account Steve Hiskey FUN 406 Lead Program Manager, SBTU - Security Business Technology Unit Microsoft Corporation

Agenda LUA == UAP Why User Account Protection (UAP)? The UAP Approach UAP technologies in Windows Vista How this affects your applications today Writing Vista Logo Compliant Code

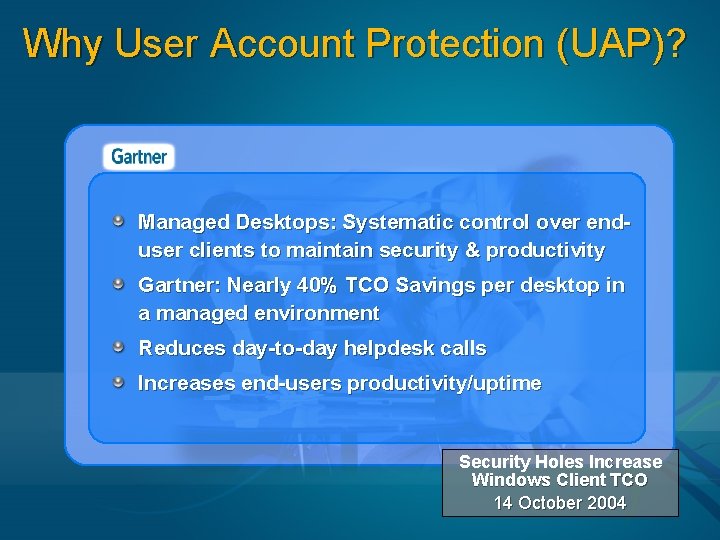
Why User Account Protection (UAP)? Managed Desktops: Systematic control over enduser clients to maintain security & productivity Gartner: Nearly 40% TCO Savings per desktop in a managed environment Reduces day-to-day helpdesk calls Increases end-users productivity/uptime Security Holes Increase Windows Client TCO 14 October 2004

Pain Points Productivity is lost when my machine is compromised Malware, without my knowledge, can modify Windows when run with elevated privileges Enterprise users running elevated privileges can compromise the corporation We have to relax security to run Line of Business (Lo. B) applications Lo. B applications require elevated privileges to run System security must be relaxed to run the Lo. B application It is costly to re-evaluate the required security settings for each application with every OS release Common OS Configuration tasks require elevated privilege Simple scenarios like VPN don’t work Standard Users are not able to manage configuration changes that affect only their account

Windows Vista UAP Goals All users run as Standard User by default even when you log on as admin! Common user tasks redesigned to work for Standard User High application compatibility Administrators use full privilege only for administrative tasks or applications User provides explicit consent before using elevated privilege

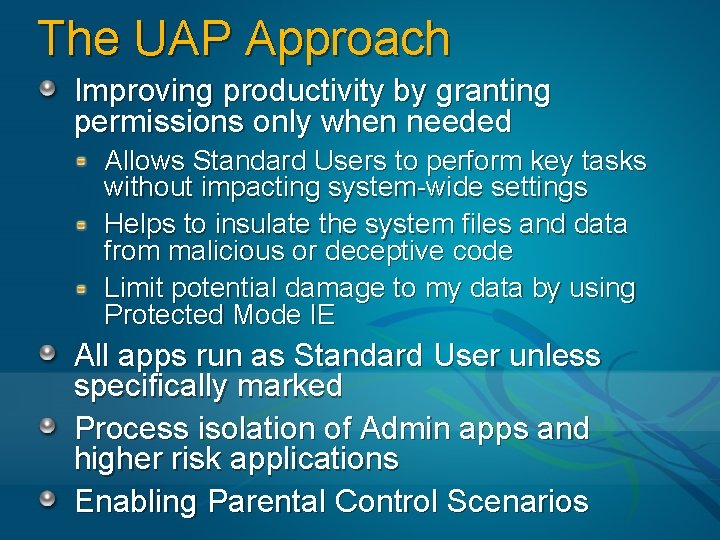
The UAP Approach Improving productivity by granting permissions only when needed Allows Standard Users to perform key tasks without impacting system-wide settings Helps to insulate the system files and data from malicious or deceptive code Limit potential damage to my data by using Protected Mode IE All apps run as Standard User unless specifically marked Process isolation of Admin apps and higher risk applications Enabling Parental Control Scenarios

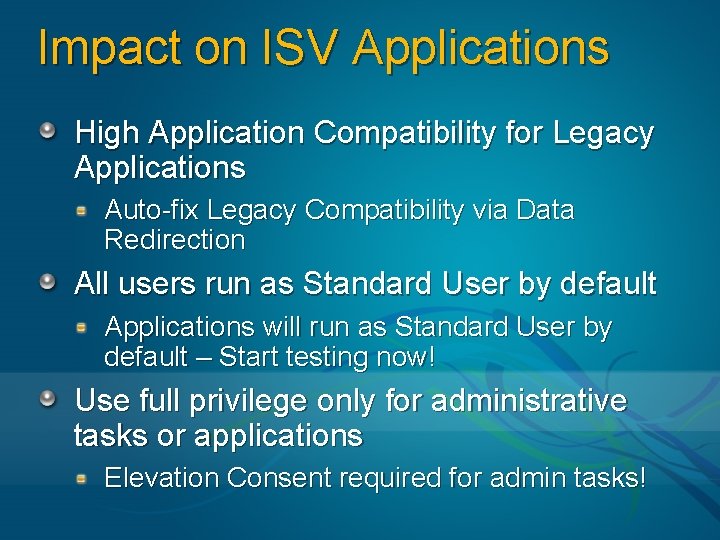
Impact on ISV Applications High Application Compatibility for Legacy Applications Auto-fix Legacy Compatibility via Data Redirection All users run as Standard User by default Applications will run as Standard User by default – Start testing now! Use full privilege only for administrative tasks or applications Elevation Consent required for admin tasks!

High Application Compatibility for Legacy Applications Legacy apps write to admin locations HLKMSoftware %System. Drive%Program Files %System. Root% Redirection allows legacy apps to run as Standard User Writes to HKLM go to HKCU redirected store Writes to system directories redirected to peruser store, copy-on-write … you can still write Admin code

Impact on ISV Applications Darren Canavor Program Manager SBTU - Security Business Technology Unit Microsoft Corporation

Admin Applications vs Running Elevated By default apps run as Standard User unless: Application Manifest requests Admin Identification in App Compat database Heuristic installer detection “Shield” concept for UI “in place” elevation clicking on the item will immediately produce the elevation prompt. Run Elevated… Right mouse click menu option Abby

UAP User Experience Goals: Simple and Predictable Designing a great UAP User Experience First Choice: Make application Standard user only Second Choice: Clearly identify Administrative tasks Identify tasks that need elevation with a “shield” Ensure Standard users can be fully productive UAP User Experience “Rules of the Road” Use common Shield graphic Use design practices to separate Administrative tasks Use provided API to show Elevation Dialog and run Elevated objects / processes

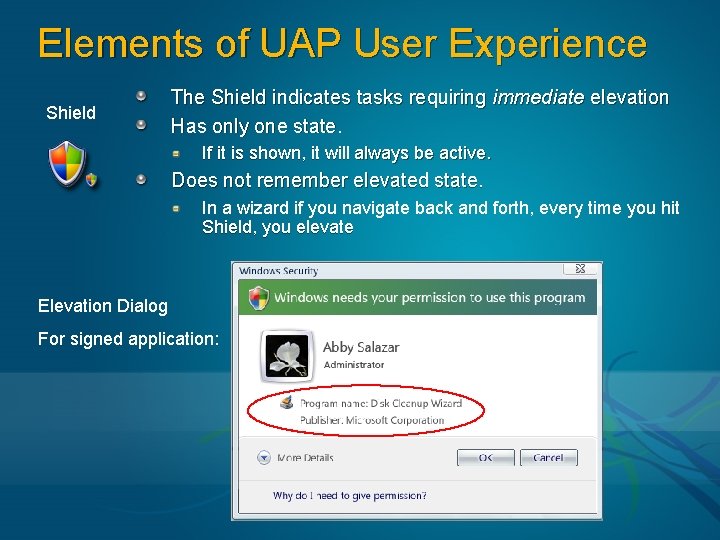
Elements of UAP User Experience Shield The Shield indicates tasks requiring immediate elevation Has only one state. If it is shown, it will always be active. Does not remember elevated state. In a wizard if you navigate back and forth, every time you hit Shield, you elevate Elevation Dialog For signed application:

Admin Application Marking Darren Canavor Program Manager SBTU - Security Business Technology Unit Microsoft Corporation

Process isolation of Admin apps and higher risk applications Administrative and Standard User applications share the same desktop Primary threats Cross-process Window messages (Shatter) DLL injection and create remote thread Process Isolation mechanisms Integrity level for processes UI privilege isolation “Lower” can no longer attack “Higher”

Summary: Impact on ISV Apps Windows XP Logo’d for Standard User? It will just work on Vista Fails on Windows XP as Standard User Mitigated by Redirection Mitigated by App Compat Shim “Is. Admin()? ” Simple app with Admin dependencies Admin app on Windows XP? Needs to be marked! Web apps need special attention due to Protected Mode IE Use the LUA Predictor to fix your app now!

Using the LUA Predictor Darren Canavor Program Manager SBTU - Security Business Technology Unit Microsoft Corporation

Logo Application - Configuration Best Practices Your app’s per-user setup is performed at first run Place per-user data into %LOCALAPPDATA% Roaming into %APPDATA% Place Per-Machine (Shared) data into %ALLUSERPROFILE% Examples of what not to do: Do not perform admin configuration at first run. Do your admin operations during setup Do not perform explicit Admin checks for Standard User applications UAP and Code Access Security (CAS) can be used together for defense in depth

Logo Application Install Best Practices Use MSI 3. 1 for Install and Update Alternate to MSI 3. 1 – call Update. exe marked as admin to do the update Self Updating Code – DON’T DO IT This is our LARGEST App Compat problem Home consumer user applications Examples of what not to do: Do not assume the user is an administrator Run Custom Actions in right context! Click. Once is a great deployment technology for Standard User apps

Call to Action In Windows Vista Beta 1 Toggle UAP Settings ON Test your product or component as a Standard User! Prepare for Beta 2 User Account Protection On by default Review design decisions. Assume the user is a Standard User Continue to test applications, especially older Lo. B and internal applications

Top Takeaways! 1. Window Vista users will run most applications as Standard User by default Even if they log on as Admin! 2. Write UAP compliant software! We have a whitepaper at the FUNDamentals Lounge 3. Current applications will just run as Standard User on Windows Vista because of new UAP technology

More Information Hands On Lab – Room 505 Test your application against the LUA Predictor to make it UAP compliant – all week FUN 222 Exploring the Windows Installer (MSI) and Click. Once Options Friday, 1: 00 PM Room: 406 AB UAP Ask the Experts Wednesday night FUNL 03 – Protected Mode IE 12: 30 Today in 402 AB FUN 210 – Enhancing the Windows Vista Security Platform Wednesday, 3: 15 PM Room: 515 Come get UAP Whitepaper from FUNdamentals Lounge!

Top 10 Questions If I mark my app as “admin”, can I skip the elevation consent dialog? – No Can you modify the privilege of a running application? - No Will LUA elevate whenever a privileged API is used? – No, the entire process is either elevated or not How long does the elevated process last? Can it time out? – Life of the process Can I enable which users will use UAP? – Currently this is a per machine setting Does UAP apply to all processes and services? – Interactive processes only What areas of the Registry and File system get redirected? – HKLMSoftware, %System. Root%, %Program. Files% Won’t Redirection de-motivate developers to fix their code? – Yes, it is a short term mitigation, not in 64 bit What happens when installer detection fails? – The app runs as non-admin Will UAP be going down-level? - No

Questions?

© 2005 Microsoft Corporation. All rights reserved. This presentation is for informational purposes only. Microsoft makes no warranties, express or implied, in this summary.

appendix

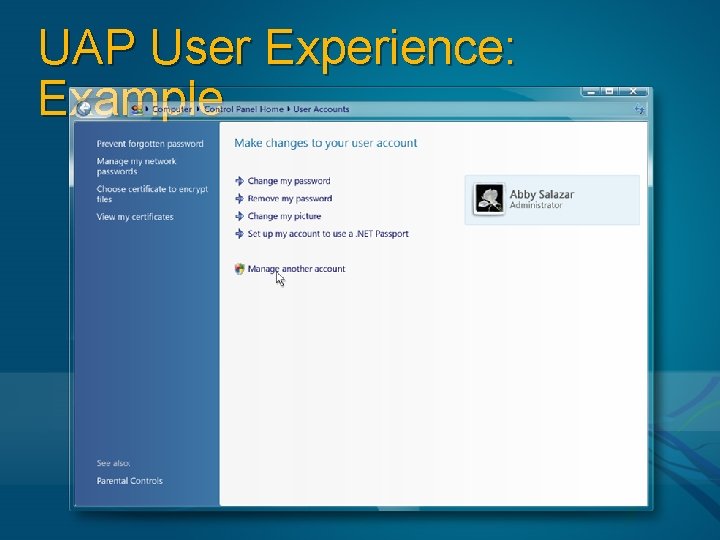
UAP User Experience: Example

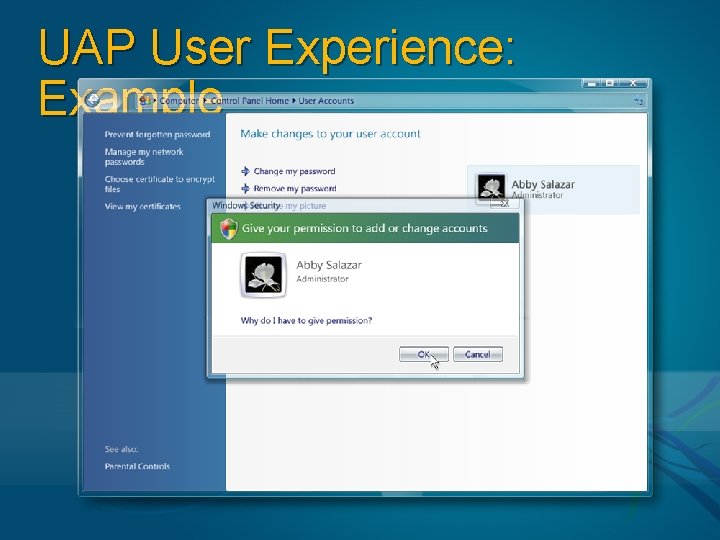
UAP User Experience: Example

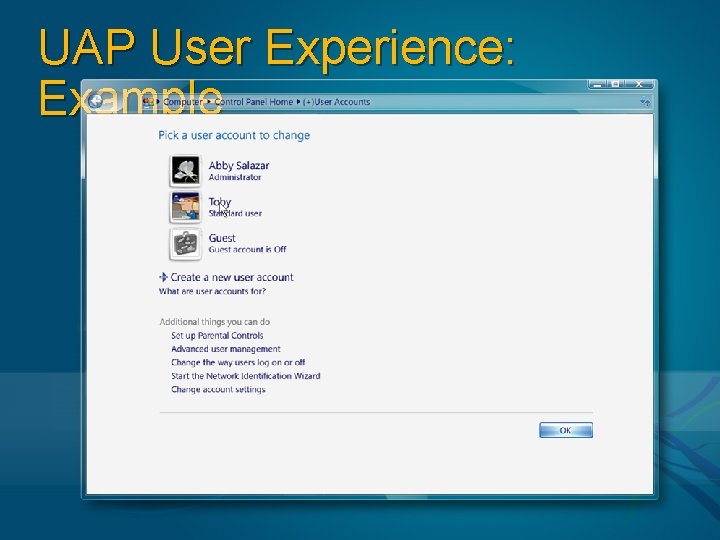
UAP User Experience: Example