Windows 2000XP Internet Protocol Security IPSec Mike Chirico








- Slides: 23

Windows 2000/XP Internet Protocol Security IPSec Mike Chirico M. S. souptonuts. sourceforge. net/chirico/ mchirico@comcast. net December 18, 2003

What would you do if you had less than 5 minutes to lockdown a Windows 2000/XP computer?

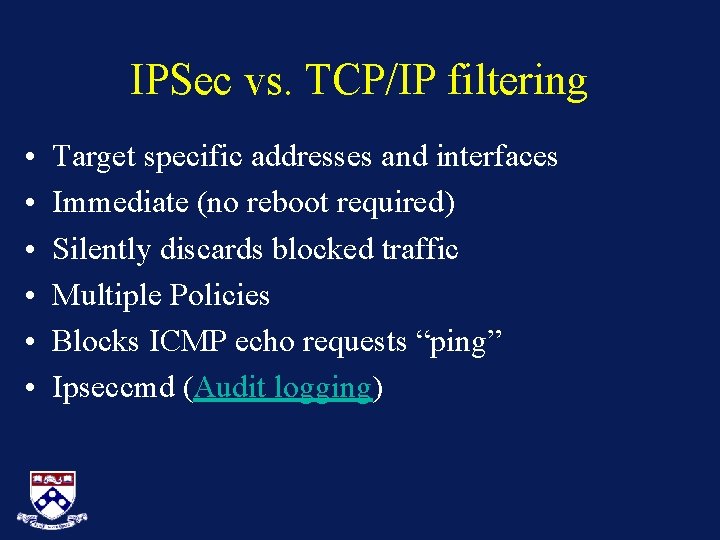
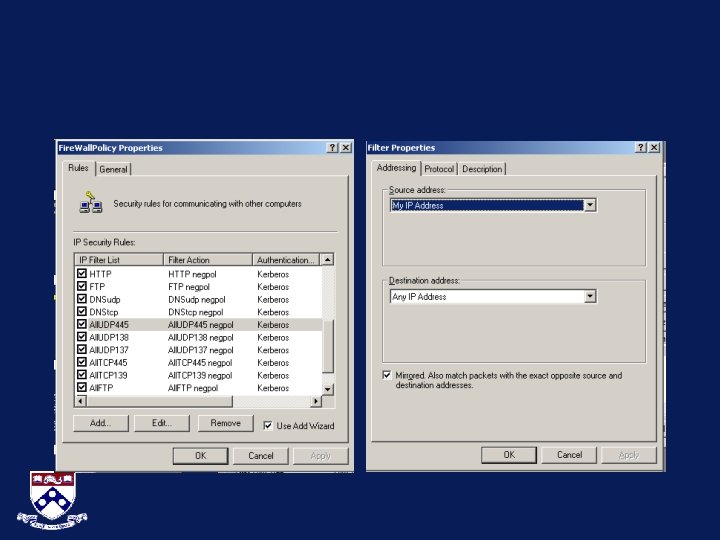
IPSec vs. TCP/IP filtering • • • Target specific addresses and interfaces Immediate (no reboot required) Silently discards blocked traffic Multiple Policies Blocks ICMP echo requests “ping” Ipseccmd (Audit logging)

Windows 2000 and Window XP Different commands: • Windows 2000 uses ipsecpol • Windows XP uses ipseccmd (also all changes are static and supports audit logging)

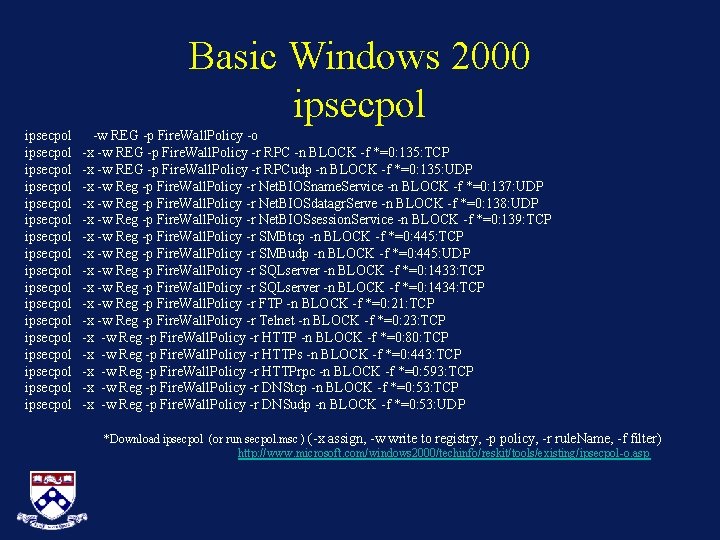
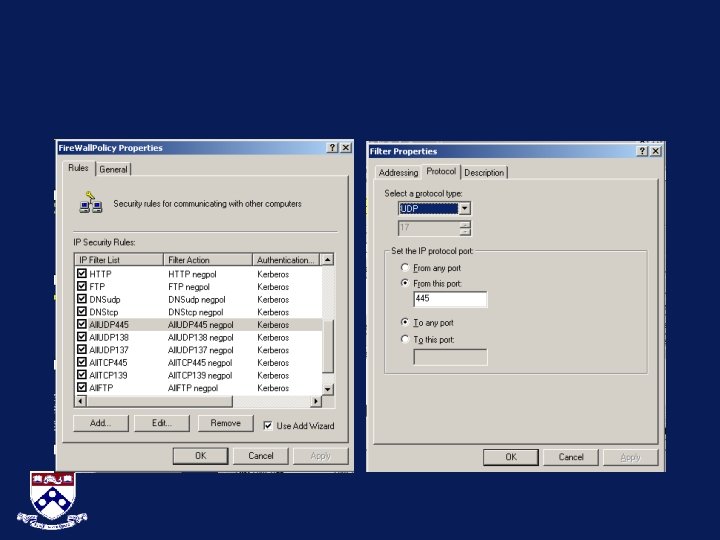
Basic Windows 2000 ipsecpol ipsecpol ipsecpol ipsecpol ipsecpol -w REG -p Fire. Wall. Policy -o -x -w REG -p Fire. Wall. Policy -r RPC -n BLOCK -f *=0: 135: TCP -x -w REG -p Fire. Wall. Policy -r RPCudp -n BLOCK -f *=0: 135: UDP -x -w Reg -p Fire. Wall. Policy -r Net. BIOSname. Service -n BLOCK -f *=0: 137: UDP -x -w Reg -p Fire. Wall. Policy -r Net. BIOSdatagr. Serve -n BLOCK -f *=0: 138: UDP -x -w Reg -p Fire. Wall. Policy -r Net. BIOSsession. Service -n BLOCK -f *=0: 139: TCP -x -w Reg -p Fire. Wall. Policy -r SMBtcp -n BLOCK -f *=0: 445: TCP -x -w Reg -p Fire. Wall. Policy -r SMBudp -n BLOCK -f *=0: 445: UDP -x -w Reg -p Fire. Wall. Policy -r SQLserver -n BLOCK -f *=0: 1433: TCP -x -w Reg -p Fire. Wall. Policy -r SQLserver -n BLOCK -f *=0: 1434: TCP -x -w Reg -p Fire. Wall. Policy -r FTP -n BLOCK -f *=0: 21: TCP -x -w Reg -p Fire. Wall. Policy -r Telnet -n BLOCK -f *=0: 23: TCP -x -w Reg -p Fire. Wall. Policy -r HTTP -n BLOCK -f *=0: 80: TCP -x -w Reg -p Fire. Wall. Policy -r HTTPs -n BLOCK -f *=0: 443: TCP -x -w Reg -p Fire. Wall. Policy -r HTTPrpc -n BLOCK -f *=0: 593: TCP -x -w Reg -p Fire. Wall. Policy -r DNStcp -n BLOCK -f *=0: 53: TCP -x -w Reg -p Fire. Wall. Policy -r DNSudp -n BLOCK -f *=0: 53: UDP *Download ipsecpol (or run secpol. msc ) (-x assign, -w write to registry, -p policy, -r rule. Name, -f filter) http: //www. microsoft. com/windows 2000/techinfo/reskit/tools/existing/ipsecpol-o. asp

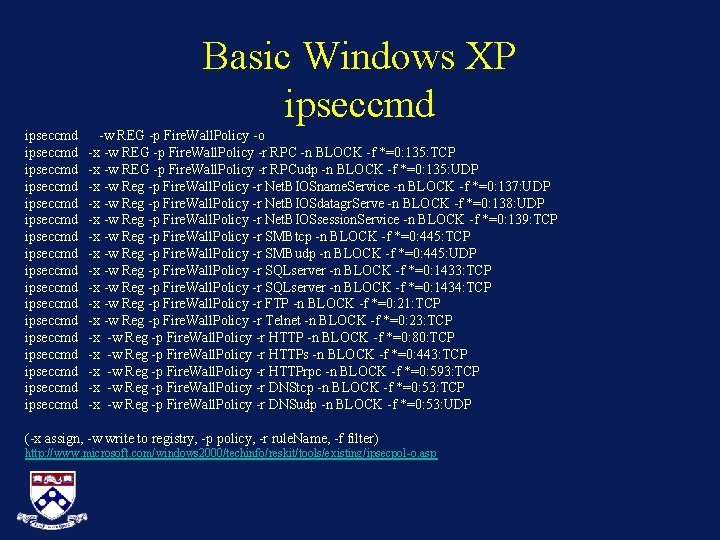
Basic Windows XP ipseccmd ipseccmd ipseccmd ipseccmd ipseccmd -w REG -p Fire. Wall. Policy -o -x -w REG -p Fire. Wall. Policy -r RPC -n BLOCK -f *=0: 135: TCP -x -w REG -p Fire. Wall. Policy -r RPCudp -n BLOCK -f *=0: 135: UDP -x -w Reg -p Fire. Wall. Policy -r Net. BIOSname. Service -n BLOCK -f *=0: 137: UDP -x -w Reg -p Fire. Wall. Policy -r Net. BIOSdatagr. Serve -n BLOCK -f *=0: 138: UDP -x -w Reg -p Fire. Wall. Policy -r Net. BIOSsession. Service -n BLOCK -f *=0: 139: TCP -x -w Reg -p Fire. Wall. Policy -r SMBtcp -n BLOCK -f *=0: 445: TCP -x -w Reg -p Fire. Wall. Policy -r SMBudp -n BLOCK -f *=0: 445: UDP -x -w Reg -p Fire. Wall. Policy -r SQLserver -n BLOCK -f *=0: 1433: TCP -x -w Reg -p Fire. Wall. Policy -r SQLserver -n BLOCK -f *=0: 1434: TCP -x -w Reg -p Fire. Wall. Policy -r FTP -n BLOCK -f *=0: 21: TCP -x -w Reg -p Fire. Wall. Policy -r Telnet -n BLOCK -f *=0: 23: TCP -x -w Reg -p Fire. Wall. Policy -r HTTP -n BLOCK -f *=0: 80: TCP -x -w Reg -p Fire. Wall. Policy -r HTTPs -n BLOCK -f *=0: 443: TCP -x -w Reg -p Fire. Wall. Policy -r HTTPrpc -n BLOCK -f *=0: 593: TCP -x -w Reg -p Fire. Wall. Policy -r DNStcp -n BLOCK -f *=0: 53: TCP -x -w Reg -p Fire. Wall. Policy -r DNSudp -n BLOCK -f *=0: 53: UDP (-x assign, -w write to registry, -p policy, -r rule. Name, -f filter) http: //www. microsoft. com/windows 2000/techinfo/reskit/tools/existing/ipsecpol-o. asp

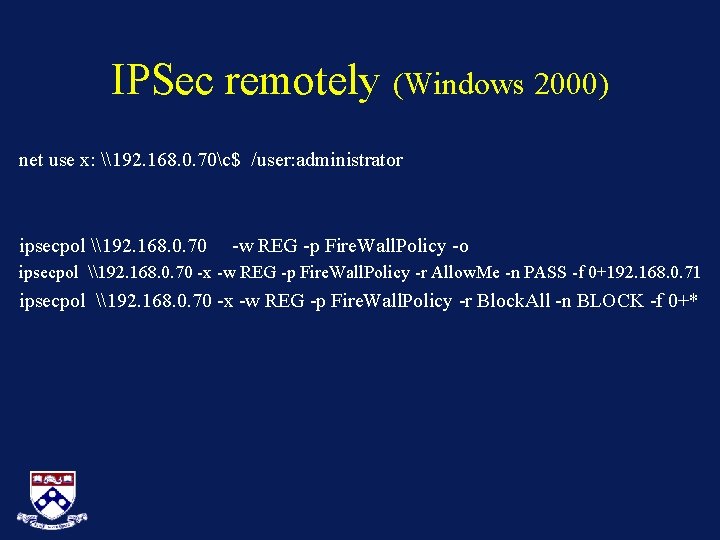
IPSec remotely (Windows 2000) net use x: \192. 168. 0. 70c$ /user: administrator ipsecpol \192. 168. 0. 70 -w REG -p Fire. Wall. Policy -o ipsecpol \192. 168. 0. 70 -x -w REG -p Fire. Wall. Policy -r Allow. Me -n PASS -f 0+192. 168. 0. 71 ipsecpol \192. 168. 0. 70 -x -w REG -p Fire. Wall. Policy -r Block. All -n BLOCK -f 0+*

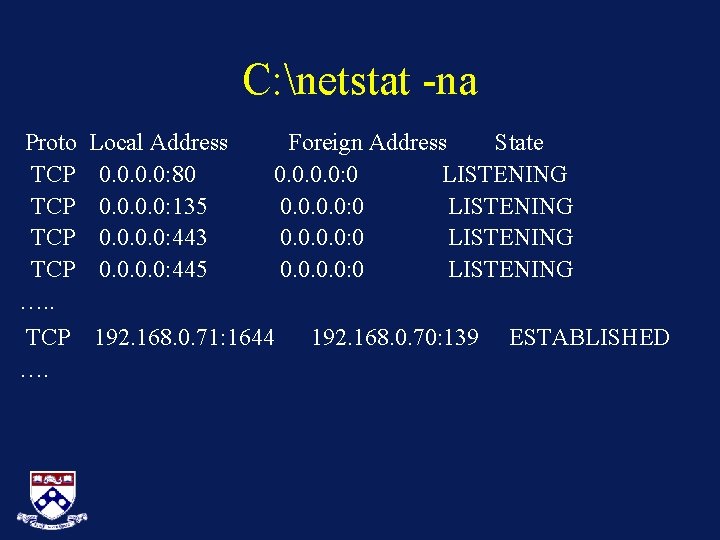
C: netstat -na Proto TCP TCP …. . Local Address 0. 0: 80 0. 0: 135 0. 0: 443 0. 0: 445 Foreign Address State 0. 0: 0 LISTENING TCP …. 192. 168. 0. 71: 1644 192. 168. 0. 70: 139 ESTABLISHED

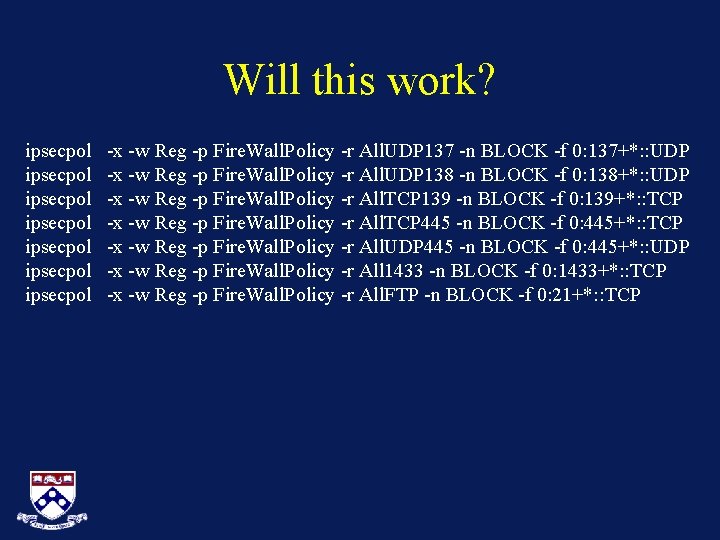
Will this work? ipsecpol ipsecpol -x -w Reg -p Fire. Wall. Policy -r All. UDP 137 -n BLOCK -f 0: 137+*: : UDP -x -w Reg -p Fire. Wall. Policy -r All. UDP 138 -n BLOCK -f 0: 138+*: : UDP -x -w Reg -p Fire. Wall. Policy -r All. TCP 139 -n BLOCK -f 0: 139+*: : TCP -x -w Reg -p Fire. Wall. Policy -r All. TCP 445 -n BLOCK -f 0: 445+*: : TCP -x -w Reg -p Fire. Wall. Policy -r All. UDP 445 -n BLOCK -f 0: 445+*: : UDP -x -w Reg -p Fire. Wall. Policy -r All 1433 -n BLOCK -f 0: 1433+*: : TCP -x -w Reg -p Fire. Wall. Policy -r All. FTP -n BLOCK -f 0: 21+*: : TCP





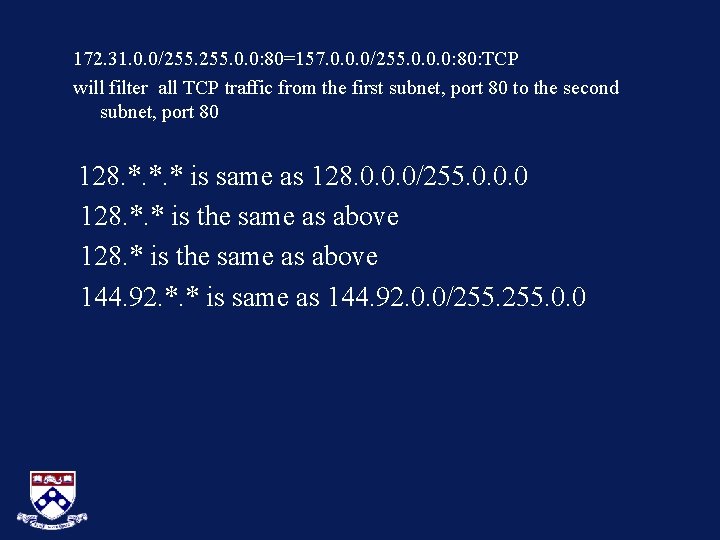
172. 31. 0. 0/255. 0. 0: 80=157. 0. 0. 0/255. 0. 0. 0: 80: TCP will filter all TCP traffic from the first subnet, port 80 to the second subnet, port 80 128. *. *. * is same as 128. 0. 0. 0/255. 0. 0. 0 128. *. * is the same as above 128. * is the same as above 144. 92. *. * is same as 144. 92. 0. 0/255. 0. 0

Common commands Rem blocks everything ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "Block. All" -n BLOCK -f 0+* Rem blocks ping ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "Block. ICMP" -n BLOCK -f 0+*: : ICMP

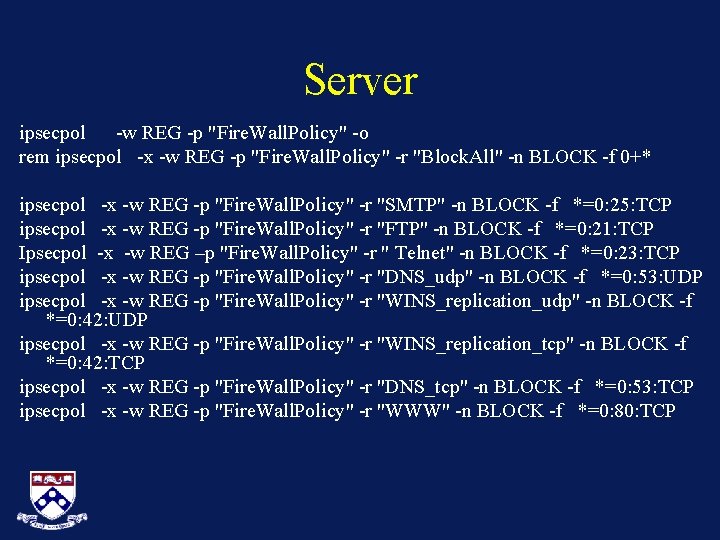
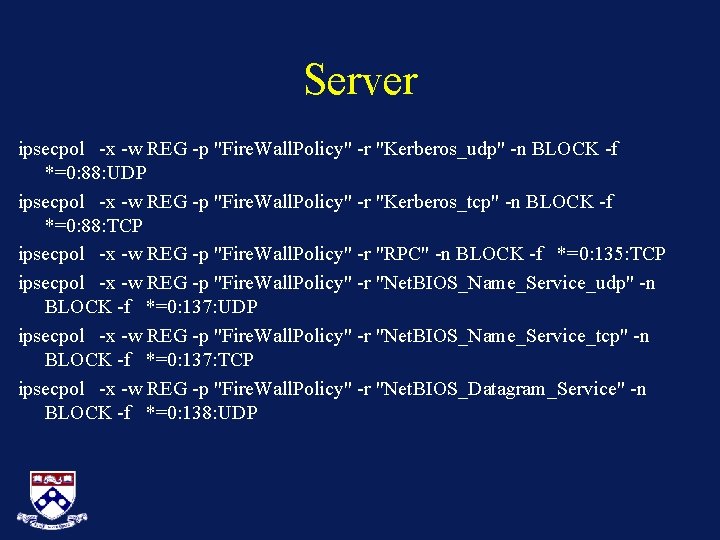
Server ipsecpol -w REG -p "Fire. Wall. Policy" -o rem ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "Block. All" -n BLOCK -f 0+* ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "SMTP" -n BLOCK -f *=0: 25: TCP ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "FTP" -n BLOCK -f *=0: 21: TCP Ipsecpol -x -w REG –p "Fire. Wall. Policy" -r " Telnet" -n BLOCK -f *=0: 23: TCP ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "DNS_udp" -n BLOCK -f *=0: 53: UDP ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "WINS_replication_udp" -n BLOCK -f *=0: 42: UDP ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "WINS_replication_tcp" -n BLOCK -f *=0: 42: TCP ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "DNS_tcp" -n BLOCK -f *=0: 53: TCP ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "WWW" -n BLOCK -f *=0: 80: TCP

Server ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "Kerberos_udp" -n BLOCK -f *=0: 88: UDP ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "Kerberos_tcp" -n BLOCK -f *=0: 88: TCP ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "RPC" -n BLOCK -f *=0: 135: TCP ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "Net. BIOS_Name_Service_udp" -n BLOCK -f *=0: 137: UDP ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "Net. BIOS_Name_Service_tcp" -n BLOCK -f *=0: 137: TCP ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "Net. BIOS_Datagram_Service" -n BLOCK -f *=0: 138: UDP

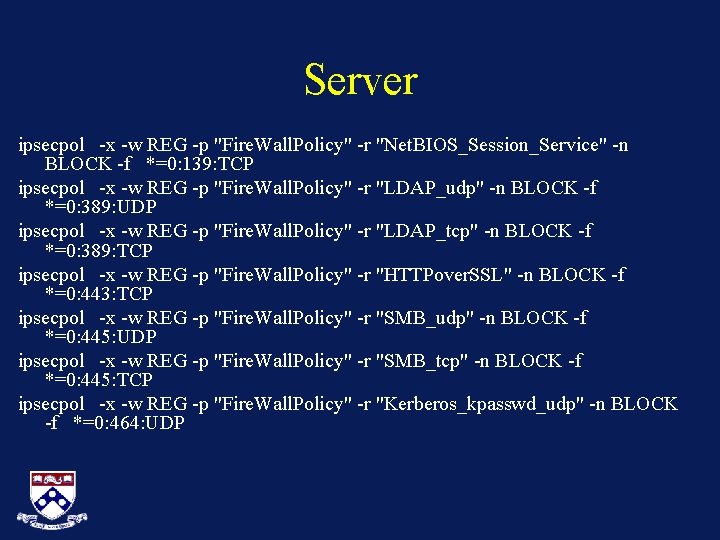
Server ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "Net. BIOS_Session_Service" -n BLOCK -f *=0: 139: TCP ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "LDAP_udp" -n BLOCK -f *=0: 389: UDP ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "LDAP_tcp" -n BLOCK -f *=0: 389: TCP ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "HTTPover. SSL" -n BLOCK -f *=0: 443: TCP ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "SMB_udp" -n BLOCK -f *=0: 445: UDP ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "SMB_tcp" -n BLOCK -f *=0: 445: TCP ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "Kerberos_kpasswd_udp" -n BLOCK -f *=0: 464: UDP

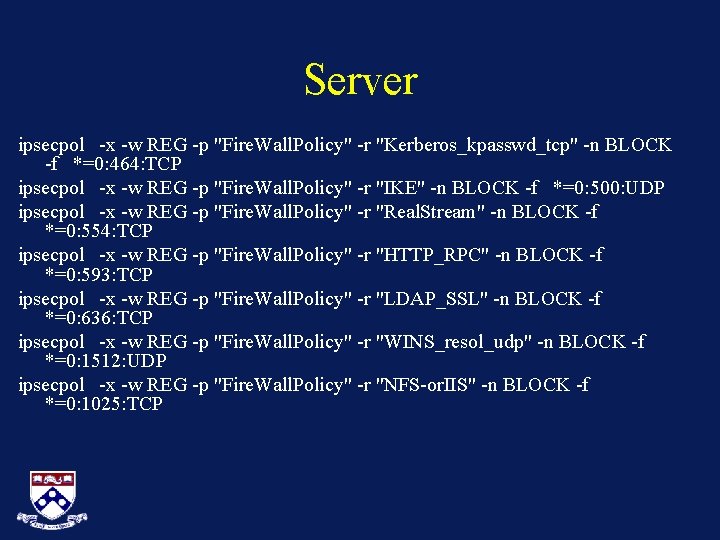
Server ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "Kerberos_kpasswd_tcp" -n BLOCK -f *=0: 464: TCP ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "IKE" -n BLOCK -f *=0: 500: UDP ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "Real. Stream" -n BLOCK -f *=0: 554: TCP ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "HTTP_RPC" -n BLOCK -f *=0: 593: TCP ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "LDAP_SSL" -n BLOCK -f *=0: 636: TCP ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "WINS_resol_udp" -n BLOCK -f *=0: 1512: UDP ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "NFS-or. IIS" -n BLOCK -f *=0: 1025: TCP

Server ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "iad 2" -n BLOCK -f *=0: 1031: TCP ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "pptp" -n BLOCK -f *=0: 1723: TCP ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "mysql" -n BLOCK -f *=0: 3306: TCP ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "msdtc" -n BLOCK -f *=0: 3372: TCP ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "WINS_resol_tcp" -n BLOCK -f *=0: 1512: TCP ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "SQL_Server" -n BLOCK -f *=0: 1433: TCP

Server ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "AD_GLobal_Catalog" -n BLOCK -f *=0: 3268: TCP ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "AD_Global_Catalog_ssl" -n BLOCK -f *=0: 3269: TCP ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "ssh" -n BLOCK -f *=0: 22: TCP ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "ssh_udp" -n BLOCK -f *=0: 22: UDP ipsecpol -x -w REG -p "Fire. Wall. Policy" -r "Windows_Terminal_Service" -n BLOCK -f *=0: 3389: TCP

References Good overview IPSec setup http: //www. microsoft. com/serviceproviders/colum ns/using_ipsec. asp List of ports http: //www. microsoft. com/windows 2000/techinfo/ reskit/samplechapters/cnfc_por_simw. asp http: //www. microsoft. com/technet/treeview/defaul t. asp? url=/technet/ittasks/adrepfir. asp Current scanning activity http: //www. cert. org/current/scanning. html

References continued Nmap (good for testing your configuration) http: //www. insecure. org/nmap_download. html More on IPSec IEFT standard http: //rr. sans. org/win 2000/ipsec_w 2 k. php Security Sites http: //www. ntsecurity. net/ http: //project. honeynet. org http: //www. cert. org/nav/index_main. html http: //www. ciac. org/ciac/