Why eduroam sucks and how to fix it
















- Slides: 20

Why eduroam sucks, and how to fix it. Josh Howlett, UKERNA. TNC 2007, Copenhagen.

eduroam doesn’t suck

eduroam rocks! • it is one of the best ideas in academic networking in years. • hundreds of Institutions already support it. • it is revolutionising network service delivery. “So what’s this talk about? ”

Outline • eduroam has become a victim of its own success. • explain the challenges. • discuss how these are being addressed. • I am not here to evangalise!

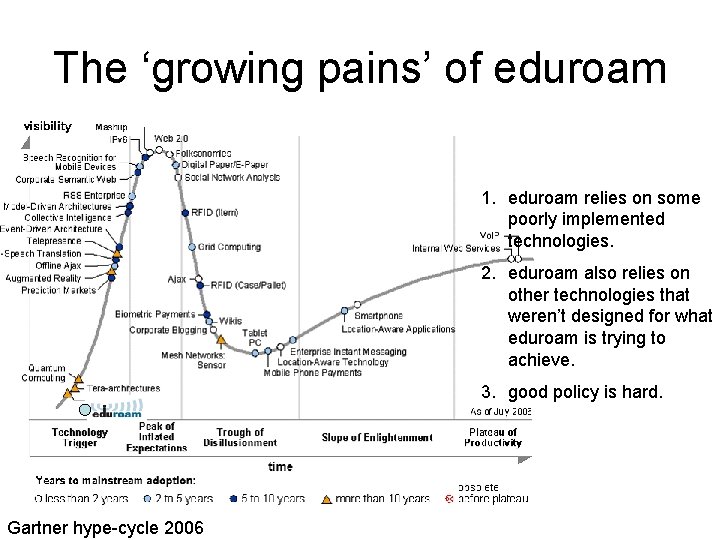
The ‘growing pains’ of eduroam 1. eduroam relies on some poorly implemented technologies. 2. eduroam also relies on other technologies that weren’t designed for what eduroam is trying to achieve. 3. good policy is hard. Gartner hype-cycle 2006

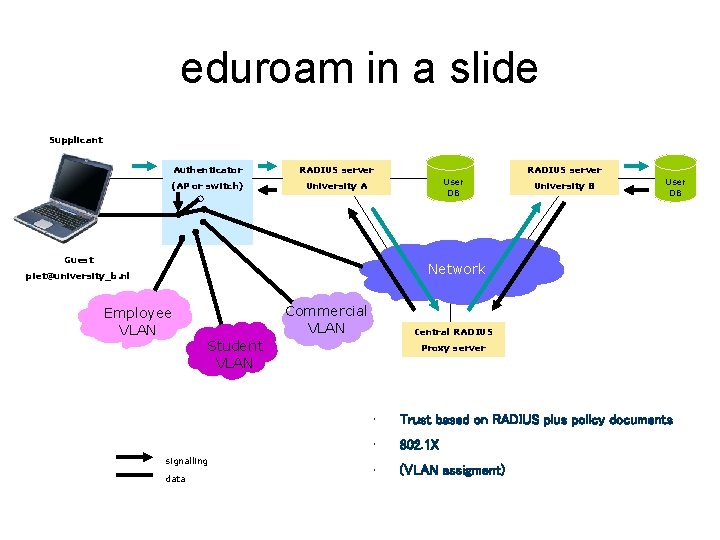
eduroam in a slide Supplicant Authenticator (AP or switch) RADIUS server User DB University A Guest University B User DB Network piet@university_b. nl Employee VLAN Commercial VLAN Student VLAN signalling data Central RADIUS Proxy server • Trust based on RADIUS plus policy documents • 802. 1 X • (VLAN assigment)

Windows sucks (Windows’ supplicant, at least…)

Why Windows’ supplicant sucks • Limited authentication options – EAP-TLS (user certificates suck) – EAP-PEAP (MS-CHAP sucks) • Can’t authenticate against ‘hidden’ SSIDs • Passwords cached in the registry • The default configuration settings – ~20 steps to implement a good configuration. – ~4 sides of A 4 including screenshots.

How we’re trying to fix it • Our pain is the supplicant industry’s gain – Some good but costly commercial supplicants • Open source supplicants (Windows) – Secure. W 2 • An EAP-TTLS plug-in for the Windows supplicant • Addresses some of the problems, but not all. – Open 1 x project • Port of Xsupplicant to Windows • Managed by Open. SEA Alliance (Extreme Networks, Identity Engines, Infoblox, Symantec Corporation, Tipping. Point, Trapeze Networks and UKERNA)

PKI sucks (for wireless authentication…)

Why PKI sucks • The only available secure EAP methods depend on PKI – No one understands PKI, least of all users. – Certificates rooted to CAs in Windows cost €. • Certificate-based TLS handshake is highly verbose – Authentication is slow and fragile over a lossy network.

How we’re trying to fix it • TERENA Server Certificate Service – Another excellent initiative from TERENA • Proposed shared-secret methods – EAP-TLS-PSK – EAP-GPSK • Use a reliable transport for EAP (more later)

RADIUS sucks (…or RADIUS wasn’t designed for this!)

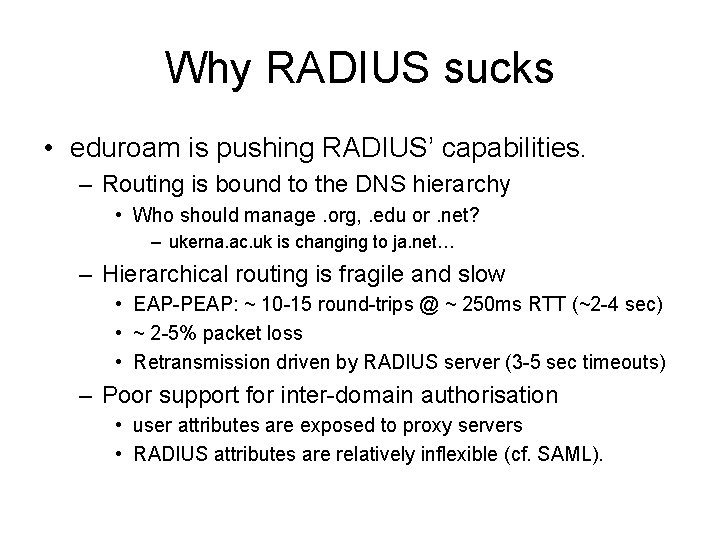
Why RADIUS sucks • eduroam is pushing RADIUS’ capabilities. – Routing is bound to the DNS hierarchy • Who should manage. org, . edu or. net? – ukerna. ac. uk is changing to ja. net… – Hierarchical routing is fragile and slow • EAP-PEAP: ~ 10 -15 round-trips @ ~ 250 ms RTT (~2 -4 sec) • ~ 2 -5% packet loss • Retransmission driven by RADIUS server (3 -5 sec timeouts) – Poor support for inter-domain authorisation • user attributes are exposed to proxy servers • RADIUS attributes are relatively inflexible (cf. SAML).

How we’re trying to fix it • Routing – RADSec • RADIUS over TLS over TCP. • Unlikely to gain traction in IETF. – Diameter • IETF’s proposed successor to RADIUS. • Only one commercial implementation. – We need PKI for both. . . • Authorisation – DAMe (GN JRA 5) – RADIUS-SAML (Internet 2 FWNA) – Perhaps we’re trying to be too clever? • Would a small set of RADIUS attributes be sufficient to cover our use-cases?

Inconsistent policy sucks

Why inconsistent policy sucks • Visible Services, Transparent Networks • Consistency matters – Reduces costs and user satisfaction. • eduroam confederation policy – “[Institutions] SHOULD provide open network access” – Great idea, but will the ‘SHOULD’ be ignored? • If tcp/80 is the only common denominator then in practice eduroam becomes interweb only. • eduroam has competitors – Commercial 802. 11, GRPS, UMTS, 802. 16, 802. 20…

How we’re trying to fix it • Opinions differ – 26 NRENs, 100 s Institutions… • How should policy be balanced between Institutions, NRENs and confederation? – Perhaps we need more experience? • I carry about a GPRS/UMTS dongle; a sign of things to come? • Do we need to add more value?

Conclusions • Most Institutions can deploy eduroam without problems today. • There are technology issues for some Institutions, but we’re close to fixing these. • There are scaling issues, but these will be fixed in the medium term. – This is not an excuse for delaying joining! • The confederation policy may need some minor adjustments, but nothing significant. • De we need to add more value?

Thank you for your attention • Any questions?