When Encryption Isnt Enough Kamal Sharma Technical Consultant





- Slides: 13

When Encryption Isn't Enough … Kamal Sharma – Technical Consultant kamal_s@trendmicro. com Copyright 2009 Trend Micro Inc. 1

Agenda §The Impact §Encryption Modules §Think Again §DPL and SPN §Summary Copyright 2009 Trend Micro Inc.

The Impact of Data Loss • Cost: $6. 3 M per breach* • Loss of customers/business • Brand damage • Stock price decrease • Regulatory fines • Legal defense • Notification and compensation * Ponemon Institute • Public relations & security response Copyright 2009 Trend Micro Inc.

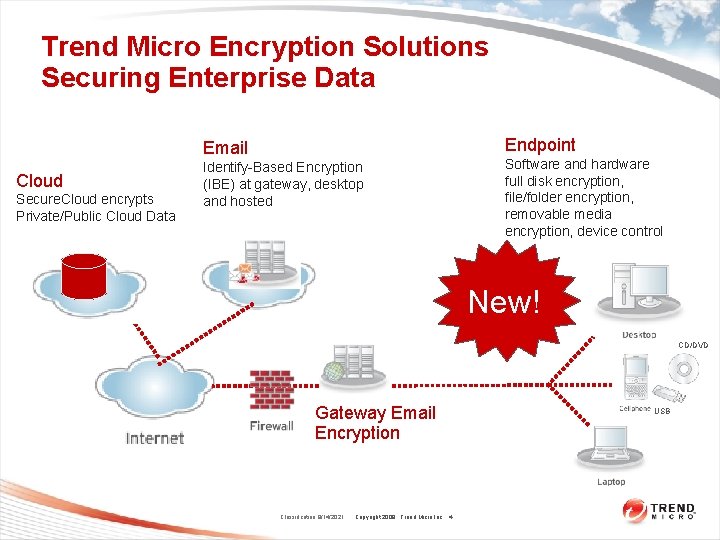
Trend Micro Encryption Solutions Securing Enterprise Data Endpoint Email Cloud Secure. Cloud encrypts Private/Public Cloud Data Identify-Based Encryption (IBE) at gateway, desktop and hosted Software and hardware full disk encryption, file/folder encryption, removable media encryption, device control New! CD/DVD Gateway Email Encryption Classification 9/14/2021 Copyright 2009 Trend Micro Inc. 4 USB

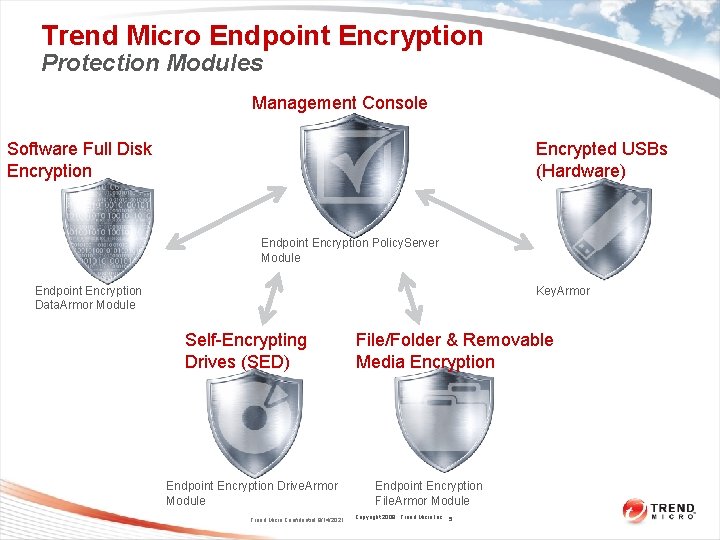
Trend Micro Endpoint Encryption Protection Modules Management Console Software Full Disk Encryption Encrypted USBs (Hardware) Endpoint Encryption Policy. Server Module Endpoint Encryption Data. Armor Module Key. Armor Self-Encrypting Drives (SED) Endpoint Encryption Drive. Armor Module Trend Micro Confidential 9/14/2021 File/Folder & Removable Media Encryption Endpoint Encryption File. Armor Module Copyright 2009 Trend Micro Inc. 5

Think Your Data is Secure? Think Again External Attacks Organizational Data Criminal Threats: • Come from many sources, spam, spyware, malicious sites and employee downloads Hackers: • Compromise web-based applications to access databases Insider Threats: • Malicious and accidental breaches of private data and intellectual property • Lost and stolen laptops Internal Threats! 59% of all data loss originates from the INSIDE* * Source: datalossdb. org Copyright 2009 Trend Micro Inc. 6

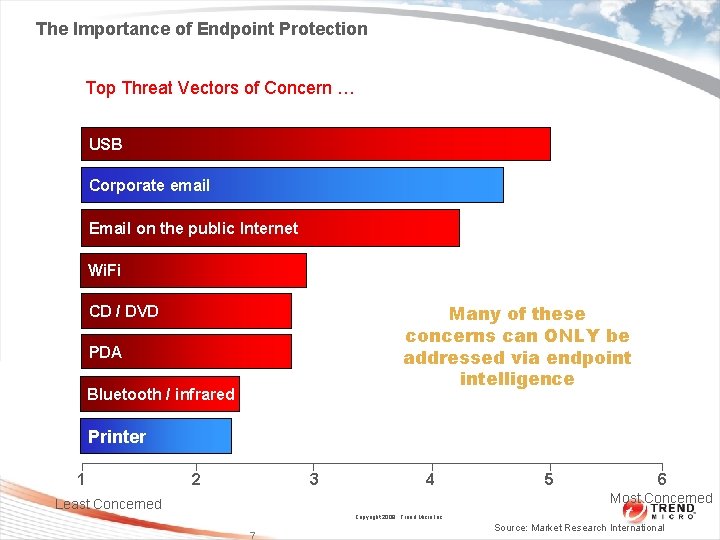
The Importance of Endpoint Protection Top Threat Vectors of Concern … USB Corporate email Email on the public Internet Wi. Fi Many of these concerns can ONLY be addressed via endpoint intelligence CD / DVD PDA Bluetooth//infrared Bluetooth Printer 1 2 3 4 5 6 Most Concerned Least Concerned Copyright 2009 Trend Micro Inc. 7 Source: Market Research International

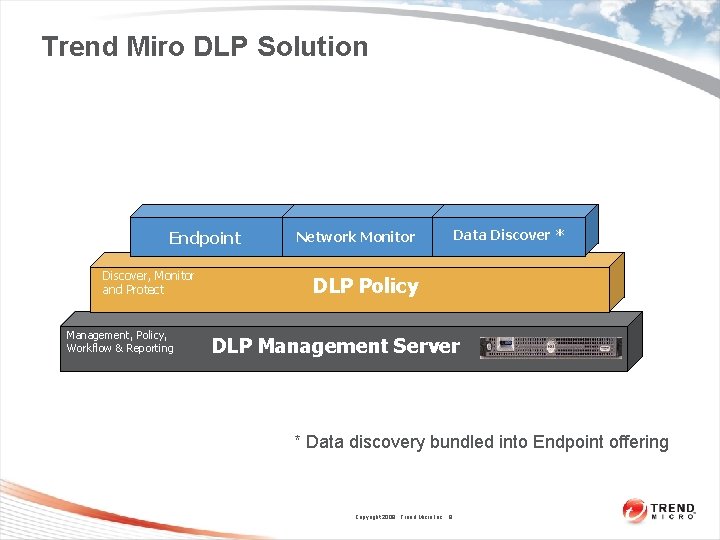
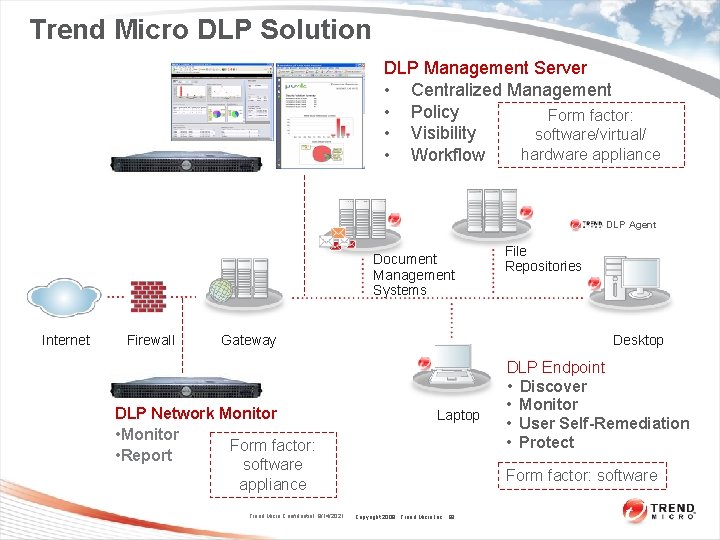
Trend Miro DLP Solution Endpoint Discover, Monitor and Protect Management, Policy, Workflow & Reporting Network Monitor Data Discover * DLP Policy DLP Management Server * Data discovery bundled into Endpoint offering Copyright 2009 Trend Micro Inc. 8

Trend Micro DLP Solution DLP Management Server • Centralized Management • Policy Form factor: • Visibility software/virtual/ hardware appliance • Workflow DLP Agent Document Management Systems Internet Firewall Gateway DLP Network Monitor • Monitor Form factor: • Report software appliance Trend Micro Confidential 9/14/2021 File Repositories Desktop Laptop DLP Endpoint • Discover • Monitor • User Self-Remediation • Protect Form factor: software Copyright 2009 Trend Micro Inc. 99

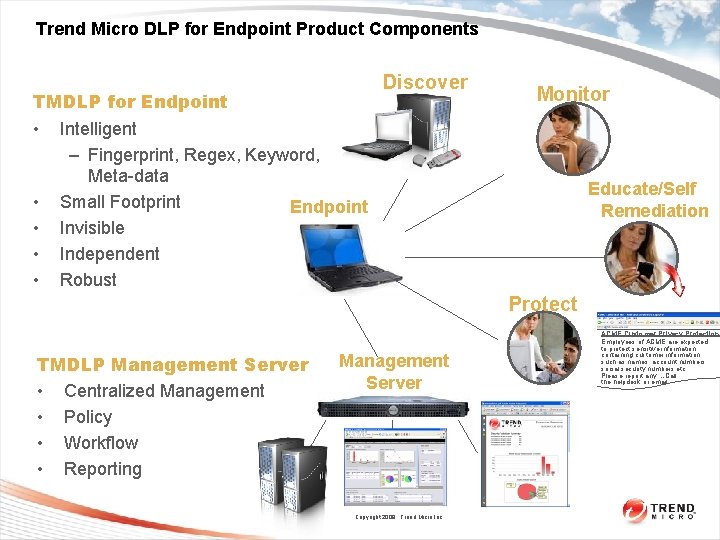
Trend Micro DLP for Endpoint Product Components TMDLP for Endpoint • Intelligent – Fingerprint, Regex, Keyword, Meta-data • Small Footprint Endpoint • Invisible • Independent • Robust Discover Monitor Educate/Self Remediation Protect TMDLP Management Server • Centralized Management • Policy • Workflow • Reporting Management Server Copyright 2009 Trend Micro Inc. ACME Customer Privacy Protection Employees of ACME are expected to protect sensitive information containing customer information such as names, account numbers, social security numbers etc. Please report any …Call the helpdesk or email.

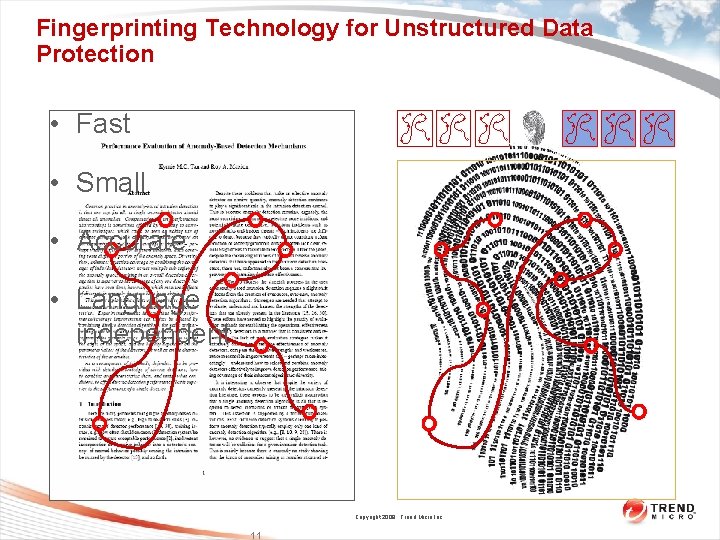
Fingerprinting Technology for Unstructured Data Protection • Fast • Small • Accurate • Language independent Copyright 2009 Trend Micro Inc. 11

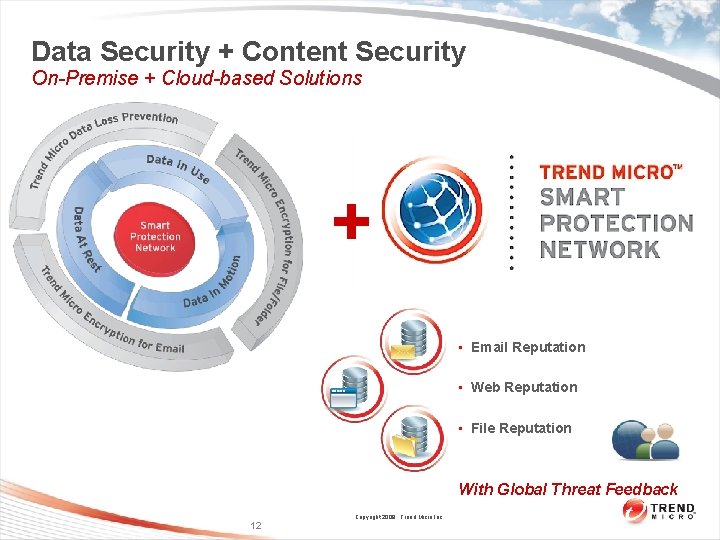
Data Security + Content Security On-Premise + Cloud-based Solutions + • Email Reputation • Web Reputation • File Reputation With Global Threat Feedback Copyright 2009 Trend Micro Inc. 12

Thank You Learn more: www. trendmicro. com/us/home/enterprise Copyright 2009 Trend Micro Inc.