When DRM Meets Restricted Multicast A Content Encryption











- Slides: 17

When DRM Meets Restricted Multicast A Content Encryption Key Scheme for Restricted Multicast and DRM Min FENG and Bin ZHU Microsoft Research Asia

Outline • • Introduction Two straight-forward solutions Our solution Conclusion

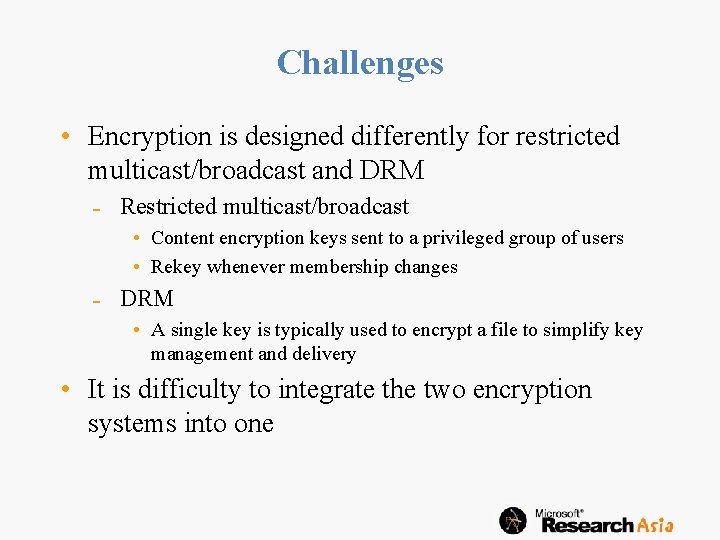
Scenario • Restricted multicast/broadcast Content is encrypted with symmetric encryption Users may want to save encrypted multicast/broadcast content locally for replay • Premium content stored at client side should be DRM protected to prevent unauthorized usage • How to combine DRM with restricted multicast/broadcast?

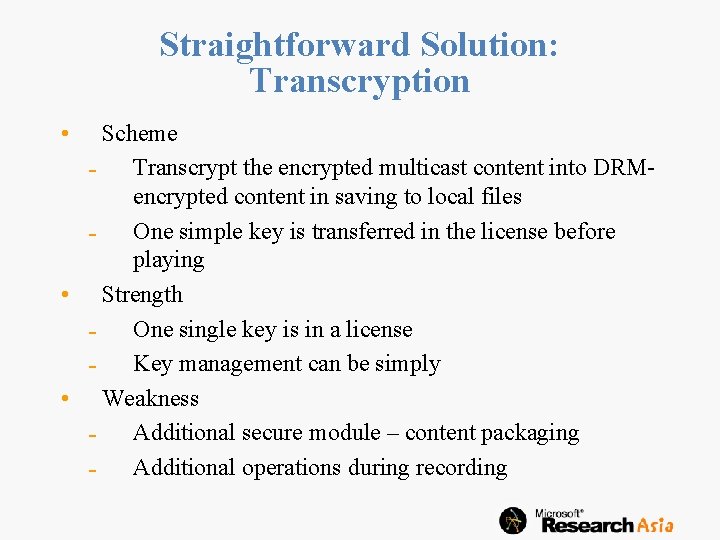
Challenges • Encryption is designed differently for restricted multicast/broadcast and DRM Restricted multicast/broadcast • Content encryption keys sent to a privileged group of users • Rekey whenever membership changes DRM • A single key is typically used to encrypt a file to simplify key management and delivery • It is difficulty to integrate the two encryption systems into one

Straightforward Solution: Direct Recording • Scheme Save encrypted multicast content directly Get all the encryption keys associated to the saved content from license server before playing • Strength • No extra operations needed to save content Weakness Complex key management – all multicast content encryption keys are maintained at license server Many keys may need to be delivered in a license to a client

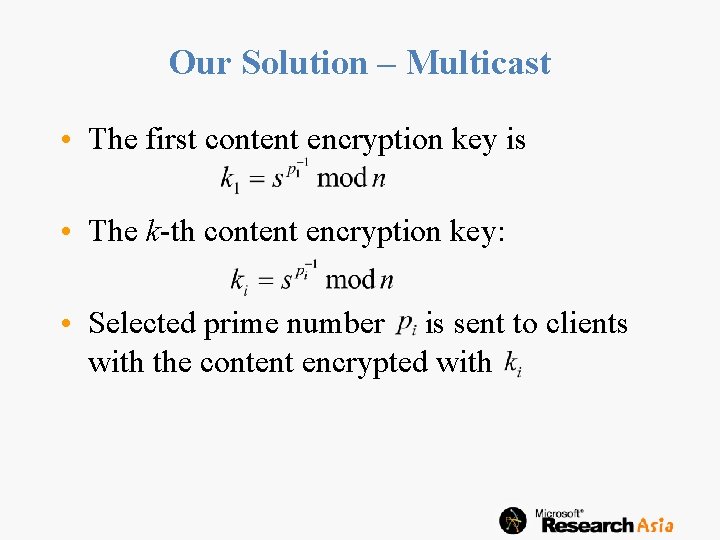
Straightforward Solution: Transcryption • • • Scheme Transcrypt the encrypted multicast content into DRMencrypted content in saving to local files One simple key is transferred in the license before playing Strength One single key is in a license Key management can be simply Weakness Additional secure module – content packaging Additional operations during recording

Question • Is it possible to design a key scheme for multicast such that the DRM has the advantages of both schemes? Saving multicast content directly to local files Simple DRM key management and delivery • The answer is yes – An integrated content encryption key scheme proposed here

Goals of Our Project • Combining advantages of both straightforward methods • With the knowledge of all used keys, a hacker cannot derive the next key • Control is exact: Only the requested content can be decrypted • Secure against collusion and other attacks

Main Ideas in Our Solution • Content encryption keys Related to each other Generated with some master secret • A “seed” secret corresponding to saved content can be generated • Content decryption keys can be regenerated from the “seed” secret • “Seed” secret cannot derive the master secret or other content encryption keys

Our Solution – Setup • n = pq, p and q are two large secret prime numbers • • P – a large collection of prime numbers • s – a random number in (1, n) and co-prime to n • A selection scheme to select numbers from P sequentially that are co-prime to • and selection scheme are master secret

Our Solution – Multicast • The first content encryption key is • The k-th content encryption key: • Selected prime number is sent to clients with the content encrypted with

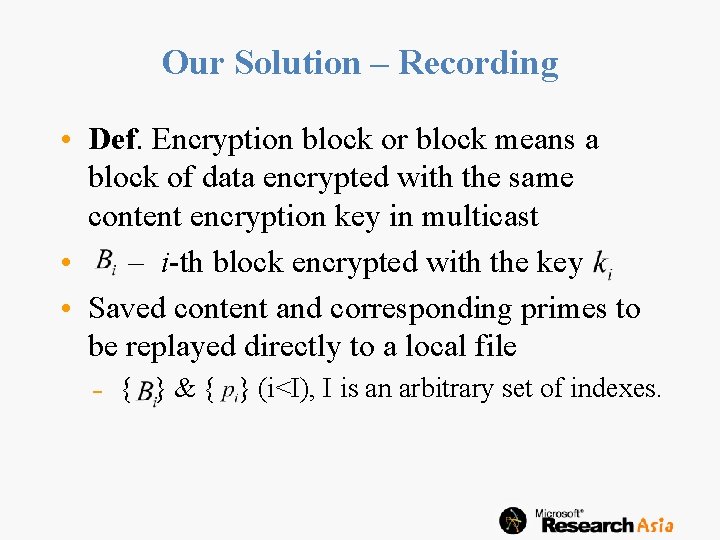
Our Solution – Recording • Def. Encryption block or block means a block of data encrypted with the same content encryption key in multicast • – i-th block encrypted with the key • Saved content and corresponding primes to be replayed directly to a local file { } & { } (i<I), I is an arbitrary set of indexes.

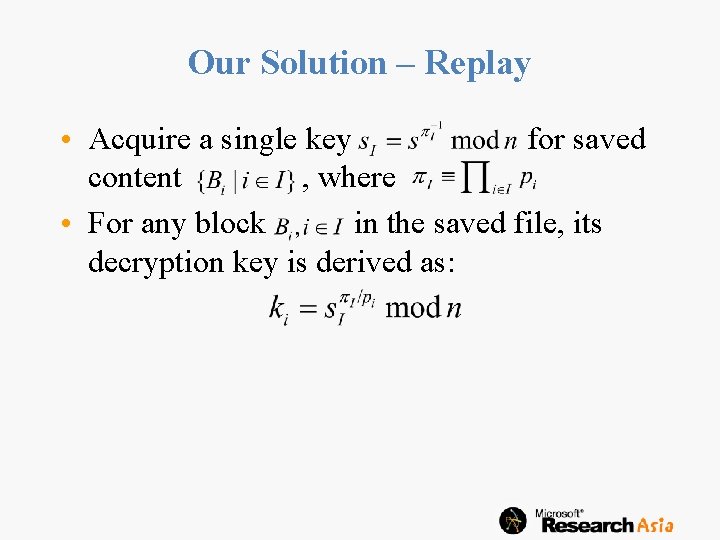
Our Solution – Replay • Acquire a single key for saved content , where • For any block in the saved file, its decryption key is derived as:

Our Solution – Security • We have proved: The seed key in the license can derive only the keys corresponding to saved content and vice versa Collusion attacks cannot deduce any new keys that they have already had • We can prove our scheme is equivalent to Strong RSA Assumption

Our Solution – Strength & Weakness • Strength Saving multicast content directly Easy key management and one single key in a license for an arbitrarily saved blocks (no need to be indexed consecutively) Easy merging and deleting contents – Only a new seed key is delivered in a new license Secure • Weakness Computation complexity Set of prime numbers may run out and reset of parameters such as s is then needed.

Conclusion • We addressed problem to protect with DRM recorded content from restricted multicast/broadcast • We proposed a novel multicast content encryption key scheme to facilitate subsequent DRM operations • Our solution is secure and makes recording and DRM key management/delivery simple

Questions?