Whats New in Fireware v 11 11 Watch























- Slides: 121

What’s New in Fireware v 11. 11 Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

2 What’s New in Fireware v 11. 11 § New Features and Enhancements • Network Discovery • Mobile Security • Botnet Detection • Explicit Proxy • Allowed Google Apps domains • Multiple Hotspot Portals • RADIUS Single Sign-On • BOVPN Virtual Interface Interoperability Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

3 What’s New in Fireware v 11. 11 § Additional Feature Enhancements • APT Blocker Clean threat level • Remove Office documents that contain macros with the SMTP Proxy • Self-signed certificate support for SMTP over TLS deep inspection • Username in HTTP Proxy Deny Message • Gateway Wireless Controller enhancements • Fire. Cluster upgrade improvements • Loopback Interface • 32 -bit BGP AS number support Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

4 Network Discovery View a graphical representation of your network Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

5 Network Discovery § Network Discovery is a subscription service that provides the ability to discover devices on your internal network and display them on a network map in Fireware Web UI § Get this information for each device: • IP Address • Device Name / Host Name • MAC address • Operating System and services • Open network ports • Mobile Security devices and compliance status Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

6 Network Discovery § When you enable Network Discovery, the process load increases and consumes additional memory • Can noticeably affect the performance of your Firebox, particularly if you have a large network § Only enable Network Discovery if you plan to use it • To minimize the performance impact, configure the Network Discovery scan settings to only scan the networks that you must monitor § Network Discovery is only supported on M and T Series Fireboxes, and XTMv devices Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

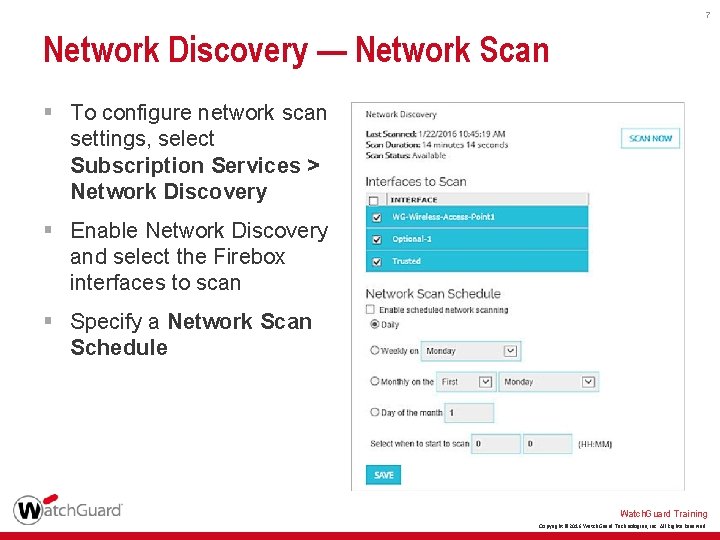
7 Network Discovery — Network Scan § To configure network scan settings, select Subscription Services > Network Discovery § Enable Network Discovery and select the Firebox interfaces to scan § Specify a Network Scan Schedule Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

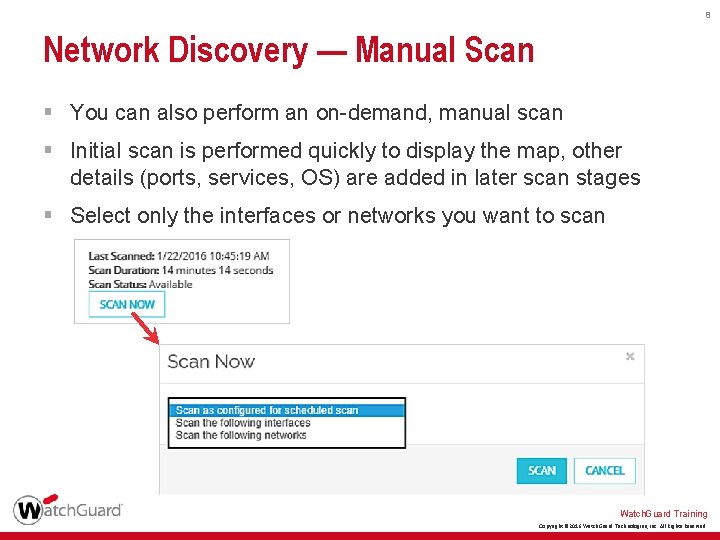
8 Network Discovery — Manual Scan § You can also perform an on-demand, manual scan § Initial scan is performed quickly to display the map, other details (ports, services, OS) are added in later scan stages § Select only the interfaces or networks you want to scan Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

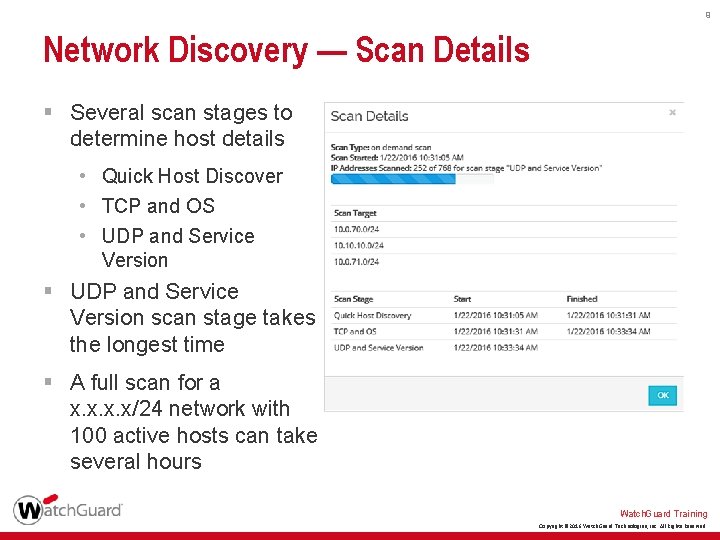
9 Network Discovery — Scan Details § Several scan stages to determine host details • Quick Host Discover • TCP and OS • UDP and Service Version § UDP and Service Version scan stage takes the longest time § A full scan for a x. x/24 network with 100 active hosts can take several hours Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

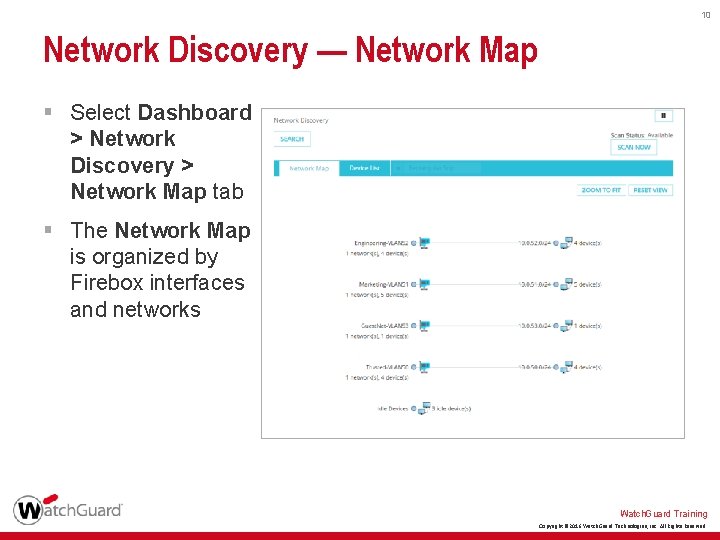
10 Network Discovery — Network Map § Select Dashboard > Network Discovery > Network Map tab § The Network Map is organized by Firebox interfaces and networks Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

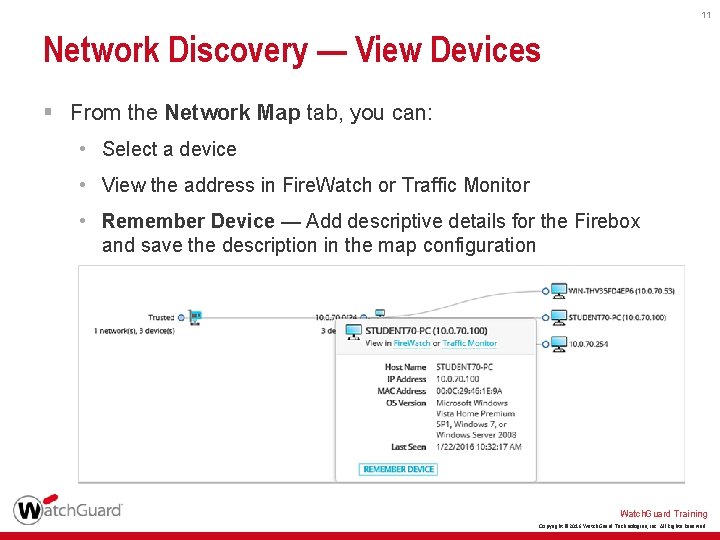
11 Network Discovery — View Devices § From the Network Map tab, you can: • Select a device • View the address in Fire. Watch or Traffic Monitor • Remember Device — Add descriptive details for the Firebox and save the description in the map configuration Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

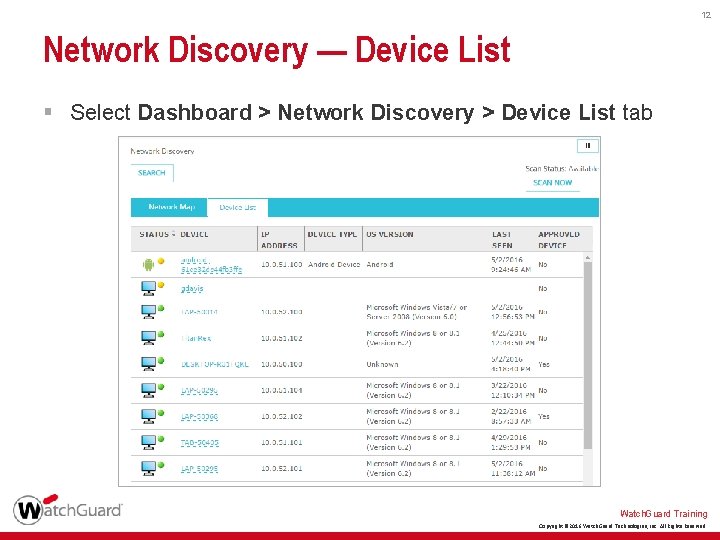
12 Network Discovery — Device List § Select Dashboard > Network Discovery > Device List tab Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

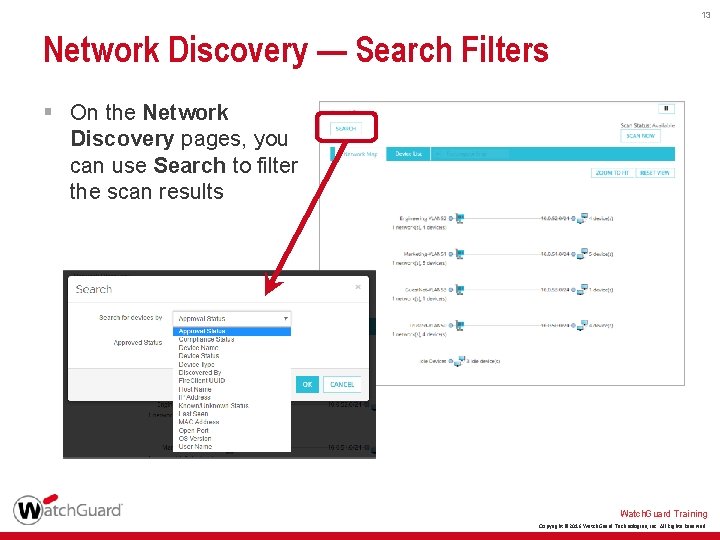
13 Network Discovery — Search Filters § On the Network Discovery pages, you can use Search to filter the scan results Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

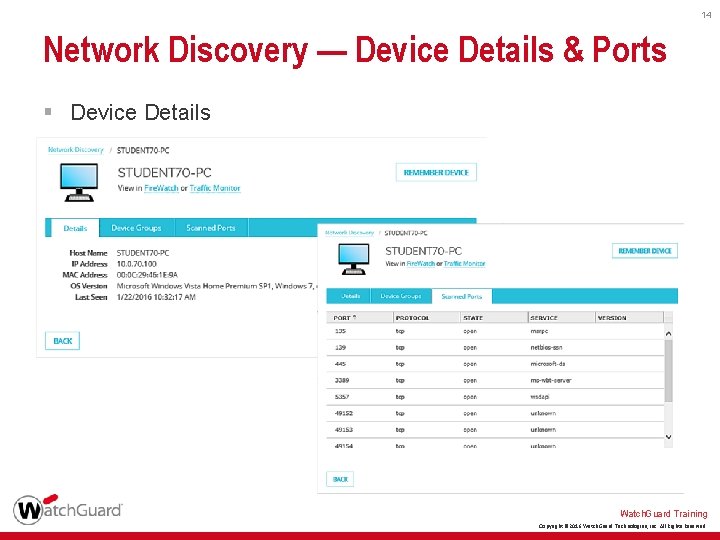
14 Network Discovery — Device Details & Ports § Device Details Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

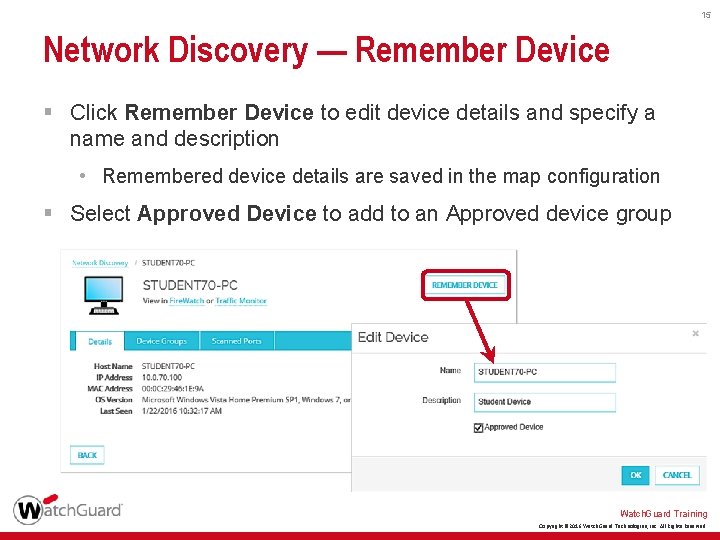
15 Network Discovery — Remember Device § Click Remember Device to edit device details and specify a name and description • Remembered device details are saved in the map configuration § Select Approved Device to add to an Approved device group Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

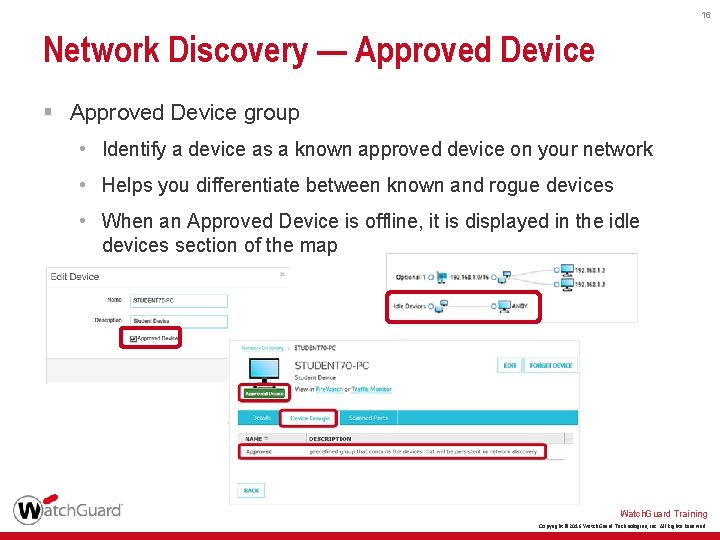
16 Network Discovery — Approved Device § Approved Device group • Identify a device as a known approved device on your network • Helps you differentiate between known and rogue devices • When an Approved Device is offline, it is displayed in the idle devices section of the map Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

17 Network Discovery — Device Expiration § Device expiration from the Network Map • Previously detected devices expire and are removed from the map when: – A new manual or scheduled scan does not discover the device – After seven days if no manual or scheduled scan is performed • Mobile devices are considered offline if no traffic is sent for more than two hours Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

18 Network Discovery — Limitations § Intermediary firewalls or other NAT devices can affect the accuracy of the scan path • Hosts cannot be discovered behind NAT § Less common OS types and services might not be recognized § Most Firebox OS versions can be detected, but not hardware models § Host name or device type cannot always be correctly detected § Subnet mask limits for scans: • /24 — Remote networks • /16 — Neighbor networks • /8 — Not scanned Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

19 Mobile Security Extend firewall security to mobile devices Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

20 Mobile Security Overview § Mobile Security sets security requirements for i. OS and Android mobile devices to send traffic through your network § Requires an additional license (number of users with expiration date) § On the Firebox, you set device compliance requirements • Approved OS versions • Not rooted or jailbroken • No malware/riskware/adware (Android only) § To be compliant, mobile users must run the Fire. Client app § Compliance status appears in the Mobile Security Dashboard § The Firebox denies traffic from mobile devices that are not compliant Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

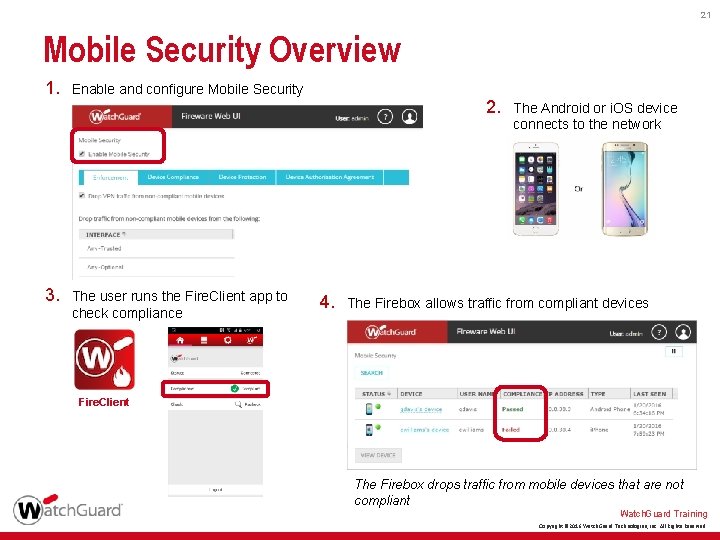
21 Mobile Security Overview 1. 3. Enable and configure Mobile Security The user runs the Fire. Client app to check compliance 2. 4. The Android or i. OS device connects to the network The Firebox allows traffic from compliant devices Fire. Client The Firebox drops traffic from mobile devices that are not compliant Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

22 Mobile Security Licensing § Mobile Security license • Specifies the maximum number of unique concurrent users • Has an expiration date • Example: MOBILE_SECURITY_USER#1000@Nov-15 -2016 – This license allows 1, 000 unique users and expires 15 Nov 2016 § User licensing is per unique user • Users must authenticate to use Mobile Security • A user can use Fire. Client to connect from more than one mobile device simultaneously, and it counts as only one user § Mobile Security is supported for Firebox models only • The Mobile Security license is not available for XTM models Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

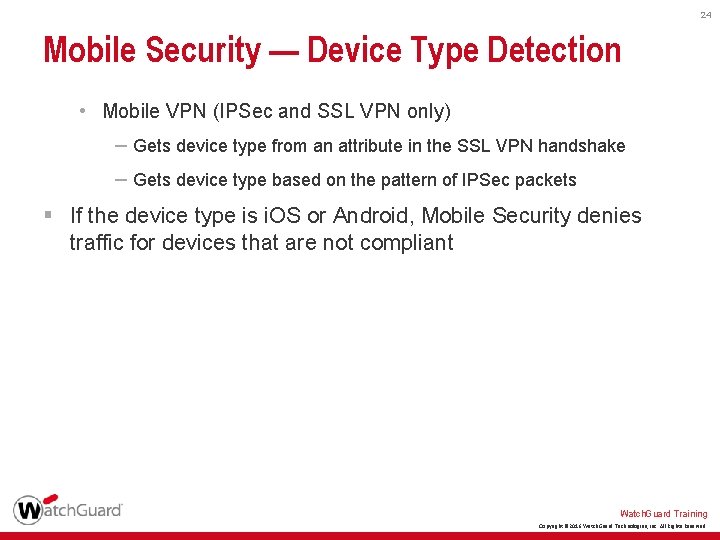
23 Mobile Security — Device Type Detection § The Firebox uses these methods to detect the device type for all devices that connect: • Firebox web portals (Hotspot Portal, Authentication Portal) – Gets device type from User-Agent in the HTTP header • Single Sign-On with Exchange Monitor – Gets device type from Exchange Server log messages • DHCP fingerprinting – Gets device type based on the pattern of traffic from DHCP clients through the Firebox – The DHCP server can be on the Firebox or on another server Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

24 Mobile Security — Device Type Detection • Mobile VPN (IPSec and SSL VPN only) – Gets device type from an attribute in the SSL VPN handshake – Gets device type based on the pattern of IPSec packets § If the device type is i. OS or Android, Mobile Security denies traffic for devices that are not compliant Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

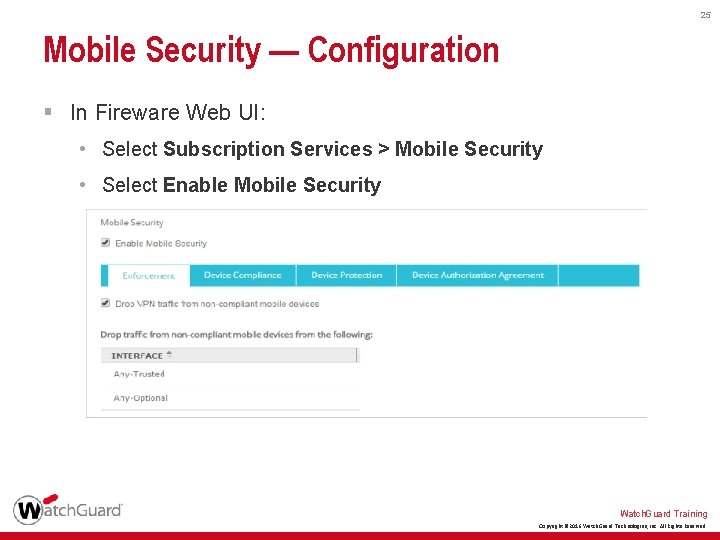
25 Mobile Security — Configuration § In Fireware Web UI: • Select Subscription Services > Mobile Security • Select Enable Mobile Security Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

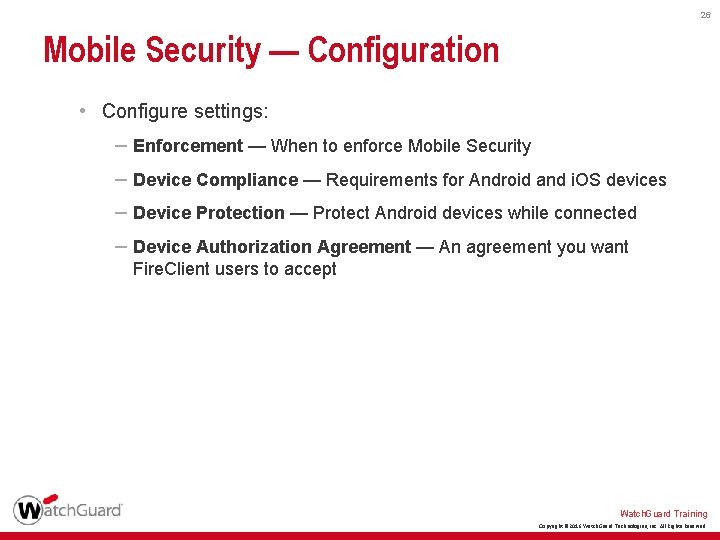
26 Mobile Security — Configuration • Configure settings: – Enforcement — When to enforce Mobile Security – Device Compliance — Requirements for Android and i. OS devices – Device Protection — Protect Android devices while connected – Device Authorization Agreement — An agreement you want Fire. Client users to accept Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

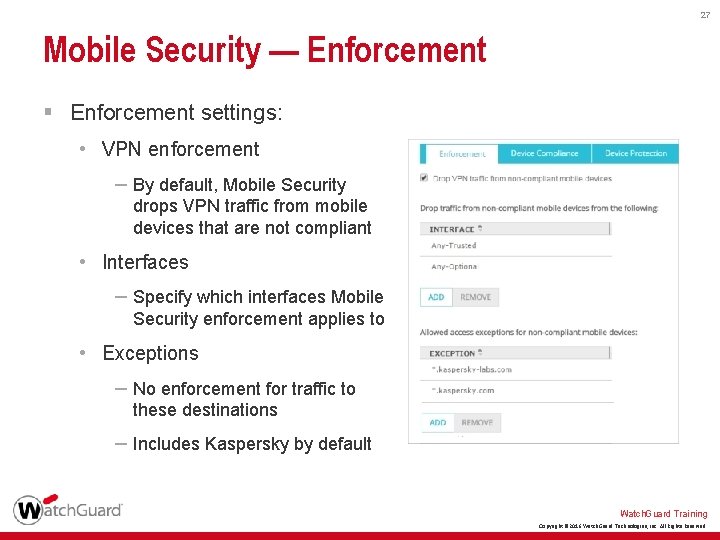
27 Mobile Security — Enforcement § Enforcement settings: • VPN enforcement – By default, Mobile Security drops VPN traffic from mobile devices that are not compliant • Interfaces – Specify which interfaces Mobile Security enforcement applies to • Exceptions – No enforcement for traffic to these destinations – Includes Kaspersky by default Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

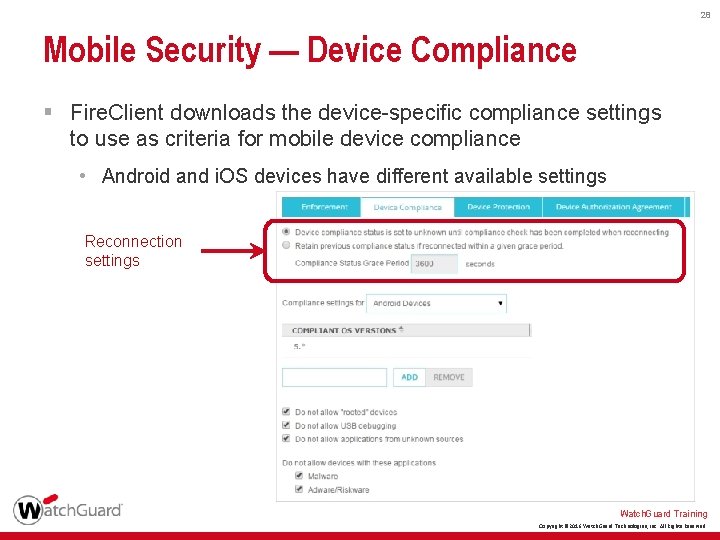
28 Mobile Security — Device Compliance § Fire. Client downloads the device-specific compliance settings to use as criteria for mobile device compliance • Android and i. OS devices have different available settings Reconnection settings Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

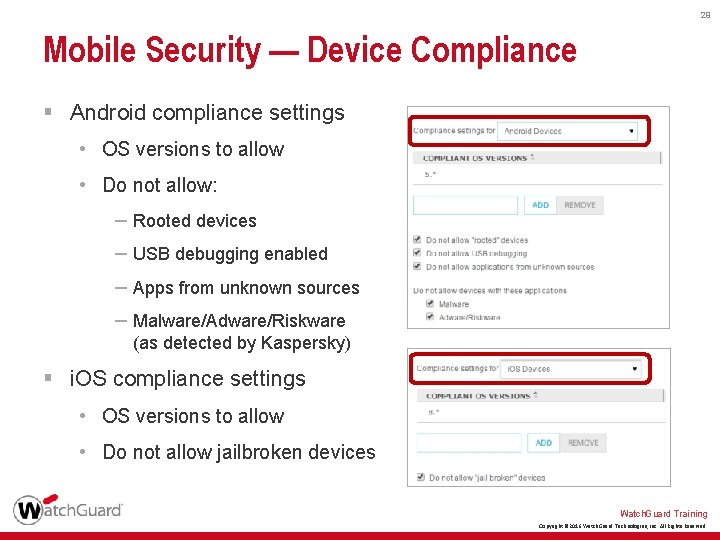
29 Mobile Security — Device Compliance § Android compliance settings • OS versions to allow • Do not allow: – Rooted devices – USB debugging enabled – Apps from unknown sources – Malware/Adware/Riskware (as detected by Kaspersky) § i. OS compliance settings • OS versions to allow • Do not allow jailbroken devices Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

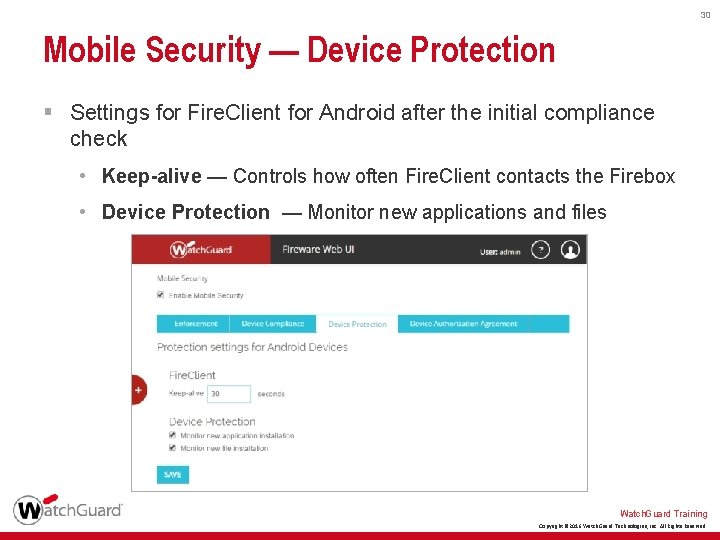
30 Mobile Security — Device Protection § Settings for Fire. Client for Android after the initial compliance check • Keep-alive — Controls how often Fire. Client contacts the Firebox • Device Protection — Monitor new applications and files Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

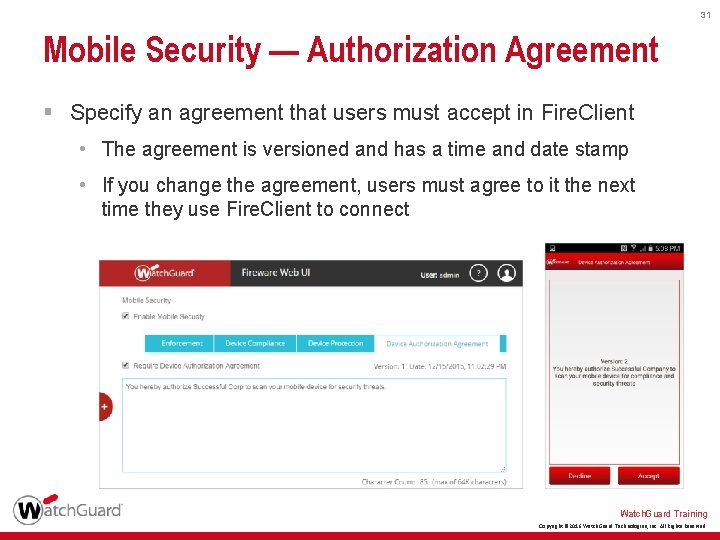
31 Mobile Security — Authorization Agreement § Specify an agreement that users must accept in Fire. Client • The agreement is versioned and has a time and date stamp • If you change the agreement, users must agree to it the next time they use Fire. Client to connect Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

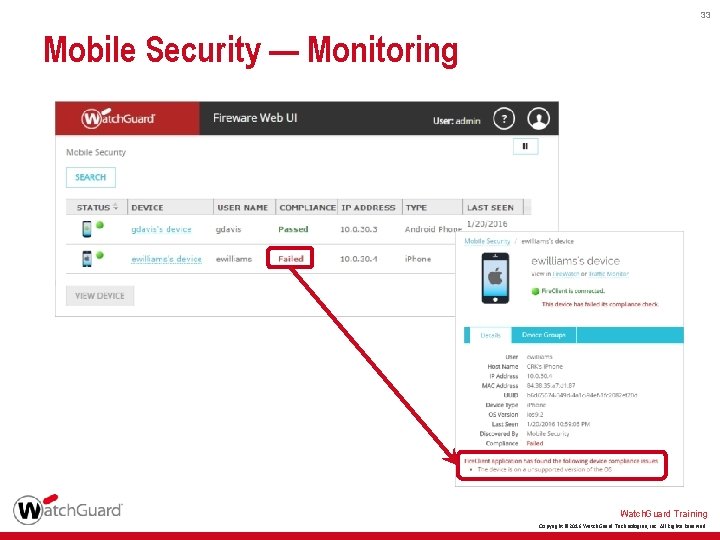
32 Mobile Security — Monitoring § Mobile Security Dashboard • Includes all mobile devices that have connected with Fire. Client • View device details to see why the device is not compliant • Compliance status: – Passed — Device is compliant – Failed — Device is not compliant – Unknown — Fire. Client is not connected or did not yet report compliance status Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

33 Mobile Security — Monitoring Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

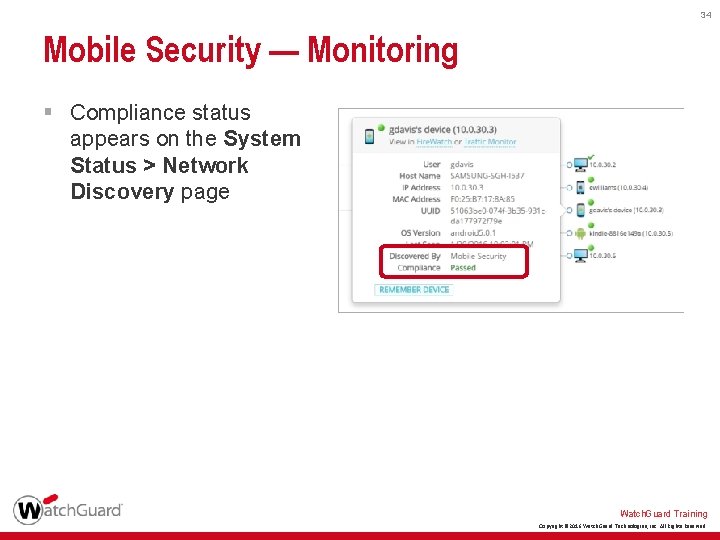
34 Mobile Security — Monitoring § Compliance status appears on the System Status > Network Discovery page Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

35 Fire. Client § Mobile app for Android and i. OS devices • Requires user to authenticate unless already authenticated • Downloads a compliance checklist from the Firebox • Uses Kaspersky service for malware detection (Android only) • Checks mobile device compliance status and reports to Firebox • Uses HTTP and HTTPS to communicate to the Firebox • Sends keep-alive requests to maintain a connection to the Firebox Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

36 Fire. Client § OS Compatibility • Android 4. 1 and higher • i. OS 8 and higher § Availability • Free in the Google Play store and the Apple App Store Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

37 Use Fire. Client § Install Fire. Client from Google Play store or Apple App Store § To install Fire. Client, connect to a network that does not have Mobile Security enabled § Connect to the corporate network with Wi. Fi or a VPN § Launch Fire. Client Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

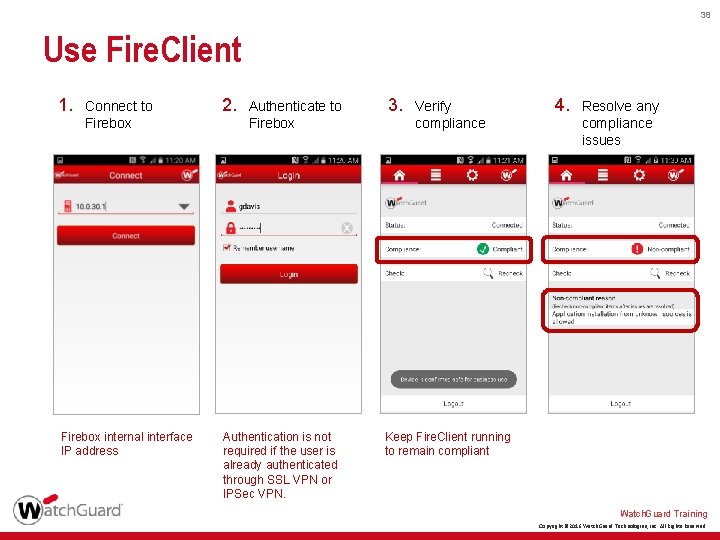
38 Use Fire. Client 1. Connect to Firebox internal interface IP address 2. Authenticate to Firebox Authentication is not required if the user is already authenticated through SSL VPN or IPSec VPN. 3. Verify compliance 4. Resolve any compliance issues Keep Fire. Client running to remain compliant Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

39 Scenario — Local Connection § Employee brings Android tablet to work and wants to use the company internal wireless network • User connects the tablet to an AP device on the trusted network • Without Fire. Client, the device can only connect to destinations on the Mobile Security exception list (Kaspersky) • User connects and authenticates from Fire. Client – Fire. Client downloads the compliance checklist from the Firebox – Fire. Client uses Kaspersky cloud service for malware detection – If malware is found, the user is prompted to remove the app – If detected malware is not removed, the compliance check fails • After Fire. Client reports the device is compliant, the tablet can access all destinations allowed by other policies Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

40 Scenario — VPN Connection § Employee uses IPSec or SSL Mobile VPN to connect and authenticate to the corporate network from an i. Pad • VPN component on the Firebox detects the device type is i. Pad • Mobile Security drops VPN traffic from mobile devices that are not compliant (enabled by default) • Traffic through the VPN is allowed only to sites on the Mobile Security exception list • User connects from Fire. Client – No authentication is required, because user is already authenticated – Fire. Client downloads compliance checklist and checks compliance • After Fire. Client reports the device is compliant, the i. Pad can access all destinations allowed by other policies Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

41 Botnet Detection Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

42 Botnet Detection § A botnet comprises a large number of malware-infected client computers that are controlled by a remote server to perform malicious acts • Denial-of-service attacks • Sending spam and viruses • Stealing private data from clients § The Firebox can already block access from infected clients on your network to botnet sites over HTTP with the Web. Blocker Command Control and Botnet Activity categories § Botnets are now finding other paths to control infected botnet clients using non-traditional network ports, social networks, and P 2 P networks Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

43 Botnet Detection § The new Botnet Detection Subscription Service uses a feed of known botnet site IP addresses from Reputation Enabled Defense (RED) and adds these addresses to the Blocked Sites List • Note: The Botnet Sites list is too large to display in the Blocked Sites List § Enables your Firebox to block botnet activity at the packet level § Botnet Detection is enabled with the RED feature key Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

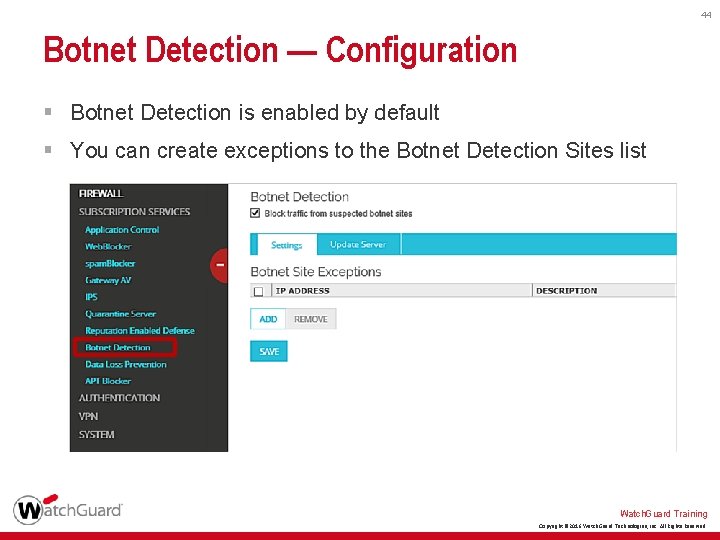
44 Botnet Detection — Configuration § Botnet Detection is enabled by default § You can create exceptions to the Botnet Detection Sites list Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

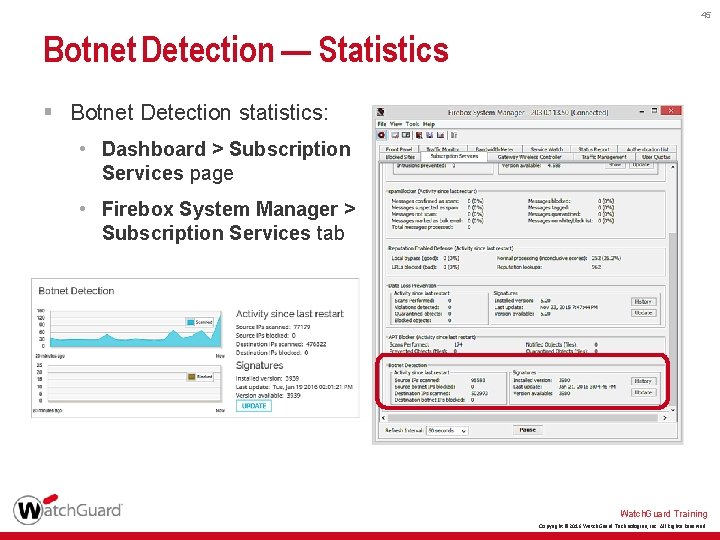
45 Botnet Detection — Statistics § Botnet Detection statistics: • Dashboard > Subscription Services page • Firebox System Manager > Subscription Services tab Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

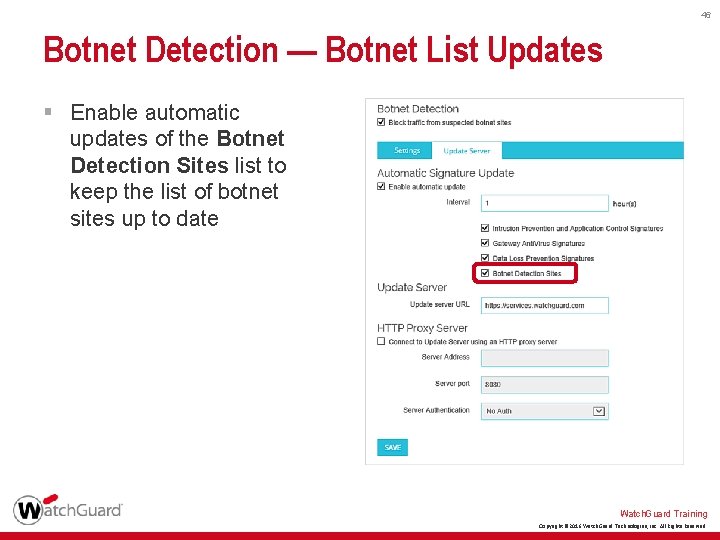
46 Botnet Detection — Botnet List Updates § Enable automatic updates of the Botnet Detection Sites list to keep the list of botnet sites up to date Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

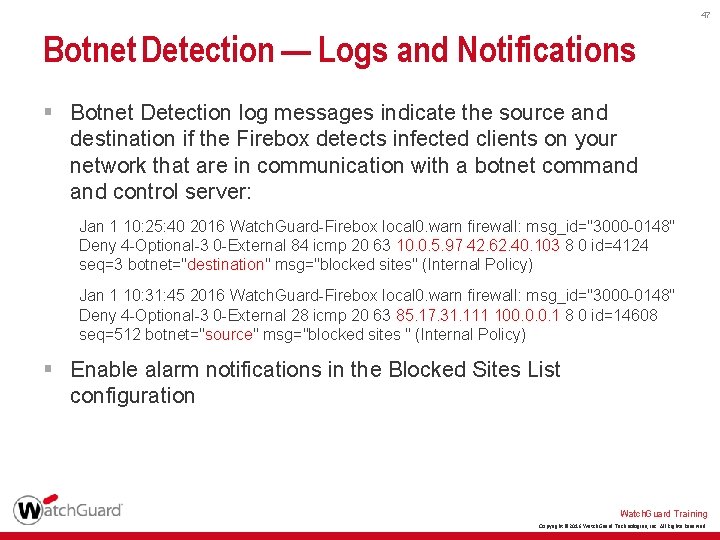
47 Botnet Detection — Logs and Notifications § Botnet Detection log messages indicate the source and destination if the Firebox detects infected clients on your network that are in communication with a botnet command control server: Jan 1 10: 25: 40 2016 Watch. Guard-Firebox local 0. warn firewall: msg_id="3000 -0148" Deny 4 -Optional-3 0 -External 84 icmp 20 63 10. 0. 5. 97 42. 62. 40. 103 8 0 id=4124 seq=3 botnet="destination" msg="blocked sites" (Internal Policy) Jan 1 10: 31: 45 2016 Watch. Guard-Firebox local 0. warn firewall: msg_id="3000 -0148" Deny 4 -Optional-3 0 -External 28 icmp 20 63 85. 17. 31. 111 100. 0. 0. 1 8 0 id=14608 seq=512 botnet="source" msg="blocked sites " (Internal Policy) § Enable alarm notifications in the Blocked Sites List configuration Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

48 Explicit Proxy Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

49 Explicit Proxy § In a typical proxy configuration, the Firebox transparently proxies and inspects client connections to servers § Explicit proxy support enables the Firebox to accept direct requests from clients and then connect to specified servers and retrieve the information on behalf of the client § Provides easier drop-in integration for customers that want to replace an existing proxy server with a Firebox, without infrastructure and client reconfiguration Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

50 Explicit Proxy — HTTP Explicit Proxy § HTTP Explicit Proxy • Web browser clients are configured to send requests directly to the Firebox IP address and port • HTTP traffic is proxied and inspected by Firebox security services, and the configured HTTP Proxy Action rules apply • Firebox adds a Via Header to the HTTP Request/Response – This can be the Firebox IP address or a customizable alias • Explicit Proxy uses TCP port 3128 by default • Web caching is not performed by the Firebox • Explicit Proxy is logged and reported in Dimension as HTTP Proxy traffic Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

51 Explicit Proxy — HTTP CONNECT Tunnel § HTTP CONNECT tunneling support for HTTPS • Client sends an HTTP request to the Firebox Explicit Proxy on port number 3128 • The Explicit Proxy establishes a TCP connection to the specified destination • When the connection is established, the Explicit Proxy responds to the original HTTP request with an HTTP response, and then the client can send data to the destination server • Allow, Deny, or Block based on the specified ports, or select an HTTPS proxy action to use for HTTPS traffic through a tunnel Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

52 Explicit Proxy — FTP over HTTP (Web FTP) § FTP over HTTP connection support • The Explicit Proxy can proxy FTP connections sent over HTTP (also known as Web FTP) • For example, a web URL specified as ftp: //ftp. example. com/path or ftp: //user: password@ftp. example. com/path/ • The Explicit Proxy connects to the destination server with native FTP commands to retrieve a directory listing or file, and then sends the data to the client in an HTTP response – HTTP request is subject to the Explicit Proxy rules – Firebox uses the FTP protocol through the specified FTP proxy action, and standard FTP proxy action rules apply – HTTP response to the client is not passed through the Explicit Proxy action Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

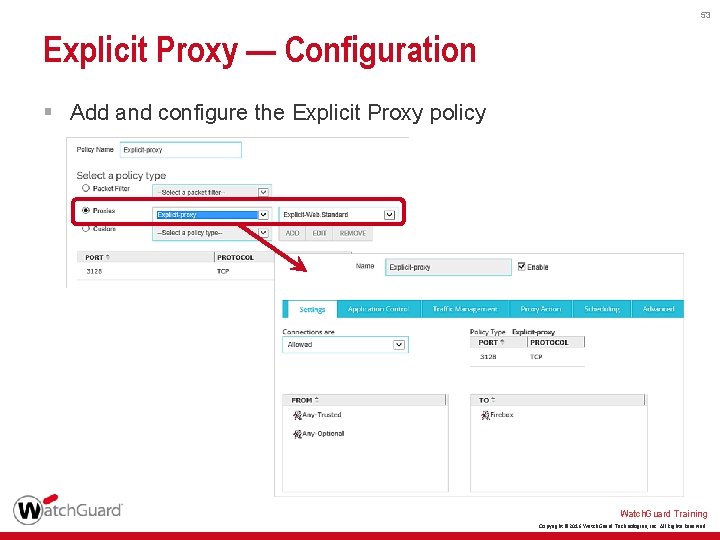
53 Explicit Proxy — Configuration § Add and configure the Explicit Proxy policy Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

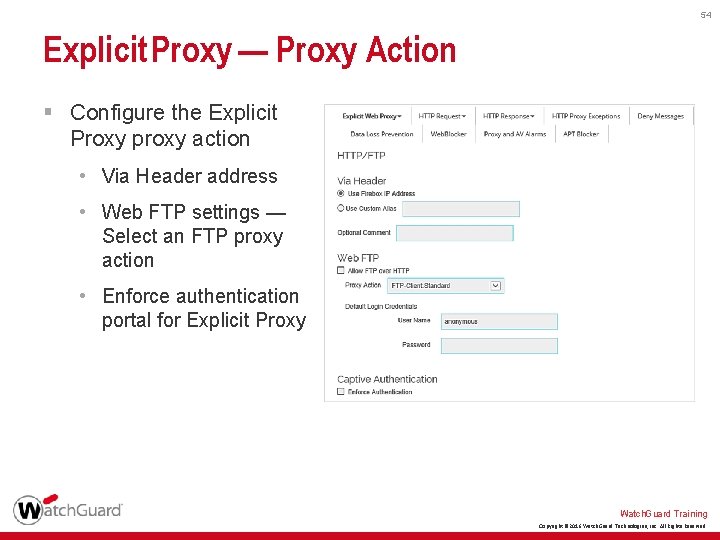
54 Explicit Proxy — Proxy Action § Configure the Explicit Proxy proxy action • Via Header address • Web FTP settings — Select an FTP proxy action • Enforce authentication portal for Explicit Proxy Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

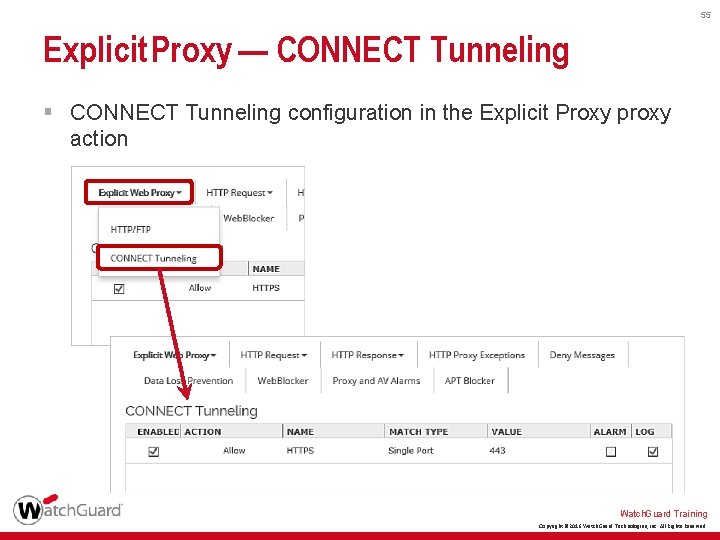
55 Explicit Proxy — CONNECT Tunneling § CONNECT Tunneling configuration in the Explicit Proxy proxy action Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

56 Explicit Proxy — PAC Files § Proxy Auto-Configuration (PAC) File Support • A PAC file is a simple Java. Script file with the proxy configuration for a client web browser • The PAC file configures the web browser with a proxy server address (the Firebox) • The PAC file can be hosted on the Firebox and made available to clients with Web Proxy Auto-Discovery Protocol (WPAD) • Configure WPAD with a custom DHCP rule on a Firebox interface – Option 252 – Note: The Firebox does not support WPAD with DNS Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

57 Explicit Proxy — PAC Files • You can manage multiple PAC files on the Firebox • PAC files can be synchronized in a cluster – Note: The Firebox does not validate the contents of PAC files Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

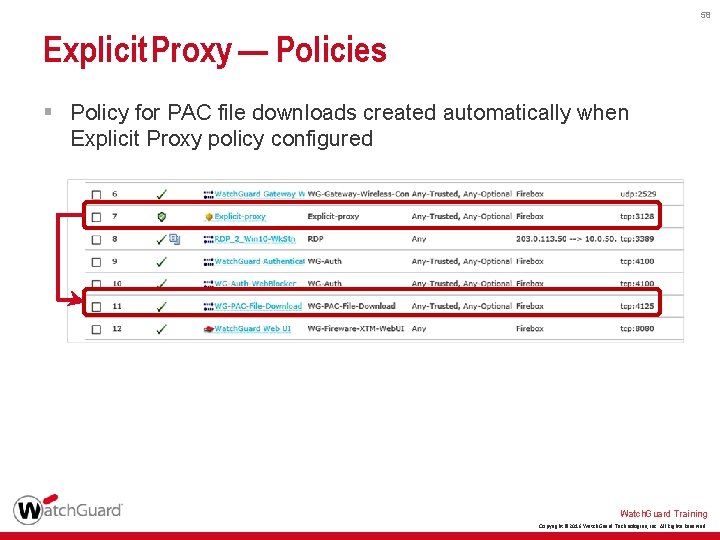
58 Explicit Proxy — Policies § Policy for PAC file downloads created automatically when Explicit Proxy policy configured Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

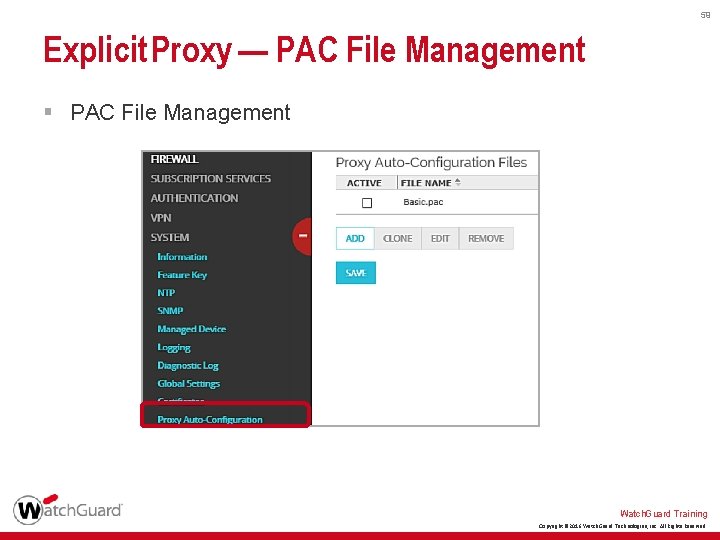
59 Explicit Proxy — PAC File Management § PAC File Management Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

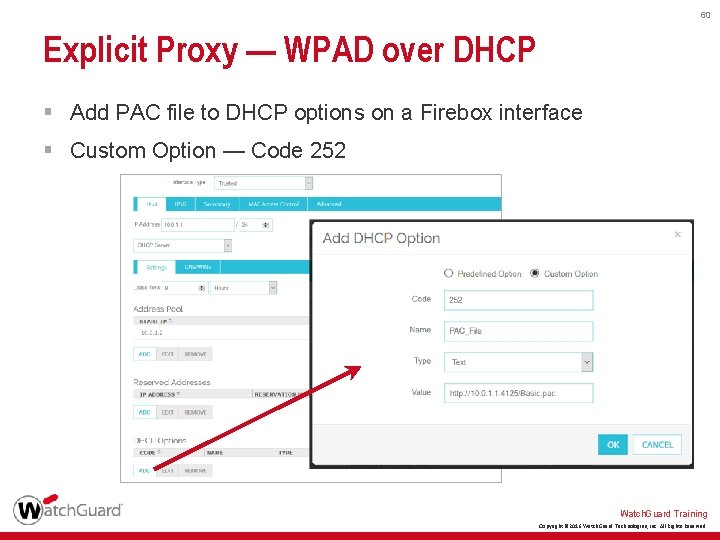
60 Explicit Proxy — WPAD over DHCP § Add PAC file to DHCP options on a Firebox interface § Custom Option — Code 252 Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

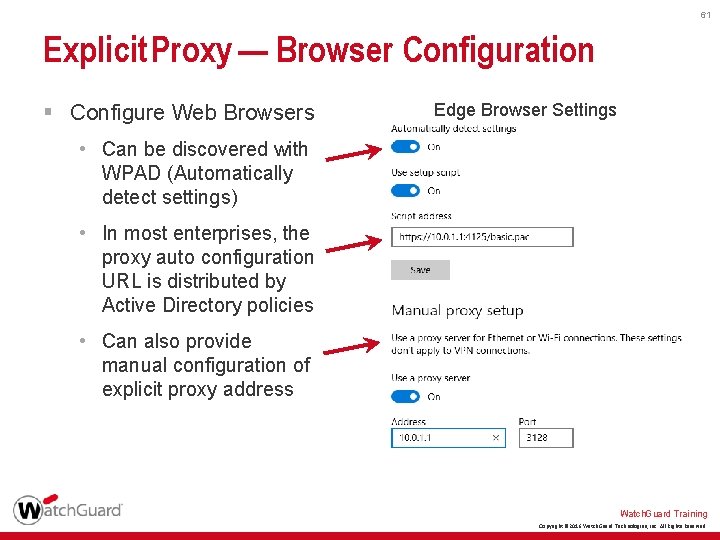
61 Explicit Proxy — Browser Configuration § Configure Web Browsers Edge Browser Settings • Can be discovered with WPAD (Automatically detect settings) • In most enterprises, the proxy auto configuration URL is distributed by Active Directory policies • Can also provide manual configuration of explicit proxy address Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

62 Allowed Google Apps Domains Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

63 Allowed Google Apps Domains § Use the HTTPS Proxy with content inspection enabled to block users from accessing personal Google services § Configure specific domains that are allowed access to Google services § Allow domains used for Google for Work services and block users from logging into Google Gmail or other personal Google service accounts § Content inspection must be enabled because most Google services are SSL encrypted Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

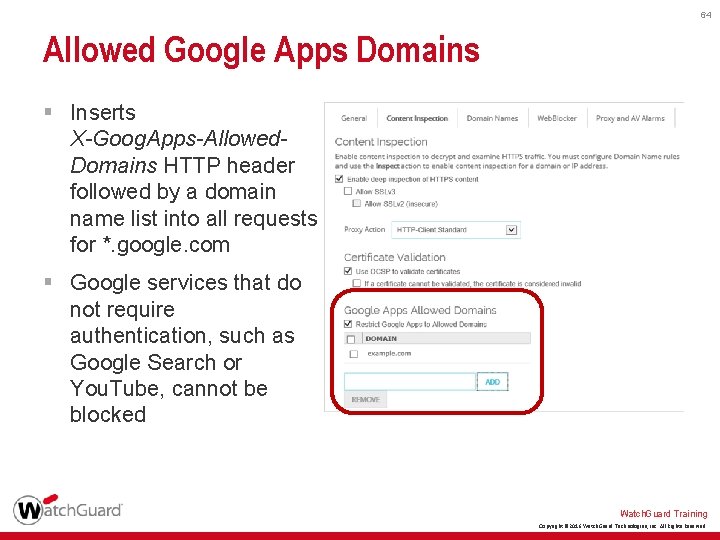
64 Allowed Google Apps Domains § Inserts X-Goog. Apps-Allowed. Domains HTTP header followed by a domain name list into all requests for *. google. com § Google services that do not require authentication, such as Google Search or You. Tube, cannot be blocked Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

65 RADIUS SSO Single Sign-On with RADIUS Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

66 RADIUS SSO — Overview § RADIUS SSO (RSSO) enables single sign-on for users who have already authenticated to a RADIUS server with 802. 1 x authentication • Targeted primarily at wireless users – Many universities and large schools have existing wireless networks that use RADIUS for user authentication • Can also work for a wired network – Switch must have 802. 1 x enabled and must be used for NAC (network access control) with the RADIUS server Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

67 RADIUS SSO — Overview • Requirement for RSSO – The wireless access point (AP), switch, or access controller (AC) that users connect to must support 802. 1 x authentication and RADIUS accounting – The AP or AC switch must send RADIUS accounting messages that include the user’s IP address to the RADIUS server Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

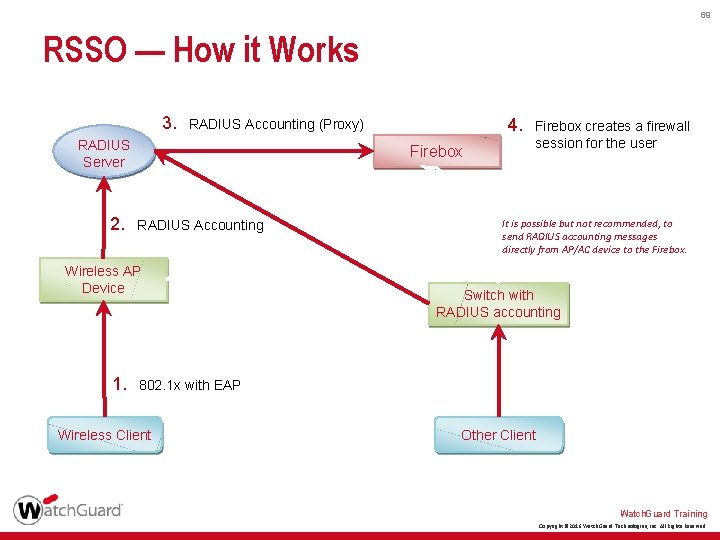
68 RSSO — How it Works 1. Client authenticates to the AP with WPA/WPA 2 Enterprise 2. AP interacts with RADIUS server to authenticate the user 3. AP sends RADIUS accounting messages with user name and IP address through RADIUS proxy server to the Firebox 4. Firebox creates a firewall session for the authenticated user Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

69 RSSO — How it Works 3. RADIUS Server 2. Firebox RADIUS Accounting Wireless AP Device 1. 4. RADIUS Accounting (Proxy) Firebox creates a firewall session for the user It is possible but not recommended, to send RADIUS accounting messages directly from AP/AC device to the Firebox. Switch with RADIUS accounting 802. 1 x with EAP Wireless Client Other Client Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

70 RSSO — How it Works § For RSSO to work, the Start, Stop and Interim-Update RADIUS accounting messages must include these attributes: • User-Name — Name of the authenticated user • Framed-IP-Address — Actual IP address of the user § When mobile devices connect with WPA/WPA 2 authentication: • AP device sends RADIUS accounting messages from the RADIUS proxy server to Firebox • Firebox creates a user session when it receives a Start or Interim-Update message with the user name and IP address Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

71 RSSO — How it Works § When mobile devices disconnect: • AP device sends RADIUS accounting message from the RADIUS proxy server to Firebox • Firebox removes the user session when it receives the Stop accounting message with the user name and IP address Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

72 RSSO Support § RSSO should work for connections to AP and AC devices that support the User-Name and Framed-IP-Address attributes in RADIUS accounting messages § Who supports it: • Watch. Guard AP devices — Supported on all Watch. Guard AP device models in an AP firmware update to be released with Fireware v 11. 11 • Aruba IAP — Verified it works well • Ruckus AC — Not confirmed (Ruckus documentation indicates it supports Framed-IP-Address) • Cisco Meraki — Cloud management, not confirmed (Cisco documentation says it supports Framed-IP-Address) Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

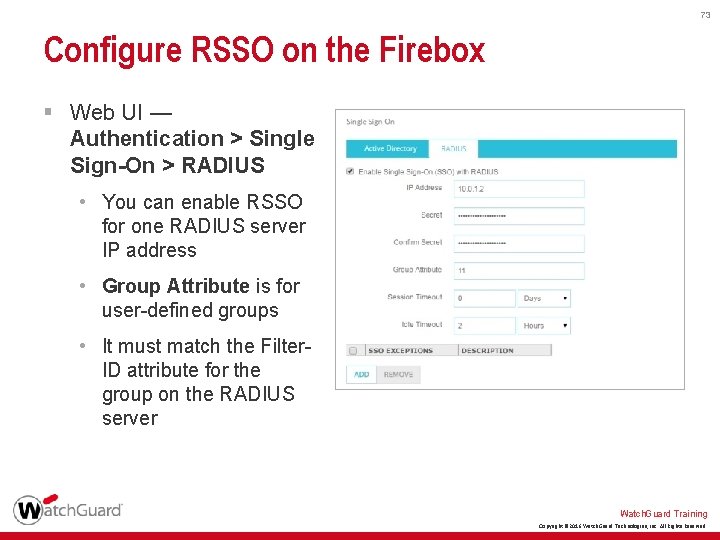
73 Configure RSSO on the Firebox § Web UI — Authentication > Single Sign-On > RADIUS • You can enable RSSO for one RADIUS server IP address • Group Attribute is for user-defined groups • It must match the Filter. ID attribute for the group on the RADIUS server Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

74 RSSO — Groups and Policies § When you enable RSSO, the group RADIUS-SSO-Users is automatically created on the Firebox • RSSO also supports user-defined groups configured on both the RADIUS server and the Firebox • Only RSSO users who are not a member of a user-defined group are considered members of the RADIUS-SSO-Users group Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

75 RSSO — Groups and Policies § When you enable RSSO, two policies are automatically added • Allow RADIUS SSO Service – Allows incoming accounting traffic on port 1813 to the Firebox – Allows traffic from the RADIUS server IP address to the Firebox • Allow RADIUS SSO Users – Allows outgoing traffic from authenticated users – Allows TCP-UDP traffic from RADIUS-SSO-Users to Any-External Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

76 RADIUS Proxy Server § You can configure a RADIUS server, such as freeradius, as a RADIUS accounting proxy • The RADIUS server receives accounting messages from the AP device or AC and sends them to the Firebox – Communication is protected by the shared secret – The Firebox can only receive accounting communication from the one IP address configured in the Firebox RADIUS SSO settings Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

77 RADIUS Proxy Server § One AP device or AC can send RADIUS accounting messages directly to the Firebox rather than through a proxy • The IP address of the AP device or AC must match what is configured in the Firebox RADIUS SSO settings • For SSO from more than one AP device or AC, accounting messages must be routed through a RADIUS accounting proxy server § RSSO Session Timeout and Idle Timeout are independent of global Firebox timeouts or timeouts on the RADIUS server Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

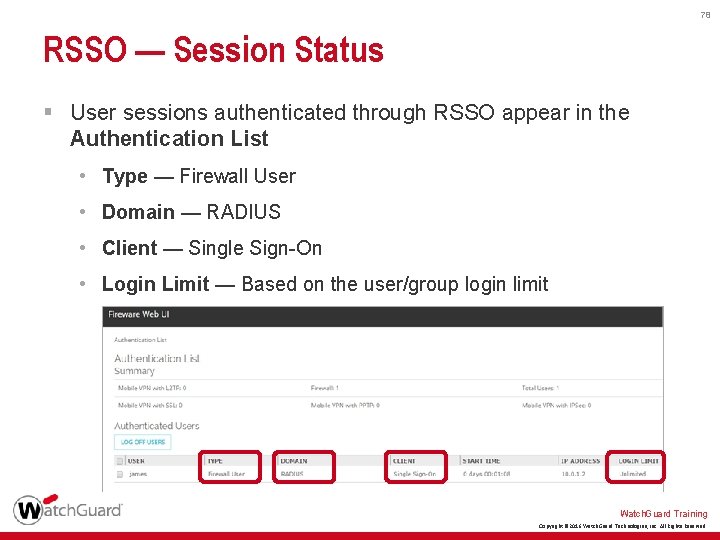
78 RSSO — Session Status § User sessions authenticated through RSSO appear in the Authentication List • Type — Firewall User • Domain — RADIUS • Client — Single Sign-On • Login Limit — Based on the user/group login limit Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

79 RSSO and the Authentication Portal § When RSSO is enabled, users can still use the Authentication Portal on the Firebox to authenticate with another account in a different domain or with different group membership § Authentication Portal sessions override RSSO sessions for user connections from the same IP address • A session created by the Authentication Portal replaces any existing session created by RSSO for the same IP address • A session created by RSSO does not replace an existing session created by the Authentication Portal for the same IP address Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

80 RSSO and AD SSO § You can enable both RSSO and AD SSO at the same time § RSSO will not replace sessions created by AD SSO § If possible, to avoid an overlap that can cause authentication inconsistencies, do not use both RSSO and AD SSO for the same subnet or IP address range § If you must use both SSO types for some clients in the same subnet, use the RSSO or AD SSO Exception list to define the expected session priority • The Exception list defines IP addresses for clients that do not use that SSO type Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

81 Multiple Hotspots Configure different hotspot portals for different Firebox interfaces Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

82 Multiple Hotspots Overview § You can now configure multiple hotspots § You can enable each hotspot for one or more interfaces • Interfaces can be physical or virtual (VLAN, bridge, link aggregation, wireless) § Each hotspot can use a different authentication type • Connect without credentials • Require users to authenticate with generated credentials (user name and passphrase or passphrase only) § External Guest Authentication • There is still only one external guest hotspot • You can now enable it for multiple interfaces Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

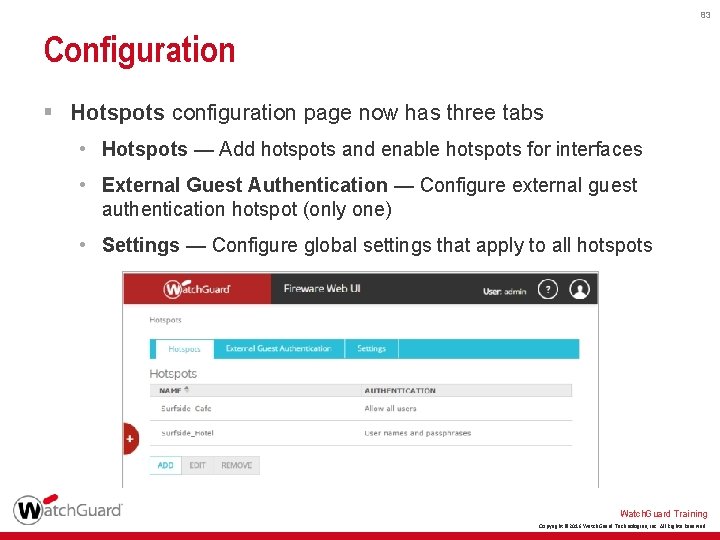
83 Configuration § Hotspots configuration page now has three tabs • Hotspots — Add hotspots and enable hotspots for interfaces • External Guest Authentication — Configure external guest authentication hotspot (only one) • Settings — Configure global settings that apply to all hotspots Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

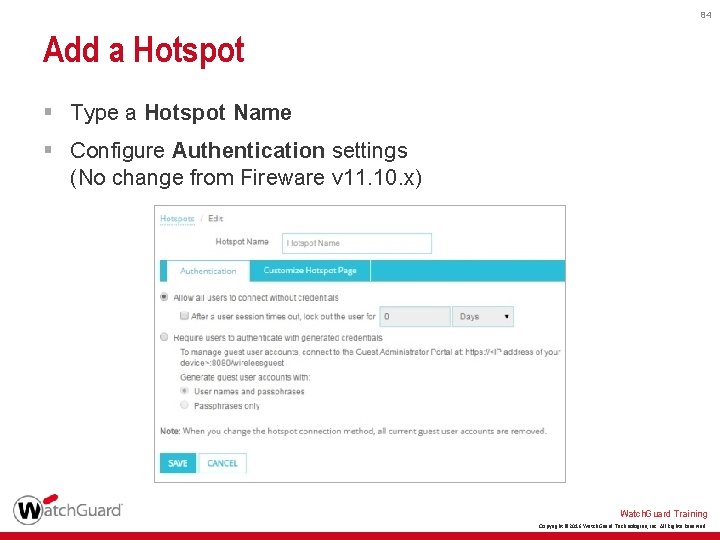
84 Add a Hotspot § Type a Hotspot Name § Configure Authentication settings (No change from Fireware v 11. 10. x) Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

85 Add a Hotspot § Customize the hotspot page • Text, logo, terms, color • No change from Fireware v 11. 10. x Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

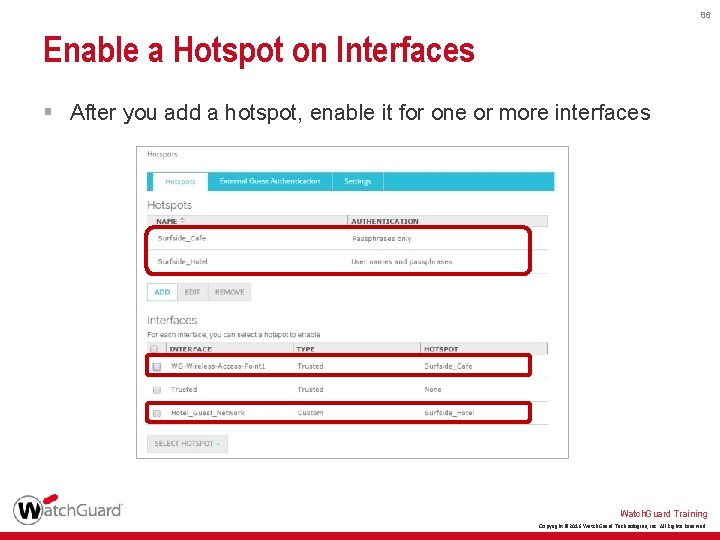
86 Enable a Hotspot on Interfaces § After you add a hotspot, enable it for one or more interfaces Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

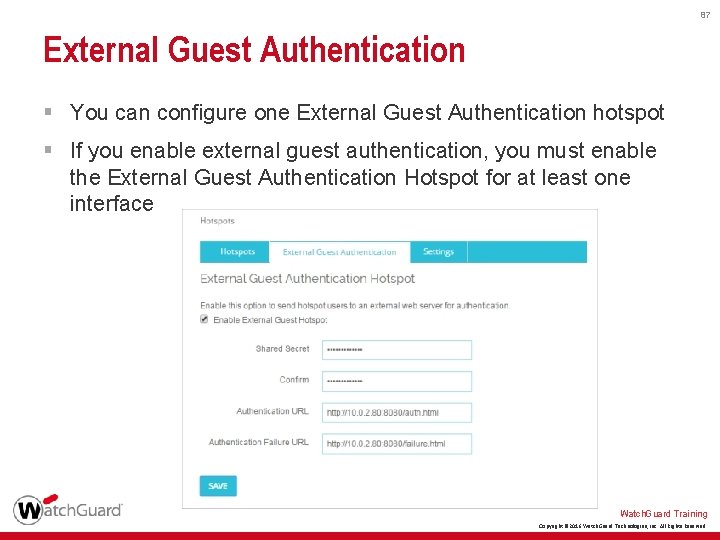
87 External Guest Authentication § You can configure one External Guest Authentication hotspot § If you enable external guest authentication, you must enable the External Guest Authentication Hotspot for at least one interface Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

88 Hotspot Settings § On the Settings tab, configure settings common to all hotspots • No change from Fireware v 11. 10. x. Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

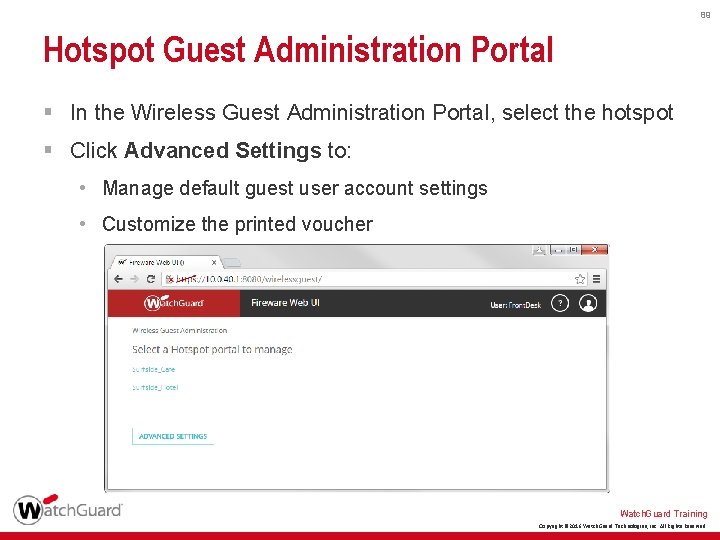
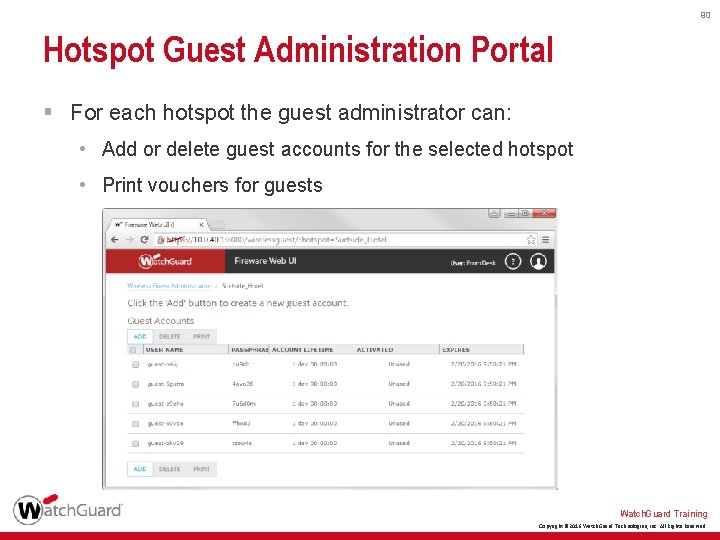
89 Hotspot Guest Administration Portal § In the Wireless Guest Administration Portal, select the hotspot § Click Advanced Settings to: • Manage default guest user account settings • Customize the printed voucher Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

90 Hotspot Guest Administration Portal § For each hotspot the guest administrator can: • Add or delete guest accounts for the selected hotspot • Print vouchers for guests Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

91 BOVPN Interoperability Connect a BOVPN virtual interface to a third-party VPN endpoint that supports GRE Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

92 BOVPN Interoperability § BOVPN virtual interface routes are now supported between a Firebox and a third-party device that uses GRE • Examples: – Firebox to Cisco – Firebox to Fortinet § Both static and dynamic routing through the BOVPN virtual interface are supported • For static routing through the VPN, configure BOVPN virtual interface routes exactly the same as for BOVPN virtual interface routes between two Fireboxes • For dynamic routing to a third-party VPN endpoint, the configuration is different Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

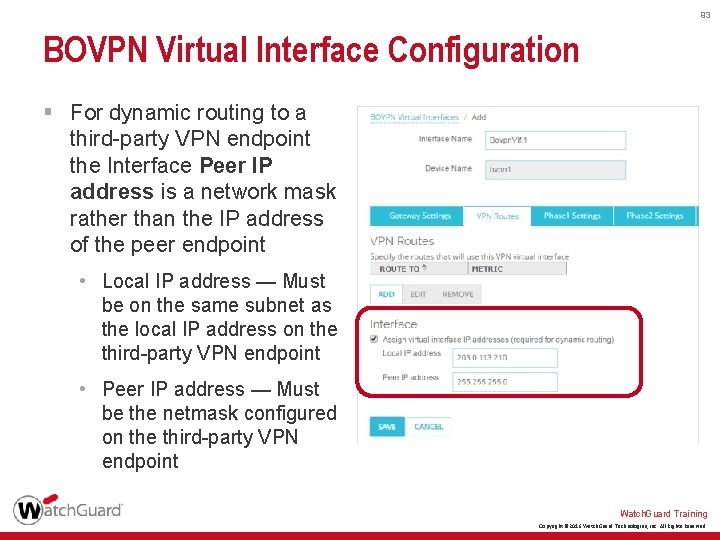
93 BOVPN Virtual Interface Configuration § For dynamic routing to a third-party VPN endpoint the Interface Peer IP address is a network mask rather than the IP address of the peer endpoint • Local IP address — Must be on the same subnet as the local IP address on the third-party VPN endpoint • Peer IP address — Must be the netmask configured on the third-party VPN endpoint Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

94 Supported Third-Party VPN Endpoints § Third-party endpoints that support GRE over IPSec are supported as a BOVPN virtual interface endpoint § Supported third-party endpoints include: • Cisco • Fortinet • Juniper • Checkpoint Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

95 Non-Supported Third-Party VPN Endpoints § Third-party endpoints that do not support GRE over IPSec are not supported as a BOVPN virtual interface endpoint § Non-supported third-party endpoints include: • Dell Sonic. WALL • Palo Alto Networks • Amazon AWS • Microsoft Azure Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

96 Other Enhancements Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

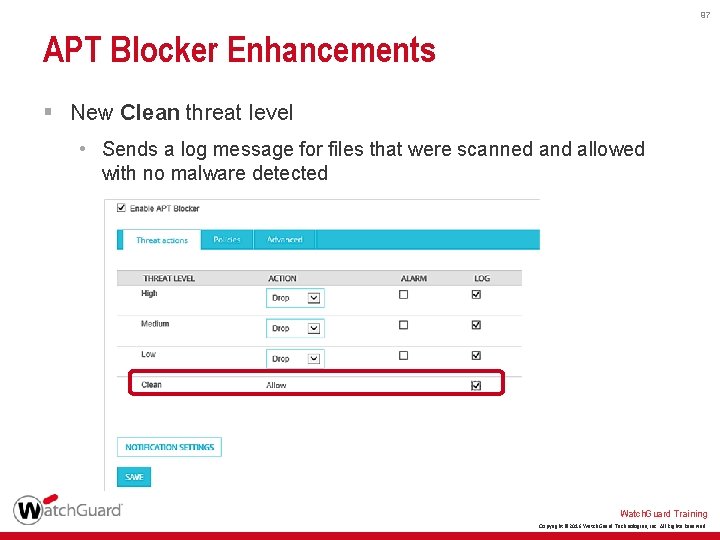
97 APT Blocker Enhancements § New Clean threat level • Sends a log message for files that were scanned and allowed with no malware detected Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

98 APT Blocker Enhancements § Apple Mac application file support • Mac executable files (. app files) can now be sent to the Lastline cloud server for analysis § New compressed file support • RAR and 7 z files can now be decompressed Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

99 Strip Documents with Macros — SMTP Proxy § With the SMTP Proxy, you can now strip Microsoft Office document attachments if they contain VBScript macros § Macros in Office documents have become a popular way for malicious malware, such as ransomware, to spread into a network § This rule type only applies to VBScript type macros in documents, not for macro-embedded document files Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

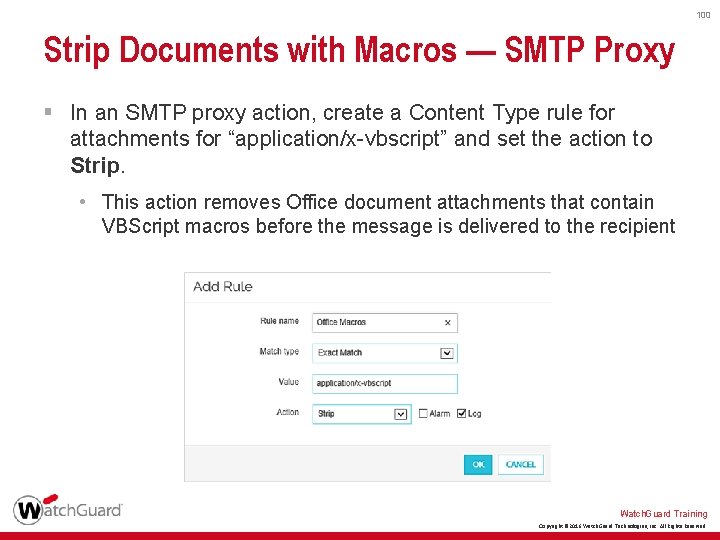
100 Strip Documents with Macros — SMTP Proxy § In an SMTP proxy action, create a Content Type rule for attachments for “application/x-vbscript” and set the action to Strip. • This action removes Office document attachments that contain VBScript macros before the message is delivered to the recipient Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

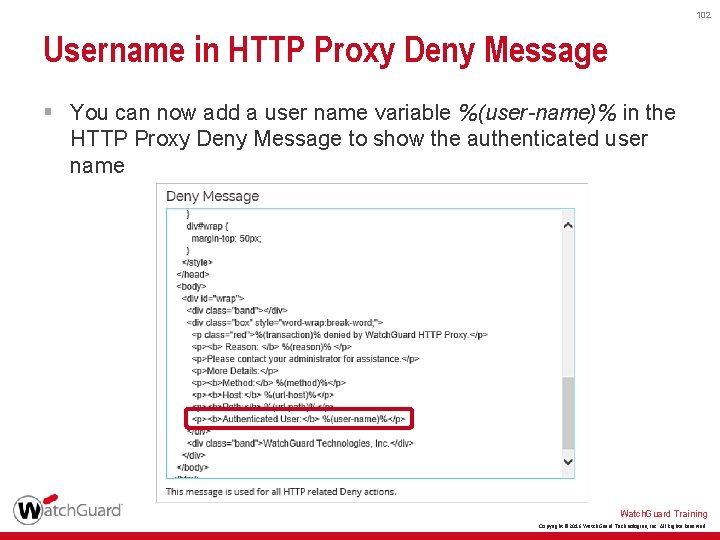
101 Self-Signed Certificates — SMTP with TLS § You can now use third-party self-signed certificates when you enable deep inspection of SMTP with TLS encryption § Allows users to import self-signed certificates from other devices, such as Watch. Guard XCS or mail servers Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

102 Username in HTTP Proxy Deny Message § You can now add a user name variable %(user-name)% in the HTTP Proxy Deny Message to show the authenticated user name Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

103 Gateway Wireless Controller Enhancements § Watch. Guard AP Device Automatic Deployment • Add an unpaired AP device to the network and have it configured automatically by the Gateway Wireless Controller (GWC) – Configure specific SSIDs for automatic deployment – When an unpaired AP device is connected to the network, it is automatically configured by the GWC with the auto-deployment SSID settings (security encryption and other SSID settings) – All other AP device settings such as radio settings are set to the defaults Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

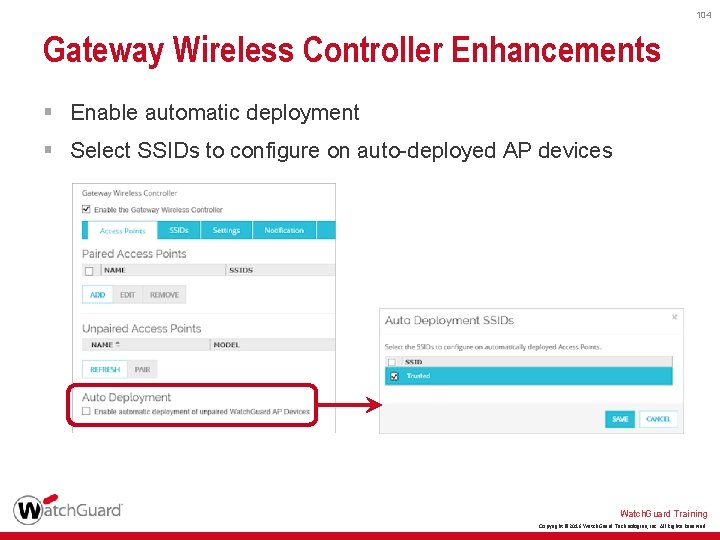
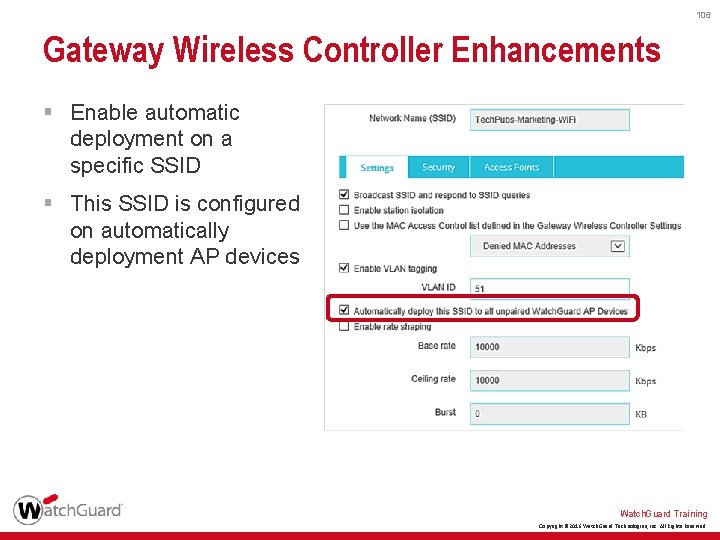
104 Gateway Wireless Controller Enhancements § Enable automatic deployment § Select SSIDs to configure on auto-deployed AP devices Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

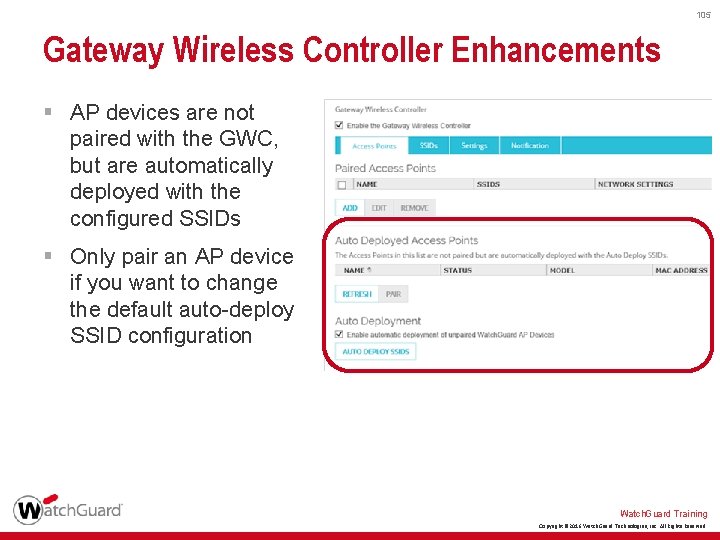
105 Gateway Wireless Controller Enhancements § AP devices are not paired with the GWC, but are automatically deployed with the configured SSIDs § Only pair an AP device if you want to change the default auto-deploy SSID configuration Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

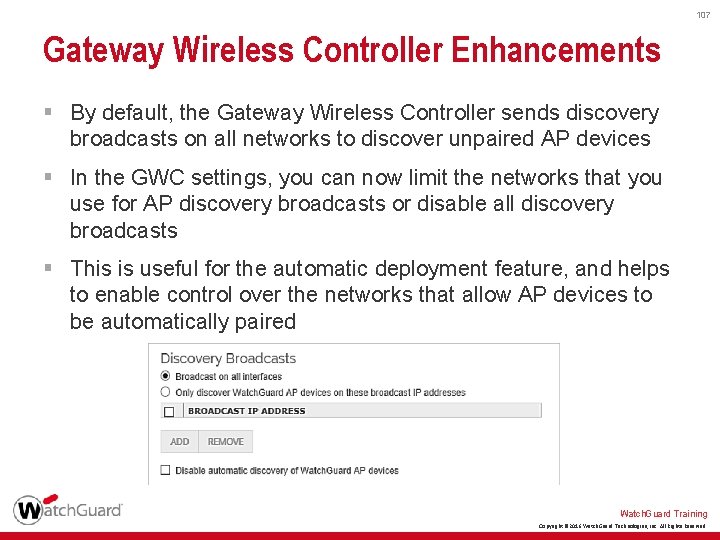
106 Gateway Wireless Controller Enhancements § Enable automatic deployment on a specific SSID § This SSID is configured on automatically deployment AP devices Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

107 Gateway Wireless Controller Enhancements § By default, the Gateway Wireless Controller sends discovery broadcasts on all networks to discover unpaired AP devices § In the GWC settings, you can now limit the networks that you use for AP discovery broadcasts or disable all discovery broadcasts § This is useful for the automatic deployment feature, and helps to enable control over the networks that allow AP devices to be automatically paired Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

108 Gateway Wireless Controller Enhancements § Gateway Wireless Controllers scalability improvements • A single GWC instance can now manage a much larger number of AP devices § Gateway Wireless Controller now supported in Firebox drop-in mode § AP support for RADIUS SSO accounting § Wireless client monitoring page includes PHY mode to indicate specific wireless modes, which includes b, g, a, n, n 40, ac 80, etc. Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

109 Improved Fire. Cluster Upgrade Process § The cluster manages the upgrade of both members • The cluster master uploads the Fireware OS upgrade file and manages the upgrades of both members § Why this change? • Enables upgrade of both cluster members from Fireware Web UI • Improves remote Fire. Cluster upgrade – Previously, for Policy Manager to remotely upgrade a Fire. Cluster, each cluster member was required to have a dedicated external IP address assigned as the management IP address – When you upgrade a Fire. Cluster from Fireware OS v 11. 11 or higher, external cluster management IP addresses are not required Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

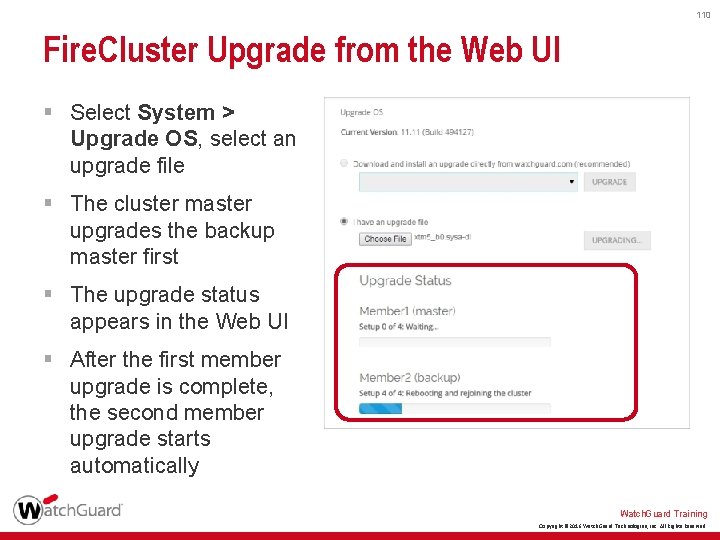
110 Fire. Cluster Upgrade from the Web UI § Select System > Upgrade OS, select an upgrade file § The cluster master upgrades the backup master first § The upgrade status appears in the Web UI § After the first member upgrade is complete, the second member upgrade starts automatically Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

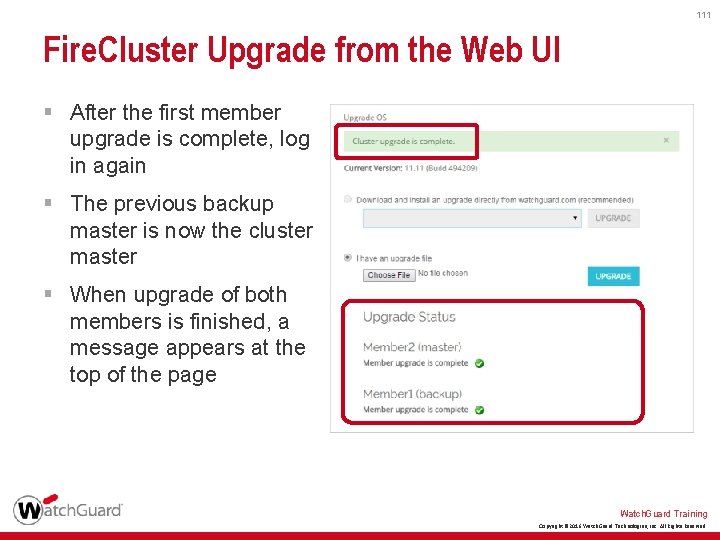
111 Fire. Cluster Upgrade from the Web UI § After the first member upgrade is complete, log in again § The previous backup master is now the cluster master § When upgrade of both members is finished, a message appears at the top of the page Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

112 Fire. Cluster Upgrade from Policy Manager § To start a Fire. Cluster upgrade select File > Upgrade § For upgrades from Fireware OS v 11. 11 or higher, the upgrade method Policy Manager uses depends on the IP address you connect to when you do the upgrade: • To use the new method, connect to an interface IP address – Policy Manager uploads the OS upgrade to the cluster master – The cluster master sends the OS upgrade file to the backup master and automatically coordinates the upgrade of both cluster members – Policy Manager does not connect to the Management IP addresses • To use the old method, connect to a Management IP address – Policy Manager connects individually to the Management IP addresses of each member to perform the upgrade Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

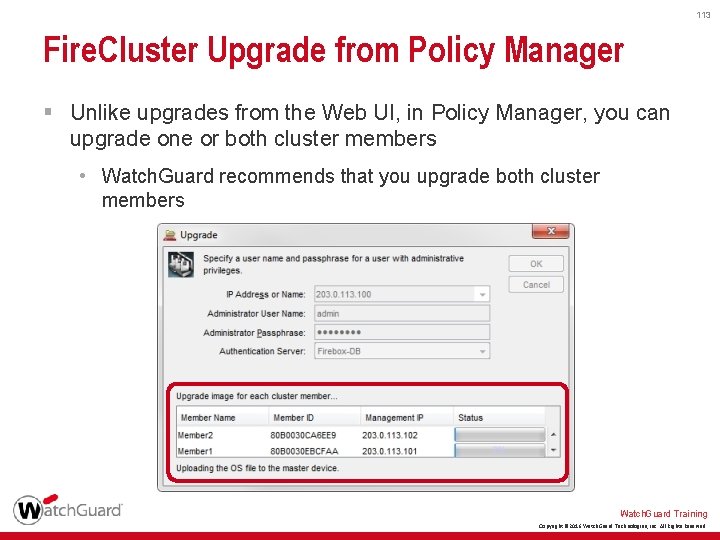
113 Fire. Cluster Upgrade from Policy Manager § Unlike upgrades from the Web UI, in Policy Manager, you can upgrade one or both cluster members • Watch. Guard recommends that you upgrade both cluster members Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

114 Fire. Cluster Upgrade from the CLI § You can also use the upgrade system CLI command to upgrade both members of a Fire. Cluster • After the first member upgrade is finished you must log in again to monitor the cluster upgrade status • After you log in again, to see the status of the cluster upgrade use the show upgrade status command Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

115 Loopback Interface § You can now enable a Loopback interface • The Loopback interface is a virtual interface for dynamic routing (RIP, OSPF, BGP) to multiple ISPs • Supported in Mixed Routing Mode only • Supported for both active/active or active/passive Fire. Cluster § Limitations • You cannot use the Loopback interface IP address or secondary IP address as a physical/virtual interface, local gateway IP address of a BOVPN or BOVPN virtual interface, or the route to IP address of a network route Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

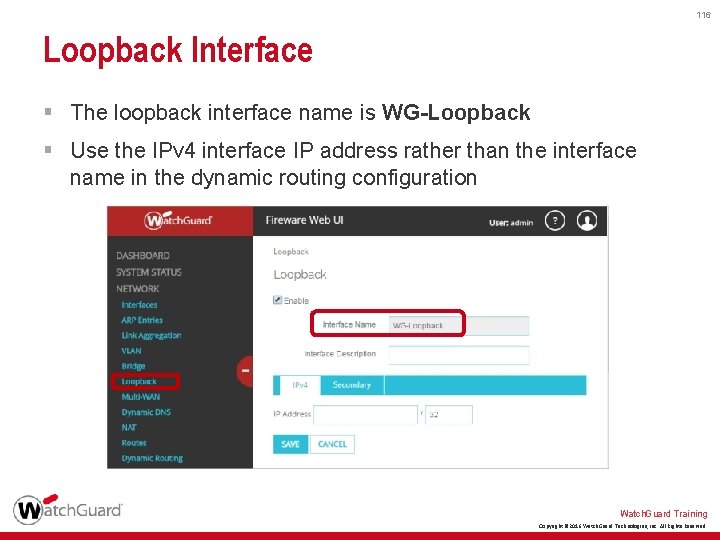
116 Loopback Interface § The loopback interface name is WG-Loopback § Use the IPv 4 interface IP address rather than the interface name in the dynamic routing configuration Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

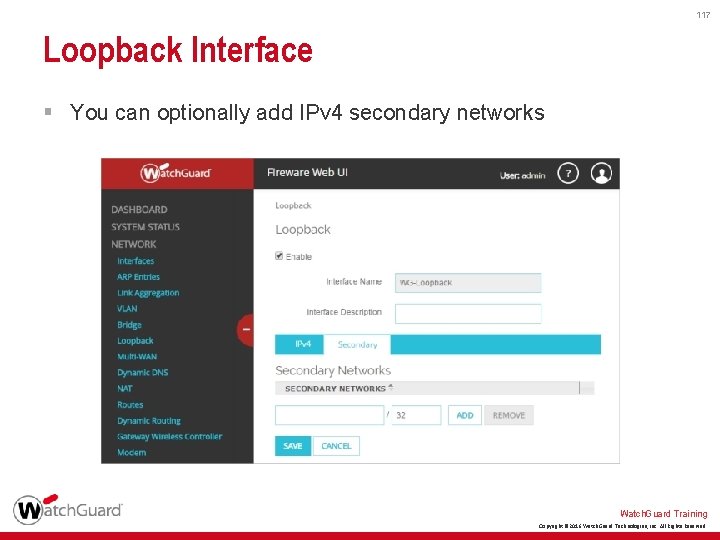
117 Loopback Interface § You can optionally add IPv 4 secondary networks Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

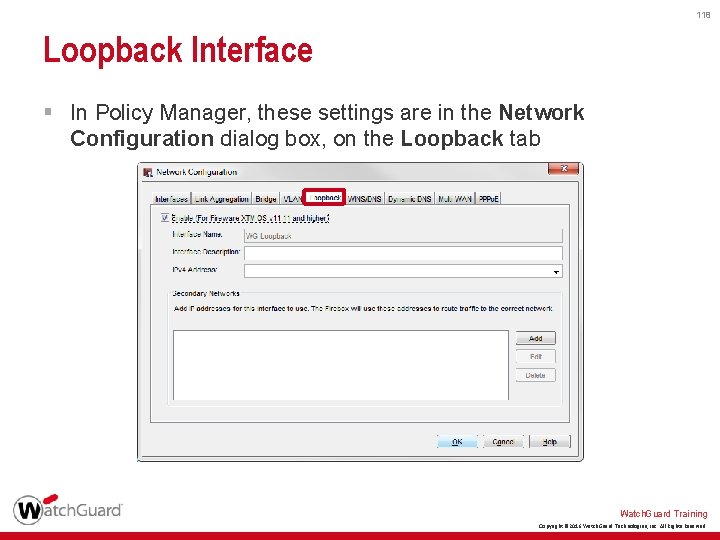
118 Loopback Interface § In Policy Manager, these settings are in the Network Configuration dialog box, on the Loopback tab Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

119 32 -bit BGP AS Number Support § Added support for 32 -bit BGP Autonomous System numbers Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

Thank You! Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved

Watch. Guard Training Copyright © 2016 Watch. Guard Technologies, Inc. All Rights Reserved