What They Need When They Need It Implementing



























- Slides: 47

What They Need When They Need It: Implementing a Statewide System for Sharing Library Resources Copyright Stephen Miller, David Kennedy, Uche Enwesi, and Jamie Bush, 2007. This work is the intellectual property of the authors. Permission is granted for this material to be shared for noncommercial, educational purposes, provided that this copyright statement appears on the reproduced materials and notice is given that the copying is by permission of the authors. To disseminate otherwise or to republish requires written permission from the authors.

What They Need When They Need It: Implementing a Statewide System for Sharing Library Resources Stephen Miller, David Kennedy, Uche Enwesi, and Jamie Bush EDUCAUSE Mid-Atlantic Regional Conference, January 18, 2007

Panelists • Stephen Miller – Associate Director for Information & Library Services, University of Maryland University College (UMUC) • David Kennedy, Programmer, USMAI Information Technology Division (ITD) • Uche Enwesi, LAN Coordinator, USMAI Information Technology Division (ITD) • Jamie Bush – Integrated Library System Manager, USMAI Information Technology Division (ITD)

Overview of Talk • • • Intro to USMAI Library Consortium Resource sharing in libraries Background of our project Infrastructure development and testing Implementation process

USMAI Library Consortium • University System of Maryland Affiliated Institutions (USMAI) – 16 Libraries: § 14 University System of Maryland Libraries § St. Mary’s College of Maryland Morgan State University • Serves over 140, 000 students in Maryland beyond

USMAI Institutions USMAI

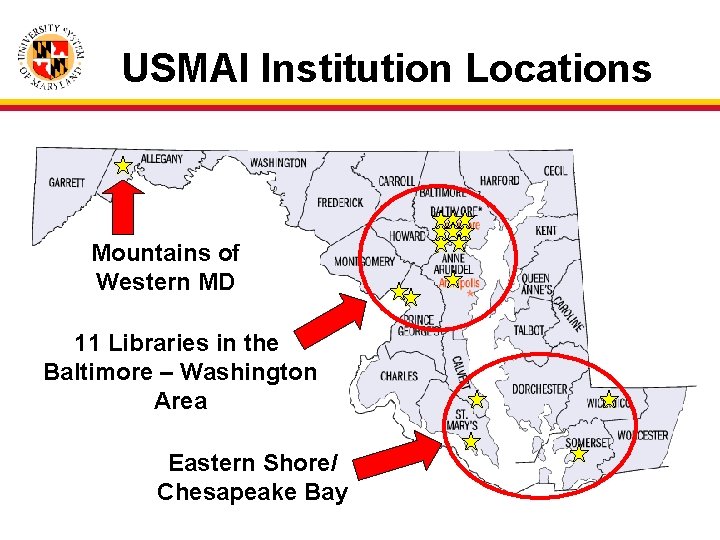
USMAI Institution Locations Mountains of Western MD 11 Libraries in the Baltimore – Washington Area Eastern Shore/ Chesapeake Bay

USMAI Library Consortium • • Founded in the late 1990 s Shared Integrated Library System Request/pickup services Metasearching and cross-linking capabilities • Shared Interlibrary Loan (ILL) platform

Resource Sharing in Libraries • Libraries have a long history of sharing • Shared catalog and circulation • Interlibrary Loan (ILL) – ILLiad § Leading ILL application § Developed by Atlas Systems § Supported by OCLC

About the Project • As of 2005, 8 of the 16 USMAI Libraries had purchased ILLiad • Opportunity to create level playing field for the entire USMAI consortium • Integrated electronic article delivery services would allow libraries within the consortium to share materials digitally

USMAI ILLiad Sites Standalone Sites Shared Sites • Towson University • University of Baltimore Law Library • UM Health Sciences and Human Services Library • UM Baltimore County • UM College Park • UM Law Library • UM University College • Bowie State University • Center for Environmental Science • Coppin State University • Frostburg State University • Morgan State University • Salisbury University • St. Mary’s College of Maryland • UM Eastern Shore

Why ILLiad for USMAI? • Desktop article delivery • Odyssey – Allows for inter-campus article delivery • Patron self-service – – 24/7 access Request tracking Fewer calls to ILL office Request history Confidentiality: Can break patron—request links • Compatible with metasearching and cross-linking products used by USMAI • Auto-generated patron emails

Why ILLiad for USMAI? – pt. 2 • Web-based management statistics • Simple one-time patron registration • Staff efficiencies can handle increases in request volume • Works with major ILL service providers • Can handle billing processes

The Project Plan • ILLiad implementation for 8 libraries without ILLiad – – – Centralized training Centralized ITD support and OCLC contact Shared, locally hosted server at ITD Centralized financial support Standard look and feel/implementation Authentication against existing library patron database used by all campuses • 8 sites already on ILLiad would maintain their own separate installations for now

Implementation highlights • • Shared Installation Authentication/Authorization Networking Actual Implementation

Shared Installation • First shared installation of ILLiad • Separate settings, templates, web pages, etc. per institution

Authentication/Authorization Definitions • Authentication – “Who are you? ” • Authorization – “What are you allowed to do? ”

Authentication/Authorization Shibboleth at USMAI • Provides authentication across library applications – Single login – Supplies attributes

Authentication/Authorization ILLiad Needs • External authentication • Reliable user attributes • Interface customized by attribute (borrower type, expiration date)

Authentication/Authorization External authentication • ILLiad as Shibboleth service provider • Shibboleth provides authentication • ILLiad aware of one user attribute, user id

Authentication/Authorization Reliable user attributes • Autopopulate user registration form • Borrower status is hidden (immutable) • Implemented with combination of Javascript and JScript

Authentication/Authorization Customize by attribute • Borrower type • Expiration date

Challenges/Successes • Challenges – Shibboleth provides authentication, not authorization • Successes – Customer support (Atlas – Genie Powell)

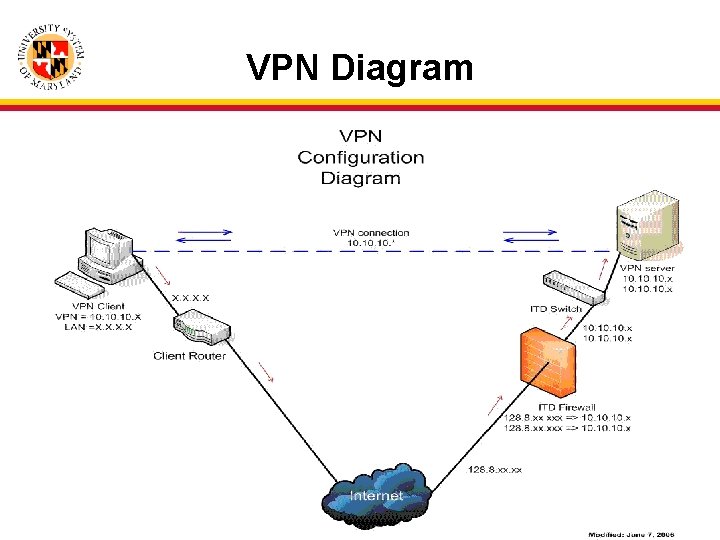
Network Implementation • File Sharing • VPN • Successes and challenges

File Sharing • File Share or VPN? • Options: – Open necessary ports on our campus border – Ask other campuses to open needed ports on their campus border – Create VPN for independent solution

File Sharing • Open needed ports on our campus border • Outcome: – Needed port blocked on internet provider’s border

VPN Requirements • Ease of setup to avoid user having system administrator account – Simple Plug and Play • Easy deployment and installation – Able to create packages with preconfigured server names and settings • Secured

VPN • • VPN Requirements (cont’d) Avoid campus network security and bypass closed ports on the border of each campus Tunnel to a private network over a public network Avoid dependency on campus networks Ease of installation

VPN Options • Cisco VPN – Through PIX 525 firewall • Microsoft VPN – Already built in Microsoft Windows Server OS, VPN client software in Microsoft Windows Desktop OS

VPN • Microsoft VPN – Ease of Setup – Simple Plug and Play – Configure on the fly without having to redeploy new packages – One password for VPN that takes care of file sharing

VPN Diagram

Challenges/Successes • Challenges – Configuring VPN to work the way we envisioned it – Campuses that locked down their network • Successes – Had good team members that tested VPN solution for every possible problem before we released it

Hardware we Used • Cisco PIX 525 Fire. Wall – Used for firewall protection and also used for IP address translations • Dell Poweredge Server – Windows 2003 Server (Live and Test Server) – Microsoft VPN Software • Cisco Switch

ILLiad Implementation • • • Implementation team Implementation timeline Site visit steps Supporting shared applications Successes and challenges

Implementation Team • • Systems Librarian Programmer Network Administrator Trainers from USMAI ILLiad standalone sites • ILL Staff at shared sites

Implementation Plan - Timeline • Original plan was Feb - Aug 2006 • February 2006 – Vendor training • March 2006 – Networking configuration – File Sharing VS VPN – Test server setup and configuration • April 2006 – Scheduling of sites (long range) – Remote site surveys distributed

Implementation Plan - Timeline • May 2006 – Test Client installed at 1 st site – Web User Interface setup in test for 1 st site(global look and feel, minor local customization) – Production environment setup – Authentication/Shibboleth work with vendor – Final scheduling of 1 st site • June 2006 – 1 st site in production (St. Mary’s College) – Troubleshooting

Implementation Plan - Timeline • July 2006 – Test environment becomes development – 2 nd and 3 rd sites brought up in production • August 2006 – 4 th and 5 th sites brought up in production • Sept/October 2006 – Troubleshooting Odyssey

Implementation Plan - Timeline • Nov 2006 – 6 th and 7 th sites brought up in production • Spring 2007 – Final site brought up – ILLiad version upgrade – Resolve outstanding issues – Web Interface updates

Implementation Steps • Conducted one day site visit • Pre-visit planning – Survey conducted – Installation of applications by local staff – Pre-configuration of client based on survey – Web environment configuration – Coordinate availability of IT staff during the site visit

Implementation Steps • Site visit steps: – Verify installations/resolve problems – Last minute configuration (information not included on survey) – Create local staff accounts – Trainers work through local client customization (serves as intro into application)

Implementation Steps • Site visit steps: – Trainers work with local ILL staff creating test transactions, lending and borrowing – ITD Staff fix/resolve problems as appropriate – Test all functionality (email, print, delivery)

USMAI Technical Support • Diversity in experience and resources – Have's vs have not's – Technology and human resources • Determining factors – Organization structure of library – Size of ILL staff – Internal and external IT support

USMAI Technical Support • ITD support of ILLiad – Supporting library system for more than 20 years – Established communication processes and resources – Support framework easily implemented

Challenges/Successes • Challenges – Supporting Odyssey § Networking/email/smtp – Lack of functional experience in ITD • Successes – ILLiad and USMAI resource sharing – Working with local ILL/IT staff and USMAI Trainers – Learning ILLiad

What They Need When They Need It: Implementing a Statewide System for Sharing Library Resources Questions? Stephen Miller, David Kennedy, Uche Enwesi, and Jamie Bush EDUCAUSE Mid-Atlantic Regional Conference, January 18, 2007

Contacts Jamie Bush – USMAI/ITD gjbush@umd. edu http: //usmai. umd. edu/itd/ Stephen Miller - UMUC smiller@umuc. edu http: //www. umuc. edu/library David Kennedy – USMAI/ITD davekenn@umd. edu http: //usmai. umd. edu/itd/ USMAI Website: http: //usmai. umd. edu/ USMAI RSTG Website: http: //usmai. umd. edu/resshare/ Uche Enwesi – USMAI/ITD uenwesi@umd. edu http: //usmai. umd. edu/itd/