What Keeps a CISO Awake at Night Presenters



















- Slides: 26

What Keeps a CISO Awake at Night? Presenters: Karen Painter Randall Frank Tranor Robert Babin Sr. ' Francois Bodhuin Lou Dignam Michael Chirico www. connellfoley. com

According to the 2017 Ponemon Institute Study, What Is the Cost of a Data Breach in the Healthcare Industry? A. B. C. D. $2. 2 Billion $3. 6 Billion $4. 0 Billion $6. 2 Billion

According to the 2017 Ponemon Institute Study, What Is the Cost of a Data Breach in the Healthcare Industry? • ANSWER D - $6. 2 Billion – Healthcare data breaches cost $380 per record, or 2. 5 times more than the global average across industries of $141.

Healthcare Data Breaches in Q 1: 2018 • The first three months of 2018 have seen 77 healthcare data breaches reported to the Department of Health and Human Services’ Office for Civil Rights (OCR). • Those breaches have impacted more than one million patients and health plan members – Almost twice the number of individuals that were impacted by healthcare data breaches in Q 4, 2017. – Between January 1 and March 31, 2018, 1, 073, 766 individuals had their PHI exposed, viewed, or stolen compared to 520, 141 individuals in Q 4, 2017.

Healthcare Data Breaches are Costly… • When a healthcare organization experiences a breach, forensics costs added up to $610, 000. • Breach notification costs $560, 000 on average. • Costs affiliated with lawsuits average $880, 000. • For each data breach, healthcare organizations average $3. 7 million in lost revenue. • Healthcare organizations average $500, 000 in lost brand value after a breach. • The average HIPAA settlement fine is approximately $1. 1 million. • Post-breach cleanup costs average $440, 000.

What Are the Most Common Types of Cyber. Attacks? • Although there are many different ways for a data breach to occur, the following are the five most common types of cyber-attacks: 1. 2. 3. 4. 5. Ransomware Unauthorized Access Social Engineering Theft of Digital Assets Hacktivists

Ransomware • The healthcare industry is taking the lion’s share of ransomware attacks, according to a threat report released May 1, 2018 by endpoint security firm Cylance.

Ransomware • 400, 000 new strains of ransomware detected daily making the attacks more sophisticated and harder to respond to. – According to Cylance, the top ten malware families are Wanna. Cry, Upatre, Cerber, Emotet, Locky, Petya, Ramnit, Fareit, Poly. Ransom, and Terdot/Zloader. • The ransomware attack against Hollywood Presbyterian Medical Center in February 2016 was a particularly harsh healthcare attack that resulted in the hospital paying the $17, 000 in Bitcoin.

Social Engineering (Spearphishing Attacks) • 91% of targeted cyber-attacks begin with a spearphishing email. – Users are still clicking on too many links, putting the organization at risk • Open dialogue and recognition of cybersecurity threats represent a significant shift in our collective awareness of cyber-risks. • Education and security awareness training is imperative!

CISO Challenge 1: Preventing a Cyber-Attack • Bad News: – According to most cybersecurity experts, “It is not a matter of if, but when…” when dealing with a cyber-attack. • Good News: – There are steps to take to limit your exposure and mitigate your legal, operational and reputational damages.

CISO Challenge 1: Preventing a Cyber-Attack

CISO Challenge 2: Where Does Your PHI/PII Data Reside and Who Is Using It? • Cloud computing is generally based upon three separate and distinct architectures that matter when considering the security of the data sitting in the particular cloud environment: 1. Infrastructure as a Service (Iaa. S) 2. Platform as a Service (Paa. S) 3. Software as a Service (Saa. S)

CISO Challenge 2: Where Does Your PHI/PII Data Reside and Who Is Using It?

CISO Challenge 3: Concerns About the Internet of Things

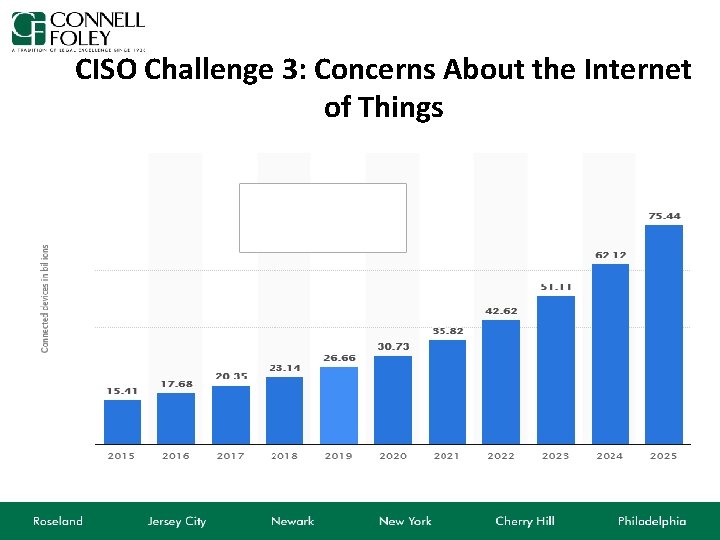
CISO Challenge 3: Concerns About the Internet of Things • It is estimated that the global healthcare sector will pour approx. $410 billion into Io. T devices, services, and software in 2022, according to a report from the research firm Grand View Research. – GE partnered with a hospital in New York to connect and track hospital beds using sensors. These sensors enabled hospital operators to tell when a bed was free and helped reduce emergency room wait times by as much as four hours. – Philips Healthcare recently rolled out an Io. T solution called e-Alert, which is a hardware/software solution, that virtually monitors the health of its machines so that they never suffer an outage.

CISO Challenge 3: Concerns About the Internet of Things • Benefits to Using Io. T – Improved treatment outcomes access to real-time information will in turn allow caregivers to make better-informed decisions and propose treatment strategies. – Improved management of drugs and diseases having an accurate collection of data through the use of Io. T medical alert systems will guarantee a minimization of errors in treatment and disease management overall. – Enhanced experience of patients greater efficiency in care by improving accurate diagnoses, proactively treating illnesses, and allowing physicians to timely intervene are all ways that Io. T can make for better patient experiences.

CISO Challenge 3: Concerns About the Internet of Things • In a recent alert the U. S. Department of Homeland Security highlighted one weakness affecting approximately 300 medical devices, including drug infusion pumps, ventilators and external defibrillators. • A range of medical devices run on standard software such as Windows XP and are vulnerable to common viruses that plague home and office computers.

CISO Challenge 3: Concerns About the Internet of Things

CISO Challenge 4: Third Party Vendor Management • The growing use of external service providers presents new and difficult challenges for organizations, especially in the area of information system security. • Relationships with external service providers can be established in a variety of ways, for example, through joint ventures, business partnerships, outsourcing arrangements (i. e. , through contracts, interagency agreements, lines of business arrangements, service-level agreements), licensing agreements, and/or supply chain exchanges.

CISO Challenge 4: Third Party Vendor Management

CISO Challenge 5: Preparing the Board for Changes in Regulations • Many CISOs agreed that while they used to have to spell out security to board members, the situation is improving. • The number of breaches that have been in the news recently has helped, especially when asking for budget.

CISO Challenge 5: Preparing the Board for Changes in Regulations • However, there is still more to be done in terms of building effective C-level relationships. • Security needs to be part of the business, not just a cog in the IT wheel. • Security is more than an enabler now; it is a requirement. – Ex) The General Data Protection Regulation (“GDPR”) is a new set of rules designed to give EU citizens more control over their personal data. – Under the terms of GDPR, not only will organizations have to ensure that personal data is gathered legally and under strict conditions, but those who collect and manage it will be obliged to protect it from misuse and exploitation, as well as to respect the rights of data owners - or face significant penalties for not doing so.

CISO Challenge 5: Preparing the Board for Changes in Regulations

Cybersecurity Trends for 2018 • Expect zero regulator tolerance when GDPR comes into force. • Criminal will continue to innovate to find vulnerabilities. • Governments will prioritize collaboration and intelligence sharing. • The creation of a new cybersecurity model. • Expect to see more automation of controls and compliance. • Endemic poor security in the internet of things will not be solved in 2018. • State-directed cyber threats continue to evolve and intensify.

Final Thoughts on Cybersecurity • “If you’re not doing scans and penetration tests, then just know that someone else is. And they don’t work for you. ” ‒ George Grachis, Senior Consultant, Maxis 360 - 2016
