WHAT IS INFORMATION SECURITY Information security consists of


- Slides: 8

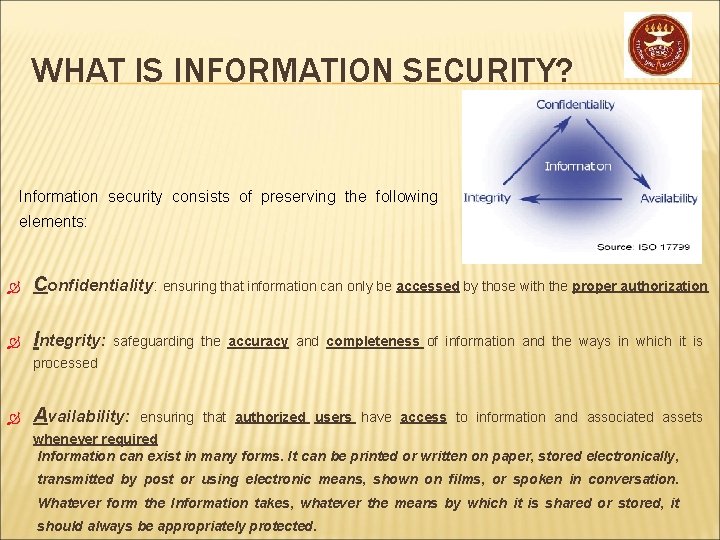
WHAT IS INFORMATION SECURITY? Information security consists of preserving the following elements: Confidentiality: ensuring that information can only be accessed by those with the proper authorization Integrity: safeguarding the accuracy and completeness of information and the ways in which it is processed Availability: ensuring that authorized users have access to information and associated assets whenever required Information can exist in many forms. It can be printed or written on paper, stored electronically, transmitted by post or using electronic means, shown on films, or spoken in conversation. Whatever form the Information takes, whatever the means by which it is shared or stored, it should always be appropriately protected.

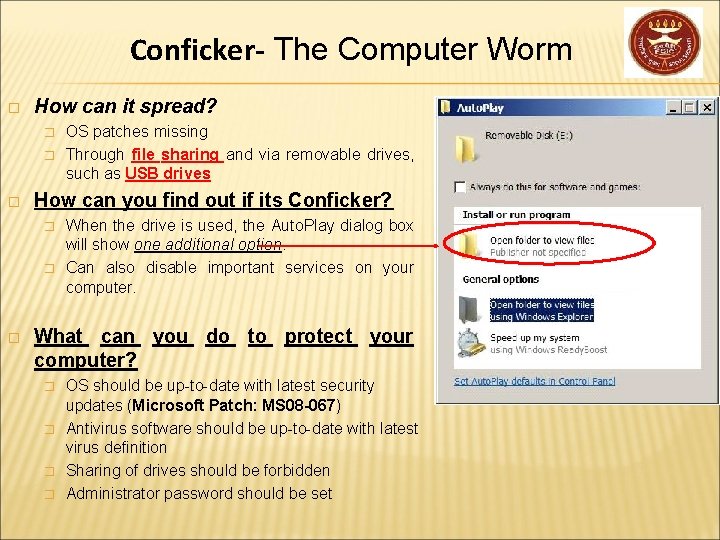
Conficker- The Computer Worm � How can it spread? � � � How can you find out if its Conficker? � � � OS patches missing Through file sharing and via removable drives, such as USB drives When the drive is used, the Auto. Play dialog box will show one additional option. Can also disable important services on your computer. What can you do to protect your computer? � � OS should be up-to-date with latest security updates (Microsoft Patch: MS 08 -067) Antivirus software should be up-to-date with latest virus definition Sharing of drives should be forbidden Administrator password should be set

Always lock your PC before you leave your desk • Press CTRL+ALT+DEL Shut down your PC and monitor before leaving from work everyday Do not share your password with anyone, not even your colleague Do not download any unauthorized software on your PC Do not store personal data on your PC

Do’s Don’ts • Always lock your PC before you leave your desk (Press CTRL+ALT+DEL) • Shut down your PC and monitor before leaving from work everyday • Do not share your password with anyone, not even your colleague • Do not download any unauthorized software on your PC • Do not store personal data on your PC

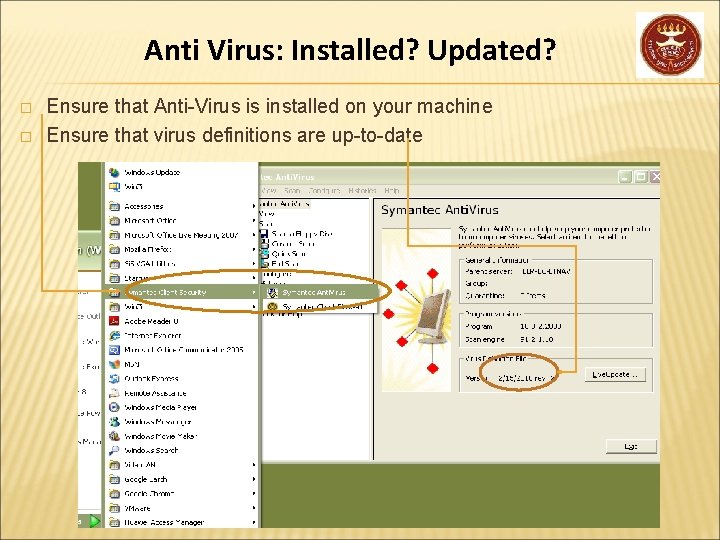
Anti Virus: Installed? Updated? � � Ensure that Anti-Virus is installed on your machine Ensure that virus definitions are up-to-date

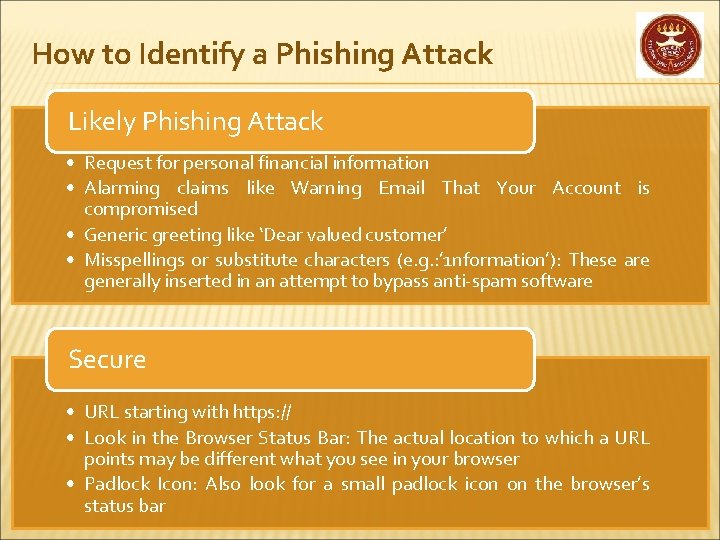
How to Identify a Phishing Attack Likely Phishing Attack • Request for personal financial information • Alarming claims like Warning Email That Your Account is compromised • Generic greeting like ‘Dear valued customer’ • Misspellings or substitute characters (e. g. : ’ 1 nformati 0 n’): These are generally inserted in an attempt to bypass anti-spam software Secure • URL starting with https: // • Look in the Browser Status Bar: The actual location to which a URL points may be different what you see in your browser • Padlock Icon: Also look for a small padlock icon on the browser’s status bar

You are responsible for…. . � Print outs that lie unattended………… � � Do not leave any print outs lying unattended Collect the prints immediately Shred/ Discard/Tear-off the pages which are not of any use Take print outs only if it is absolutely necessary

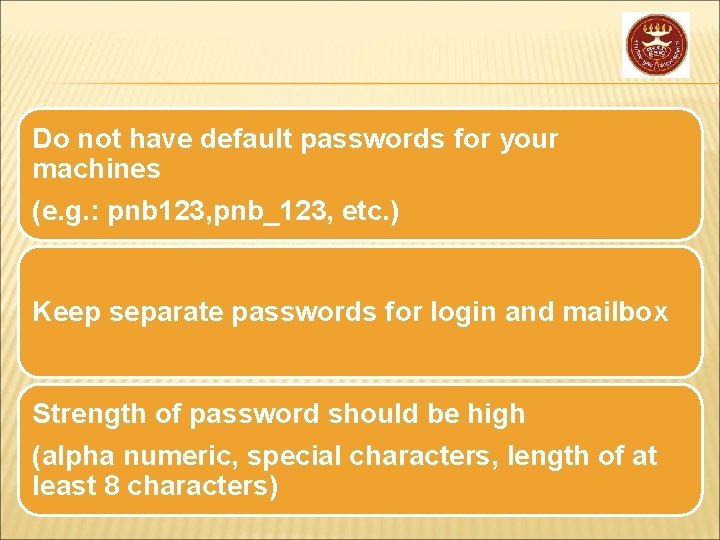
Do not have default passwords for your machines (e. g. : pnb 123, pnb_123, etc. ) Keep separate passwords for login and mailbox Strength of password should be high (alpha numeric, special characters, length of at least 8 characters)