What is Identity Theft and how can you














- Slides: 22

What is Identity Theft, and how can you protect yourself from it? Scams and Schemes

Lesson Objectives • understand what identity theft is and why it is important to guard against it. • learn to recognize strategies that scam artists use to access private information. • learn how to guard against phishing and identity theft.

Key Vocabulary scam: an attempt to trick someone, usually with the intention of stealing money or private information identity theft: a type of crime in which your private information is stolen and used for criminal activity vulnerable: in a position that makes it easier for you to be harmed or attacked phishing: when people send you phony emails, pop-up messages, social media messages, texts, calls, or links to fake websites in order to hook you into giving out your personal and financial information Scam and Flim-Flam: Has it happened to you?

What is Identity Theft? What is your identity, how can it be stolen?

Your Identity: �Full Name �Date and Location of Birth �Current and Previous Street Address �Home/Cell Number �Driver’s License/Passport/ Social Security Number �Bank/Credit Account Numbers �Username/Passwords

Identity Scams: � Identity thieves look for “clean” Social Security numbers that haven’t yet been used to get credit. They target teens and kids, who often have Social Security numbers that have no credit history yet. Identity thieves might sell or use these numbers, which would allow someone else to get a credit card or loan and build up debt � Being a victim of identity theft can ruin your financial future and your ability to obtain loans and purchase things. For example, it could affect your ability to get a student loan for college or a loan to buy a car.

Identity Scams: �If children use parents’ accounts and credit cards online, or fill out forms with parents’ information, they are sharing information that could potentially put parents’ identities at risk. �It can take months, even years, to recover your identity if it’s stolen. Cleaning up such a mess takes a lot of time and energy, and it can also be expensive.

How to Catch a Phish… How identity thieves try to get your information?

Activity: Spot a Scam FEATURES OF A PHISHING EMAIL: Need to “verify account information” Sense of urgency Spelling errors “Account is in trouble” Link in email or attachment Too good to be true Generic greeting Email address/website doesn’t match YOUR JOB: On the next 3 Slides find one or more feature of a phishing email Answers will appear after 30 seconds Compare answers Give yourself 1 point for each correct answer

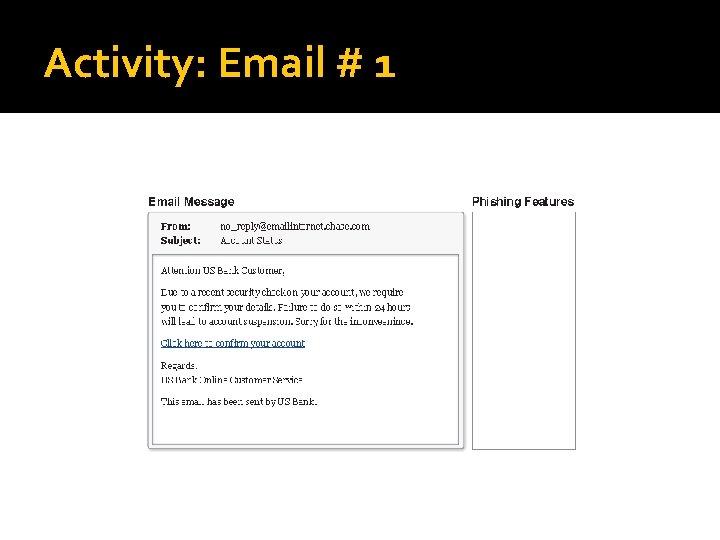
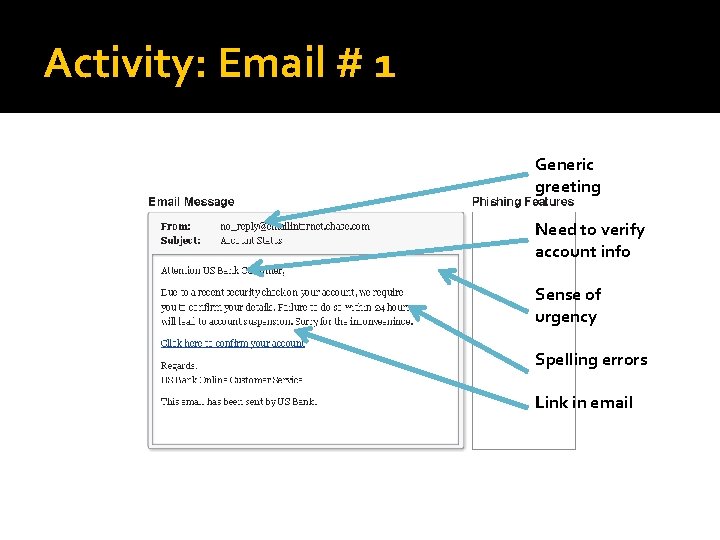
Activity: Email # 1

Activity: Email # 1 Generic greeting Need to verify account info Sense of urgency Spelling errors Link in email

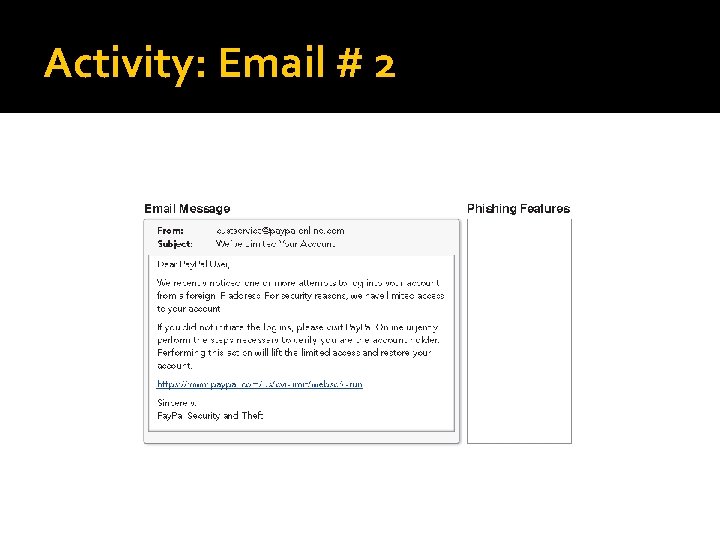
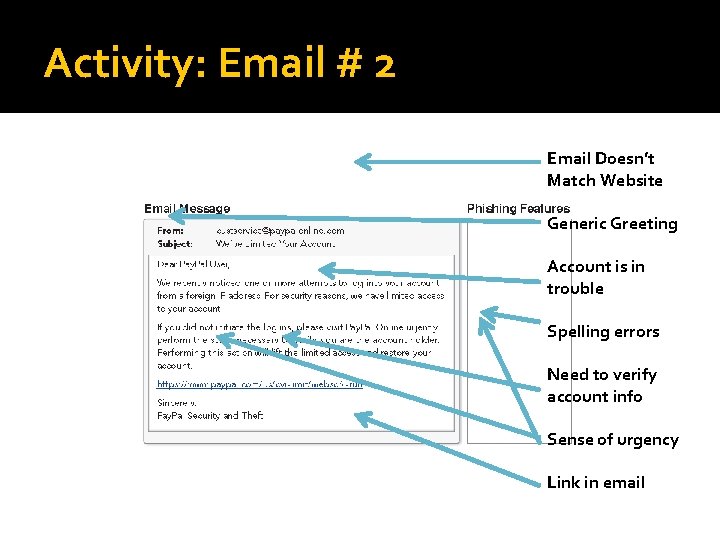
Activity: Email # 2

Activity: Email # 2 Email Doesn’t Match Website Generic Greeting Account is in trouble Spelling errors Need to verify account info Sense of urgency Link in email

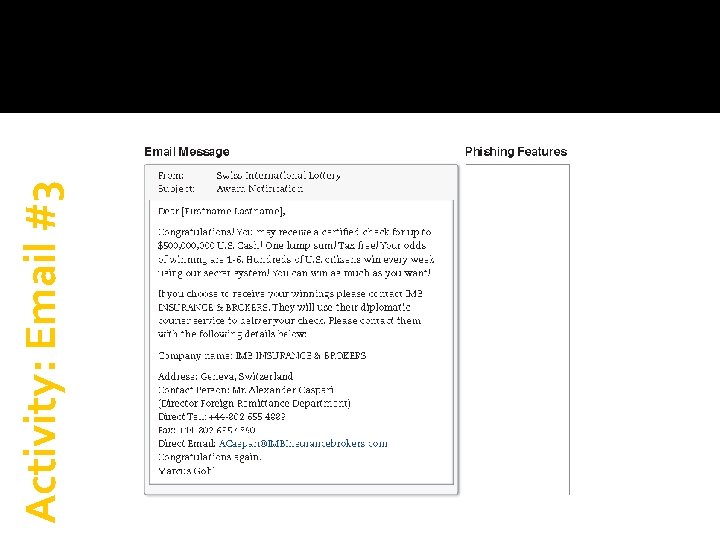
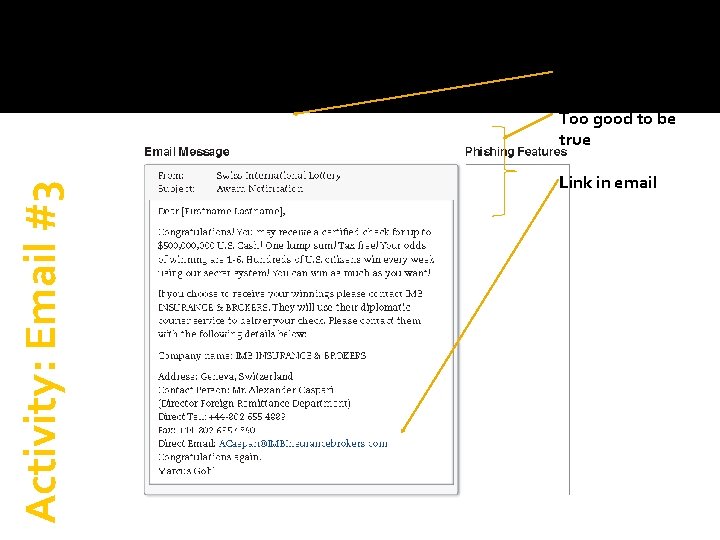
Activity: Email #3

Generic greeting Activity: Email #3 Too good to be true Link in email

Protect Yourself from Scams The next step…

How to be Scam-Free �Avoid opening emails/messages from strangers �Read all emails looking for signs of phishing �Do not click links or open attachments from spam or phishing emails �Don’t reply to spam/phishing emails �Report phishing or “mark as spam” �Find accurate phone numbers for your accounts and verify over the phone if you have questions (do not use the phone number from the email)

Think like a Phish… A final activity to help you avoid scams and schemes.

Ask yourself: �What kind of information do identity thieves look for? Why? �How do thieves try to get that information? �What can I do to avoid scams?

Now try it yourself: �Use 4 or more of the following features of phishing emails/scams and CREATE YOUR OWN phishing email �Now, share that email and see if someone else can spot the scam! (Do not send via email or prank anyone, use this email to teach someone what you have learned. )

Other Sites to Visit: �www. ftc. gov/idtheft - Federal Trade Commission ID Theft website �www. onguardonline. gov – additional security measures recommended by the government �www. ccis. ccsdtitle 1. org – view the other lessons we have for you!

Thank you! Please take the session evaluation survey. The title of this lesson is: Scams and Schemes Did you learn: • what identity theft is and why it is important to guard against it. • to recognize strategies that scam artists use to access your information. • how to guard against phishing and identity theft. Survey Website link: http: //www. surveymonkey. com/s/F 9 QJ 9 PM Participate in lessons on other topics at http: //CCIS. CCSDTitle 1. org Lesson Plan adapted from and used with permission from Common Sense Media @ http: //commonsensemedia. org