What is Cybersecurity Office of Information Technology Security

What is Cybersecurity Office of Information Technology Security & Compliance Think Security and Do Good Things! Elizabeth Cole-Walker (Information Security Specialist, Information Security Risk & Assurance)
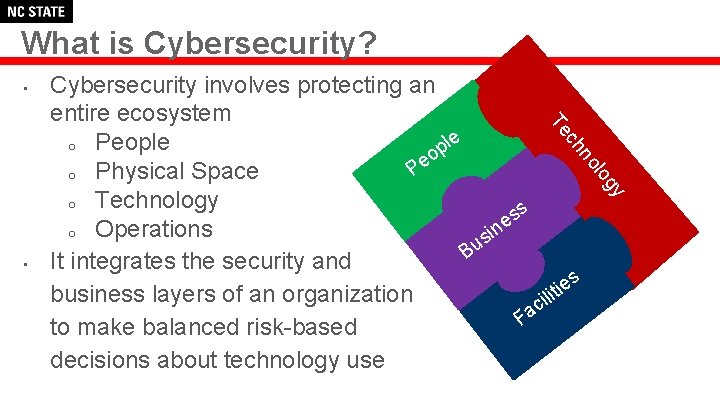
What is Cybersecurity? • gy • lo no ch Te Cybersecurity involves protecting an entire ecosystem le o People p o e P o Physical Space o Technology ss e o Operations in s u B It integrates the security and s e i t business layers of an organization ili c a F to make balanced risk-based decisions about technology use

Importance of People & Operations • • Data drives the business and people use the data Business must focus more on the processes and use of people A risk based approach, where people understand the role they play in security is vital for success Security controls need to be assessed against real risks and risk tolerance to meet mission

Security Career Tracks • • • Information Security – Less Technical/Non-Technical (i. e. , risk, assurance, policy, governance, or regulatory compliance, etc. ) Information Security – Technical (i. e. , security analyst, • architect, tester, engineer, or administrator, etc. ) • Network and Cloud Technologies • • • Hardware, Services, and Infrastructure IT Management and Strategy Storage and Data Web and Mobile Software Development and Business Analysist Training Auditing and Assessment

Functional Roles in Cybersecurity 1. Executive Management and Senior Leadership • • Visible advocate for cybersecurity program Promotes and demands accountability Promotes policy and governance Directs assessments

Functional Roles in Cybersecurity 2. Human Resources • • Knows the people and types of data used Key in identifying insider threat indications Develops and implements policy and procedures Understands many laws and regulations

Functional Roles in Cybersecurity 3. Legal Counsel • • 4. Reviews/advises on policy (i. e. , data collection, data use, cyber investigations, etc. ) Supports compliance with regulations, rules, laws Finance • • Knowledge of financial assets, data use Knowledge of risk and impacts

Functional Roles in Cybersecurity 5. Information Technology • • Builds operates and maintains data collection solutions Represents expertise in computer systems engineering, system and database administration, interface design, and algorithms development for using data Understanding of software and hardware and user interface Knowledge of operations that support business

Functional Roles in Cybersecurity 5. Security • • • Works with all elements of the organizations to secure assets (people, facilities, data, etc. ) Represents industrial, IT, information assurance, auditing, physical, personal, and operational security Training and awareness Logging, monitoring, investigations Understands the operational functions and people

Protection of Critical Assets • • Cybersecurity is really asset and risk management You can not protect what you don’t know you have. An asset can be “Tangible” (physical in nature or measurable) or “Intangible” (not physical in nature and is often difficult to determine a value) Requires documentation and continual review, testing, and improving

The Treat Landscape Nation States Organized Crime Hackers Espionage The lines are blurring They are all bad guys and email is the most likely attack method!
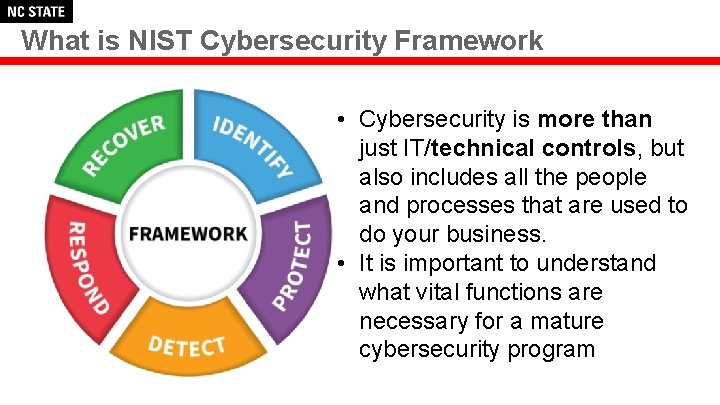
What is NIST Cybersecurity Framework • Cybersecurity is more than just IT/technical controls, but also includes all the people and processes that are used to do your business. • It is important to understand what vital functions are necessary for a mature cybersecurity program
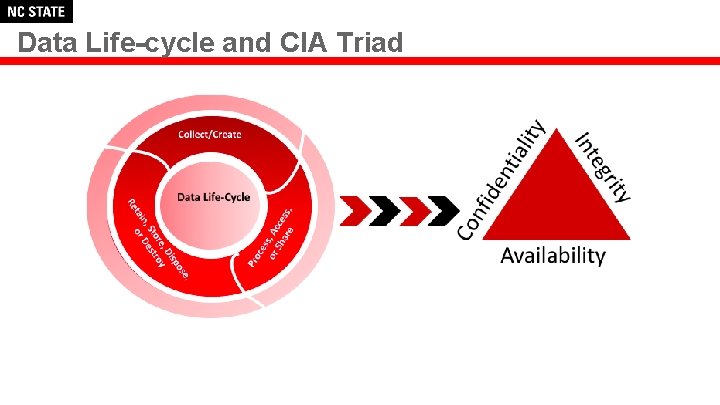
Data Life-cycle and CIA Triad

Risk Factors Strategic - Affects the ability to carry out goals and objectives Reputational - Affects reputation, public perception, political issues, etc. Financial - Effects loss of (or ability to acquire) assets, technology, etc. Operational - Effects ongoing management processes and procedures Compliance - Affects compliance with laws and regulations; student, faculty, staff & visitor safety; environmental issues; litigation; conflicts of interest; privacy; and so forth. Hazard - Affects ongoing operation of a business by man-made, natural or other negative events

Impact Scale • • NIST ranks impact as to how the company would be affected by an attack or unauthorized disclosure or loss of an asset. It is defined on a scale from Low, Moderate, and High Understanding the impact that loss or unauthorized disclosure has on an asset for each risk factor is key to developing a strategic cyber program
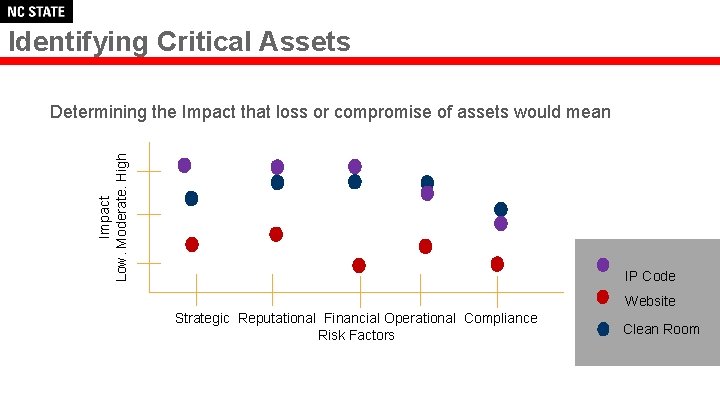
Identifying Critical Assets Impact Low. Moderate. High Determining the Impact that loss or compromise of assets would mean IP Code Website Strategic Reputational Financial Operational Compliance Risk Factors Clean Room

Cybersecurity Career References • • Comp. TIA IT Certification Roadmap Cyber Security Degrees & Careers – How to Work in Cyber Security Getting Started in Cybersecurity with a Non-Technical Background Which non-technical skills are most important to a career in security? IT careers for non-technical people ISACA Certification: IT Audit, Security, Governance and Risk NIST Cybersecurity Framework CIA Triad Model
- Slides: 17