What is Bit Locker and How Does It

What is Bit. Locker and How Does It Work? Steve Lamb IT Pro Evangelist, Microsoft Ltd http: //blogs. technet. com/steve_lamb mailto: //stephlam@microsoft. com

What is IT Pro Momentum? • A program to recruit early adopters • Provides you with free support and training • Share your story and influence the next wave of early adopters • Rewards you with a free Tech. Net Direct subscription

More information? For more information on the IT Pro Momentum Program or to nominate someone e-mail: Steve Lamb Stephen. lamb@microsoft. com

“Bit. Locker Drive Encryption provides stronger protection for data stored on your Windows Vista ™ systems – even when the system is in unauthorized hands or is running a different or attacking OS. Bit. Locker does this by utilizing full volume encryption; this prevents a thief who boots another OS or runs a software disk inspection tool from breaking Vista file and system protections or even the offline viewing of data files. ”
Bit. Locker Drive Encryption fully encrypts the entire Windows Vista volume. Designed specifically to prevent the unauthorized disclosure of data when it is at rest. Provides data protection on your Windows client systems, even when the system is in unauthorized hands. Designed to utilize a v 1. 2 Trusted Platform Module (TPM) for secure key storage and boot environment authentication Bit. Locker

What is a Trusted Platform Module? It’s a Smartcard-like module on the motherboard • • Protects secrets Performs cryptographic functions • • • Meets encryption export requirements Can create, store and manage keys • • • RSA, SHA-1, RNG Provides a unique Endorsement Key (EK) Provides a unique Storage Root Key (SRK) Performs digital signature operations Holds Platform Measurements (hashes) Anchors chain of trust for keys and credentials Protects itself against attacks TPM 1. 2 spec: www. trustedcomputinggroup. org
Why use a TPM 1. 2 chip? • The TPM solves the ‘where do we put the encryption key? ’ problem • Hardware can be made to be robust against attacks • • • Certified to be tamper resistant Provides anti-hammering capabilities A TPM is an implementation of a Root-of-Trust • • Enables implementation of the Static Root of Trust Measurement Hardware based solution more secure than software one • Difficult to root trust in software that has to validate itself
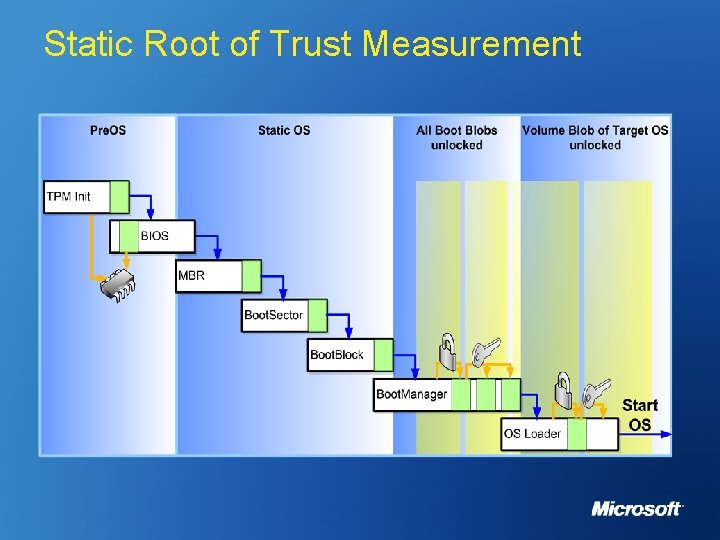
Static Root of Trust Measurement
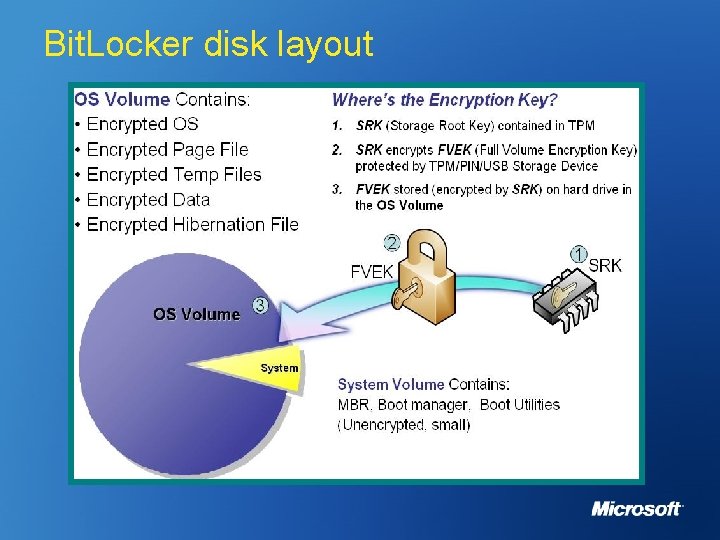
Bit. Locker disk layout
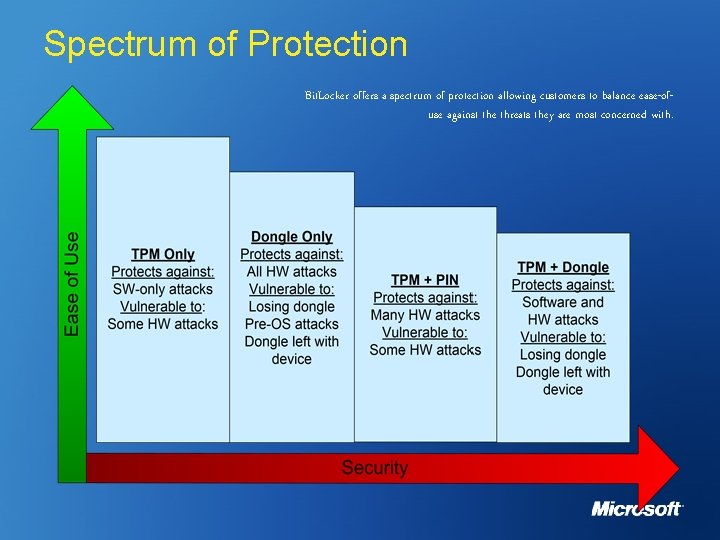
Spectrum of Protection Bit. Locker offers a spectrum of protection allowing customers to balance ease-ofuse against the threats they are most concerned with.
An integrated solution • Bit. Locker is integrated in WMI and Group Policy • • Bit. Locker automatically escrow keys and passwords into AD • • Enables customizable, automated deployment Centralized storage/management keys Recovery console built into the new Vista boot architecture • • Recovery can occur “in the field” Windows operation can continue as normal after a recovery
Further information? • Web Resources: • Specs & Whitepapers: • • TCG: • • www. microsoft. com/technet/windowsvista/security/bitlockr. mspx www. trustedcomputinggroup. org Bit. Locker™ Questions or Ideas: BDEInfo@microsoft. com


© 2006 Microsoft Corporation. All rights reserved. This presentation is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS SUMMARY.
- Slides: 14