What does Information Security IS mean Information security












- Slides: 16


What does Information Security (IS) mean? Information security (IS) is designed to protect the confidentiality, integrity and availability of computer system data from those with malicious intentions. Confidentiality, integrity and availability are sometimes referred to as the CIA Triad of information security. Cybercriminals are becoming more sophisticated and collaborative with every coming year.


Confidentiality. The aim of confidentiality is to ensure that information is hidden from people unauthorized to access it. The confidentiality principle dictates that information should solely be viewed by people with appropriate and correct privileges. The science (and art) used to ensure data confidentiality is cryptography, which involves encryption and decryption methods. To continue, confidentiality can be easily breached so each employee in an organization or company should be aware of his responsibilities in maintaining confidentiality of the information delegated to him for the exercise of his duties. For instance, if an employee allows someone to take a glimpse of his computer screen while he is, at that moment, displaying confidential information on the computer screen may have already constituted a breach of confidentiality. Furthermore, confidentiality and privacy are often used interchangeably. Cryptography - effective manner of protecting confidentiality.

Cryptography involves creating written or generated codes that allows information to be kept secret. Cryptography converts data into a format that is unreadable for an unauthorized user, allowing it to be transmitted without anyone decoding it back into a readable format, thus compromising the data. Information security uses cryptography on several levels. The information cannot be read without a key to decrypt it. The information maintains its integrity during transit and while being stored. Cryptography also aids in nonrepudiation. This means that neither the creator nor the receiver of the information may claim they did not create or receive it.

Cryptography also allows senders and receivers to authenticate each other through the use of key pairs. There are various types of algorithms for encryption, some common algorithms include: Secret Key Cryptography (SKC) - Here only one key is used for both encryption and decryption. This type of encryption is also referred to as symmetric encryption. Public Key Cryptography (PKC): Here two keys are used. This type of encryption is also called asymmetric encryption. One key is the public key and anyone can have access to it. The other key is the private key, and only the owner can access it. The sender encrypts the information using the receiver’s public key. The receiver decrypts the message using his/her private key. For non-repudiation, the sender encrypts plain text using a private key, while the receiver uses the sender’s public key to decrypt it. Thus, the receiver knows who sent it. Hash Functions: These are different from SKC and PKC. They have no key at all and are also called one-way encryption. Hash functions are mainly used to ensure that a file has remained unchanged.

A digital signature guarantees the authenticity of an electronic document or message in digital communication and uses encryption techniques to provide proof of original and unmodified documentation. Digital signatures are used in e-commerce, software distribution, financial transactions and other situations that rely on forgery or tampering detection techniques. A digital signature is also known as an electronic signature. A digital signature is applied and verified, as follows: The document or message sender (signer) or public/private key supplier shares the public key with the end user(s). The sender, using his private key, appends the encrypted signature to the message or document. The end user decrypts the document and verifies the signature, which lets the end user know that the document is from the original sender.

Network security is an over-arching term that describes that the policies and procedures implemented by a network administrator to avoid and keep track of unauthorized access, exploitation, modification, or denial of the network and network resources. This means that a well-implemented network security blocks viruses, malware, hackers, etc. from accessing or altering secure information. The first layer of network security is enforced through a username/password mechanism, which only allows access to authenticated users with customized privileges. When a user is authenticated and granted specific system access, the configured firewall enforces network policies, that is, accessible user services. However, firewalls do not always detect and stop viruses or harmful malware, which may lead to data loss. An anti-virus software or an intrusion prevention system (IPS) is implemented to prevent the virus and/or harmful malware from entering the network. Network security is sometimes confused with information security, which has a different scope and relates to data integrity of all forms, print or electronic.

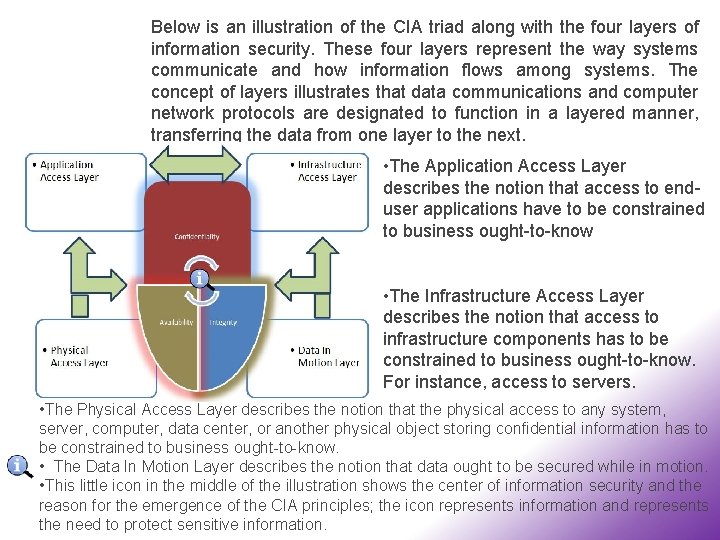
Below is an illustration of the CIA triad along with the four layers of information security. These four layers represent the way systems communicate and how information flows among systems. Тhe concept of layers illustrates that data communications and computer network protocols are designated to function in a layered manner, transferring the data from one layer to the next. • The Application Access Layer describes the notion that access to enduser applications have to be constrained to business ought-to-know • The Infrastructure Access Layer describes the notion that access to infrastructure components has to be constrained to business ought-to-know. For instance, access to servers. • The Physical Access Layer describes the notion that the physical access to any system, server, computer, data center, or another physical object storing confidential information has to be constrained to business ought-to-know. • The Data In Motion Layer describes the notion that data ought to be secured while in motion. • This little icon in the middle of the illustration shows the center of information security and the reason for the emergence of the CIA principles; the icon represents information and represents the need to protect sensitive information.

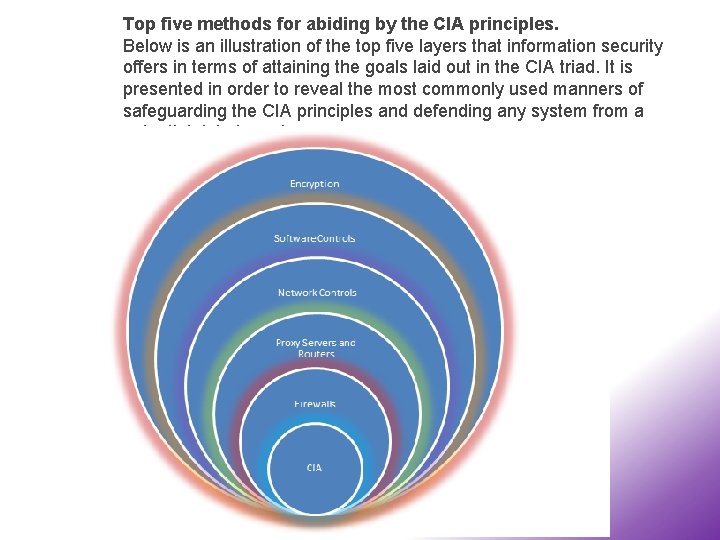
Top five methods for abiding by the CIA principles. Below is an illustration of the top five layers that information security offers in terms of attaining the goals laid out in the CIA triad. It is presented in order to reveal the most commonly used manners of safeguarding the CIA principles and defending any system from a potential data breach.

• The core of the chart is represented by the CIA principles • Firewalls can be hardware-based and software-based. Firewalls are a piece of equipment or software that are designed to block unsolicited connections, protocols, unwanted network activity and block spam and other malicious requests while you are connected a third-party network (usually the Internet). The hardware firewall utilizes packet filtering to examine the header of a packet and decide if the packet should be forwarded or dropped. Firewalls serve as an intermediary between your computer and the Internet connection. Thus, firewalls can block connections that their user did not wish to make, filter out bad data and prevent outside endeavors to gain control or access to your machine. They have a set of predefined rules that enable them to allow, deny or drop connections and as such their function is of a filtering gateway. • A server, through hardware such as proxy server can regulate what the external world sees of the network, this could be a type of protection by providing a “smoke screen” on the network. It can disguise the real network and display a minimal connection to the Internet

• Routers, another piece of hardware, can regulate access to the network, just like firewalls, it may have access lists that allow or deny access into the network. Nonetheless, they route IP packets to the other networks, a thing which is neither performed by firewalls, nor by any other appliance on the network or the Internet. • Network controls are implemented at local level, they involve authentication like logins and passwords. • Software controls are software that prevent malware from penetrating the machines. Should a malware infest the system, software controls are in charge of removing the infection and returning the system to the pre-infestation state. Unlike firewalls, software controls can remove existent malware, malware that has already affected the machine, whereas firewalls cannot deal with malware that has already been loaded on your computer. • Encryption has already been discussed above (Cryptography)

Integrity is one of the five pillars of Information Assurance (IA or IS). Data integrity maintenance is an information security requirement. Integrity is a major Information Security component because users must be able to trust information. Untrusted data is devoid of integrity. Stored data must remain unchanged within an information system (IS), as well as during data transport. Events like storage erosion, error and intentional data or system damage can create data changes. For example, hackers may cause damage by infiltrating systems with malware, including Trojan horses, which overtake computer systems, as well as worms and viruses. An employee may create company damage through intentionally false data entry. Data integrity verification measures include checksums and the use of data comparisons.

Data integrity is enforced in both hierarchical and relational database models. The following three integrity constraints are used in a relational database structure to achieve data integrity: • Entity Integrity: This is concerned with the concept of primary keys. The rule states that every table must have its own primary key and that each has to be unique and not null. • Referential Integrity: This is the concept of foreign keys. The rule states that the foreign key value can be in two states. The first state is that the foreign key value would refer to a primary key value of another table, or it can be null. Being null could simply mean that there are no relationships, or that the relationship is unknown. • Domain Integrity: This states that all columns in a relational database are in a defined domain. The concept of data integrity ensures that all data in a database can be traced and connected to other data. This ensures that everything is recoverable and searchable. Having a single, well-defined and well-controlled data integrity system increases stability, performance, reusability and maintainability. If one of these features cannot be implemented in the database, it must be implemented through the software.

Availability, in the context of a computer system, refers to the ability of a user to access information or resources in a specified location and in the correct format. Availability is one of the five pillars of Information Assurance (IA). The other four are integrity, authentication, confidentiality and nonrepudiation. When a system is regularly non-functioning, information availability is affected and significantly impacts users. In addition, when data is not secure and easily available, information security is affected, i. e. , top secret security clearances. Another factor affecting availability is time. If a computer system cannot deliver information efficiently, then availability is compromised. Data availability must be ensured by storage, which may be local or at an offsite facility. In the case of an offsite facility, an established business continuity plan should state the availability of this data when onsite data is not available. At all times, information must be available to those with clearance.

Resources: http: //www. computerweekly. com/feature/To p-five-threats http: //www. techrepublic. com/blog/itsecurity/the-cia-triad/ http: //resources. infosecinstitute. com/guidingprinciples-in-information-security/ http: //www. isaca. org/chapters 5/Ireland/Docu ments/2012%20 Presentations/Security%20 Thr eats%20 and%20 their%20 implication%20 in%20 Information%20 Systems. pdf http: //www. sciencedirect. com/science/article/ pii/S 1877050914006528